Understanding the Military's Role in Ending State-Sponsored Terrorism
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

THE POLITICS of REPRODUCTION FORMATIONS: ADOPTION, KINSHIP, and CULTURE Emily Hipchen and John Mcleod, Series Editors the Politics of Reproduction
THE POLITICS OF REPRODUCTION FORMATIONS: ADOPTION, KINSHIP, AND CULTURE Emily Hipchen and John McLeod, Series Editors The Politics of Reproduction Adoption, Abortion, and Surrogacy in the Age of Neoliberalism Edited by Modhumita Roy and Mary Thompson THE OHIO STATE UNIVERSITY PRESS COLUMBUS Copyright © 2019 by Th e Ohio State University. Th is edition licensed under a Creative Commons Attribution-NonCommercial-NoDerivs License. Library of Congress Cataloging-in-Publication Data is available online at catalog.loc.gov. Cover design by Nathan Putens Text design by Juliet Williams Type set in Adobe Minion Pro Th e paper used in this publication meets the minimum requirements of the American National Standard for Information Sciences—Permanence of Paper for Printed Library Materials. ANSI Z39.48-1992. We dedicate this volume to the memory of our fathers, Richard E. Thompson Jr. (1924–2011) and Birendra Narayan Roy (1926–2011), and to our mothers, Barbara J. Thompson and Pranati Roy, with love and thanks. CONTENTS Acknowledgments ix INTRODUCTION MODHUMITA ROY AND MARY THOMPSON 1 CHAPTER 1 Precarity and Disaster in Jesmyn Ward’s Salvage the Bones: A Reproductive Justice Reading MARY THOMPSON 25 CHAPTER 2 Privileging God the Father: The Neoliberal Theology of the Evangelical Orphan Care Movement VALERIE A. STEIN 42 CHAPTER 3 White Futures: Reproduction and Labor in Neoliberal Times HEATHER MOONEY 61 CHAPTER 4 One Woman’s Choice Is Another Woman’s Disobedience: Seguro Popular and Threats to Midwifery in Mexico ROSALYNN VEGA 82 CHAPTER 5 The Work/Life -

Race, Migration, and Chinese and Irish Domestic Servants in the United States, 1850-1920
An Intimate World: Race, Migration, and Chinese and Irish Domestic Servants in the United States, 1850-1920 A DISSERTATION SUBMITTED TO THE FACULTY OF THE GRADUATE SCHOOL OF THE UNIVERSITY OF MINNESOTA BY Andrew Theodore Urban IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY Advised by Donna Gabaccia and Erika Lee June 2009 © Andrew Urban, 2009 Acknowledgements While I rarely discussed the specifics of my dissertation with my fellow graduate students and friends at the University of Minnesota – I talked about basically everything else with them. No question or topic was too large or small for conversations that often carried on into the wee hours of the morning. Caley Horan, Eric Richtmyer, Tim Smit, and Aaron Windel will undoubtedly be lifelong friends, mahjong and euchre partners, fantasy football opponents, kindred spirits at the CC Club and Mortimer’s, and so on. I am especially grateful for the hospitality that Eric and Tim (and Tank the cat) offered during the fall of 2008, as I moved back and forth between Syracuse and Minneapolis. Aaron and I had the fortune of living in New York City at the same time in our graduate careers, and I have fond memories of our walks around Stuyvesant Park in the East Village and Prospect Park in Brooklyn, and our time spent with the folks of Tuesday night. Although we did not solve all of the world’s problems, we certainly tried. Living in Brooklyn, I also had the opportunity to participate in the short-lived yet productive “Brooklyn Scholars of Domestic Service” (AKA the BSDS crew) reading group with Vanessa May and Lara Vapnek. -

