Should the US Government Maintain Control Over the Internet's Root
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

An Evaluation of Developments of E- Commerce Practices in Kazakhstan in the Framework of Historical Process
ISSN 0798 1015 HOME Revista ESPACIOS ÍNDICES / Index A LOS AUTORES / To the ! ! AUTORS ! Vol. 40 (Number 22) Year 2019. Page 10 An evaluation of developments of e- commerce practices in Kazakhstan in the framework of historical process Una evaluación de la evolución de las prácticas de comercio electrónico en Kazajstán en el marco del proceso histórico SEN, Bulent 1; YDYRYS, Serikbay 2; MUNASSIPOVA, Malike 3 & KURALBAYEV, Almas 4 Received: 28/02/2019 • Approved: 07/06/2019 • Published 01/07/2019 Contents 1. Introduction 2. Methodology 3. Results 4. Conclusions Bibliographic references ABSTRACT: RESUMEN: The use of internet in Kazakhstan seems to have El uso de internet en Kazajstán parece haber increased considerably, especially between 2008 and aumentado considerablemente, especialmente entre 2011. The increase of 176.4% in 2008 is the highest 2008 y 2011. El aumento del 176,4% en 2008 es el in all years. When the country’s wide land and low más alto de todos los años. Cuando se considera la population ratio is considered, the given situations amplia proporción de tierra y baja población del país, make it an ideal candidate for the internet ordering las situaciones dadas lo convierten en un candidato sector. Products that are developing in the sense of ideal para el sector de pedidos por Internet. Los retail and that are considered suitable for electronic productos que se están desarrollando en el sentido de commerce are respectively as follows: cosmetics, la venta minorista y que se consideran adecuados electronic goods, home textile and leisure products. para el comercio electrónico son, respectivamente, los Keywords: public-private partnerships, public-private siguientes: cosméticos, productos electrónicos, partnership projects, project efficiency, technical and textiles para el hogar y productos de ocio. -

The Internet and Isi: Four Decades of Innovation
THE INTERNET AND ISI: FOUR DECADES OF INNOVATION ROD BECKSTROM President and Chief Executive Officer Internet Corporation for Assigned Names and Numbers (ICANN) 40th Anniversary of USC Information Sciences Institute 26 April 2012 As prepared for delivery It’s an honor to be here today to mark the 40th anniversary of the University of Southern California’s Information Sciences Institute. Thank you to Herb Schorr for inviting me to speak with you today and participate in the day’s events. When he steps down he will leave some very large shoes to fill. When I received Herb’s invitation, I seized upon it as an opportunity to come before you to express the sincere gratitude that my colleagues and I feel for the work and support of ISI. When I think of ICANN and its development, and all we have accomplished, I never forget that we stand upon the shoulders of giants, many of whom contributed to my remarks today. In fact, I owe a special debt of gratitude to Bob Kahn, who has been a mentor to me. I am honored that he took the time to walk through a number of details in the history I have been asked to relate. The organizers asked me to speak about the history of ISI and ICANN. They also invited me to talk a bit about the future of the Internet. In my role as President and CEO of ICANN, I have many speaking engagements that are forward looking. They are opportunities to talk about ICANN’s work and how it will usher in the next phase in the history of the global, unified Internet that many of you have helped to create. -

