ACR Planning, Installation and Administration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

07 Vectorization for Intel C++ & Fortran Compiler .Pdf
Vectorization for Intel® C++ & Fortran Compiler Presenter: Georg Zitzlsberger Date: 10-07-2015 1 Agenda • Introduction to SIMD for Intel® Architecture • Compiler & Vectorization • Validating Vectorization Success • Reasons for Vectorization Fails • Intel® Cilk™ Plus • Summary 2 Optimization Notice Copyright © 2015, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Vectorization • Single Instruction Multiple Data (SIMD): . Processing vector with a single operation . Provides data level parallelism (DLP) . Because of DLP more efficient than scalar processing • Vector: . Consists of more than one element . Elements are of same scalar data types (e.g. floats, integers, …) • Vector length (VL): Elements of the vector A B AAi i BBi i A B Ai i Bi i Scalar Vector Processing + Processing + C CCi i C Ci i VL 3 Optimization Notice Copyright © 2015, Intel Corporation. All rights reserved. *Other names and brands may be claimed as the property of others. Evolution of SIMD for Intel Processors Present & Future: Goal: Intel® MIC Architecture, 8x peak FLOPs (FMA) over 4 generations! Intel® AVX-512: • 512 bit Vectors • 2x FP/Load/FMA 4th Generation Intel® Core™ Processors Intel® AVX2 (256 bit): • 2x FMA peak Performance/Core • Gather Instructions 2nd Generation 3rd Generation Intel® Core™ Processors Intel® Core™ Processors Intel® AVX (256 bit): • Half-float support • 2x FP Throughput • Random Numbers • 2x Load Throughput Since 1999: Now & 2010 2012 2013 128 bit Vectors Future Time 4 Optimization Notice -

New Instruction Set Extensions
New Instruction Set Extensions Instruction Set Innovation in Intels Processor Code Named Haswell [email protected] Agenda • Introduction - Overview of ISA Extensions • Haswell New Instructions • New Instructions Overview • Intel® AVX2 (256-bit Integer Vectors) • Gather • FMA: Fused Multiply-Add • Bit Manipulation Instructions • TSX/HLE/RTM • Tools Support for New Instruction Set Extensions • Summary/References Copyright© 2012, Intel Corporation. All rights reserved. Partially Intel Confidential Information. 2 *Other brands and names are the property of their respective owners. Instruction Set Architecture (ISA) Extensions 199x MMX, CMOV, Multiple new instruction sets added to the initial 32bit instruction PAUSE, set of the Intel® 386 processor XCHG, … 1999 Intel® SSE 70 new instructions for 128-bit single-precision FP support 2001 Intel® SSE2 144 new instructions adding 128-bit integer and double-precision FP support 2004 Intel® SSE3 13 new 128-bit DSP-oriented math instructions and thread synchronization instructions 2006 Intel SSSE3 16 new 128-bit instructions including fixed-point multiply and horizontal instructions 2007 Intel® SSE4.1 47 new instructions improving media, imaging and 3D workloads 2008 Intel® SSE4.2 7 new instructions improving text processing and CRC 2010 Intel® AES-NI 7 new instructions to speedup AES 2011 Intel® AVX 256-bit FP support, non-destructive (3-operand) 2012 Ivy Bridge NI RNG, 16 Bit FP 2013 Haswell NI AVX2, TSX, FMA, Gather, Bit NI A long history of ISA Extensions ! Copyright© 2012, Intel Corporation. All rights reserved. Partially Intel Confidential Information. 3 *Other brands and names are the property of their respective owners. Instruction Set Architecture (ISA) Extensions • Why new instructions? • Higher absolute performance • More energy efficient performance • New application domains • Customer requests • Fill gaps left from earlier extensions • For a historical overview see http://en.wikipedia.org/wiki/X86_instruction_listings Copyright© 2012, Intel Corporation. -

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -

SIMD Extensions
SIMD Extensions PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 12 May 2012 17:14:46 UTC Contents Articles SIMD 1 MMX (instruction set) 6 3DNow! 8 Streaming SIMD Extensions 12 SSE2 16 SSE3 18 SSSE3 20 SSE4 22 SSE5 26 Advanced Vector Extensions 28 CVT16 instruction set 31 XOP instruction set 31 References Article Sources and Contributors 33 Image Sources, Licenses and Contributors 34 Article Licenses License 35 SIMD 1 SIMD Single instruction Multiple instruction Single data SISD MISD Multiple data SIMD MIMD Single instruction, multiple data (SIMD), is a class of parallel computers in Flynn's taxonomy. It describes computers with multiple processing elements that perform the same operation on multiple data simultaneously. Thus, such machines exploit data level parallelism. History The first use of SIMD instructions was in vector supercomputers of the early 1970s such as the CDC Star-100 and the Texas Instruments ASC, which could operate on a vector of data with a single instruction. Vector processing was especially popularized by Cray in the 1970s and 1980s. Vector-processing architectures are now considered separate from SIMD machines, based on the fact that vector machines processed the vectors one word at a time through pipelined processors (though still based on a single instruction), whereas modern SIMD machines process all elements of the vector simultaneously.[1] The first era of modern SIMD machines was characterized by massively parallel processing-style supercomputers such as the Thinking Machines CM-1 and CM-2. These machines had many limited-functionality processors that would work in parallel. -

