2001 CERT Advisories
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vmware Fusion 12 Vmware Fusion Pro 12 Using Vmware Fusion
Using VMware Fusion 8 SEP 2020 VMware Fusion 12 VMware Fusion Pro 12 Using VMware Fusion You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents Using VMware Fusion 9 1 Getting Started with Fusion 10 About VMware Fusion 10 About VMware Fusion Pro 11 System Requirements for Fusion 11 Install Fusion 12 Start Fusion 13 How-To Videos 13 Take Advantage of Fusion Online Resources 13 2 Understanding Fusion 15 Virtual Machines and What Fusion Can Do 15 What Is a Virtual Machine? 15 Fusion Capabilities 16 Supported Guest Operating Systems 16 Virtual Hardware Specifications 16 Navigating and Taking Action by Using the Fusion Interface 21 VMware Fusion Toolbar 21 Use the Fusion Toolbar to Access the Virtual-Machine Path 21 Default File Location of a Virtual Machine 22 Change the File Location of a Virtual Machine 22 Perform Actions on Your Virtual Machines from the Virtual Machine Library Window 23 Using the Home Pane to Create a Virtual Machine or Obtain One from Another Source 24 Using the Fusion Applications Menus 25 Using Different Views in the Fusion Interface 29 Resize the Virtual Machine Display to Fit 35 Using Multiple Displays 35 3 Configuring Fusion 37 Setting Fusion Preferences 37 Set General Preferences 37 Select a Keyboard and Mouse Profile 38 Set Key Mappings on the Keyboard and Mouse Preferences Pane 39 Set Mouse Shortcuts on the Keyboard and Mouse Preference Pane 40 Enable or Disable Mac Host Shortcuts on the Keyboard and Mouse Preference Pane 40 Enable Fusion Shortcuts on the Keyboard and Mouse Preference Pane 41 Set Fusion Display Resolution Preferences 41 VMware, Inc. -

090.070-CS Quantum HD Unity Compressor Control Panel
Form 090.070-CS (DEC 2019) COMMUNICATIONS SETUP File: SERVICE MANUAL - Section 90 Replaces: 090.070-CS (JAN 2018) Dist: 3, 3a, 3b, 3c Revised: December 18, 2019 COMMUNICATIONS SETUP FRICK QUANTUM HD UNITY COMPRESSOR CONTROL PANEL Version 10.5x - 11.x, 12.x Check www.FrickCold.com for the latest version of this publication. 090.070-CS (DEC 2019) QUANTUM™ HD UNITY COMPRESSOR CONTROL PANEL Page 2 COMMUNICATIONS SETUP CONTENTS Section 1 - Quantum HD Unity Control System Section 4 - Modbus Protocol Introduction To Quantum™ HD Unity 6 Modbus Protocol 41 Description .................................................................. 6 General Description ....................................................41 How to Use this Manual .......................................... 6 Modbus TCP/IP (Ethernet)...........................................41 The Operating/Home Screen ....................................... 6 Modbus ASCII (Serial Communications) ..................... 43 Ethernet And Networking 7 Modbus RTU (Serial Communications) ....................... 43 Description .................................................................. 7 Serial Port Configuration of the Master ..................... 43 Cabling ........................................................................ 7 Data Packet ............................................................... 43 RJ-45 Connectors ........................................................ 8 The Query ................................................................ 43 The Hub ...................................................................... -