Per Concordiam V7N2 ENG.Pdf
per VOLUME 7, ISSUE 2, 2016 ConcordiamJournal of European Security and Defense Issues n BALTIC CYBER DEFENSE n BATTLING BOKO HARAM Nations sign important agreement Nigeria’s online war against extremism n CYBER TERRORISM PLUS Categorizing attacks by severity Partnership for Peace n PROTECTING UKRAINE Kazakhstan seeks security Kyiv faces an array of threats Georgia’s approach to cyber INFORMATION SHARING A Cooperative Approach to Cyber Security Table of Contents features ON THE COVER Cyber attacks rarely recognize national borders. So the strategies aimed at preventing, deflecting and responding to these attacks must also be regionally and globally oriented. GETTY IMAGES 24 10 Defining Cyber Terrorism 28 Online Extremism in Nigeria By Ruben Tuitel By Tommy Victor Udoh, Nigerian Defense Space Agency Coming up with a globally acceptable definition The government focuses on countering Boko Haram’s of what constitutes Internet-based terrorism is use of social media to seduce vulnerable recruits. difficult. 34 Kazakhstan Adapts to the 18 Baltic Cyber Cooperation Cyber Age By Vytautas Butrimas, senior advisor, Cybersecurity By Anna Gussarova, Kazakhstan Institute for and IT Department, Ministry of National Defense, Strategic Studies Republic of Lithuania The country’s growing reliance on the digital economy Lithuania, Latvia and Estonia advance regional demands a change in thinking about security. cooperation by aligning their cyber defense policies. 40 Moldova’s Cyber Security Center By Natalia Spinu, Chief, Moldovan Cyber Security Center, 24 A New Cyber Security Curriculum E.S. Center for Special Telecommunications By Sean Costigan and Michael Hennessy The country uses a comprehensive approach to NATO and the Partnership for Peace devise an improve its ability to defend itself against online threats. -

The State of the Internet in France
2020 TOME 3 2020 REPORT The state of the Internet in France French Republic - June 2020 2020 REPORT The state of the Internet in France TABLE OF CONTENTS EDITORIAL 06 CHAPTER 3 ACCELERATING Editorial by Sébastien Soriano, THE TRANSITION TO IPV6 40 President of Arcep 06 1. Phasing out IPv4: the indispensable transition to IPv6 40 NETWORKS DURING 2. Barometer of the transition HET COVID-19 CRISIS 08 to IPv6 in France 47 3. Creation of an IPv6 task force 54 PART 1 000012 gathering the Internet ecosystem ENSURING THE INTERNET FUNCTIONS PROPERLY PART 2 58 CHAPTER 1 ENSURING IMPROVING INTERNET INTERNET OPENNESS QUALITY MEASUREMENT 14 CHAPTER 4 1. Potential biases of quality of service GUARANTEEING measurement 15 NET NEUTRALITY 60 2. Implementing an API in customer 1. Net neutrality outside of France 60 boxes to characterise the user environment 15 2. Arcep’s involvement in European works 65 3. Towards more transparent and robust measurement 3. Developing Arcep’s toolkit 68 18 methodologies 4. Inventory of observed practices 70 4. Importance of choosing the right test servers 22 CHAPTER 5 5. Arcep’s monitoring of mobile DEVICES AND PLATFORMS, Internet quality 26 TWO STRUCTURAL LINKS IN THE INTERNET ACCESS CHAPTER 2 CHAIN 72 SUPERVISING DATA 1. Device neutrality: progress report 72 INTERCONNECTION 29 2. Structural digital platforms 74 1. How the Internet’s architecture has evolved over time 29 2. State of interconnection in France 33 PART 3 76 TACKLE THE DIGITAL TECHNOLOGY’S ENVIRONMENTAL CHALLENGE CHAPTER 6 INTEGRATE DIGITAL TECH’S ENVIRONMENTAL FOOTPRINT INTO THE REGULATION 78 1. -

