Single Instance Storage in Windows 2000 1. Introduction
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

11.7 the Windows 2000 File System
830 CASE STUDY 2: WINDOWS 2000 CHAP. 11 11.7 THE WINDOWS 2000 FILE SYSTEM Windows 2000 supports several file systems, the most important of which are FAT-16, FAT-32, and NTFS (NT File System). FAT-16 is the old MS-DOS file system. It uses 16-bit disk addresses, which limits it to disk partitions no larger than 2 GB. FAT-32 uses 32-bit disk addresses and supports disk partitions up to 2 TB. NTFS is a new file system developed specifically for Windows NT and car- ried over to Windows 2000. It uses 64-bit disk addresses and can (theoretically) support disk partitions up to 264 bytes, although other considerations limit it to smaller sizes. Windows 2000 also supports read-only file systems for CD-ROMs and DVDs. It is possible (even common) to have the same running system have access to multiple file system types available at the same time. In this chapter we will treat the NTFS file system because it is a modern file system unencumbered by the need to be fully compatible with the MS-DOS file system, which was based on the CP/M file system designed for 8-inch floppy disks more than 20 years ago. Times have changed and 8-inch floppy disks are not quite state of the art any more. Neither are their file systems. Also, NTFS differs both in user interface and implementation in a number of ways from the UNIX file system, which makes it a good second example to study. NTFS is a large and complex system and space limitations prevent us from covering all of its features, but the material presented below should give a reasonable impression of it. -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

When Windows 2000 Or Windows Server 2003 Is Introduced
IMPORTANT INFORMATION FOR PRIMERGY CUSTOMERS July 11th, 2007 FUJITSU, LTD. NOTICE: Any server using an Intel Xeon 7100 or higher model CPU and has either Windows 2000, Windows 2000 Server, or Windows 2003 Server installed may encounter a “blue screen.” The problem occurs when the operating system running on a computer with a fast processor and a large L3 cache encounters a timing problem with asynchronous hardware. Although Fujitsu has not received any reports of this problem to date, there is a possibility that PRIMERGY server products may be affected. Problem: Any computer running any edition of Windows 2000, Windows 2000 Server, or Windows 2003 with an Intel Xeon processor (model 7100 or higher) that utilizes a large L3 cache may generate a “blue screen.” An error similar to: STOP 0x0000008E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED or STOP 0x0000001E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED may be displayed with Windows 2003-based and Windows 2000-based computers, respectively. Affected Operating Systems: Microsoft® Windows® 2000 Server Microsoft® Windows® 2000 Advanced Server Microsoft® Windows Server® 2003, Standard Edition (*) Microsoft® Windows Server® 2003, Enterprise Edition (*) (*)This problem has been corrected in Service Pack 1 for Windows Server 2003. Therefore Windows 2003 Server SP1 is not affected by this problem. Affected Fujitsu PRIMERGY models: The following models use Intel Xeon 7100 or higher processors. PRIMERGY Models, Product Codes, and CPU z PRIMERGY RX600 S3 (SAS), Product codes PGR603D* and PGR603B* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) z PRIMERGY RX600 S3, Product codes PGR6038* and PGR6036* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) * Changes by type. -
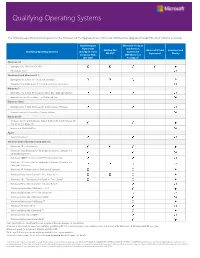
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 2000 Accessibility Options
© 2004 Microsoft Corporation Step By Step Tutorials for Microsoft® Windows 2000 Accessibility Options Step by Step Tutorials for Microsoft Windows 2000 Accessibility Options Table of Contents Overview .................................................................................................................................. 4 Using the Accessibility Wizard ............................................................................................... 6 Opening Accessibility Wizard ............................................................................................... 7 Changing the Font Size of Text on the Screen ...................................................................... 9 Switching to a Lower Screen Resolution to Increase the Size of Items on the Screen ....... 10 Changing the Size of Items on the Screen ........................................................................... 11 Disabling Personalized Menus ............................................................................................ 13 Setting Options for People Who Are Blind or Have Difficulty Seeing Things on the Screen ............................................................................................................................................. 14 Setting Options for People Who Are Deaf or Have Difficulty Hearing Sounds from the Computer ............................................................................................................................. 16 Setting Options for People Who Have Difficulty Using the Keyboard -

