Virtual System Administrator 4.7.0.0 HELP System Documentation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Taking Advantage of the SAS System on Windows NT
Taking advantage of the SAS System on Windows NT Mark W. Cates, SAS Institute Inc., Cary, NC ABSTRACT Unless specified, all the SAS System products and features are provided on both Windows NT Windows NT is fast becoming the universal Workstation and Windows NT Server. This desktop client operating system as well as an paper assumes the current release of Windows important file and compute server for mission NT is Version 4.0. For brevity, the abbreviation critical applications. This paper presents a NT will be used for Windows NT. discussion of the state of Windows NT and how the SAS System Release 6.12 for Windows takes advantage and integrates with the operating Windows Family - Single Executable Image system. Areas such as the user interface, OLE and Web integration are presented. Data access Windows NT is now in its full 3rd generation, and Microsoft BackOffice integration, and with the release of Windows NT Workstation hardware considerations are also presented. 4.0 and Windows NT Server 4.0. NT Workstation and NT Server share the same microkernel, and is portable to several RISC INTRODUCTION platforms, including DEC Alpha AXP, and the PowerPC Prep Platforms. The MIPS chip Microsoft Windows NT sales grew dramatically is no longer supported by Windows NT. The in 1996, as many corporations which have been majority of NT installations still run on the Intel investigating Windows NT have now begun to Pentium® and Pentium Pro® processor. The deploy Windows NT for the client desktop. SAS System Release 6.12 only supports the Intel Many of these deployments were replacing platform, and the Pentium Pro processor is ® Windows 3.1 and Windows 95 . -

9.4 Flight Operations Data
REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington Headquarters Services, Directorate for information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188), Washington, DC 20503. 1. AGENCY USE ONLY (Leave blank) 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED August 1995 Final Report Jan 93 - Aug 95 4. TITLE AND SUBTITLE 5. FUNDING NUMBERS Integrated Noise Model (INM) Version 5.0 User's Guide DTFA01-93-C-00078 6. AUTHOR(S) Task Orders 2 and 5 ATAC Olmstead, Bryan, Jeng, Mirsky, Rajan* VNTSC Fleming, D'Aprile, Gerbi*, Rickley*, Turner* FA565/A5012 LeTech Le, Le, Chen * subcontractors FAA Plante, Gulding (Prog. Mgr.), Vahovich, Warren 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. PERFORMING ORGANIZATION ATAC Corporation DOT/VNTSC LeTech, Inc. REPORT NUMBER 757 N. Mary Ave. DTS-75, Kendall Sq. 5400 Shawnee Rd #202 Sunnyvale, CA 94086 Cambridge, MA 02142 Alexandria, VA 22312 9. SPONSORING/MONITORING AGENCY NAME(S) AND ADDRESS(ES) 10. SPONSORING/MONITORING U.S. Department of Transportation AGENCY REPORT NUMBER Federal Aviation Administration Office of Environment and Energy, AEE-120 FAA-AEE-95-01 800 Independence Ave. -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19 -

Microsoft Palladium
Microsoft Palladium: A Business Overview Combining Microsoft Windows Features, Personal Computing Hardware, and Software Applications for Greater Security, Personal Privacy, and System Integrity by Amy Carroll, Mario Juarez, Julia Polk, Tony Leininger Microsoft Content Security Business Unit June 2002 Legal Notice This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place or event is intended or should be inferred. -

Getting Started Guide
Getting Started Guide P/N 066450-004 EZBuilder Intermec Technologies Corporation 6001 36th Avenue West P.O. Box 4280 Everett, WA 98203-9280 U.S. technical and service support: 1-800-755-5505 U.S. media supplies ordering information: 1-800-227-9947 Canadian technical and service support: 1-800-687-7043 Canadian media supplies ordering information: 1-800-267-6936 Outside U.S. and Canada: Contact your local Intermec service supplier. The information contained herein is proprietary and is provided solely for the purpose of allowing customers to operate and/or service Intermec manufactured equipment and is not to be released, reproduced, or used for any other purpose without written permission of Intermec. Information and specifications in this manual are subject to change without notice. 2000 by Intermec Technologies Corporation All Rights Reserved The word Intermec, the Intermec logo, EZBuilder, JANUS, IRL, Trakker Antares, Adara, Duratherm, Precision Print, PrintSet, Virtual Wedge, and CrossBar are either trademarks or registered trademarks of Intermec Technologies Corporation. Microsoft, Active X, Visual C++, Windows, Win32s, the Windows logo, and Windows NT are either trademarks or registered trademarks of Microsoft Corporation. Throughout this manual, trademarked names may be used. Rather than put a trademark (™ or ®) symbol in every occurrence of a trademarked name, we state that we are using the names only in an editorial fashion, and to the benefit of the trademark owner, with no intention of infringement. EZBuilder Getting Started Guide Welcome to EZBuilder EZBuilder™ is a fast, easy-to-use development tool for creating applications that run on Trakker Antares®, T2090, and 6400 terminals. -