Issues with Using IE9 Browser
NOTICE: Browser Compatibility Issues with Internet Explorer 9 VIPR uses eAuthentication for authentication and the eAuth system is most compatible with Internet Explorer 8. Therefore, IE8 is the preferred browser for use with VIPR. Older versions of Internet Explorer (IE6, IE7) as well as the current version of Mozilla Firefox are working options also. If a customer is using IE9 and having issues, there are several options available to the user in this case: Option 1: Change IE9 to browse in IE8 mode • Open IE9 and hit the F12 key (or Tools > Developer Tools Menu). Click Browser Mode and select IE8. Try again. Option 2: Download Mozilla Firefox, make it your default browser, and try again • Mozilla Firefox can be downloaded from http://www.mozilla.org/en-US/firefox/new/ • To make Firefox the default browser: 1. At the top of the Firefox window, click on the Firefox button (Tools menu in Windows XP) and then click Options. 2. Select the Advanced panel, then click the General tab, and then click Check Now. 3. Select Yes to set Firefox as your default browser. Option 3: Rollback from IE9 to IE8 1. Open the Control Panel. Click on Programs and Features. This may be called Add/Remove programs if you are using an older version of Windows. 2. Click on View Installed Updates in the left pane. 3. Right click on Windows Internet Explorer 9 and select Uninstall. 4. Restart your computer when prompted and it should now be running IE8. If you continue to have issues with logging into VIPR, please contact the IIA Helpdesk at 866-224-7677, or by e-mail at [email protected]. -

Böngésző Programok 23. Tétel
23.tétel 1.0 Böngész ő programok használata, összehasonlítása. Az információ keresés technikái. Bogdán;Sleisz Böngész ő programok (Használata, összehasonlítása. Az információ keresés technikái) 23. tétel Az Internet kialakulása 20. század második felére helyezhet ő. Az ARPA rendszerb ől fejl ődött tovább az USA-ban, azóta folyamatosan fejlesztgetik a különböz ő protokollokat, illetve technológiákat, az adatforgalom sebességének növelése érdekében. Komoly tévhitet képez a világban, hogy az Internet az a böngész őben megjeleníthet ő weboldalak összessége. Nagy tévedés, ugyanis ez csak a HTTP protokoll által szolgáltatott tartalom, amely a teljes internetes adatforgalomnak kevesebb, mint az 1/10-ét képezi. Az internetet úgy kell elképzelni, mint egy hardvereszközt, ami az egész világot lefedi, a rajta elérhet ő szolgáltatásokat pedig nevezzük "szoftvereknek". Kétségkívül az egyik legelterjedtebb szolgáltatás ("szoftver") a 80-as port -on kommunikáló HTTP protokoll, amihez tartozik egy kommunikációs nyelv is. A HTTP protokoll célja hagyományos esetben- a távoli "szerveren/kiszolgálón" elhelyezked ő weboldal letöltése a helyi számítógépre. 1. A böngész ő a HTTP kommunikációs nyelven megfogalmazott kérést küld a szerver felé, hogy szeretnénk megjeleníteni a kért weboldalt 2. A szerver válaszol. Többféle üzenetet küldhet vissza a böngész őnek, és minden üzenethez tartozik egy azonosító szám is, úgynevezett Status Code. A legismertebb visszatérési érték talán a Not Found (a keresett weboldal nem található), melynek Status Code-ja a 404. Ilyet könnyedén el őidézhetünk, ha pl. nem létez ő oldalt próbálunk letölteni. A leggyakoribb azonban, ha a 200-as üzenetet kapjuk vissza, vagyis megjelenik az oldal. 3. Ezek után a böngész ő elkezdi letölteni a kért oldal forráskódját . A forráskód egy olyan leíró kód nagyrészt HTML nyelven, amely leírja, hogyan néz ki a weboldal. -

