MICROCOMP Output File
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Compliance & Legal Sections Annual Virtual Meeting 2020
Compliance & Legal Sections Annual Virtual Meeting 2020 Registration List Name Title Company City/State Kristin M. Abbott Director, Compliance & Regulatory Affairs ACLI Washington, DC Amber L. Adams VP, Chief Legal Counsel, Chief Compliance American-Amicable Life Insurance Company of Waco, TX Officer & Asst Corporate Secretary Texas Dwain A. Akins Senior Vice President, Chief Corporate American National Insurance Company Galveston, TX Compliance Officer Joseph Arite Director, Legislative Relations Guarantee Trust Life Insurance Company Glenview, IL Kate Austin Senior Counsel Allianz Minneapolis, MN Randi J. Bader Vice President & Associate General New York Life New York, NY Counsel Lauren A. Barbaruolo Corporate Counsel & Director, Compliance Oxford Life Insurance Company Phoenix, AZ Chad Batterson Vice President, Compliance Athene Annuity and Life Company West Des Moines, IA Erin Baum Consultant, Ethics & Compliance CUNA Mutual Group Madison, WI John Baumgardner Supervisor, Compliance Team Standard Insurance Company Portland, OR Simon Berry Senior Counsel Great American Life Insurance Company Cincinnati, OH Mona Bhalla Deputy Superintendent Life Insurance New York State Department of Financial Services New York, NY Division Laura Blahosky Compliance Counsel, Compliance & Federated Life Insurance Company Owatonna, MN Government Relations Lester L. Bohnert General Counsel Modern Woodmen of America Rock Island, IL Timothy H. Bolden Vice President, Chief Compliance Officer American Fidelity Assurance Company Oklahoma City, OK Patricia Diane Boyette Vice President, Chief Compliance Officer Southern Farm Bureau Life Jackson, MS Corinne L. Brand Counsel State Farm Bloomington, IL 12/14/2020 American Council of Life Insurers acli.com Page 1 Compliance & Legal Sections Annual Virtual Meeting 2020 Registration List Name Title Company City/State JoAnne Breese-Jaeck Chief Privacy Officer Northwestern Mutual Milwaukee, WI Kermitt J. -
STATEMENT of VOTE, Summary Pages Xxii
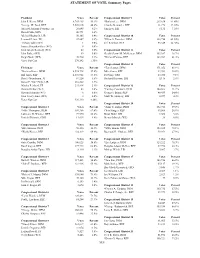
STATEMENT OF VOTE, Summary Pages President Votes Percent Congressional District 9 Votes Percent John F. Kerry, DEM 6,745,485 54.4% *Barbara Lee, DEM 215,630 84.60% *George W. Bush, REP 5,509,826 44.4% Claudia Bermudez, REP 31,278 12.30% Michael Anthony Peroutka, AI 26,645 0.2% Jim Eyer, LIB 8,131 3.10% David Cobb, GRN 40,771 0.3% Michael Badnarik, LIB 50,165 0.4% Congressional District 10 Votes Percent Leonard Peltier, PF 27,607 0.2% *Ellen O. Tauscher, DEM 182,750 65.80% Anthony Jabin (W/I) 1 0.0% Jeff Ketelson, REP 95,349 34.20% James Alexander-Pace (W/I) 8 0.0% John Joseph Kennedy (W/I) 82 0.0% Congressional District 11 Votes Percent John Parker (W/I) 49 0.0% Gerald (Jerry) M. McNerney, DEM 103,587 38.7% Ralph Nader (W/I) 20,714 0.1% *Richard Pombo, REP 163,582 61.3% Votes Not Cast 170,142 1.35% Congressional District 12 Votes Percent US Senate Votes Percent *Tom Lantos, DEM 171,852 68.1% *Barbara Boxer, DEM 6,955,728 57.8% Mike Garza, REP 52,593 20.8% Bill Jones, REP 4,555,922 37.8% Pat Gray, GRN 23,038 9.1% Don J. Grundmann, AI 81,224 0.6% Harland Harrison, LIB 5,116 2.0% James P. "Jim" Gray, LIB 216,522 1.7% Marsha Feinland, PF 243,846 2.1% Congressional District 13 Votes Percent Dennis Richter (W/I) 43 0.0% *Fortney Pete Stark, DEM 144,605 71.7% Howard Johnson (W/I) 6 0.0% George I. -

