Celebrating 50 Years of Campus-Wide Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security on the Mainframe Stay Connected to IBM Redbooks
Front cover Security on the IBM Mainframe Operating system and application security IBM Security Blueprint and Framework IBM mainframe security concepts Karan Singh Lennie Dymoke-Bradshaw Thomas Castiglion Pekka Hanninen Vincente Ranieri Junior Patrick Kappeler ibm.com/redbooks International Technical Support Organization Security on the IBM Mainframe April 2010 SG24-7803-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition (April 2010) This edition applies to the IBM System z10 Enterprise Class server, the IBM System z10 Business Class server, and Version 1, Release 11, Modification 0 of z/OS (product number 5694-A01). © Copyright International Business Machines Corporation 2010. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . .x Preface . xi The team who wrote this book . xi Now you can become a published author, too! . xii Comments welcome. xii Stay connected to IBM Redbooks . xiii Part 1. Introduction . 1 Chapter 1. Introduction. 3 1.1 IBM Security Framework. 4 1.1.1 People and identity . 5 1.1.2 Data and information. 5 1.1.3 Application and process . 5 1.1.4 Network, server, and endpoint . 5 1.1.5 Physical Infrastructure . 6 1.2 Framework and Blueprint . 7 1.3 IBM Security Blueprint. 7 Chapter 2. Security of the IBM Mainframe: yesterday and today . 13 2.1 Operating systems . 14 2.1.1 z/OS operating system family . 14 2.1.2 z/VM Hypervisor family . -
Operating Systems
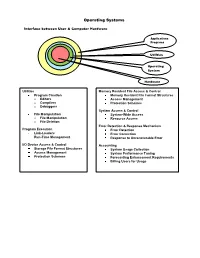
Operating Systems Interface between User & Computer Hardware Applications Programs Utilities Operating System Hardware Utilities Memory Resident File Access & Control Program Creation Memory Resident File Format Structures o Editors Access Management o Compilers Protection Schemes o Debuggers System Access & Control File Manipulation System-Wide Access o File Manipulation Resource Access o File Deletion Error Detection & Response Mechanism Program Execution Error Detection Link-Loaders Error Correction Run-Time Management Response to Unrecoverable Error I/O Device Access & Control Accounting Storage File Format Structures System Usage Collection Access Management System Performance Tuning Protection Schemes Forecasting Enhancement Requirements Billing Users for Usage Resource Manager O/S KernelKernel I/O Controller Printers, Keyboards, I/O Controller Monitors, Portions of Cameras, the O/S Etc. currently in use Computer Main System Memory Portions of Various I/O Application Devices Programs Currently in use Operating System Data Application Programs I/O Controller Storage Processor Processor Data Processor Processor Operation Allocation of Main Memory is made jointly by both the O/S and Memory Management Hardware O/S controls access to I/O devices by Application Programs O/S controls access to and use of files O/S controls access to and use of the processors, i.e., how much time can be allocated to the execution of a particular Application Program Classification of Operating Systems Interactive O/S Keyboard & Monitor Access to O/S Immediate, -

8. IBM Z and Hybrid Cloud
The Centers for Medicare and Medicaid Services The role of the IBM Z® in Hybrid Cloud Architecture Paul Giangarra – IBM Distinguished Engineer December 2020 © IBM Corporation 2020 The Centers for Medicare and Medicaid Services The Role of IBM Z in Hybrid Cloud Architecture White Paper, December 2020 1. Foreword ............................................................................................................................................... 3 2. Executive Summary .............................................................................................................................. 4 3. Introduction ........................................................................................................................................... 7 4. IBM Z and NIST’s Five Essential Elements of Cloud Computing ..................................................... 10 5. IBM Z as a Cloud Computing Platform: Core Elements .................................................................... 12 5.1. The IBM Z for Cloud starts with Hardware .............................................................................. 13 5.2. Cross IBM Z Foundation Enables Enterprise Cloud Computing .............................................. 14 5.3. Capacity Provisioning and Capacity on Demand for Usage Metering and Chargeback (Infrastructure-as-a-Service) ................................................................................................................... 17 5.4. Multi-Tenancy and Security (Infrastructure-as-a-Service) ....................................................... -

CA Top Secret for Z/OS Control Options Guide
CA Top Secret® for z/OS Control Options Guide r15 Ninth Edition This Documentation, which includes embedded help systems and electronically distributed materials (hereinafter referred to as the “Documentation”), is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