Amd Epyc 7351
SPEC CPU2017 Floating Point Rate Result spec Copyright 2017-2019 Standard Performance Evaluation Corporation Sugon SPECrate2017_fp_base = 176 Sugon A620-G30 (AMD EPYC 7351) SPECrate2017_fp_peak = 177 CPU2017 License: 9046 Test Date: Dec-2017 Test Sponsor: Sugon Hardware Availability: Dec-2017 Tested by: Sugon Software Availability: Aug-2017 Copies 0 30.0 60.0 90.0 120 150 180 210 240 270 300 330 360 390 420 450 480 510 560 64 550 503.bwaves_r 32 552 165 507.cactuBSSN_r 64 163 130 508.namd_r 64 142 64 141 510.parest_r 32 146 168 511.povray_r 64 175 64 121 519.lbm_r 32 124 64 192 521.wrf_r 32 161 190 526.blender_r 64 188 164 527.cam4_r 64 162 248 538.imagick_r 64 250 205 544.nab_r 64 205 64 160 549.fotonik3d_r 32 163 64 96.7 554.roms_r 32 103 SPECrate2017_fp_base (176) SPECrate2017_fp_peak (177) Hardware Software CPU Name: AMD EPYC 7351 OS: Red Hat Enterprise Linux Server 7.4 Max MHz.: 2900 kernel 3.10.0-693.2.2 Nominal: 2400 Enabled: 32 cores, 2 chips, 2 threads/core Compiler: C/C++: Version 1.0.0 of AOCC Orderable: 1,2 chips Fortran: Version 4.8.2 of GCC Cache L1: 64 KB I + 32 KB D on chip per core Parallel: No L2: 512 KB I+D on chip per core Firmware: American Megatrends Inc. BIOS Version 0WYSZ018 released Aug-2017 L3: 64 MB I+D on chip per chip, 8 MB shared / 2 cores File System: ext4 Other: None System State: Run level 3 (Multi User) Memory: 512 GB (16 x 32 GB 2Rx4 PC4-2667V-R, running at Base Pointers: 64-bit 2400) Peak Pointers: 32/64-bit Storage: 1 x 3000 GB SATA, 7200 RPM Other: None Other: None Page 1 Standard Performance Evaluation -

CS 110 Discussion 15 Programming with SIMD Intrinsics
CS 110 Discussion 15 Programming with SIMD Intrinsics Yanjie Song School of Information Science and Technology May 7, 2020 Yanjie Song (S.I.S.T.) CS 110 Discussion 15 2020.05.07 1 / 21 Table of Contents 1 Introduction on Intrinsics 2 Compiler and SIMD Intrinsics 3 Intel(R) SDE 4 Application: Horizontal sum in vector Yanjie Song (S.I.S.T.) CS 110 Discussion 15 2020.05.07 2 / 21 Table of Contents 1 Introduction on Intrinsics 2 Compiler and SIMD Intrinsics 3 Intel(R) SDE 4 Application: Horizontal sum in vector Yanjie Song (S.I.S.T.) CS 110 Discussion 15 2020.05.07 3 / 21 Introduction on Intrinsics Definition In computer software, in compiler theory, an intrinsic function (or builtin function) is a function (subroutine) available for use in a given programming language whose implementation is handled specially by the compiler. Yanjie Song (S.I.S.T.) CS 110 Discussion 15 2020.05.07 4 / 21 Intrinsics in C/C++ Compilers for C and C++, of Microsoft, Intel, and the GNU Compiler Collection (GCC) implement intrinsics that map directly to the x86 single instruction, multiple data (SIMD) instructions (MMX, Streaming SIMD Extensions (SSE), SSE2, SSE3, SSSE3, SSE4). Yanjie Song (S.I.S.T.) CS 110 Discussion 15 2020.05.07 5 / 21 x86 SIMD instruction set extensions MMX (1996, 64 bits) 3DNow! (1998) Streaming SIMD Extensions (SSE, 1999, 128 bits) SSE2 (2001) SSE3 (2004) SSSE3 (2006) SSE4 (2006) Advanced Vector eXtensions (AVX, 2008, 256 bits) AVX2 (2013) F16C (2009) XOP (2009) FMA FMA4 (2011) FMA3 (2012) AVX-512 (2015, 512 bits) Yanjie Song (S.I.S.T.) CS 110 Discussion 15 2020.05.07 6 / 21 SIMD extensions in other ISAs There are SIMD instructions for other ISAs as well, e.g. -