MICROCOMP Output File
FINAL EDITION OFFICIAL LIST OF MEMBERS OF THE HOUSE OF REPRESENTATIVES of the UNITED STATES AND THEIR PLACES OF RESIDENCE ONE HUNDRED SIXTH CONGRESS . JANUARY 4, 2001 Compiled by JEFF TRANDAHL, Clerk of the House of Representatives http://clerk.house.gov Republicans in roman (222); Democrats in italic (208); Independents in SMALL CAPS (2); vacancies (3) 1st VA, 4th MN, 32d CA; total 435. The number preceding the name is the Member’s district. ALABAMA 1 Sonny Callahan ........................................... Mobile 2 Terry Everett ............................................... Enterprise 3 Bob Riley ..................................................... Ashland 4 Robert B. Aderholt ...................................... Haleyville 5 Robert E. (Bud) Cramer, Jr. ........................ Huntsville 6 Spencer Bachus ........................................... Vestavia Hills 7 Earl F. Hilliard ........................................... Birmingham ALASKA AT LARGE Don Young ................................................... Fort Yukon ARIZONA 1 Matt Salmon ................................................ Mesa 2 Ed Pastor ..................................................... Phoenix 3 Bob Stump ................................................... Tolleson 4 John B. Shadegg .......................................... Phoenix 5 Jim Kolbe ..................................................... Tucson 6 J. D. Hayworth ............................................ Scottsdale ARKANSAS 1 Marion Berry ............................................... Gillett -

Remarks at the Simon Wiesenthal Center Dinner in Los Angeles, California June 16, 1991
Administration of George Bush, 1991 / June 16 all. But most of all, may God bless the tion KNBC; Porntip Narkhirunkanok, 1989 United States of America. Thank you very Miss Universe; Elizabeth Szu, Inder Singh, much. Thank you. and Ky Ngo, coordinators for the event; John Tsu, senior adviser for the event; Henry Note: The President spoke at 12:38 p.m. at Tang, an education and sports leader in the Mile Square Park. In his remarks, he re- community; Leo Esaki, 1973 Nobel Prize ferred to Senator John Seymour; Representa- tives Dana Rohrabacher, Robert K. Dornan, winner for physics; President Saddam Hus- C. Christopher Cox, Norman Y. Mineta, sein of Iraq; Patricia F. Saiki, Administrator David Dreier, and Nancy Pelosi; Delegate of the Small Business Administration; Julia to Congress Eni F.H. Faleomavaega; Deputy Chang Bloch, U.S. Ambassador to Nepal; Secretary of Transportation Elaine L. Chao; and Sichan Siv, Deputy Assistant to the Frank Kwan, a producer for television sta- President for Public Liaison. Remarks at the Simon Wiesenthal Center Dinner in Los Angeles, California June 16, 1991 Thank you all very much. Let me first I also want to pay a special tribute to thank my dear friend, Jerry Weintraub, for Gayle Wilson. Sorry Pete couldn’t be with that generous introduction. And thanks to us tonight; he’s up wrestling with the budg- Wilson Phillips for the anthem so beau- et problems. And to Senator John Seymour, tifully done. My thanks to Tony Danza for our wonderful new Senator in the United being here. [Laughter] Had to go out and States Senate; to David Dreier, who’s with get a haircut so we would recognize him. -

Binding Corporate Rules for Employees
Employee Privacy Rules version April 2011 SHELL EMPLOYEE PRIVACY RULES Contents 1 Article 1 – Scope and Applicable Law ................................................ 2 2 Article 2 – Purposes for Processing Employee Data ............................... 3 3 Article 3 – Processing Sensitive Data ................................................ 5 4 Article 4 – Additional requirements for Processing Data of Dependants ....... 5 Article 5 – Employee Consent ......................................................... 7 6 Article 6 – Quantity and Quality of Data ............................................ 9 7 Article 7 – Information Requirements .............................................. 10 8 Article 8 – Employee Rights of Access and Rectification .......................... 9 Article 9 – Security and Confidentiality Requirements ......................... 12 10 Article 10 – Automated Decision Making ........................................... 12 11 Article 11 – Transfer of Employee Data to Third Parties ....................... 13 12 Article 12 – Overriding Interests ..................................................... 15 13 Article 13 – Supervision and Compliance .......................................... 17 14 Article 14 – Complaints procedure .................................................. 17 15 Article 15 – Remedies .................................................................. 18 16 Article 16 – Sanctions for non compliance ......................................... 20 17 Article 17 – Effective Date, Transition Periods and publication -