Forceware Release 50 Graphics Drivers User’S Guide
nViewGuide_.book Page 1 Monday, October 20, 2003 4:31 PM ForceWare Release 50 Graphics Drivers User’s Guide Version 52.16 for Windows NVIDIA Corporation October 2003 (v0.3) nViewGuide_.book Page 2 Monday, October 20, 2003 4:31 PM NVIDIA Display Properties User’s Guide Published by NVIDIA Corporation 2701 San Tomas Expressway Santa Clara, CA 95050 Copyright © 2003 NVIDIA Corporation. All rights reserved. This software may not, in whole or in part, be copied through any means, mechanical, electromechanical, or otherwise, without the express permission of NVIDIA Corporation. Information furnished is believed to be accurate and reliable. However, NVIDIA assumes no responsibility for the consequences of use of such information nor for any infringement of patents or other rights of third parties, which may result from its use. No License is granted by implication or otherwise under any patent or patent rights of NVIDIA Corporation. Specifications mentioned in the software are subject to change without notice. NVIDIA Corporation products are not authorized for use as critical components in life support devices or systems without express written approval of NVIDIA Corporation. NVIDIA, the NVIDIA logo, Accuview Antialiasing, Detonator, Digital Vibrance Control, GeForce, nForce, nView, NVKeystone, PowerMizer, Quadro, RIVA, TNT, TNT2, TwinView, and Vanta are registered trademarks or trademarks of NVIDIA Corporation in the United States and/or other countries. International Color Consortium and the ICC logo are registered trademarks of the International Color Consortium. Intel and Pentium are registered trademarks of Intel. DirectX, Microsoft, Microsoft Internet Explorer logo, Outlook, PowerPoint, Windows, Windows logo, Windows NT, and/or other Microsoft products referenced in this guide are either registered trademarks or trademarks of Microsoft Corporation in the U.S. -
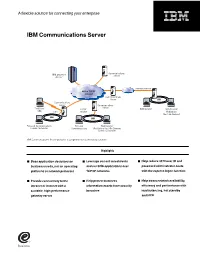
IBM Communications Server
A flexible solution for connecting your enterprise IBM Communications Server ^ Communications IBM Server zSeriesTM Internet/extranet SNA or TCP/IP intranet Communications Server LAN Communications Server Communications Server Traditional TCP/IP Web browser Web browser SNA SNA intranet WebSphere Host On-Demand LAN LAN Personal Communications Personal Web browser Screen Customizer Communications WebSphere Host On-Demand Screen Customizer IBM Communications Server provides a comprehensive connectivity solution. Highlights ■ Base application decisions on ■ Leverage current investments ■ Help reduce 3270 user ID and business needs, not on operating and run SNA applications over password administrator costs platforms or network protocols TCP/IP networks with the express logon function ■ Provide connectivity to the ■ Help protect business ■ Help boost network availability, intranet or Internet with a information assets from security efficiency and performance with scalable, high-performance breaches load balancing, hot standby gateway server and HPR As your business needs grow, place, while making the transition at applications over existing SNA chances are, so will your network. your own pace. IBM Communications networks without adding a separate Explosive growth and constant change Server can connect your employees, TCP/IP network. And you can extend in the information management and customers and trading partners to SNA applications to TCP/IP users delivery arena call for versatile the information and applications they without the addition of a separate technologies to meet your company’s need, independent of the underlying SNA network. growing needs. IBM Communications network. Designed to meet your Server meets the challenge—offering company’s growing e-business needs, Reliability and flexibility a comprehensive package of IBM Communications Server provides IBM Communications Server also enterprise networking solutions to fast, efficient ways to extend data to works as a Telnet server, providing effectively connect your employees, Web users. -

Win Xp Pe Iso Download
Win Xp Pe Iso Download 1 / 4 Win Xp Pe Iso Download 2 / 4 3 / 4 Download Files. Download PEbuilder 3.1.10 File: Download PEbuilder 3.1.10 File. BartPE Iso WINXP Emulated Version 155MB: .... To start working with WinPE, download and install both the Windows ... To learn how to create a bootable WinPE CD, DVD, ISO, or VHD, see .... A tutorial on installing BartPE onto a bootable USB drive. ... but instead of going straight into the BartPE OS, it loaded the BartPE ISO file into the ... Secondly, download Microsoft's Windows Server 2003 SP1 installation file (this can ... This utility has the ability to properly format a USB disk & install a Windows XP boot sector.. Jump to Boot WinPE/BartPE from an ISO file - Download firadisk.gz from the Beta ... For example, for the Avast BartPE ISO you can use a .... Download BartPE builder from http://www.nu2.nu/pebuilder/ ... When it's done building, image file "c:\pebuilder\pebuilder.iso" should be created properly.. Use Windows 7/XP ISO File or DVD to Create Bootable Install USB Drive ... it also allows you transfer Windows PE( Windows XP / Windows 7 / Vista / 2003 / 2008 ) to usb pen drive in a few clicks. ... Download it from softpedia.. Here we show you 5 Windows PE based boot discs to help technicians and ... disc is fully automated including the downloading of the Windows ISO image file.. 1.1 USB Drive; 1.2 BIOS/UEFI configuration; 1.3 ISO image ... If not, download BartPE; The original CD of Windows XP Professional, not a Windows XP Home ... -

