Icts and Human Rights Practice
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chair of the Committee on the Elimination of Discrimination Against Women (Ms
GA65 Third Committee Subject to change – Status as of 8 October 2010 Special procedure mandate-holders, Chairs of human rights treaty bodies or Chairs of Working Groups presenting reports Monday, 11 October (am) Chair of the Committee on the Elimination of Discrimination against Women (Ms. Xiaoqiau ZOU, Vice-Chair, on behalf of Ms. Naela GABR, Chair of CEDAW) – oral report and interactive dialogue. Special Rapporteur on violence against women, its causes and consequences, Ms. Rashida MANJOO – oral report Wednesday, 13 October (pm) Special Representative of the Secretary-General on violence against children, Ms. Marta SANTOS PAIS. Chair of the Committee on the Rights of the Child, Ms. Yanghee LEE - oral report. Special Rapporteur on the sale of children, child prostitution and child pornography, Ms. Najat M’jid MAALLA Monday, 18 October (am) Special Rapporteur on the situation of human rights and fundamental freedom of indigenous people, Mr. James ANAYA Tuesday, 19 October (am) Chair of the Committee against Torture, Mr. Claudio GROSSMAN – oral report and interactive dialogue. Chair of the Subcommittee on Prevention of Torture, Mr. Victor Manuel RODRIGUEZ RESCIA – oral report and interactive dialogue. Wednesday, 20 October (pm) Independent Expert on minority issues, Ms. Gay McDOUGALL. Special Rapporteur on the situation of human rights in Myanmar, Mr. Tomas Ojea QUINTANA. Special Rapporteur on the situation of human rights in the Palestinian territories occupied since 1967, Mr. Richard FALK. Thursday, 21 October (am) Special Rapporteur on the right to food, Mr. Olivier DE SCHUTTER. Independent expert on the effects of foreign debt and other related international financial obligations of States on the full enjoyment of human rights, particularly economic, social and cultural rights, Mr. -

Special Procedure Mandate-Holders Presenting to the Third Committee
GA66 Third Committee Subject to change – Status as of 7 October 2011 Special procedure mandate-holders, Chairs of human rights treaty bodies or Chairs of Working Groups presenting reports Monday, 10 October (am) • Chair of the Committee on the Elimination of Discrimination against Women, Ms. Silvia Pimentel – oral report and interactive dialogue. • Special Rapporteur on violence against women, its causes and consequences, Ms. Rashida MANJOO report and interactive dialogue. Wednesday, 12 October (pm) • Chair of the Committee on the Rights of the Child, Mr. Jean Zermatten, – oral report. • Special Representative of the Secretary-General on violence against children, Ms. Marta SANTOS PAIS. • Special Rapporteur on the sale of children, child prostitution and child pornography, Ms. Najat M’jid MAALLA. Monday, 17 October (am) • Special Rapporteur on the situation of human rights and fundamental freedoms of indigenous people, Mr. James ANAYA. Tuesday, 18 October (am) • Chair of the Committee against Torture, Mr. Claudio GROSSMAN – oral report and interactive dialogue. • Chair of the Subcommittee on Prevention of Torture, Mr. Malcolm David Evans – oral report and interactive dialogue. • Special Rapporteur on torture and other cruel, inhuman or degrading treatment of punishment, Mr. Juan MENDEZ Wednesday, 19 October (pm) • Special Rapporteur on the situation of human rights in Iran, Mr. Ahmed SHAHEED. • Special Rapporteur on the situation of human rights in Myanmar, Mr. Tomas Ojea QUINTANA. • Special Rapporteur on the situation of human rights in the Democratic People’s Republic of Korea, Mr. Marzuki DARUSMAN. Thursday, 20 October (am) • Special Rapporteur on the situation of human rights in the Palestinian territories occupied since 1967, Mr. -