Op E N So U R C E Yea R B O O K 2 0
OPEN SOURCE YEARBOOK 2016 ..... ........ .... ... .. .... .. .. ... .. OPENSOURCE.COM Opensource.com publishes stories about creating, adopting, and sharing open source solutions. Visit Opensource.com to learn more about how the open source way is improving technologies, education, business, government, health, law, entertainment, humanitarian efforts, and more. Submit a story idea: https://opensource.com/story Email us: [email protected] Chat with us in Freenode IRC: #opensource.com . OPEN SOURCE YEARBOOK 2016 . OPENSOURCE.COM 3 ...... ........ .. .. .. ... .... AUTOGRAPHS . ... .. .... .. .. ... .. ........ ...... ........ .. .. .. ... .... AUTOGRAPHS . ... .. .... .. .. ... .. ........ OPENSOURCE.COM...... ........ .. .. .. ... .... ........ WRITE FOR US ..... .. .. .. ... .... 7 big reasons to contribute to Opensource.com: Career benefits: “I probably would not have gotten my most recent job if it had not been for my articles on 1 Opensource.com.” Raise awareness: “The platform and publicity that is available through Opensource.com is extremely 2 valuable.” Grow your network: “I met a lot of interesting people after that, boosted my blog stats immediately, and 3 even got some business offers!” Contribute back to open source communities: “Writing for Opensource.com has allowed me to give 4 back to a community of users and developers from whom I have truly benefited for many years.” Receive free, professional editing services: “The team helps me, through feedback, on improving my 5 writing skills.” We’re loveable: “I love the Opensource.com team. I have known some of them for years and they are 6 good people.” 7 Writing for us is easy: “I couldn't have been more pleased with my writing experience.” Email us to learn more or to share your feedback about writing for us: https://opensource.com/story Visit our Participate page to more about joining in the Opensource.com community: https://opensource.com/participate Find our editorial team, moderators, authors, and readers on Freenode IRC at #opensource.com: https://opensource.com/irc . -

Build Your Own Distro Tired of the Run-Of-The-Mill Stuff on Distrowatch? Why Not Heed Mayank Sharma and Create the Perfect Operating System for You?
Build your own distro Tired of the run-of-the-mill stuff on Distrowatch? Why not heed Mayank Sharma and create the perfect operating system for you? few issues ago, [LXF171, 50 making it your own – by removing apps and Now traditional wisdom says that creating Distros Tested], we looked at drivers that you don’t need and adding the your own Linux system is a rather difficult the best Linux distributions for ones you do. You’ll also probably change the thing to do and shouldn’t be attempted by A all kinds of users. There were factory-fitted artwork that says more about anyone other than Linux veterans. distros that were designed with ease of use the distro vendor than you. We begin the feature with graphical point- in mind, some focused on productivity, Sure that’s one way to go about it. and-click tools. Yes, you read that right. All it while others catered to specialised use You tweak and customise the distro to suit takes is a couple of clicks to craft your very cases, such as security and privacy your requirements. But wouldn’t it be really own flavour of Linux that you can pass to conscious users. But we can guarantee great if you just create your very own, custom friends and family. We’ve got tools that’ll help that there wasn’t a distro designed Linux distribution? you create and distribute customised spins specifically and entirely for you! based on Ubuntu, Fedora and While most Linux users make do OpenSUSE – the three mainstream with one of the mainstream distros out “We’ve got tools that’ll Linux distributions that house there, there’s always something or the help you create and thousands of open source software in other that’s missing. -

The Developer's Guide to Azure
E-book Series The Developer’s Guide to Azure Published May 2019 May The Developer’s 2 2019 Guide to Azure 03 / 40 / 82 / Introduction Chapter 3: Securing Chapter 6: Where your application and how to deploy We’re here to help your Azure services How can Azure help secure 05 / your app? How can Azure deploy your Encryption services? Chapter 1: Getting Azure Security Center Infrastructure as Code started with Azure Logging and monitoring Azure Blueprints Containers in Azure What can Azure do for you? Azure Stack Where to host your 51 / Where to deploy, application and when? Chapter 4: Adding Azure App Service Features Azure Functions intelligence to Azure Logic Apps your application 89 / Azure Batch Containers How can Azure integrate AI Chapter 7: Share your What to use, and when? into your app? code, track work, and ship Making your application Azure Search software more performant Cognitive Services Azure Front Door Azure Bot Service How can Azure help you plan Azure Content Delivery Azure Machine Learning smarter, collaborate better, and ship Network Studio your apps faster? Azure Redis Cache Developer tooling for AI Azure Boards AI and mixed reality Azure Repos Using events and messages in Azure Pipelines 22 / your application Azure Test Plans Azure Artifacts Chapter 2: Connecting your app with data 72 / 98 / What can Azure do for Chapter 5: Connect your your data? business with IoT Chapter 8: Azure in Action Where to store your data Azure Cosmos DB How can Azure connect, secure, Walk-through: Azure portal Azure SQL Database manage, monitor, -