DLCC Software Catalog
Daniel's Legacy Computer Collections Software Catalog Category Platform Software Category Title Author Year Media Commercial Apple II Integrated Suite Claris AppleWorks 2.0 Claris Corporation and Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 1.0.2 --> 1.1.1 Update Apple Computer, Inc. 1984 400K Commercial Apple II Operating System Apple IIGS System 1.1 Apple Computer, Inc. 1986 800K Commercial Apple II Operating System Apple IIGS System 2.0 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.1 Apple Computer, Inc. 1987 800K Commercial Apple II Operating System Apple IIGS System 3.2 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 4.0 Apple Computer, Inc. 1988 800K Commercial Apple II Operating System Apple IIGS System 5.0 Apple Computer, Inc. 1989 800K Commercial Apple II Operating System Apple IIGS System 5.0.2 Apple Computer, Inc. 1989 800K Commercial Apple II Reference: Programming ProDOS Basic Programming Examples Apple Computer, Inc. 1983 800K Commercial Apple II Utility: Printer ImageWriter Toolkit 1.5 Apple Computer, Inc. 1984 400K Commercial Apple II Utility: User ProDOS User's Disk Apple Computer, Inc. 1983 800K Total Apple II Titles: 12 Commercial Apple Lisa Emulator MacWorks 1.00 Apple Computer, Inc. 1984 400K Commercial Apple Lisa Office Suite Lisa 7/7 3.0 Apple Computer, Inc. 1984 400K Total Apple Lisa Titles: 2 Commercial Apple Mac OS 0-9 Audio Audioshop 1.03 Opcode Systems, Inc. 1992 800K Commercial Apple Mac OS 0-9 Audio Audioshop 2.0 Opcode Systems, Inc. -
Microsoft Windows for MS
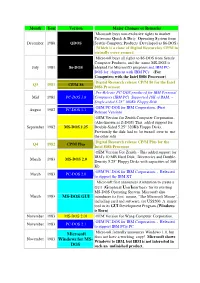
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

Novell Appnotes September 2002
Novell, Inc. 464-000063-009 Novell AppNotes • September 2002 Novell AppNotes Order Desk PO Box 14530 Fremont, CA 94539 USA Novell AppNotes® Tel 925 463 7391 Tel 800 395 7135 Novell Research www.novell.com Call 1-800-395-7135 for subscriptions SEPTEMBER 2002 Novell’s Technical Journal for Implementing, Managing, and Programming to one Net Spotlight on Troubleshooting APPNOTES 4 Troubleshooting Novell MEDIA MAIL iChain 2.1 Authentication U.S. Postage Issues PAID Fremont, CA 29 Managing Windows 2000 Permit# 774 Group Policies with Novell Appnotes Returns ZENworks for Desktops 3 c/o Zomax, Inc. Troubleshooting Spotlight on 47 How to Use the Alarm 1640 Berryessa Rd, Suite B Management System of San Jose, CA 95133 ZENworks for Servers 3 USA DEVELOPER NOTES CHANGE SERVICE REQUESTED 59 A Methodology for Troubleshooting DirXML 79 Implementing a Utility for Searching Windows Executable Files on NetWare 87 How to Build J2EE Applications Using Novell Technologies: Part 5 SECTIONS 95 Net Management 105 Net Support 116 Code Break 127 Viewpoints AppNotes ® Novell’s Technical Journal for Implementing, Managing, and Programming to one Net September 2002 Volume 13, Number 9 Editor-in-Chief Gamal B. Herbon Novell AppNotes® (formerly Novell Application Notes, ISSN# 1077-0321, and now including the former Novell Developer Notes) is published monthly by Novell, 1800 S. Managing Editor Ken Neff Novell Place, Provo, UT 84606. The material in the AppNotes is based on actual field experience and technical research performed by Novell personnel, covering topics -

At Home with Your Computer
DEC 1995 Britain's favourite Personal Computer magazine MORTAL KOMBAT MANIA PAGE 98 Consumer PC/TVs Mortal Kombat mania ● December 1995 £2.95 Pentium Pro Arrives: Viglen’s P6 Powerhouse Overseas Price £3.95 France 110 FF Germany DM 20,00 WIN a Pentium ● Italy 18,000 Lire Spain 1,225 PTS Malta Lm 2.85c Holland HFL 17,95 Belgium 364.00 BFr Notebook p.266 Group Tests : Anti-virus packages, Storage and backup media Finland FIM 49.50 Canada CAN$12.95 VNU Business Publications At home with your PC/TVsPC/TVs computer ● Office hybrids: printer/fax/scanner Pentium Pro arrives First glimpse of ● HP Omnibook 600CT Viglen’s P6 Office hybrids Printer/ ● fax/ RAM Doublers scanner RAM Doublers Memory for less? IF YOUR CD-ROM OR 3.5" DISK ARE MISSING Anti-Virus packages ASK YOUR NEWSAGENT Seven of the best tested ALL HARDWARE TESTED BY THE VNU LABS VOL18 NO12 Group Test All sorts of storage stuff December 1995 PCW December 1995 Contents Regulars Hands On 110 Group Tests First Impressions 55 18 Newsprint PCTVs Storage and Backup 56 Gadgets Macro virus sweeps the world. Intel 134 launches the (P6) Pentium Pro. First 60 HP Omnibook 600 CT Cited as the next big growth Hardware look at “Pentium class” chip for hand- ● Often a secondary concern, storage and The latest model in Hewlett-Packard’s helds. Eight-speed CD drives. New area for PCs, the home Omnibook range will give your desktop print system sprouts cheap lasers. backup devices play an important part in com- a run for its money. -