Appendix C: Military Operations and Planning Scenarios Referred to in This Report
Appendix C: Military Operations and Planning Scenarios Referred to in This Report In describing the past and planned use of various types conducted on the territory of North Vietnam during of forces, this primer mentions a number of military the war (as opposed to air operations in South Vietnam, operations that the United States has engaged in since which were essentially continuous in support of U.S. World War II, as well as a number of scenarios that and South Vietnamese ground forces). The most nota- the Department of Defense has used to plan for future ble campaigns included Operations Rolling Thunder, conflicts. Those operations and planning scenarios are Linebacker, and Linebacker II. summarized below. 1972: Easter Offensive.This offensive, launched by Military Operations North Vietnamese ground forces, was largely defeated 1950–1953: Korean War. U.S. forces defended South by South Vietnamese ground forces along with heavy air Korea (the Republic of Korea) from an invasion by support from U.S. forces. North Korea (the Democratic People’s Republic of Korea). North Korean forces initially came close to 1975: Spring Offensive.This was the final offensive overrunning the entire Korean Peninsula before being launched by North Vietnamese ground forces during the pushed back. Later, military units from China (the war. Unlike in the Easter Offensive, the United States People’s Republic of China) intervened when U.S. forces did not provide air support to South Vietnamese ground approached the Chinese border. That intervention caused forces, and North Vietnamese forces fully conquered the conflict to devolve into a stalemate at the location of South Vietnam. -

The Military's Role in Counterterrorism
The Military’s Role in Counterterrorism: Examples and Implications for Liberal Democracies Geraint Hug etortThe LPapers The Military’s Role in Counterterrorism: Examples and Implications for Liberal Democracies Geraint Hughes Visit our website for other free publication downloads http://www.StrategicStudiesInstitute.army.mil/ To rate this publication click here. hes Strategic Studies Institute U.S. Army War College, Carlisle, PA The Letort Papers In the early 18th century, James Letort, an explorer and fur trader, was instrumental in opening up the Cumberland Valley to settlement. By 1752, there was a garrison on Letort Creek at what is today Carlisle Barracks, Pennsylvania. In those days, Carlisle Barracks lay at the western edge of the American colonies. It was a bastion for the protection of settlers and a departure point for further exploration. Today, as was the case over two centuries ago, Carlisle Barracks, as the home of the U.S. Army War College, is a place of transition and transformation. In the same spirit of bold curiosity that compelled the men and women who, like Letort, settled the American West, the Strategic Studies Institute (SSI) presents The Letort Papers. This series allows SSI to publish papers, retrospectives, speeches, or essays of interest to the defense academic community which may not correspond with our mainstream policy-oriented publications. If you think you may have a subject amenable to publication in our Letort Paper series, or if you wish to comment on a particular paper, please contact Dr. Antulio J. Echevarria II, Director of Research, U.S. Army War College, Strategic Studies Institute, 632 Wright Ave, Carlisle, PA 17013-5046. -

United States and Middle East Relations
Honors American Foreign Policy United States and Middle East Relations I. Background on US Middle East Relations A. Oil and the Middle East 1. Discovery of oil (Iran -1911) 2. Top 10 oil importing nations (Who consumes the most oil?) 3. Top 10 oil exporting countries to the United States (Where does the US import oil from?) B. Franklin Roosevelt and World War II II. Truman and the recognition of Israel (May 14, 1948) A. Pre-Israel History: Palestine: A British Colony 1. British withdrawal and United Nations Partition Plan B. David Ben-Gurion and the Zionist Movement C. President Truman and American Recognition 1. Reasons for Recognition –humanitarian, containment, and political reasons D. Results of Israeli Recognition III. IKE and the Middle East A. Iran: Operation AJAX and the Shah (1953) B. Suez Canal Crisis -July 26, 1956 – March 19, 1957 –France, Israel, Great Britain vs. Egypt 1. Egyptian President Gamal Abdel Nasser seized Suez Canal (July 26, 1956) –privately owned 2. United Kingdom, France, and Israel invaded and took control of canal (November 6, 1956) 3. Eisenhower and US Pressure –UN condemnation, economic pressure, and oil embargo 4. Results of Suez Crisis C. Results of IKE’s Middle East policy IV. JFK and Israeli Aid -JFK sent HAWK anti-aircraft missiles to Israel V. LBJ and Six Day War –June 5-10, 1967 A. Israel attacked Egypt, Syria, and Jordan B. Lyndon Johnson’s Reaction –hotline and 50 F-4 fighters C. Results of Six Day War 1. Israel took Sinai Peninsula and Gaza Strip (Egypt), Golan Heights (Syria), & Jerusalem (Jordan) 2. -