Unity System Release Notes
RELEASE NOTES Dell EMC® Unity™ Family, Dell EMC Unity™ Hybrid, Dell EMC Unity™ All Flash, Dell EMC UnityVSA™ Version 4.5.1.0.5.001 Release Notes 302-002-572 Rev 25 March 2019 These release notes contain supplemental information about this Unity release. Revision history .............................................................................................................. 2 Product description ........................................................................................................ 3 New features (4.5.1.0.5.001) ........................................................................................... 4 New features (4.5.0.0.5.096) ........................................................................................... 4 Fixed Issues .................................................................................................................... 11 Fixed in previous releases ............................................................................................. 11 Known Issues .................................................................................................................. 115 Limitations ....................................................................................................................... 139 Environment and system requirements ....................................................................... 139 Software media, organization, and files ....................................................................... 140 Documentation ............................................................................................................... -

Which Linux Distribution? Difficulty in Choosing?
Which Linux distribution? Difficulty in choosing? Ver 190916 www.ubuntutor.com Twitter @LaoYa14 Contents Page Contents 3 That's enough 4 At first 5 At first little about Linux world 6 Quick start guide for choosing the right distro for beginners 7 Basic information 8 ”Linux tree” 9 Basic information 10 Questions on the web site 11 Distros 12 App store 13 Ubuntu 16.04 and 18.04 14 Ubuntu MATE 15 Lubuntu 16 Ubuntu Budgie 17 Kubuntu 18 Xubuntu 19 Linux Mint 20 Zorin 21 MX Linux 22 Pepermint 23 Deepin 24 Arch Linux 25 Manjaro 26 Ubuntu Kylin 27 Ubuntu Studio 28 Kali Linux 29 Edubuntu 30 Desktop environments for Linux 31 File manager NEMO 32 File manager NAUTILUS 33 Installing Ubuntu live USB (test drive) That's enough When laptop is old and there is Windows XP, what to do? You can install Ubuntu Mate on your old laptop and keep at the same time Windows XP too, if you like XP. Or you can buy a tiny new laptop about 200-300 €/$ and change Windows 10 to Ubuntu. It works! I have made both about three years ago, and I haven't used Windows since then. My own laptop is cheap HP Stream 4 MB/32 GB. When I was studying Ubuntu, I noticed that simple beginner's guide books were not available. So, I did a guide book. I also created a website and named it www.ubuntutor.com. It currently includes Ubuntu 16.04 and 18.04 tutorials. And this guide is third one. -