The Making of Netscape
The Making of Netscape This case was written by Professor Rajeev Kohli, Graduate School of Business, Columbia University, for class discussion rather than to illustrate either effective or ineffective handling of an administrative situation. 1 The Making of Netscape Marc Andreessen started working on the Mosaic web browser in 1992. He was a computer science student at the University of Illinois, but he spent a lot more time at the NCSA, the University’s supercomputing center, than he did in the classroom. “Working at NCSA was fascinating,” says Andreessen. “The super-computing program in the mid-1980's originated because the government thought it was crucial that a powerful computing infrastructure be provided for scientists. An interesting thing happened around 1990: all the supercomputing centers essentially stopped running supercomputers. They shut down the Crays. They could no longer afford to keep them running, especially with the advent of more cost efficient microprocessors. Since it no longer made sense to run a supercomputer, what do you do? And so networking quickly became a very big part of NCSA, the theory being that the next stage would be to link together everything -- especially scientists and educators who up until that point had been using the Crays. Networking had arrived so fast, and everything was happening so rapidly, that people just hadn't yet gotten around to making it accessible.” The Internet phenomenon had been gaining momentum for a decade, but its use was still limited to a small group of skilled programmers. “People had also been talking about hypertext for a long time, and it finally happened at NCSA,” says Andreessen. -

Using the SAS System Release 6.12 on Windows
Using the SAS® System Release 6.12 on WindowsTM Gary Mehler, SAS Institute Inc., Cary, NC ABSTRACT This paper provides an overview of the new Release 6.12 enhancements. You should Release 6.12 of the SAS System for Per- view this paper as an introduction but you sonal Computers provides support for Mi- should refer to the SAS Companion for the crosoft Windows (version 3.1 using Win32s Microsoft Windows Environment and the technology, Windows 95, Windows NT), and OS/2 Environment: Changes and Enhance- OS/2® (Warp). With this release, the SAS ments of the SAS System for more details System incrementally improves both its user as well as online documentation, which is interface and its interoperability with other more extensive in Release 6.12. Release PC applications. This paper discusses both 6.12 continues to provide incremental en- new features and incremental enhance- hancements to the user interface and ments to the user interface. This paper also interoperability areas of the SAS System. In describes the SAS System for Windows 95 other areas such as the SAS System Viewer and Windows NT 4.0, detailing the new user and the SETUP application, new features interface features that are consistent with have also been added. the look and feel for Windows 95 and Win- dows NT 4.0. The SAS System Viewer, pro- duction for 6.12, is described as is the GUI- THE SAS SYSTEM VIEWER based SETUP program. Interoperability topics include Windows Explorer integration, The SAS System Viewer is a electronic mail, Lotus Notes, OLE, OBDC, freely redistributable application and access to external DLLs. -

The SAS System, Release 6.12 (TS065), Windows
System Requirements The SAS System Release 6.12 (TS065) Windows, Windows NT, Windows 95 This document provides requirements for installing and running the SAS System for Windows, Windows NT, and Windows 95. You must update your system to meet the minimum requirements before running the SAS System. The major requirements listed in the document are: q Software Requirements q Hardware Requirements q Additional Features q Space Requirements q Specific Product Requirements q Graphics Hardware and Software Compatibility For additional information and to view the latest system requirements for your system, access the SAS Institute Web site at: http://www.sas.com/software/enclosures/system_req.html or contact SAS Institute Technical Support (refer to Contacting SAS Institute Technical Support in the installation instructions included in your package). For information about Year 2000 compliance, see http://www.sas.com/techsup/download/technote/y2kcomp.html. Software Requirements Operating System Windows WIN32s • DOS 5.0 or later, Windows 3.1 or Windows for Workgroups 3.11 Note: The Microsoft Windows WIN32s Operating System Extension 1.30.166 is provided on the SAS System installation media. You will need 3.5 MB of disk space to upgrade to WIN32s. This product will not run in the OS/2 environment because OS/2 does not support the correct level of WIN32s. Windows, Windows NT, Windows 95, Release 6.12 (TS065) December 21, 1999 1 If SHARE.EXE is being used, then the statement used to run SHARE.EXE should be modified to include the options shown: C:\DOS\SHARE.EXE /L:500 /F:5100 SHARE.EXE is not required to run the SAS System, but may be required by other applications.