The Foreign Policy Challenges of the Clinton Administration in a Post-Cold War World
Louisiana State University LSU Digital Commons LSU Doctoral Dissertations Graduate School 2017 An Elusive Peace: The orF eign Policy Challenges of the Clinton Administration in a Post-Cold War World Jennifer Perrett aliourG as Louisiana State University and Agricultural and Mechanical College, [email protected] Follow this and additional works at: https://digitalcommons.lsu.edu/gradschool_dissertations Part of the History Commons Recommended Citation Galiouras, Jennifer Perrett, "An Elusive Peace: The orF eign Policy Challenges of the Clinton Administration in a Post-Cold War World" (2017). LSU Doctoral Dissertations. 4310. https://digitalcommons.lsu.edu/gradschool_dissertations/4310 This Dissertation is brought to you for free and open access by the Graduate School at LSU Digital Commons. It has been accepted for inclusion in LSU Doctoral Dissertations by an authorized graduate school editor of LSU Digital Commons. For more information, please [email protected]. AN ELUSIVE PEACE: THE FOREIGN POLICY CHALLENGES OF THE CLINTON ADMINISTRATION IN A POST-COLD WAR WORLD A Dissertation Submitted to the Graduate Faculty of the Louisiana State University and Agricultural and Mechanical College in partial fulfillment of the requirements for the degree of Doctor of Philosophy in The Department of Humanities and Social Sciences by Jennifer Perrett Galiouras B.S., Louisiana State University, 2000 M.A., Louisiana State University-Shreveport, 2009 August 2017 ACKNOWLEDGEMENTS My professional journey began in 2000 as a media advertising executive in the most culturally eclectic and unique city in the world: my native New Orleans. Almost nine years later, I ventured back into campus life at Louisiana State University, which served as a second home to me for so many years, on a changed course I never thought I would have the great fortune to follow. -

Statement of William S. Cohen to the National Commission on Terrorist Attacks Upon the United States
Statement of William S. Cohen to The National Commission On Terrorist Attacks Upon the United States March 23, 2004 Mr. Chairman, Mr. Vice Chairman, and Members of the Commission, I appreciate the opportunity to appear before the Commission to discuss counter- terrorism efforts of the Defense Department and the Interagency during my tenure as Secretary of Defense. You have posed several questions, which I will address to the best of my ability, although I should note that in preparing this statement I have not had access to any non-public records with regard to events that took place during this period three to eight years ago and not all public records are easily accessible despite the internet. I have also organized your questions and my responses in a manner that seems to be most responsive to your objective and that reduces redundancies. You asked that my written testimony be “comprehensive.” A truly comprehensive account would be book length, at least, and require access to materials that are not available to me. This written testimony is already longer than I anticipated, and while a few matters are discussed in detail, in most instances, I find it possible only to summarize matters addressed by your questions. U.S. Counter-Terrorism Strategy Your first question asked about the U.S. counter-terrorism strategy and the role of the Defense Department in that strategy during the second Clinton Administration. While the second Clinton Administration’s approach built on the first Administration’s efforts, just as my approach derived from my work on the Senate Intelligence and Armed Services committees, I would point to President Clinton’s December 5, 1996, announcement of the formation of his national security team for his second term. -