VALIDATED PRODUCTS LIST 1992 No.2
NISTIR 4820 (Supersedes NISTIR 4739) VALIDATED PRODUCTS LIST 1992 No. 2 Programming Languages Database Language SQL Graphics GOSIP POSIX Security Judy B. Kailey U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technoiogy Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 “QC — TOO .U56 4820 NIST 1992 N I STIR 482 (Supersedes NISTIR 4739) ' O VALIDATED PRODUCTS LIST 1992 No.2 Programming Languages Database Language SQL Graphics GOSIP POSiX Security Judy B. Kailey U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 April 1992 (Supersedes January 1992 Issue) U.S. DEPARTMENT OF COMMERCE Barbara Hackman Franklin, Secretary TECHNOLOGY ADMINISTRATION Robert M. White, Linder Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director FOREWORD The Validated Products List (formerly called the Validated Processor List) is a collection of registers describing implementations of Federal Information Processing Standards (FTPS) that have been validated for conformance to FTPS. The Validated Products List also contains information about the organizations, test methods and procedures that support the validation programs for the FTPS identified in this document. The Validated Products List is updated quarterly. lii ' " M'- v^,.^.:v;/i'fr•i•:‘fey^^?4 .•:, .V.' ini‘,r^f' isfc'^feV VihV'’, !iV.V I t: 4 #> vm- 'at' Mil! .M'? Of'S8r'»'' SIVS 'V-tv. ','V ..(Vi feiii yA ' r' ' '4: ,. = r,: 0 r^'-' ".V.^l , ;‘ • » JjTT ;»»!£ ... •':«5(4i ' |i“' T" •.(''’'ia\.':l'"' f*l, r-’i"' i'-" '.:"::'.".vi ';... '('?. .;r'H vl. '' ' " .. i.” -' f-j'" , '' '(^ • '.v;.» . -

Chapter 10 Introduction to Batch Files
Instructor’s Manual Chapter 10 Lecture Notes Introduction to Batch Files Chapter 10 Introduction to Batch Files LEARNING OBJECTIVES 1. Compare and contrast batch and interactive processing. 2. Explain how batch files work. 3. Explain the purpose and function of the REM, ECHO, and PAUSE commands. 4. Explain how to stop or interrupt the batch file process. 5. Explain the function and use of replaceable parameters in batch files. 6. Explain the function of pipes, filters, and redirection in batch files. STUDENT OUTCOMES 1. Use Edit to write batch files. 2. Use COPY CON to write batch files. 3. Write and execute a simple batch file. 4. Write a batch file to load an application program. 5. Use the REM, PAUSE, and ECHO commands in batch files. 6. Terminate a batch file while it is executing. 7. Write batch files using replaceable parameters. 8. Write a batch file using pipes, filters, and redirection. CHAPTER SUMMARY 1. Batch processing means running a series of instructions without interruption. 2. Interactive processing allows the user to interface directly with the computer and update records immediately. 3. Batch files allow a user to put together a string of commands and execute them with one command. 4. Batch files must have the .BAT or .CMD file extension. 5. Windows looks first internally for a command, then for a .COM files extension, then for a .EXE file extension, and finally for a .BAT or .CMD file extension. 6. Edit is a full-screen text editor used to write batch files. 7. A word processor, if it has a means to save files in ASCII, can be used to write batch files. -

Uni Hamburg – Mainframe Summit 2010 Z/OS – the Mainframe Operating System
Uni Hamburg – Mainframe Summit 2010 z/OS – The Mainframe Operating System Appendix 2 – JES and Batchprocessing Redelf Janßen IBM Technical Sales Mainframe Systems [email protected] © Copyright IBM Corporation 2010 Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.1 Introduction to the new mainframe Chapter 7: Batch processing and the Job Entry Subsystem (JES) © Copyright IBM Corp., 2010. All rights reserved. Introduction to the new mainframe Chapter 7 objectives Be able to: • Give an overview of batch processing and how work is initiated and managed in the system. • Explain how the job entry subsystem (JES) governs the flow of work through a z/OS system. © Copyright IBM Corp., 2010. All rights reserved. 3 Introduction to the new mainframe Key terms in this chapter • batch processing • procedure • execution • purge • initiator • queue • job • spool • job entry subsystem (JES) • symbolic reference • output • workload manager (WLM) © Copyright IBM Corp., 2010. All rights reserved. 4 Introduction to the new mainframe What is batch processing? Much of the work running on z/OS consists of programs called batch jobs. Batch processing is used for programs that can be executed: • With minimal human interaction • At a scheduled time or on an as-needed basis. After a batch job is submitted to the system for execution, there is normally no further human interaction with the job until it is complete. © Copyright IBM Corp., 2010. All rights reserved. 5 Introduction to the new mainframe What is JES? In the z/OS operating system, JES manages the input and output job queues and data. -