PCLMULQDQ Instruction Definition
® White Paper Intel Carry-Less Shay Gueron Multiplication Intel Architecture Group, Israel Development Center Intel Corporation Instruction and its Michael E. Kounavis Usage for Computing Intel Labs, Circuits and Systems Research the GCM Mode Intel Corporation The Intel® PCLMULQDQ instruction is a new instruction available beginning with the all new 2010 Intel® Core™ processor family based on the 32nm Intel® microarchitecture codename Westmere. The PCLMULQDQ instruction performs carry-less multiplication of two 64-bit operands. This paper provides information on the instruction, and its usage for computing the Galois Hash. It also provides code examples for the usage of PCLMULQDQ, together with the Intel® AES New Instructions for efficient implementation of AES in Galois Counter Mode (AES-GCM). This version of the paper also provides high performance code examples for AES-GCM, and discloses, for the first time, their measured performance numbers. 323640-002 Revision 2.02 April 2014 Intel® Carry-Less Multiplication Instruction and its Usage for Computing the GCM Mode Contents Introduction ..................................................................................................................... 4 Preliminaries .................................................................................................................... 4 PCLMULQDQ Instruction Definition .................................................................................... 7 The Galois Counter Mode (GCM) ..................................................................................... -
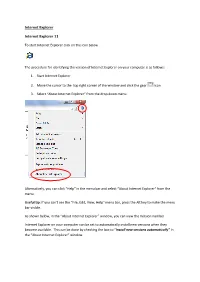
Internet Explorer
Internet Explorer Internet Explorer 11 To start Internet Explorer click on the icon below The procedure for identifying the version of Internet Explorer on your computer is as follows: 1. Start Internet Explorer 2. Move the cursor to the top right corner of the window and click the gear icon 3. Select “About Internet Explorer” from the drop down menu. Alternatively, you can click “Help” in the menu bar and select “About Internet Explorer“ from the menu. Useful tip: If you can’t see the “File, Edit, View, Help” menu bar, press the Alt key to make the menu bar visible. As shown below, in the “About Internet Explorer” window, you can view the Version number. Internet Explorer on your computer can be set to automatically install new versions when they become available. This can be done by checking the box to “Install new versions automatically” In the “About Internet Explorer” window. Internet Explorer 9 To view the “About” page in Internet Explorer: 1. At the top right of the program window, click the gear icon 2. Select “About Internet Explorer” in the drop down menu. The version number will be displayed in the “About Internet Explorer” window, see example below. Updating your Internet Explorer Browser Microsoft updates Internet Explorer using its Windows update feature. If you are regularly installing the latest Windows updates from Microsoft then you should be on the latest version of Internet Explorer. Note Windows 10 automatically updates Internet Explorer. Follow the procedure below to manually trigger an update of the Internet Explorer Browser: 1. Open the Control Panel. -

Reference Manual for Skills Development Facilitators
Reference Manual for Skills Development Facilitators 2020 The MICT SETA SDF Reference Manual 2020 Table of Contents Our Vision: ........................................................................................................................................ 3 Our Mission: ..................................................................................................................................... 3 Our Values ........................................................................................................................................ 3 PART A .............................................................................................................................................. 4 Introduction and Background Information ..................................................................................... 5 Acronyms and Definitions ................................................................................................................ 7 Process Information ......................................................................................................................... 8 The Organizing Framework for Occupations (OFO) ..................................................................... 17 Expenses that may be included in the ATR/PTR and WSP/PTP .................................................. 26 The MICT SETA Perspective .......................................................................................................... 27 Applying for Discretionary Grant Funding .................................................................................. -

X86 Intrinsics Cheat Sheet Jan Finis [email protected]
x86 Intrinsics Cheat Sheet Jan Finis [email protected] Bit Operations Conversions Boolean Logic Bit Shifting & Rotation Packed Conversions Convert all elements in a packed SSE register Reinterpet Casts Rounding Arithmetic Logic Shift Convert Float See also: Conversion to int Rotate Left/ Pack With S/D/I32 performs rounding implicitly Bool XOR Bool AND Bool NOT AND Bool OR Right Sign Extend Zero Extend 128bit Cast Shift Right Left/Right ≤64 16bit ↔ 32bit Saturation Conversion 128 SSE SSE SSE SSE Round up SSE2 xor SSE2 and SSE2 andnot SSE2 or SSE2 sra[i] SSE2 sl/rl[i] x86 _[l]rot[w]l/r CVT16 cvtX_Y SSE4.1 cvtX_Y SSE4.1 cvtX_Y SSE2 castX_Y si128,ps[SSE],pd si128,ps[SSE],pd si128,ps[SSE],pd si128,ps[SSE],pd epi16-64 epi16-64 (u16-64) ph ↔ ps SSE2 pack[u]s epi8-32 epu8-32 → epi8-32 SSE2 cvt[t]X_Y si128,ps/d (ceiling) mi xor_si128(mi a,mi b) mi and_si128(mi a,mi b) mi andnot_si128(mi a,mi b) mi or_si128(mi a,mi b) NOTE: Shifts elements right NOTE: Shifts elements left/ NOTE: Rotates bits in a left/ NOTE: Converts between 4x epi16,epi32 NOTE: Sign extends each NOTE: Zero extends each epi32,ps/d NOTE: Reinterpret casts !a & b while shifting in sign bits. right while shifting in zeros. right by a number of bits 16 bit floats and 4x 32 bit element from X to Y. Y must element from X to Y. Y must from X to Y. No operation is SSE4.1 ceil NOTE: Packs ints from two NOTE: Converts packed generated.