Digital Silk Road in Central Asia: Present and Future
Digital Silk Road in Central Asia: Present and Future NARGIS KASSENOVA & BRENDAN DUPREY, EDITORS JUNE 2021 Digital Silk Road in Central Asia: Present and Future Nargis Kassenova & Brendan Duprey, Editors JUNE 2021 Digital Silk Road in Central Asia: Present and Future is a project of the Davis Center for Russian and Eurasian Studies at Harvard University, and the Sustainable Kazakhstan Research Institute, Narxoz University, supported by a grant from Friedrich Ebert Foundation in Kazakhstan. © 2021 Davis Center for Russian and Eurasian Studies Cataloging-in-Publication data ISBN: 978-0-578-93435-8 Please direct inquiries to: Nargis Kassenova Kathryn W. and Shelby Cullom Davis Center for Russian and Eurasian Studies Harvard University 1730 Cambridge Street, Suite S301 Cambridge, MA 02138 Phone: 617.496.5684 Fax: 617.495.8319 [email protected] The full text of this report can be accessed at https://daviscenter.fas.harvard.edu/digital-silk-road. Limited print copies are also available. ii Digital Silk Road in Central Asia: Present and Future Contents iv Acknowledgements v Introduction Nargis Kassenova and Brendan Duprey vii Executive Summary 1 The Puzzle of the Digital Silk Road Elisa Oreglia, Hongyi Ren, and Chia-Chi Liao 9 Sino-Russian Advocacy for “Internet Sovereignty” and State-Led Internet Governance Miranda Lupion 17 Digital Silk Road and Surveillance Technology in Central Asia Cian Stryker 55 The Sino-Russian Digital Cooperation and Its Implications for Central Asia Miranda Lupion 77 Beyond the GovTech: The Pitfalls of Kazakhstan’s Digitalization Agenda Anna Gussarova 85 Turkmenistan’s Digitalization Strategy: Old Practices, New Façade? Rustam Muhamedov 93 The Role of Big Earth Data for the Implementation of the Sustainable Development Goals in Central Asia Brendan Duprey and Akmal Akramkhanov 118 About the Authors Contents iii Acknowledgements We would like to thank the Friedrich Ebert Foundation in Kazakhstan for providing moral and financial support to the project. -

The People Who Invented the Internet Source: Wikipedia's History of the Internet
The People Who Invented the Internet Source: Wikipedia's History of the Internet PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 22 Sep 2012 02:49:54 UTC Contents Articles History of the Internet 1 Barry Appelman 26 Paul Baran 28 Vint Cerf 33 Danny Cohen (engineer) 41 David D. Clark 44 Steve Crocker 45 Donald Davies 47 Douglas Engelbart 49 Charles M. Herzfeld 56 Internet Engineering Task Force 58 Bob Kahn 61 Peter T. Kirstein 65 Leonard Kleinrock 66 John Klensin 70 J. C. R. Licklider 71 Jon Postel 77 Louis Pouzin 80 Lawrence Roberts (scientist) 81 John Romkey 84 Ivan Sutherland 85 Robert Taylor (computer scientist) 89 Ray Tomlinson 92 Oleg Vishnepolsky 94 Phil Zimmermann 96 References Article Sources and Contributors 99 Image Sources, Licenses and Contributors 102 Article Licenses License 103 History of the Internet 1 History of the Internet The history of the Internet began with the development of electronic computers in the 1950s. This began with point-to-point communication between mainframe computers and terminals, expanded to point-to-point connections between computers and then early research into packet switching. Packet switched networks such as ARPANET, Mark I at NPL in the UK, CYCLADES, Merit Network, Tymnet, and Telenet, were developed in the late 1960s and early 1970s using a variety of protocols. The ARPANET in particular led to the development of protocols for internetworking, where multiple separate networks could be joined together into a network of networks. In 1982 the Internet Protocol Suite (TCP/IP) was standardized and the concept of a world-wide network of fully interconnected TCP/IP networks called the Internet was introduced. -

(Jake) Feinler
Oral History of Elizabeth (Jake) Feinler Interviewed by: Marc Weber Recorded: September 10, 2009 Mountain View, California Editor’s note: Material in [square brackets] has been added by Jake Feinler CHM Reference number: X5378.2009 © 2009 Computer History Museum Oral History of Elizabeth (Jake) Feinler Marc Weber: I’m Marc Weber from the Computer History Museum, and I’m here today, September 10th, 2009, with “Jake” Elizabeth Feinler, who was the director of the Network Information Systems Center at SRI. [This group provided the Network Information Center (NIC) for the Arpanet and the Defense Data Network (DDN), a project for which she was the principal investigator from 1973 until 1991. Earlier she was a member of Douglas Engelbart’s Augmentation Research Center (ARC) at SRI [which [housed] the second computer on the Arpanet. It was on this computer that the NIC resided initially.] Jake is also a volunteer here at the museum. [She has donated an extensive collection of early Internet papers to the museum, and has been working on organizing this collection for some time.] Thank you for joining us. Elizabeth (Jake) Feinler: My pleasure. Weber: I really just wanted to start with where did you grow up and what got you interested in technical things or things related to this. Feinler: [Originally I hoped to pursue a career in advertising design, but could not afford the freshman room and board away from home, so I began attending West Liberty State College (now West Liberty University) close to my home. West Liberty was very small then, and the] art department [wasn’t very good. -