Say It Loud: Protecting Protest in Australia
Say it loud: Protecting Protest in Australia Contact Hugh de Kretser Human Rights Law Centre Level 5, 175 Liverpool St Sydney NSW 2000 Level 17, 461 Bourke Street Melbourne VIC 3000 T: +61 (3) 8636 4450 E: [email protected] W: www.hrlc.org.au Human Rights Law Centre Acknowledgements The Human Rights Law Centre protects and This report was researched and written promotes human rights in Australia and beyond by Hannah Ryan, Angela Chen and through a strategic mix of legal action, advocacy, Aruna Sathanapally. research, education and UN engagement. The Human Rights Law Centre thanks We are an independent and not-for-profit The Myer Foundation for generously organisation and donations are tax deductible. supporting this project. Follow us: @rightsagenda Thank you also to all of the organisations, academics and individuals who participated Join us: www.facebook.com/ in the research for this report and provided HumanRightsLawCentreHRLC/ valuable advice and guidance. Contents Introduction 2 Principles 3 Principle 1 Protest activities are protected by 4 the Australian Constitution and international law. Principle 2 Any regulation of protest must be 5 limited to what is necessary and proportionate. Principle 3 As far as possible, protesters should be 7 able to choose how they protest. Principle 4 Laws affecting protest should be 9 drafted as clearly and carefully as possible. Principle 5 Laws regulating protest should not 11 rely on excessive police discretion, and where discretion is necessary it should be properly guided by the law. Principle 6 Lawmakers and governments 12 (including police) should take positive steps to promote freedoms of expression and assembly. -
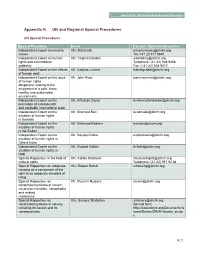
Appendix K. UN and Regional Special Procedures
Appendix K: UN and Regional Special Procedures Appendix K. UN and Regional Special Procedures UN Special Procedures Special Procedure Name Contact / Special instructions Independent Expert on minority Ms. Rita Izsák [email protected] issues Tel: +41 22 917 9640 Independent Expert on human Ms. Virginia Dandan [email protected] rights and international Telephone: (41-22) 928 9458 solidarity Fax: (+41-22) 928 9010 Independent Expert on the effects Mr. Cephas Lumina [email protected] of foreign debt Independent Expert on the issue Mr. John Knox [email protected] of human rights obligations relating to the enjoyment of a safe, clean, healthy and sustainable environment Independent Expert on the Mr. Alfred de Zayas [email protected] promotion of a democratic and equitable international order Independent Expert on the Mr. Shamsul Bari [email protected] situation of human rights in Somalia Independent Expert on the Mr. Mashood Baderin [email protected] situation of human rights in the Sudan Independent Expert on the Mr. Doudou Diène [email protected] situation of human rights in Côte d’Ivoire Independent Expert on the Mr. Gustavi Gallón [email protected] situation of human rights in Haiti Special Rapporteur in the field of Ms. Farida Shaheed [email protected] cultural rights Telephone: (41-22) 917 92 54 Special Rapporteur on adequate Ms. Raquel Rolnik [email protected] housing as a component of the right to an adequate standard of living Special Rapporteur on Mr. Mutuma Ruteere [email protected] contemporary forms of racism, racial discrimination, xenophobia and related intolerance Special Rapporteur on Ms. Gulnara Shahinian [email protected] contemporary forms of slavery, Special form: including its causes and its http://www.ohchr.org/Documents/Is consequences sues/Slavery/SR/AFslavery_en.do c K-1 Appendix K: UN and Regional Special Procedures Special Procedure Name Contact / Special instructions Special Rapporteur on Mr. -

Engaging U.N. Special Procedures to Advance Human Rights at Home: a Guide for U.S
ENGAGING U.N. SPECIAL PROCEDURES TO ADVANCE HUMAN RIGHTS AT HOME: A GUIDE FOR U.S. ADVOCATES JULY 2015 THE COLUMBIA LAW SCHOOL HUMAN RIGHTS INSTITUTE The Human Rights Institute sits at the heart of human rights teaching, practice, and scholarship at Columbia Law School. Founded in 1998 by the late Professor Louis Henkin, the Institute draws on the Law School’s deep human rights tradition to support and influence human rights practice in the United States and throughout the world. The Institute focuses its work in three main substantive areas: Counterterrorism, Armed Conflict and Human Rights; Human Rights in the United States; and Human Rights in the Global Economy. We have developed distinct approaches to our work, building bridges between scholarship and activism, developing capacity within the legal community, engaging governments, and modeling new strategies for progress. ACKNOWLEDGEMENTS This report was researched and drafted by Sara Kayyali, Nawal Maalouf, Paula Mendez, and Ami Shah, students in the Columbia Law School Human Rights Clinic during the 2013-2014 academic year. Risa Kaufman, executive director of the Columbia Law School Human Rights Institute and acting co-director of the Human Rights Clinic during the 2013-2014 academic year, supervised the research and drafting of the report and edited its contents. Columbia Law School student Shan Khan conducted interviews and contributed research and drafting. Greta Moseson, program manager for Columbia Law School’s Human Rights Institute, oversaw the report’s design and production. We are grateful to the human rights advocates, former and current U.N. special procedures, and former and current U.S. -

