Algorithms for Finite Rings Iuliana Ciocanea Teodorescu
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Artinian Rings Having a Nilpotent Group of Units
JOURNAL OF ALGEBRA 121, 253-262 (1989) Artinian Rings Having a Nilpotent Group of Units GHIOCEL GROZA Department of Mathematics, Civil Engineering Institute, Lacul Tei 124, Sec. 2, R-72307, Bucharest, Romania Communicated by Walter Feit Received July 1, 1983 Throughout this paper the symbol R will be used to denote an associative ring with a multiplicative identity. R,[R”] denotes the subring of R which is generated over R, by R”, where R, is the prime subring of R and R” is the group of units of R. We use J(R) to denote the Jacobson radical of R. In Section 1 we prove that if R is a finite ring and at most one simple component of the semi-simple ring R/J(R) is a field of order 2, then R” is a nilpotent group iff R is a direct sum of two-sided ideals that are homomorphic images of group algebras of type SP, where S is a particular commutative finite ring, P is a finite p-group, and p is a prime number. In Section 2 we study the artinian rings R (i.e., rings with minimum con- dition) with RO a finite ring, R finitely generated over its center and so that every block of R is as in Lemma 1.1. We note that every finite-dimensional algebra over a field F of characteristic p > 0, so that F is not the finite field of order 2 is of this type. We prove that R is of this type and R” is a nilpotent group iff R is a direct sum of two-sided ideals that are particular homomorphic images of crossed products. -

Representations of Finite Rings
Pacific Journal of Mathematics REPRESENTATIONS OF FINITE RINGS ROBERT S. WILSON Vol. 53, No. 2 April 1974 PACIFIC JOURNAL OF MATHEMATICS Vol. 53, No. 2, 1974 REPRESENTATIONS OF FINITE RINGS ROBERT S. WILSON In this paper we extend the concept of the Szele repre- sentation of finite rings from the case where the coefficient ring is a cyclic ring* to the case where it is a Galois ring. We then characterize completely primary and nilpotent finite rings as those rings whose Szele representations satisfy certain conditions. 1* Preliminaries* We first note that any finite ring is a direct sum of rings of prime power order. This follows from noticing that when one decomposes the additive group of a finite ring into its pime power components, the component subgroups are, in fact, ideals. So without loss of generality, up to direct sum formation, one needs only to consider rings of prime power order. For the remainder of this paper p will denote an arbitrary, fixed prime and all rings will be of order pn for some positive integer n. Of the two classes of rings that will be studied in this paper, completely primary finite rings are always of prime power order, so for the completely primary case, there is no loss of generality at all. However, nilpotent finite rings do not need to have prime power order, but we need only classify finite nilpotent rings of prime power order, the general case following from direct sum formation. If B is finite ring (of order pn) then the characteristic of B will be pk for some positive integer k. -
![The Projective Line Over the Finite Quotient Ring GF(2)[X]/⟨X3 − X⟩ and Quantum Entanglement I](https://docslib.b-cdn.net/cover/8602/the-projective-line-over-the-finite-quotient-ring-gf-2-x-x3-x-and-quantum-entanglement-i-318602.webp)
The Projective Line Over the Finite Quotient Ring GF(2)[X]/⟨X3 − X⟩ and Quantum Entanglement I
The Projective Line Over the Finite Quotient Ring GF(2)[x]/hx3 − xi and Quantum Entanglement I. Theoretical Background Metod Saniga, Michel Planat To cite this version: Metod Saniga, Michel Planat. The Projective Line Over the Finite Quotient Ring GF(2)[x]/hx3 − xi and Quantum Entanglement I. Theoretical Background. 2006. hal-00020182v1 HAL Id: hal-00020182 https://hal.archives-ouvertes.fr/hal-00020182v1 Preprint submitted on 7 Mar 2006 (v1), last revised 6 Jun 2006 (v2) HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. The Projective Line Over the Finite Quotient Ring GF(2)[x]/hx3 − xi and Quantum Entanglement I. Theoretical Background Metod Saniga† and Michel Planat‡ †Astronomical Institute, Slovak Academy of Sciences SK-05960 Tatransk´aLomnica, Slovak Republic ([email protected]) and ‡Institut FEMTO-ST, CNRS, D´epartement LPMO, 32 Avenue de l’Observatoire F-25044 Besan¸con, France ([email protected]) Abstract 3 The paper deals with the projective line over the finite factor ring R♣ ≡ GF(2)[x]/hx −xi. The line is endowed with 18 points, spanning the neighbourhoods of three pairwise distant points. As R♣ is not a local ring, the neighbour (or parallel) relation is not an equivalence relation so that the sets of neighbour points to two distant points overlap. -