Steve Crocker Resume
STEPHEN D. CROCKER 5110 Edgemoor Lane Bethesda, MD 20814 Mobile: (301) 526-4569 [email protected] SUMMARY Over 50 years of experience in the industrial, academic and government environments involving a wide range of computing and network technologies with specialization in networking and security. Strong background in formal methods, including PhD thesis creating a new logic for reasoning about the correct operation of machine language programs and the development of a program verification system to demonstrate the method. Managed numerous innovative research and development efforts benefiting private industry and government interests. Extensive involvement in the development of the Internet, including development of the initial suite of protocols for the Arpanet, the creation of the RFC series of documents, and multiple involvements in the IETF, ISOC and ICANN organizations. PROFESSIONAL EXPERIENCE BBQ Group 2018-present Founder, leader Development of framework and model for expressing possible, desired and existing registration data directory services policies governing collection, labeling and responses to authorized requests. Shinkuro, Inc., Bethesda, MD 2002-present Co-founder, Chief Executive Officer Development of information-sharing, collaboration and related tools for peer-to-peer cooperative work and inter-platform information management. Coordination of deployment of the DNS security protocol, DNSSEC, throughout the Internet. Longitude Systems, Inc., Chantilly, VA 1999-2001 Co-founder, Chief Executive Officer Development and sale of infrastructure tools for ISPs. Overall direction and management of the company including P&L responsibility, funding, marketing, and technical direction. Executive DSL, LLC, Bethesda, MD 1999-2001 Founder, Chief Executive Officer Creation and operation of DSL-based ISP using Covad and Bell Atlantic DSL circuits. -

Of States and Borders on the Internet: the Role of Domain Name Extensions in Expressions of Nationalism Online
Of States and Borders on the Internet: The role of domain name extensions in expressions of nationalism online Irina Shklovski, IT University of Copenhagen David Struthers, Carnegie Mellon University Abstract The space on the internet is easily traversable and state boundaries in the form of domain extensions can be crossed with no more effort than a click of a mouse. Yet, what might such traversals of imagined state boundaries on the internet mean to the people doing the traversing? This question is especially relevant when considering people from Kazakhstan, a country where notions of statehood and nationalism are contested and are in the process of being renegotiated. Results presented here suggest that residents of Kazakhstan are acutely aware of national boundary traversals as they navigate the internet. The naming of a state-controlled space on the internet, through the use of ccTLDs, does in fact matter to the average user. Citizens of Kazakhstan often identified their activity on the internet as happening within or outside the space of the state to which they felt allegiance and attachment. We argue that naming matters for the creation of not only imagined communities online but also for individual expressions of nationalism on the internet. Keywords: Nationalism, ethnic identity, democracy, internet use Introduction The space of the internet is easily traversable and most average users are able to cross state boundaries with no more effort than a click of a mouse, sometimes without even knowing that they are doing so (Johnson & Post 1996). Political science and policy scholars have written about this ease of state border traversals online in both concerned and exaulted terms, ranging from evaluations of censorship and state control to promises of the withering of the state. -

List of Internet Pioneers
List of Internet pioneers Instead of a single "inventor", the Internet was developed by many people over many years. The following are some Internet pioneers who contributed to its early development. These include early theoretical foundations, specifying original protocols, and expansion beyond a research tool to wide deployment. The pioneers Contents Claude Shannon The pioneers Claude Shannon Claude Shannon (1916–2001) called the "father of modern information Vannevar Bush theory", published "A Mathematical Theory of Communication" in J. C. R. Licklider 1948. His paper gave a formal way of studying communication channels. It established fundamental limits on the efficiency of Paul Baran communication over noisy channels, and presented the challenge of Donald Davies finding families of codes to achieve capacity.[1] Charles M. Herzfeld Bob Taylor Vannevar Bush Larry Roberts Leonard Kleinrock Vannevar Bush (1890–1974) helped to establish a partnership between Bob Kahn U.S. military, university research, and independent think tanks. He was Douglas Engelbart appointed Chairman of the National Defense Research Committee in Elizabeth Feinler 1940 by President Franklin D. Roosevelt, appointed Director of the Louis Pouzin Office of Scientific Research and Development in 1941, and from 1946 John Klensin to 1947, he served as chairman of the Joint Research and Development Vint Cerf Board. Out of this would come DARPA, which in turn would lead to the ARPANET Project.[2] His July 1945 Atlantic Monthly article "As We Yogen Dalal May Think" proposed Memex, a theoretical proto-hypertext computer Peter Kirstein system in which an individual compresses and stores all of their books, Steve Crocker records, and communications, which is then mechanized so that it may Jon Postel [3] be consulted with exceeding speed and flexibility. -