Catalysts for Rights: the Unique Contribution of the UN’S Independent Experts on Human Rights
Foreign Policy October 2010 at BROOKINGS Catalysts for for Catalysts r ights: The Unique Contribution of the UN’s Independent Experts on Human Rights the UN’s of Unique Contribution The Catalysts for rights: The Unique Contribution of the UN’s Independent Experts on Human Rights TEd PiccoNE Ted Piccone BROOKINGS 1775 Massachusetts Ave, NW, Washington, DC 20036 www.brookings.edu Foreign Policy October 2010 at BROOKINGS Catalysts for rights The Unique Contribution of the U.N.’s Independent Experts on Human Rights Final Report of the Brookings Research Project on Strengthening U.N. Special Procedures TEd PiccoNE The views expressed in this report do not reflect an official position of The Brookings Institution, its Board, or Advisory Council members. © 2010 The Brookings Institution TABLE oF CoNTENTS acknowledgements . iii Members of Experts advisory group . v list of abbreviations . vi Executive summary ....................................................................... viii introduction . 1 Context . 2 Methodology . 3 A Short Summary of Special Procedures . 5 summary of findings . 9 Country Visits . .9 Follow-Up to Country Visits..............................................................19 Communications . 20 Resources . 31 Joint Activities and Coordination . .32 Code of Conduct . 34 Training . .34 Universal Periodic Review...............................................................35 Relationship with Treaty Bodies . 36 recommendations..........................................................................38 Appointments . 38 Country Visits and Communications .......................................................38 Follow-Up Procedures . 40 Resources . .41 Training . .41 Code of Conduct . 42 Relationship with UPR, Treaty Bodies, and other U.N. Actors . .42 appendices Appendix A HRC Resolution 5/1, the Institution Building Package ...........................44 Appendix B HRC Resolution 5/2, the Code of Conduct . .48 Appendix C Special Procedures of the HRC - Mandate Holders (as of 1 August 2010) . -

[email protected] Sent to the Committee E-Mail Address ECOSOC Plenary
NMUN • NY HUMAN RIGHTS COUNCIL BACKGROUND GUIDE 2012 Written By: Patrick Parsons, Andrea Wong, Monika Milinauskyte, Jane Kim nmun.org NATIONAL 1 - 5 April 2012 - Sheraton COLLEGIATE CONFERENCE 3 - 7 April 2012 - Marriott associationTM CONTACT THE NMUN Please consult the FAQ section of nmun.org for answers to your questions. If you do not find a satisfactory answer you may also contact the individuals below for personal assistance. They may answer your question(s) or refer you to the best source for an answer. NMUN Director-General (Sheraton) NMUN Director-General (Marriott) Amanda M. D’Amico | [email protected] Nicholas E. Warino | [email protected] NMUN Office NMUN Secretary-General [email protected] Andrew N. Ludlow | [email protected] T: +1. 612.353.5649 | F: +1.651.305.0093 NMUN•NY 2012 Important Dates IMPORTANT NOTICE: To make hotel reservations, you must use the forms at nmun.org and include a $1,000 deposit. Discount rates are available until the room block is full or one month before the conference – whichever comes first. PLEASE BOOK EARLY! 31 January 2012 • Confirm Attendance & Delegate Count. (Count may be changed up to 1 March) • Make Transportation Arrangements - DON’T FORGET! (We recommend confirming hotel accommodations prior to booking flights.) 15 February 2012 • Committee Updates Posted to www.nmun.org 1 March 2012 • Hotel Registration with FULL PRE-PAYMENT Due to Hotel - Register Early! Group Rates on hotel rooms are available on a first come, first served basis until sold out. Group rates, if still available, may not be honored after that date. -