2020 Proxy Statement
2020 Proxy Statement Dear Fellow Owner: Welcome to Truist! We are inviting you to attend the Annual Meeting of Shareholders of Truist Financial Corporation at 11:00 a.m. (EDT) on Tuesday, April 28, 2020. This year’s meeting will be held at the Belk Theater at the Blumenthal Performing Arts Center, 130 N. Tryon Street, Charlotte, North Carolina 28202. Shareholders as of the record date of February 21, 2020 are invited to attend. Last year, we made banking history by combining two forward-looking and like-minded companies – BB&T and SunTrust – to create Truist, a premier financial institution driven by a strong shared culture to accelerate our relentless pursuit of innovation. Now, we have an incredible opportunity to fulfill the Truist purpose to inspire and build better lives and communities. Our merger of equals created the nation’s sixth largest commercial bank, serving 10 million consumer households and a full range of business clients in many of the nation’s highest growth markets. Truist will chart a new course in our industry as we seamlessly blend a high level of personal touch with cutting-edge technology to build a higher level of trust with our clients. We are truly better together. We wanted to take this opportunity to thank President and Chief Operating Officer William H. Rogers, Jr. (“Bill”) for the extraordinary opportunity he has helped create for our shareholders, teammates and communities. As SunTrust’s CEO, Bill’s vision and leadership was essential to build the foundation for successfully bringing together the two great heritages of BB&T and SunTrust. -

Ensuring Compatibility with Enhanced 911 Emergency Calling Systems: a Progress Report
ENSURING COMPATIBILITY WITH ENHANCED 911 EMERGENCY CALLING SYSTEMS: A PROGRESS REPORT HEARING BEFORE THE SUBCOMMITTEE ON TELECOMMUNICATIONS AND THE INTERNET OF THE COMMITTEE ON ENERGY AND COMMERCE HOUSE OF REPRESENTATIVES ONE HUNDRED SEVENTH CONGRESS FIRST SESSION JUNE 14, 2001 Serial No. 107–31 Printed for the use of the Committee on Energy and Commerce ( Available via the World Wide Web: http://www.access.gpo.gov/congress/house U.S. GOVERNMENT PRINTING OFFICE 73–728PS WASHINGTON : 2001 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: (202) 512–1800 Fax: (202) 512–2250 Mail: Stop SSOP, Washington, DC 20402–0001 VerDate 11-MAY-2000 14:33 Aug 10, 2001 Jkt 000000 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 73728.TXT HCOM2 PsN: HCOM2 VerDate 11-MAY-2000 14:33 Aug 10, 2001 Jkt 000000 PO 00000 Frm 00002 Fmt 5011 Sfmt 5011 73728.TXT HCOM2 PsN: HCOM2 COMMITTEE ON ENERGY AND COMMERCE W.J. ‘‘BILLY’’ TAUZIN, Louisiana, Chairman MICHAEL BILIRAKIS, Florida JOHN D. DINGELL, Michigan JOE BARTON, Texas HENRY A. WAXMAN, California FRED UPTON, Michigan EDWARD J. MARKEY, Massachusetts CLIFF STEARNS, Florida RALPH M. HALL, Texas PAUL E. GILLMOR, Ohio RICK BOUCHER, Virginia JAMES C. GREENWOOD, Pennsylvania EDOLPHUS TOWNS, New York CHRISTOPHER COX, California FRANK PALLONE, Jr., New Jersey NATHAN DEAL, Georgia SHERROD BROWN, Ohio STEVE LARGENT, Oklahoma BART GORDON, Tennessee RICHARD BURR, North Carolina PETER DEUTSCH, Florida ED WHITFIELD, Kentucky BOBBY L. RUSH, Illinois GREG GANSKE, Iowa ANNA G. ESHOO, California CHARLIE NORWOOD, Georgia BART STUPAK, Michigan BARBARA CUBIN, Wyoming ELIOT L. -