Math 250A: Groups, Rings, and Fields. H. W. Lenstra Jr. 1. Prerequisites
Math 250A: Groups, rings, and fields. H. W. Lenstra jr. 1. Prerequisites This section consists of an enumeration of terms from elementary set theory and algebra. You are supposed to be familiar with their definitions and basic properties. Set theory. Sets, subsets, the empty set , operations on sets (union, intersection, ; product), maps, composition of maps, injective maps, surjective maps, bijective maps, the identity map 1X of a set X, inverses of maps. Relations, equivalence relations, equivalence classes, partial and total orderings, the cardinality #X of a set X. The principle of math- ematical induction. Zorn's lemma will be assumed in a number of exercises. Later in the course the terminology and a few basic results from point set topology may come in useful. Group theory. Groups, multiplicative and additive notation, the unit element 1 (or the zero element 0), abelian groups, cyclic groups, the order of a group or of an element, Fermat's little theorem, products of groups, subgroups, generators for subgroups, left cosets aH, right cosets, the coset spaces G=H and H G, the index (G : H), the theorem of n Lagrange, group homomorphisms, isomorphisms, automorphisms, normal subgroups, the factor group G=N and the canonical map G G=N, homomorphism theorems, the Jordan- ! H¨older theorem (see Exercise 1.4), the commutator subgroup [G; G], the center Z(G) (see Exercise 1.12), the group Aut G of automorphisms of G, inner automorphisms. Examples of groups: the group Sym X of permutations of a set X, the symmetric group S = Sym 1; 2; : : : ; n , cycles of permutations, even and odd permutations, the alternating n f g group A , the dihedral group D = (1 2 : : : n); (1 n 1)(2 n 2) : : : , the Klein four group n n h − − i V , the quaternion group Q = 1; i; j; ij (with ii = jj = 1, ji = ij) of order 4 8 { g − − 8, additive groups of rings, the group Gl(n; R) of invertible n n-matrices over a ring R. -
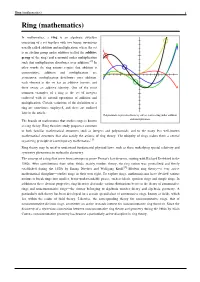
Ring (Mathematics) 1 Ring (Mathematics)
Ring (mathematics) 1 Ring (mathematics) In mathematics, a ring is an algebraic structure consisting of a set together with two binary operations usually called addition and multiplication, where the set is an abelian group under addition (called the additive group of the ring) and a monoid under multiplication such that multiplication distributes over addition.a[›] In other words the ring axioms require that addition is commutative, addition and multiplication are associative, multiplication distributes over addition, each element in the set has an additive inverse, and there exists an additive identity. One of the most common examples of a ring is the set of integers endowed with its natural operations of addition and multiplication. Certain variations of the definition of a ring are sometimes employed, and these are outlined later in the article. Polynomials, represented here by curves, form a ring under addition The branch of mathematics that studies rings is known and multiplication. as ring theory. Ring theorists study properties common to both familiar mathematical structures such as integers and polynomials, and to the many less well-known mathematical structures that also satisfy the axioms of ring theory. The ubiquity of rings makes them a central organizing principle of contemporary mathematics.[1] Ring theory may be used to understand fundamental physical laws, such as those underlying special relativity and symmetry phenomena in molecular chemistry. The concept of a ring first arose from attempts to prove Fermat's last theorem, starting with Richard Dedekind in the 1880s. After contributions from other fields, mainly number theory, the ring notion was generalized and firmly established during the 1920s by Emmy Noether and Wolfgang Krull.[2] Modern ring theory—a very active mathematical discipline—studies rings in their own right. -