UPN Alm.Del - Bilag 92 Offentligt
Det Udenrigspolitiske Nævn 2019-20 UPN Alm.del - Bilag 92 Offentligt Bilag 1: Rapporter forelagt FN’s Menneskerettighedsråd i perioden 2015-2019 (HRC31-42) Rapporter forelagt i 2019 (HRC40-42) Rapportnummer Titel A/HRC/42/1 Agenda and annotations A/HRC/42/1/Corr.1 Corrigendum A/HRC/42/2 Report of the Human Rights Council on its forty-second session A/HRC/42/3 Report of the Working Group on the Universal Periodic Review - Norway A/HRC/42/3/Add.1 Addendum A/HRC/42/3/Add.1/Annex.1 Annex A/HRC/42/4 Report of the Working Group on the Universal Periodic Review - Albania A/HRC/42/4/Add.1 Addendum A/HRC/42/5 Report of the Working Group on the Universal Periodic Review - Democratic Republic of the Congo A/HRC/42/5/Add.1 Addendum A/HRC/42/6 Report of the Working Group on the Universal Periodic Review - Côte d'Ivoire A/HRC/42/6/Add.1 Addendum A/HRC/42/7 Report of the Working Group on the Universal Periodic Review - Portugal A/HRC/42/7/Add.1 Addendum - Views on conclusions and/or recommendations, voluntary commitments and replies presented by Portugal A/HRC/42/8 Report of the Working Group on the Universal Periodic Review - Bhutan A/HRC/42/8/Add.1 Addendum A/HRC/42/9 Report of the Working Group on the Universal Periodic Review - Dominica A/HRC/42/9/Add.1 Addendum A/HRC/42/10 Report of the Working Group on the Universal Periodic Review - Democratic People's republic of Korea A/HRC/42/10/Add.1 Addendum A/HRC/42/11 Report of the Working Group on the Universal Periodic Review - Brunei Darussalam A/HRC/42/11/Add.1 Addendum A/HRC/42/12 Report of the Working -

United Nations Special Procedures
Office of the United Nations High Commissioner for Human Rights | www.ohchr.org United Nations Special Procedures FFAACCTTSS AANNDD FFIIGGUURREESS 22001111 Communications · Country visits · Coordination and joint activities Reports · Public statements and news releases· Thematic events Published by: Office of the United Nations High Commissioner for Human Rights Geneva, May 2012 Pictures on front cover: Maya Sahli, Member of the Working Group on people of African descent , briefs the Human Rights Council at its eighteenth session. A wide view of the Human Rights Council on the opening day of its eighteenth session. Olivier de Schutter, Special Rapporteur on the Right to Food, briefs the Human Rights Council at its sixteenth session. Maria Magdalena Sepulveda, Special Rapporteur on extreme poverty and human rights during a mission to Timor Leste in November 2011. Michel Forst, Independent Expert on the situation of human rights in Haiti, during a visit to the country. TABLE OF CONTENTS Introduction …………………………………. 1 List of mandates and mandate-holders …... 2 Developments in 2011……………………… 5 Communications ………………………….....9 Country visits …………………………….....12 Positive developments……………………...14 Reports ……………………………………....16 News releases ……………………………….24 The Special Procedures Facts and Figures 2011 provides a general overview of the main activities of the Special Procedures mandates of the United Nations Human Rights Council in 2011. This tool is produced by the Special Procedures Branch of the Human Rights Council and Special Procedures Division of the OHCHR. For more information about Special Procedures, please visit http://www2.ohchr.org/english/bodies/chr/special/index.htm. Information about the work of OHCHR and the support extended to Special Procedures will be available in the forthcoming OHCHR Report 2011. -

Protest and Human Rights Standards on the Rights Involved in Social Protest and the Obligations to Guide the Response of the State
OEA/SER.L/V/II CIDH/RELE/INF.22/19 September 2019 Original: Spanish Protest and Human Rights Standards on the rights involved in social protest and the obligations to guide the response of the State Office of the Special Rapporteur for Freedom of Expression of the Inter-American Commission on Human Rights Edison Lanza Special Rapporteur for Freedom of Expression 2019 OAS CATALOGING-IN-PUBLICATION DATA Inter-American Commission on Human Rights. Office of the Special Rapporteur for Freedom of Expression. Protesta y derechos humanos / Relatoría Especial para la Libertad de Expresión de la Comisión Interamericana de Derechos Humanos. v. ; cm. (OAS. Documentos oficiales ; OEA/Ser.L/V/II) ISBN 978-0-8270-6938-1 1. Protest movements--America. 2. Human rights--America. I. Lanza, Edison. II. Title. III. Series. OEA/Ser.L/V/II CIDH/RELE/INF.22/19 This report was supported, in part, through a grant from the open society foundations. INTER-AMERICAN COMMISSION ON HUMAN RIGHTS Members Margarette May Macaulay Esmeralda Arosemena de Troitiño Francisco José Eguiguren Praeli Luis Ernesto Vargas Silva Joel Hernández García Antonia Urrejola Flávia Piovesan Executive Secretary Paulo Abrão Assistant Executive Secretary for Monitoring, Promotion and Technical Cooperation Maria Claudia Pulido Chief of Staff of the Executive Secretary of the IACHR Marisol Blanchard Vera TABLE OF CONTENTS CHAPTER I GUIDING PRINCIPLES .................................................................................................................................................... -