System Fundamentals
System Fundamentals System and Network Administration Revision 2 (2020/21) Pierre-Philipp Braun <[email protected]> Table of contents ▶ What is a server? ▶ UNIX history ▶ Linux distributions ▶ Terminal tips & tricks ▶ Lab: install Slackware Linux Legal notice & guidelines ▶ Originally designed for 3rd year bachelors at Innopolis University ▶ Modified and enhanced since then ▶ Downgraded lab, much easier now ▶ Open and public knowledge – resources in the appendix ▶ This course is practice and industry oriented What’s a server? What’s the difference between a server and a desktop computer? in terms of packaging?… Rackmount - DL380 gen 10 DL380 gen 10 (w/o cover) ==> Enterprise-class ▶ Fault-tolerant storage disks ▶ Fault-tolerant Power Supply Units (PSU) ▶ Out-of-band management (Lights-out) Fault-tolerant storage disks RAID controller there is… RAID-1 DL380 gen 10 top view Fault-tolerant Power Supply Units (PSU) DL380 gen 10 rear slots DL380 gen 10 rear filled Racks More racks Datacenter cooling A self-made PC is fine too, as long as it is dedicated! ▶ low-cost PC with some AMD Ryzen inside same goes for a 500 RUB SoC ▶ TI BBB ▶ RPi4 ▶ Nvidia Jetson Nano Developer Kit ▶ … By the way, who’s selling more desktop computer CPUs, Intel or AMD?… ==> AMD took over end 2020 // hardwaretimes.com Still loosing the laptop market // hardwaretimes.com Lights-Out Management (LOM) ▶ THIS IS NOT ABOUT SSH ▶ Dedicated daughter board –or– ▶ Hardware integrated in the mobo Low-level console Reach it through ▶ Serial console ▶ Java ▶ HTML5 Remote management engines HP ▶ Management Processor (MP) on HP9000 systems ▶ HPE Integrated Lights-Out 2 (iLO2) IBM ▶ Baseboard Management Controller (BMC) ▶ e.g. -
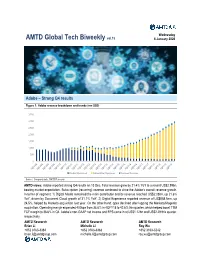
Global Tech Biweekly Vol.15 Jan 8, 2020 Adobe – Strong Q4 Results
Wednesday AMTD Global Tech Biweekly vol.15 8 January 2020 Adobe – Strong Q4 results Figure 1: Adobe revenue breakdown and trends (mn US$) 3,500 3,000 2,500 2,000 1,500 1,000 500 0 Product Revenues Subscription Revenues Services Revenue Source: Company data, AMTD Research AMTD views: Adobe reported strong Q4 results on 13 Dec. Total revenue grew by 21.4% YoY to a record US$2.99bn, beating market expectation. Subscription (recurring) revenue continued to drive the Adobe’s overall revenue growth. In terms of segment: 1) Digital Media remained the main contributor and its revenue reached US$2.08bn, up 21.6% YoY, driven by Document Cloud growth of 31.1% YoY; 2) Digital Experience reported revenue of US$858.5mn, up 24.5%, helped by Marketo acquisition last year. On the other hand, opex declined after lapping the Marketo/Magento acquisition. Operating margin expanded 400bps from 38.6% in 4QFY18 to 42.6% this quarter, which helped boost TTM FCF margin to 36.6% in Q4. Adobe’s non-GAAP net income and EPS came in at US$1.12bn and US$2.29 this quarter, respectively. AMTD Research AMTD Research AMTD Research Brian Li Michelle Li Roy Wu +852 3163-3384 +852 3163-3383 +852 3163-3242 [email protected] [email protected] [email protected] Cloud Figure 2: Adobe’s operating margin (Non-GAAP) and TTM free cash flow (FCF) margin 50% SaaS Operating margin - Non GAAP TTM FCF margin Adobe 40% 30% 20% 10% Source: Company data, AMTD Research Looking ahead, we see strong growth potential of Adobe: 1) Digital Media has accelerated with the help of innovative products. -

Debian, Ubuntu, and 101 Other Derivatives
Debian, Ubuntu, and 101 other derivatives Stefano Zacchiroli Debian Project Leader 20 November 2010 Ubuntu Party — Toulouse, France Stefano Zacchiroli (Debian) Debian, Ubuntu & co. Ubuntu Party, Toulouse 1 / 27 Outline 1 Debian What’s so special about it? 2 Ubuntu Relationship with Debian Debian $ Ubuntu collaboration 3 Free Software The distro ecosystem Stefano Zacchiroli (Debian) Debian, Ubuntu & co. Ubuntu Party, Toulouse 2 / 27 Outline 1 Debian What’s so special about it? 2 Ubuntu Relationship with Debian Debian $ Ubuntu collaboration 3 Free Software The distro ecosystem Stefano Zacchiroli (Debian) Debian, Ubuntu & co. Ubuntu Party, Toulouse 3 / 27 Debian: once upon a time Fellow Linuxers, This is just to announce the imminent completion of a brand-new Linux release, which I’m calling the Debian Linux Release. [. ] Ian A Murdock, 16/08/1993 comp.os.linux.development make GNU/Linux competitive with commercial OS easy to install built collaboratively by software experts 1st major distro developed “openly in the spirit of GNU” GNU-supported for a while trivia: named after DEBra Lynn and IAN Ashley Murdock Stefano Zacchiroli (Debian) Debian, Ubuntu & co. Ubuntu Party, Toulouse 4 / 27 Debian: the operating system completely Free Software ñ DFSG ñ contrib, non-free a dozen architectures alpha, amd64, arm(el), hppa, i386, ia64, mips(el), powerpc, s390, sparc 2 non-Linux ports upcoming features miscellanea. ports, stability, packaging system, documentation, old hw support, smooth upgrades, i18n/l10n, the testing suite, runs anywhere, The largest GNU/Linux distro technical policy, a lot of packages, porting platform ... 29’000 packages (Squeeze) Stefano Zacchiroli (Debian) Debian, Ubuntu & co. -