Acceleration of Finite Field Arithmetic with an Application to Reverse Engineering Genetic Networks
ACCELERATION OF FINITE FIELD ARITHMETIC WITH AN APPLICATION TO REVERSE ENGINEERING GENETIC NETWORKS by Edgar Ferrer Moreno A thesis submitted in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY in COMPUTING AND INFORMATION SCIENCES AND ENGINEERING UNIVERSITY OF PUERTO RICO MAYAGÜEZ CAMPUS 2008 Approved by: ________________________________ __________________ Omar Colón, PhD Date Member, Graduate Committee ________________________________ __________________ Oscar Moreno, PhD Date Member, Graduate Committee ________________________________ __________________ Nayda Santiago, PhD Date Member, Graduate Committee ________________________________ __________________ Dorothy Bollman, PhD Date President, Graduate Committee ________________________________ __________________ Edusmildo Orozco, PhD Date Representative of Graduate Studies ________________________________ __________________ Néstor Rodríguez, PhD Date Chairperson of the Department Abstract Finite field arithmetic plays an important role in a wide range of applications. This research is originally motivated by an application of computational biology where genetic networks are modeled by means of finite fields. Nonetheless, this work has application in various research fields including digital signal processing, error correct- ing codes, Reed-Solomon encoders/decoders, elliptic curve cryptosystems, or compu- tational and algorithmic aspects of commutative algebra. We present a set of efficient algorithms for finite field arithmetic over GF (2m), which are implemented -

Part IB — Groups, Rings and Modules
Part IB | Groups, Rings and Modules Based on lectures by O. Randal-Williams Notes taken by Dexter Chua Lent 2016 These notes are not endorsed by the lecturers, and I have modified them (often significantly) after lectures. They are nowhere near accurate representations of what was actually lectured, and in particular, all errors are almost surely mine. Groups Basic concepts of group theory recalled from Part IA Groups. Normal subgroups, quotient groups and isomorphism theorems. Permutation groups. Groups acting on sets, permutation representations. Conjugacy classes, centralizers and normalizers. The centre of a group. Elementary properties of finite p-groups. Examples of finite linear groups and groups arising from geometry. Simplicity of An. Sylow subgroups and Sylow theorems. Applications, groups of small order. [8] Rings Definition and examples of rings (commutative, with 1). Ideals, homomorphisms, quotient rings, isomorphism theorems. Prime and maximal ideals. Fields. The characteristic of a field. Field of fractions of an integral domain. Factorization in rings; units, primes and irreducibles. Unique factorization in principal ideal domains, and in polynomial rings. Gauss' Lemma and Eisenstein's irreducibility criterion. Rings Z[α] of algebraic integers as subsets of C and quotients of Z[x]. Examples of Euclidean domains and uniqueness and non-uniqueness of factorization. Factorization in the ring of Gaussian integers; representation of integers as sums of two squares. Ideals in polynomial rings. Hilbert basis theorem. [10] Modules Definitions, examples of vector spaces, abelian groups and vector spaces with an endomorphism. Sub-modules, homomorphisms, quotient modules and direct sums. Equivalence of matrices, canonical form. Structure of finitely generated modules over Euclidean domains, applications to abelian groups and Jordan normal form. -