1998 U.S. Embassy Bombings in East Africa
1998 U.S. Embassy Bombings in East Africa On August 7, 1998, the U.S. Embassies in Tanzania and Kenya were almost simultaneously attacked. One car bomb was detonated at each site, resulting in massive casualties and injuries of both embassy staff and local civilians. A total of 213 people were killed, of whom 44 were American Embassy employees (12 Americans and 32 Foreign Service National employees). Ten Americans and eleven FSNs were seriously injured, as were an estimated 4,000 Kenyan civilians. The U.S. Department of State responded quickly by dispatching special teams to the region to assist with rescue and recovery and by issuing a travel advisory to all U.S. citizens abroad. An intense investigation ensued and on August 20, 1998, President Clinton authorized Operation Infinite Reach. The mission was a retaliatory missile attack on the Al-Shifa pharmaceutical company in Sudan and Al-Qaeda training camps in Afghanistan. This crisis is important While the American media because the bombing of the and public were distracted U.S. embassies in Kenya by sexual scandals, the and Tanzania changed the international intelligence way the U.S. Government community had been slowly perceived the threat of becoming more aware terrorism. It was significant of the increased danger because the size of the of terrorist organizations bomb served as a warning worldwide. signal to U.S. intelligence of the potential damage Occasions for terrorists could cause. Not Decision only were the bombings a • How should the direct attack on the U.S., immediate safety of U.S. Damaged cars and debris cover the ground outside the U.S. -

Targeted Killing As an Element of U.S. Foreign Policy in the War on Terror
Targeted Killing as an Element of U.S. Foreign Policy in the War on Terror A Monograph by MAJ Matthew J. Machon U.S. Army School of Advanced Military Studies United States Army Command and General Staff College Fort Leavenworth, Kansas AY 05-06 Approved for Public Release; Distribution is Unlimited Form Approved REPORT DOCUMENTATION PAGE OMS No. 0704-0188 The public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions. searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing the burden, to Department of Defense. Washington Headquarters Services, Directorate for Information Operations and Reports (0704-0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302. Respondents should be aware that not withstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. 1. REPORT DATE (DD-MM- YYYY) 2. REPORT TYPE 3. DATES COVERED (From - To) 25-05-2006 MONOGRAPH SEPT 2005-MAR 2006 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER Targeted Killing as an Element of the U.S. War on Terror 5b. GRANT NUMBER 5c. PROGRAM ELEMENT NUMBER 6. AUTHOR(S) 5d. PROJECT NUMBER MAJ Matthew J. Machon 5e. TASK NUMBER 5f. WORK UNIT NUMBER 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. -
Bill Clinton -Foreign Policy
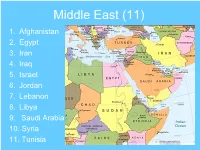
Middle East (11) 1. Afghanistan 2. Egypt 3. Iran 4. Iraq 5. Israel 6. Jordan 7. Lebanon 8. Libya 9. Saudi Arabia 10. Syria 11. Tunisia 1. Afghanistan • Carter • Soviet Invasion • Reagan • supported Mujahedeen • Reagan • INF Treaty • Clinton • Operation Infinite Reach • GW • Operation Enduring Freedom • Obama • US forces will withdraw by 2014 2. Egypt • IKE • Suez Crisis • LBJ • 6 Day War • Nixon • Yom Kippur War Started • Ford • Yom Kippur War Ended • Carter • Camp David Accords • Obama • Cairo Speech • Obama • Called for Mubarak to step down 3. Iran • IKE • Operation AJAX • Carter • Iran-Hostage Crisis • Reagan • Iran-Contra Scandal • GW • Axis of Evil 4. Iraq • Reagan • Iran-Iraq War • Herby • Operation Desert Storm • Clinton • 3 missile attacks • GW • Axis of Evil • GW • Operation Iraqi Freedom • Obama • Withdrew Iraq (2011) 5(A). Israel • Truman • Recognition • IKE • Suez Canal Crisis • JFK • First sent military aid • LBJ • 6 Day War • Nixon • Yom Kippur War • Carter • Camp David Accords • Clinton • Oslo Accords • Clinton • Treaty of Peace • Clinton • Israeli withdraw from Lebanon 5(B). Israel • GW • Roadmap to Peace • GW • July War • GW • Gaza War • Obama • Called for an end of settlements • Obama • Dissenting vote on Palestine 6. Jordan • LBJ • 6 Day War • Clinton • Treaty of Peace 7. Lebanon • Reagan • Withdrew US troops • Clinton • Negotiated Israeli withdraw • GW • July War (2006) 8. Libya • Reagan • Gulf of Sidra • Reagan • West Berlin bombing • Reagan • Operation El Dorado Canyon • Reagan • Lockerbie bombing • GW • Axis of Evil • GW • Disarmament and Diplomatic Ties • Obama • NATO: Unified Protector 9. Saudi Arabia • Exporter • #3 Exporter of oil to US • Holy Land • Land: Mecca and Medina 10. -