SEAL-Embedded: a Homomorphic Encryption Library for the Internet of Things
IACR Transactions on Cryptographic Hardware and Embedded Systems ISSN 2569-2925, Vol. 2021, No. 3, pp. 756–779. DOI:10.46586/tches.v2021.i3.756-779 SEAL-Embedded: A Homomorphic Encryption Library for the Internet of Things Deepika Natarajan1 and Wei Dai2 1 University of Michigan, Ann Arbor, MI, [email protected] 2 Microsoft Research, Redmond, WA, [email protected] Abstract. The growth of the Internet of Things (IoT) has led to concerns over the lack of security and privacy guarantees afforded by IoT systems. Homomorphic encryption (HE) is a promising privacy-preserving solution to allow devices to securely share data with a cloud backend; however, its high memory consumption and computational overhead have limited its use on resource-constrained embedded devices. To address this problem, we present SEAL-Embedded, the first HE library targeted for em- bedded devices, featuring the CKKS approximate homomorphic encryption scheme. SEAL-Embedded employs several computational and algorithmic optimizations along with a detailed memory re-use scheme to achieve memory efficient, high performance CKKS encoding and encryption on embedded devices without any sacrifice of security. We additionally provide an “adapter” server module to convert data encrypted by SEAL-Embedded to be compatible with the Microsoft SEAL library for homomorphic encryption, enabling an end-to-end solution for building privacy-preserving applica- tions. For a polynomial ring degree of 4096, using RNS primes of 30 or fewer bits, our library can be configured to use between 64–137 KB of RAM and 1–264 KB of flash data, depending on developer-selected configurations and tradeoffs. -

Debian: 17 Ans De Logiciel Libre, ``Do-Ocracy'' Et Démocratie
Debian: 17 ans de logiciel libre, “do-ocracy” et démocratie Stefano Zacchiroli Debian Project Leader 24 février 2010 Télecom & Management SudParis Évry, France Stefano Zacchiroli (Debian) Debian: do-ocracy et démocratie Évry, France 1 / 43 Outline 1 What is Debian? History A system, a project, a community 2 What’s so special about Debian? 3 More in-depth Commitments Decision making Processes 4 Derivatives 5 Contribute to Debian Stefano Zacchiroli (Debian) Debian: do-ocracy et démocratie Évry, France 2 / 43 Prelude — the notion of “distribution” distributions are meant to ease software management key notion: the abstraction of package offer coherent collections of software killer application: package managers Stefano Zacchiroli (Debian) Debian: do-ocracy et démocratie Évry, France 3 / 43 Outline 1 What is Debian? History A system, a project, a community 2 What’s so special about Debian? 3 More in-depth Commitments Decision making Processes 4 Derivatives 5 Contribute to Debian Stefano Zacchiroli (Debian) Debian: do-ocracy et démocratie Évry, France 4 / 43 Debian: once upon a time Fellow Linuxers, This is just to announce the imminent completion of a brand-new Linux release, which I’m calling the Debian Linux Release. [. ] Ian A Murdock, 16/08/1993 comp.os.linux.development make GNU/Linux competitive with commercial OS easy to install built collaboratively by software experts 1st major distro developed “openly in the spirit of GNU” FSF-supported for a while trivia: named after DEBra Lynn and IAN Ashley Murdock Stefano Zacchiroli (Debian)