Clean Rings & Clean Group Rings
CLEAN RINGS & CLEAN GROUP RINGS Nicholas A. Immormino A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY August 2013 Committee: Warren Wm. McGovern, Advisor Rieuwert J. Blok, Advisor Sheila J. Roberts, Graduate Faculty Representative Mihai D. Staic ii ABSTRACT Warren Wm. McGovern, Advisor Rieuwert J. Blok, Advisor A ring is said to be clean if each element in the ring can be written as the sum of a unit and an idempotent of the ring. More generally, an element in a ring is said to be clean if it can be written as the sum of a unit and an idempotent of the ring. The notion of a clean ring was introduced by Nicholson in his 1977 study of lifting idempotents and exchange rings, and these rings have since been studied by many different authors. In our study of clean rings, we classify the rings that consist entirely of units, idempotents, and quasiregular elements. It is well known that the units, idempotents, and quasiregular elements of any ring are clean. Therefore any ring that consists entirely of these types of elements is clean. We prove that a ring consists entirely of units, idempotents, and quasiregular elements if and only if it is a boolean ring, a local ring, isomorphic to the direct product of two division rings, isomorphic to the full matrix ring M2(D) for some division ring D, or isomorphic to the ring of a Morita context with zero pairings where both of the underlying rings are division rings. -

On Distinguishing Local Finite Rings from Finite Rings Only by Counting Elements and Zero Divisors Marcos J
EUROPEAN JOURNAL OF PURE AND APPLIED MATHEMATICS Vol. 7, No. 1, 2014, 109-113 ISSN 1307-5543 – www.ejpam.com On Distinguishing Local Finite Rings from Finite Rings Only by Counting Elements and Zero Divisors Marcos J. González Departamento de Matemáticas, Universidad Simón Bolívar, Caracas 1080-A, Venezuela Abstract. The purpose of this short communication is to prove the following: Let R be a finite associa- tive ring with unit. Then R is local if and only if jRj = pn and jZ(R)j = pm for some prime number p and integers 1 m < n. For the commutative case, this have been recently discovered by Behboodi and Beyranvand≤ [1, Theorem 3]. We will also present yet another proof for the commutative case. 2010 Mathematics Subject Classifications: 16B99, 13A99, 68R10 Key Words and Phrases: Finite ring, Zero-divisor, Local rings 1. Introduction The purpose of this paper is to prove the following: Theorem 1. Let R be a finite associative ring with unit. Then R is local if and only if jRj = pm and jZ(R)j = pn for some prime number p and integers 1 n < m. ≤ This allows us to recognize local rings out of finite rings only by counting the number of elements in the ring and the number of zero divisors. This result is inspired by the corre- sponding result Behboodi and Beyranvand [1, Theorem 3, pp. 306–307] where R is assumed to be commutative. More precisely, they proved the following: Theorem 2. Let R be a finite commutative ring with unit. Then R is local if and only if jRj = pm and jZ(R)j = pn for some prime number p and integers 1 n < m. -

Geometries Over Finite Rings
Innovations in Incidence Geometry Volume 15 (2017), Pages 123–143 ISSN 1781-6475 50 years of Finite Geometry, the “Geometries over finite rings” part Dedicated to Prof. J.A. Thas on the occasion of his 70th birthday Dirk Keppens Abstract Whereas for a substantial part, “Finite Geometry” during the past 50 years has focussed on geometries over finite fields, geometries over finite rings that are not division rings have got less attention. Nevertheless, sev- eral important classes of finite rings give rise to interesting geometries. In this paper we bring together some results, scattered over the litera- ture, concerning finite rings and plane projective geometry over such rings. The paper does not contain new material, but by collecting information in one place, we hope to stimulate further research in this area for at least another 50 years of Finite Geometry. Keywords: ring geometry, finite geometry, finite ring, projective plane MSC 2010: 51C05,51E26,13M05,16P10,16Y30,16Y60 1 Introduction Geometries over rings that are not division rings have been studied for a long time. The first systematic study was done by Dan Barbilian [11], besides a mathematician also one of the greatest Romanian poets (with pseudonym Ion Barbu). He introduced plane projective geometries over a class of associative rings with unit, called Z-rings (abbreviation for Zweiseitig singulare¨ Ringe) which today are also known as Dedekind-finite rings. These are rings with the property that ab = 1 implies ba = 1 and they include of course all commutative rings but also all finite rings (even non-commutative). Wilhelm Klingenberg introduced in [52] projective planes and 3-spaces over local rings. -