Internet Governance: ! Where Are We Now?
Internet Governance: ! Where Are We Now? Feb 24, 1999 Scott Bradner Harvard University [email protected] gov - 1 Internet Realities ◆ once a toy, now infrastructure ◆ thousands of Internet service providers (ISPs) ◆ hundreds of exchange points between ISPs ◆ little government money some support for basic research, but not operations (US anyway) ◆ no one “runs” it gov - 2 Is anyone in control? ◆ no (well mostly no) no dominant provider trans-border so no single government no useful industry group ◆ standards group “closest thing to governance” ( The Gordian Knot ) Internet Engineering Task Force (IETF) but that is not governance! gov - 3 Internet Engineering Task Force - IETF ◆ develops Internet “standards” not “standards” in the ISO / ITU / ANSI sense standards in the ‘lots of people use it’ sense ◆ does little policy technology does dictate some policy - e.g RFC 2050 required good security in IPv6 ◆ international, non-member organization ◆ IETF is the standards creation part of the Internet Society (ISOC) gov - 4 IETF, contd. ◆ now working in the same area as “traditional” standards organizations result of “convergence” everything over IP (the Internet Protocol) competing standards in some cases cooperation in others ◆ technical part of the Internet now runs under IETF rules not all that unhappy to be rid of the responsibility gov - 5 What does governance mean in the Internet context? ◆ governance means answering two questions Who says who makes the rules? Who says who pays for what? ◆ easy in most current technology areas railroad regulations, -
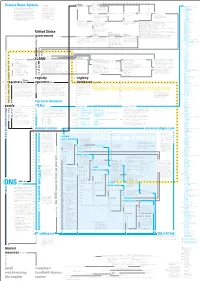
Domain Name System Concept
8 originally chartered standards charters 0 Concept Map organizations include ISoc members form 243 active ccTLDs Domain Name System rely on .ac Ascension Island (licensed) 28 Internet Society (ISoc) is a professional .ad Andorra A concept map is a web of terms. Verbs membership society with more than 150 This diagram is a model of the Domain .ae United Arab Emirates connect nouns to form propositions. organizations and 11,000 individual mem- .af Afghanistan 27 Name System (DNS), a system vital to the Groups of propositions form larger struc- bers from over 182 countries. tures. Examples and details accompany .ag Antigua and Barbuda smooth operation of the Internet. The goal most terms. More important terms re- .ai Anguilla of the diagram is to explain what DNS ceive visual emphasis; less important 11 .al Albania terms, details, and examples are in gray. IETF sponsors working groups are managed by IESG decisions can be appealed to IAB provides advice to IANA functions were moved to .am Armenia is, how it works, and how it’s governed. Terms related to names and addresses write approves .an Netherlands Antilles The diagram knits together many facts (the heart of DNS) are in blue. Terms Internet Engineering Task Force (IETF) Internet Engineering Steering Internet Architecture Board (IAB) Internet Assigned Numbers .ao Angola followed by a number link to terms pre- is a voluntary, non-commercial organization Group (IESG) Authority (IANA) originally handled .aq Antarctica about DNS in hopes of presenting a com- ceded by the same number. comprised of individuals concerned with the many of the functions that are now 626,000 .ar Argentina prehensive picture of the system and the evolution of the architecture and operation ICANN’s responsibility.