Notice of Annual and Special Meeting of Shareholders of Information Services Corporation to Be Held on May 17, 2017 and Management Information Circular
Notice of Annual and Special Meeting of Shareholders of Information Services Corporation to be held on May 17, 2017 and Management Information Circular April 12, 2017 isc.ca TSX:ISV 202106_CF_ISC_MIC_NEW | Black | 10-Apr-1712:27:31 Contents Page Letter to Shareholders 3 Notice of Annual and Special Meeting 4 Management Information Circular 5 About the Meeting 6 Who Can Vote 6 Appointment of Directors by Province of Saskatchewan 7 Principal Owners of Class A Shares 7 How to Vote 7 Electing Our Directors 11 Appointing Our Auditors 20 Approval of Amended and Restated Stock Option Plan 21 Corporate Governance and Board Committees 25 Director Compensation 29 Executive Officers 32 Compensation Discussion and Analysis 34 Employee Agreements, Termination and Change of Control Benefits 47 Securities Authorized for Issuance Under Equity Compensation Plans 48 Additional Information 49 Appendix A – Amended and Restated Stock Option Plan 50 2 ISC®MANAGEMENT INFORMATION CIRCULAR 2017 202106_CF_ISC_MIC_NEW | Black | 10-Apr-1712:27:31 April 12, 2017 Dear Shareholder: We are pleased to invite you to the annual and special meeting of shareholders of Information Services Corporation (“ISC”), which will be held at 9:00 a.m. (Saskatchewan time/MDT) on May 17, 2017, at Innovation Place, 6 Research Drive, Regina, Saskatchewan. The annual and special meeting is an opportunity to consider matters of importance to ISC and shareholders. We look forward to your participation in person or by proxy at the meeting. You are encouraged to read the accompanying Management Information Circular in advance of the meeting, which describes the business to be conducted at the meeting and provides information on ISC’s approach to executive compensation and governance practices. -

Annual Privacy Report
U.S. DEPARTMENT OF JUSTICE ANNUAL PRIVACY REPORT THE CHIEF PRIVACY AND CIVIL LIBERTIES OFFICER AND THE OFFICE OF PRIVACY AND CIVIL LIBERTIES OCTOBER 1, 2016 – SEPTEMBER 30, 2020 1 (MULTI) ANNUAL PRIVACY REPORT MESSAGE FROM THE CHIEF PRIVACY AND CIVIL LIBERTIES OFFICER I am pleased to present the Department of Justice’s (Department or DOJ) Annual Privacy Report, describing the operations and activities of the Chief Privacy and Civil Liberties Officer (CPCLO) and the Office of Privacy and Civil Liberties (OPCL), in accordance with Section 1174 of the Violence Against Women and Department of Justice Reauthorization Act of 2005. This report covers the period from October 1, 2016, through September 30, 2020. The Department’s privacy program is supported by a team of dedicated privacy professionals who strive to build a culture and understanding of privacy within the complex and diverse mission work of the Department. The work of the Department’s privacy team is evident in the care, consideration, and dialogue about privacy that is incorporated in the daily operations of the Department. During this reporting period, there has been an evolving landscape of technological development and advancement in areas such as artificial intelligence, biometrics, complex data flows, and an increase in the number of cyber security events resulting in significant impacts to the privacy of individuals. Thus, the CPCLO and OPCL have developed new policies and guidance to assist the Department with navigating these areas, some of which include the following: -

Christopher Cox Partner, Bingham Mccutchen LLP
Christopher Cox Partner, Bingham McCutchen LLP Chris Cox is a partner at Bingham and a member of the Corporate, Mergers & Acquisitions, and Securities Group, advising global companies on strategic issues, corporate governance, securities regulation and general business matters worldwide. He is also a principal of Bingham Consulting Group, focused on strategic issues involving federal and state governments, homeland security, and multistate litigation. In private practice prior to joining Bingham, Chris was a partner in the international law firm of Latham & Watkins in Los Angeles and Orange County, and a member of the firm’s national management. In 1986 he left Latham to work as a White House counsel to President Ronald Reagan. During a 23-year Washington career, Chris was chairman of the U.S. Securities and Exchange Commission, chairman of the Homeland Security Committee in the U.S. House of Representatives, the fifth- ranking elected leader in the House an a 17-year member of Congress from California. As a member of the House, in addition to his role as chairman of the Committee on Homeland Security, Chris was chairman of the Select Committee on U.S. National Security and a senior member of the Energy and Commerce Committee and the Financial Services Committee. For 10 years he served as chairman of the House Policy Committee. In each of these capacities he was responsible for significant legislation, including the Internet Tax Freedom Act, the Securities Litigation Reform Act and the Support for Eastern European Democracy Act. He earned his Juris Doctor from Harvard Law School, where he was an editor of the Harvard Law Review. -