ON the STRUCTURE of FINITE RINGS by Robert S
COMPOSITIO MATHEMATICA ROBERT S. WILSON On the structure of finite rings Compositio Mathematica, tome 26, no 1 (1973), p. 79-93 <http://www.numdam.org/item?id=CM_1973__26_1_79_0> © Foundation Compositio Mathematica, 1973, tous droits réservés. L’accès aux archives de la revue « Compositio Mathematica » (http: //http://www.compositio.nl/) implique l’accord avec les conditions géné- rales d’utilisation (http://www.numdam.org/conditions). Toute utilisation commerciale ou impression systématique est constitutive d’une infrac- tion pénale. Toute copie ou impression de ce fichier doit contenir la présente mention de copyright. Article numérisé dans le cadre du programme Numérisation de documents anciens mathématiques http://www.numdam.org/ COMPOSITIO MATHEMATICA, Vol. 26, Fasc. 1, 1973, pag. 79-93 Noordhoff International Publishing Printed in the Netherlands ON THE STRUCTURE OF FINITE RINGS by Robert S. Wilson * Introduction In this paper we shall concern ourselves primarily with completely primary finite rings and shall obtain results about other types of rings by means of the Peirce decomposition and other methods. Recall that an Artinian ring R with radical J is called primary if R/J is simple and is called completely primary if R/J is a division ring The deepest study into the nature of completely primary finite rings appears to have been made by Raghavendran [5]. We first state some of his major results. In what follows Z will denote the rational integers, and if S is a finite set, #(S) will denote the number of elements in S. THEOREM A. Let R be a completely primary finite ring with radical J and let R/J ~ GF(pr). -

Contributions to the Taxonomy of Rings
Contributions to the Taxonomy of Rings A dissertation presented to the faculty of the College of Arts and Sciences of Ohio University In partial fulfillment of the requirements for the degree Doctor of Philosophy Henry Chimal-Dzul April 2021 © 2021 Henry Chimal-Dzul. All Rights Reserved. 2 This dissertation titled Contributions to the Taxonomy of Rings by HENRY CHIMAL-DZUL has been approved for the Department of Mathematics and the College of Arts and Sciences by Sergio R. L´opez-Permouth Professor of Mathematics Florenz Plassmann Dean, College of Arts and Sciences 3 Abstract CHIMAL-DZUL, HENRY, Ph.D., April 2021, Mathematics Contributions to the Taxonomy of Rings (139 pp.) Director of Dissertation: Sergio R. L´opez-Permouth The present work aims to contribute to the taxonomy of various classes of non-commutative rings. These include the classes of reversible, reflexive, semicommutative, 2-primal, NI, abelian, Dedekind finite, Armendariz, and McCoy rings. In addition, two new families of rings are introduced, namely right real McCoy and polynomial semicommutative. The first contribution concerns the hierarchy and interconnections of reflexive, abelian, and semicommutative rings in the setting of finite rings. It is shown that a minimal reflexive abelian non-semicommutative ring has order 256 and that the group algebra F2D8 is an example of such a ring. This answers an open question in a paper on a taxonomy of finite 2-primal rings. The second set of contributions includes characterizations of reflexive, 2-primal, weakly 2-primal and NI rings in the setting of Morita context rings. The results on Morita context rings which are reflexive are shown to generalize known characterizations of prime and semiprime Morita context rings.