Approaches to Optimize Batch Processing on Z/OS
Front cover Approaches to Optimize Batch Processing on z/OS Apply the latest z/OS features Analyze bottlenecks Evaluate critical path Alex Louwe Kooijmans Elsie Ramos Jan van Cappelle Lydia Duijvestijn Tomohiko Kaneki Martin Packer ibm.com/redbooks Redpaper International Technical Support Organization Approaches to Optimize Batch Processing on z/OS October 2012 REDP-4816-00 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (October 2012) This edition applies to all supported z/OS versions and releases. This document created or updated on October 24, 2012. © Copyright International Business Machines Corporation 2012. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team who wrote this paper . vii Now you can become a published author, too! . viii Comments welcome. viii Stay connected to IBM Redbooks . ix Chapter 1. Getting started . 1 1.1 The initial business problem statement. 2 1.2 How to clarify the problem statement . 3 1.3 Process to formulate a good problem statement . 3 1.4 How to create a good business case . 5 1.5 Analysis methodology . 6 1.5.1 Initialization . 6 1.5.2 Analysis. 6 1.5.3 Implementation . 10 Chapter 2. Analysis steps. 13 2.1 Setting the technical strategy . 14 2.2 Understanding the batch landscape . 15 2.2.1 Identifying where batch runs and the available resources . 15 2.2.2 Job naming conventions . 15 2.2.3 Application level performance analysis. -

Hercules General Information
Hercules System/370, ESA/390, z/Architecture Emulator Hercules – General Information Version 3 Release 06 Contents Contents ........................................................................................................................................................2 Figures...........................................................................................................................................................7 Tables............................................................................................................................................................9 1. Preface .............................................................................................................................................10 1.1 Edition information ........................................................................................................................10 1.2 What this book is about.................................................................................................................10 1.3 Who should read this book ...........................................................................................................10 1.4 What you need to know to understand this book..........................................................................10 1.5 How to use this book.....................................................................................................................10 1.6 Revision Notice .............................................................................................................................10 -

OS Structures and System Calls
COS 318: Operating Systems OS Structures and System Calls Kai Li Computer Science Department Princeton University (http://www.cs.princeton.edu/courses/cos318/) Outline Protection mechanisms OS structures System and library calls 2 Protection Issues CPU Kernel has the ability to take CPU away from users to prevent a user from using the CPU forever Users should not have such an ability Memory Prevent a user from accessing others’ data Prevent users from modifying kernel code and data structures I/O Prevent users from performing “illegal” I/Os Question What’s the difference between protection and security? 3 Architecture Support: Privileged Mode An interrupt or exception (INT) User mode Kernel (privileged) mode • Regular instructions • Regular instructions • Access user memory • Privileged instructions • Access user memory • Access kernel memory A special instruction (IRET) 4 Privileged Instruction Examples Memory address mapping Flush or invalidate data cache Invalidate TLB entries Load and read system registers Change processor modes from kernel to user Change the voltage and frequency of processor Halt a processor Reset a processor Perform I/O operations 5 x86 Protection Rings Privileged instructions Can be executed only When current privileged Level (CPR) is 0 Operating system kernel Level 0 Operating system services Level 1 Level 2 Applications Level 3 6 Layered Structure Hiding information at each layer Layered dependency Examples Level N THE (6 layers) . MS-DOS (4 layers) . Pros Level 2 Layered abstraction -

NASA Contrattbr 4Report 178229 S E M I a N N U a L R E P O
NASA Contrattbr 4Report 178229 ICASE SEMIANNUAL REPORT April 1, 1986 through September 30, 1986 Contract No. NAS1-18107 January 1987 INSTITUTE FOR COMPUTER APPLICATIONS IN SCIENCE AND ENGINEERING NASA Langley Research Center, Hampton, Virginia 23665 Operatsd by the Universities Space Research Association National Aeronautics and Space Ad minis t rat ion bnglay Research Center HamDton,Virginia23665 CONTENTS Page Introduction .............................................................. iii Research in erogress ...................................................... 1 Reports and Abstracts ..................................................... 32 ICASE Colloquia........................................................... 49 ICASE Summer Activities ................................................... 52 Other Activities .......................................................... 58 ICASE Staff ............................................................... 60 i INTRODUCTION The Institute for Computer Applications in Science and Engineering (ICASE) is operated at the Langley Research Center (LaRC) of NASA by the Universities Space Research Associat€on (USRA) under a contract with the Center. USRA is a nonpro€it consortium of major U. S. colleges and universities. The Institute conducts unclassified basic research in applied mathematics, numerical analysis, and computer science in order to extend and improve problem-solving capabilities in science and engineering, particularly in aeronautics and space. ICASE has a small permanent staff. Research -

CA Top Secret R16 Security Target
CA Top Secret r16 Security Target ST Version: 1.0 August 18, 2017 3333 Warrenville Road Suite 800 Lisle, IL 60532 Prepared By: Cyber Assurance Testing Laboratory 304 Sentinel Drive, Suite 100 Annapolis Junction, MD 20701 Security Target CA Top Secret r16 Table of Contents 1 Security Target Introduction ................................................................................................................. 6 1.1 ST Reference ................................................................................................................................. 6 1.1.1 ST Identification ................................................................................................................... 6 1.1.2 Document Organization ........................................................................................................ 6 1.1.3 Terminology .......................................................................................................................... 7 1.1.4 Acronyms .............................................................................................................................. 8 1.1.5 References ............................................................................................................................. 9 1.2 TOE Reference .............................................................................................................................. 9 1.3 TOE Overview .............................................................................................................................