UN Special Procedures System Is “Designed to Be Ineffective”
ISSN 1806-6445 v. 11 • n. 20 • Jun./Dec. 2014 COMMEMORATIVE ISSUE HUMAN RIGHTS IN MOTION 20 EDITORIAL BOARD ADVISORY BOARD Christof Heyns University of Pretoria (South Africa) Alejandro M. Garro Columbia University (United Emilio García Méndez University of Buenos Aires (Argentina) States) Fifi Benaboud North-South Centre of the Council of Europe (Portugal) Fiona Macaulay Bradford University (United Kingdom) Bernardo Sorj Federal University of Rio de Janeiro / Flavia Piovesan Pontifi cal Catholic University of Edelstein Center (Brazil) São Paulo (Brazil) Bertrand Badie Sciences-Po (France) J. Paul Martin Columbia University (United States) Kwame Karikari University of Ghana (Ghana) Cosmas Gitta UNDP (United States) Mustapha Kamel Al-Sayyid Cairo University (Egypt) Roberto Garretón Former-UN Offi cer of the High Commissioner for Daniel Mato CONICET / National University of Tres Human Rights (Chile) de Febrero (Argentina) Upendra Baxi University of Warwick (United Kingdom) Daniela Ikawa International Network on Economic, EDITORS Social and Cultural Rights / Columbia University Pedro Paulo Poppovic (United States) Oscar Vilhena Vieira Ellen Chapnick Columbia University (United States) EXECUTIVE EDITORS Maria Brant – Executive editor Ernesto Garzon Valdes University of Mainz Thiago Amparo – Guest editor (Germany) Luz González – Assistant executive editor Fateh Azzam Arab Human Rights fund (Lebanon) EXECUTIVE BOARD Albertina de Oliveira Costa Guy Haarscher Université Libre de Bruxelles Ana Cernov (Belgium) Conrado Hubner Mendes Glenda Mezarobba -
Directory of Special Procedures Mandate
2013 OCTOBER DIRECTORY OF SPECIAL PROCEDURES MANDATE HOLDERS Special Rapporteur on adequate housing as a Working Group on arbitrary detention component of the right to an adequate standard of living Mr. Vladimir Tochilovsky Ms. Raquel Rolnik Russian, English English, Spanish [email protected] [email protected] Working Group on the issue of human rights and Working Group on people of African descent transnational corporations and other business Ms. Monorama Biswas enterprises English Mr. Michael K. Addo [email protected] English [email protected] Working Group on people of African descent Ms. Mireille Fanon-Mendes-France Working Group on the issue of human rights and English, French transnational corporations and other business [email protected] enterprises Ms. Alexandra Guáqueta English, Spanish Working Group on people of African descent [email protected] Ms. Mirjana Najcevska English [email protected] Working Group on the issue of human rights and transnational corporations and other business enterprises Working Group on people of African descent Ms. Margaret Jungk Ms. Maya Sahli English French, Arabic [email protected] [email protected] Working Group on people of African descent Working Group on the issue of human rights and transnational corporations and other business Ms. Verene Shepherd enterprises English Mr. Puvan J. Selvanathan [email protected] English [email protected] Working Group on arbitrary detention Mr. Mads Andenas English, French Working Group on the issue of human rights and transnational corporations and other business [email protected] enterprises Mr. Pavel Sulyandziga Russian Working Group on arbitrary detention [email protected] Mr. Roberto Garretón French, Spanish [email protected] Special Rapporteur on the situation of human rights in Belarus Working Group on arbitrary detention Mr.