Federal Government, Pgs. 0103-0126
CHAPTER 3 Federal Government “House Painter” (Missouri State Archives, Putman Collection) 104 OFFICIAL MANUAL Michael Chertoff, Secretary of Homeland Secu- rity; Alphonso Jackson, Secretary of Housing and Urban Development; United States Gale Norton, Secretary of the Interior; Alberto Gonzales, Attorney General; Elaine Chao, Secretary of Labor; Government Condoleezza Rice, Secretary of State; Norman Mineta, Secretary of Transportation; John Snow, Secretary of the Treasury; Executive Branch Jim Nicholson, Secretary of Veterans’ Affairs. The White House In addition to secretaries of the cabinet, the 1600 Pennsylvania Ave., N.W. president maintains a White House staff of advis- Washington, D.C. 20500 ers who serve at his pleasure. Telephone: (202) 456-1414 President Bush’s Executive Officers The president and the vice president of the with Cabinet Rank United States are elected every four years by a majority of votes cast in the electoral college. These Richard B. Cheney, Vice President; votes are cast by delegates from each state who Stephen Johnson, Environmental Protection vote in accordance, traditionally, with the majority Agency; of the state’s voters. States have as many electoral Joshua B. Bolten, Office of Management and college votes as they have congressional delegates. Budget; Missouri has 11 electoral college votes—one for Andrew H. Card Jr., Chief of Staff; each of the nine U.S. Congress districts and two for Rob Portman, U.S. Trade Representative; John Walters, Office of National Drug Control the state’s two seats in the U.S. Senate. Policy. The president is the chief executive of the Unit- ed States, with powers to command the armed Legislative Branch forces, control foreign policy, grant reprieves and The U.S. -

Download the Microsoft Tag and We’Ll Consider Them for the Magazine
Fall 2014 Magazine Giant Creative Strategy Output @ 100% x 10"h Live: 7.375"w 8.25”w x 10.75”h Trim: Bleed: 8.75"w x 11.25"h Colors: 4CP + AD WINTER HB PATIENT PRINT GILPT11284 Speak from the PRINT live/trim_DO NOT heart about your angina “Tell your cardiologist exactly how you’re feeling. Don’t hold anything back.” Donnette, angina patient If you have been limiting your work or your activities because of your chronic angina, be sure to talk about it with your cardiologist. Your cardiologist is listening www.SpeakFromTheHeart.com Tips, information, and more from real angina patients Donnette, Ralph, and Claudia. Claudia, angina patient Speak From the Heart is a trademark, and the Speak From the Heart logo Ralph, angina patient is a registered trademark, of Gilead Sciences, Inc. © 2011 Gilead Sciences, Inc. All rights reserved. UN7951 1/11 D19528_1a_Donette.indd 11.04.2013 A17041x01G_300ucr_RBlk.tif 133 linescreen B19528x01A_3u.tif jn B19528x02A_3u.tif Dedicated to inspiring hope in heart disease patients and their families. Mission: Inspiring hope and improving the quality of life for heart patients and their families through ongoing peer-to-peer support THE MENDED HEARTS, INC. BOARD OF DIRECTORS 2013-2015 President Gus Littlefield Executive Vice President Donnette Smith Vice President Lynn Berringer Treasurer Dale Briggs Mended Little Hearts Vice President Andrea Baer Fall 2014 Regional Directors Central Jana Stewart Mid-Atlantic Gerald Kemp Midwest Cathy Byington Northeast Margaret Elbert Rocky Mountain Randy Gay Southern Fredonia Williams