Chemical Weapons in the Sudan
Report: Chemical Weapons in the Sudan CHEMICAL WEAPONS IN THE SUDAN: ALLEGATIONS AND EVIDENCE by Michael Barletta1 Michael Barletta is a Senior Research Associate at the Center for Nonproliferation Studies, Monterey Institute of International Studies. He directed research and production of the Center’s “Fact Sheet Series on WMD in the Middle East” and “Resources on the Missile Crisis over Cyprus,” both published online (http://cns.miis.edu/). Barletta is a Ph.D. candidate in Political Science at the University of Wisconsin-Madison, and is completing a dissertation entitled “Ideas and Domestic Politics in International Security Cooperation: Emergence of an Argentine-Brazilian Nuclear Regime.” n August 20, 1998, U.S. Tomahawk cruise mis- however, few if any experts would have anticipated ei- siles struck and destroyed al-Shifa Pharmaceu- ther the U.S. attack on Shifa or the specific allegations Otical Factory in Khartoum, the capital of the regarding production at that facility. Prior to August 20, Sudan. The United States said the attack was in response 1998, no U.S. official had ever publicly identified the to the bombings two weeks earlier of U.S. embassies in Sudan as a confirmed CW proliferant or “country of con- Kenya and Tanzania, which it believed were orchestrated cern.” Moreover, all prior allegations about the Sudan by Osama bin Laden. U.S. officials said the bombing of that specified a particular CW agent had identified it as the Sudanese facility was necessary to prevent bin Laden mustard gas, not VX. In addition, although a number of from acquiring deadly nerve gas precursors that were locations had been alleged to be involved in CW devel- being produced at Shifa. -

War in Afghanistan 2001
Afghanistan People and Pre-9/11 History Afghanistan Afghanistan Today: Religion • 80% Sunni Muslim • 19% Shia Muslim Afghanistan Today: Ethnicities • 42% Pashtun • 27% Tajik Life Expectancy = 50.11 years World Ranking = Updated: 219 out of 223 2/12/14 Population Growth Expected Current 31.1 million 2025 45 million 2050 75 million Updated: 2/12/14 Early Afghan History Afghanistan “Graveyard of the Empires” Afghanistan Independence (1919) from Great Britain (3 tries) • 1839 • 1878 • 1917 Afghan-Soviet War Dec 25, 1979 – Feb 15, 1989 American Support of the Mujahedeen • $3 billion in aid Stinger Missiles Results of the Afghan-Soviet War • over 1 million killed • over 5 million fled the country • over 2 million displaced within the country • 50% of all Afghans were killed, wounded, or displaced by the Soviet invasion Afghanistan Needed to Rebuild Civil War (1989 – 1996) Taliban Take Control of Afghanistan (1996 – 2001) Taliban and Al-Qaeda Taliban –political movement that governed Afghanistan from 1996 - 2001 Al-Qaeda –Islamic fundamentalist group whose objective is to end foreign influence in Muslim countries Osama bin Laden and al Qaeda Al-Qaeda and Worldwide Terrorism (based in Afghanistan) World Trade Center (1993) • 6 killed • 1,042 wounded Ramzi Yousef • Over $500 million in damages Uncle was: KSM Al Khobar, Saudi Arabia June 25, 1996 Khobar Towers • 19 killed • 372 wounded US Embassies Under Attack August 7, 1998 Dar es Salaam, Tanzania Nairobi, Kenya • 213 K & 4,000 W 11 K & 77 W American Response: Missile Attack Operation Infinite Reach August 20, 1998 Sudan Afghanistan Memorandum of Notification Clinton gave the order for the CIA to use lethal force to kill bin Laden.