Migrating from Windows 2000 to Windows Server 2003
23 0672326671 CH17 4/15/04 10:56 AM Page 463 CHAPTER 17 IN THIS CHAPTER •Windows Server 2003 Migrating from Migration Overview • Beginning the Migration Windows 2000 to Process Windows Server 2003 • Upgrading a Single Member Server • Upgrading a Windows 2000 Active Directory Forest Windows Server 2003 • Upgrading Separate AD Migration Overview Forests to a Single Forest In many ways, a migration from Windows 2000 to Windows Using Mixed-Mode Domain Server 2003 is more of a service pack upgrade than a major Redirect migration scenario. The differences between the operating • Consolidating and Migrating systems are more evolutionary than revolutionary, and there Domains Using the Active subsequently are fewer design considerations than in upgrades from the NT 4.0 operating system. Directory Migration Tool v2.0 That said, several immediate improvements to the operating • Consolidating a Windows system can be realized through migration to Windows Server 2000 Domain to a Windows 2003, whether by migrating all servers immediately or by Server 2003 Domain Using using a slow, phased approach. Improvements to Active ADMT v2.0 Directory (AD), such as the ability to rename domains and • Best Practices greater scalability, provide incentive for Windows 2000 Active Directory environments to begin migration. Standalone server improvements such as Terminal Services, File and Print Server improvements, Automated Server Recovery, and many more also serve to encourage migrations. This chapter focuses on the planning, strategy, and logistics of migration from Windows 2000 to Windows Server 2003. In addition, specialized procedures such as using Mixed-Mode Domain Redirect and migrating using the Active Directory Migration Tool (ADMT) are described, and step-by-step instructions complement these processes. -

Review NTFS Basics
Australian Journal of Basic and Applied Sciences, 6(7): 325-338, 2012 ISSN 1991-8178 Review NTFS Basics Behzad Mahjour Shafiei, Farshid Iranmanesh, Fariborz Iranmanesh Bardsir Branch, Islamic Azad University, Bardsir, Iran Abstract: The Windows NT file system (NTFS) provides a combination of performance, reliability, and compatibility not found in the FAT file system. It is designed to quickly perform standard file operations such as read, write, and search - and even advanced operations such as file-system recovery - on very large hard disks. Key words: Format, NTFS, Volume, Fat, Partition INTRODUCTION Formatting a volume with the NTFS file system results in the creation of several system files and the Master File Table (MFT), which contains information about all the files and folders on the NTFS volume. The first information on an NTFS volume is the Partition Boot Sector, which starts at sector 0 and can be up to 16 sectors long. The first file on an NTFS volume is the Master File Table (MFT). The following figure illustrates the layout of an NTFS volume when formatting has finished. Fig. 5-1: Formatted NTFS Volume. This chapter covers information about NTFS. Topics covered are listed below: NTFS Partition Boot Sector NTFS Master File Table (MFT) NTFS File Types NTFS File Attributes NTFS System Files NTFS Multiple Data Streams NTFS Compressed Files NTFS & EFS Encrypted Files . Using EFS . EFS Internals . $EFS Attribute . Issues with EFS NTFS Sparse Files NTFS Data Integrity and Recoverability The NTFS file system includes security features required for file servers and high-end personal computers in a corporate environment. -

Unit 5 Windows 2000/XP History, and Data Management
Unit 5 Windows 2000/XP History, and Data Management Copyright © 2002 Heathkit Company, Inc. All rights reserved. Microsoft Windows98 Microsoft WindowsMe Microsoft Windows 2000 Professional Microsoft WindowsXP 2 Windows 2000/XP or Windows 9x (95/98/Me)? Windows 9x Windows 2000/XP Runs on today’s Runs on “nearly any hardware, doesn’t run old hardware” well or at all on marginal hardware Secure, more difficult to Open, easy to configure configure Supports lots of Device support somewhat devices limited, so far 3 Windows XP or Windows 9x? If you need: Choose: Reliable, solid security Windows 2000/XP “Crash-proof” system Windows 2000/XP Support for older/slower Windows 9x machines Easy setup and configuration Windows 9x Support for that older scanner, Windows 9x CD Writer, NIC, Video, etc. 4 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 5 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 6 The TheWindows Windows Business Universe Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 7 Windows XP Flavors • Windows XP Professional • Windows XP Home • Windows 2003 Server • Windows 2003 Enterprise Server • Windows 2003 Datacenter Server 8 Windows Package Types • Upgrade • Full Version -

Systems Administration Guidance for Securing Windows 2000
Special Publication 800-43 Systems Administration Guidance for Securing Microsoft Windows 2000 Professional System Recommendations of the National Institute of Standards and Technology Murugiah Souppaya Anthony Harris Mark McLarnon Nikolaos Selimis This page intentionally left blank NIST Special Publication 800-43 Systems Administration Guidance for Securing Microsoft Windows 2000 Professional System Recommendations of the National Institute of Standards and Technology Send Comments to [email protected] C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 November 2002 U.S. Department of Commerce Donald L. Evans, Secretary Technology Administration Phillip J. Bond, Under Secretary for Technology National Institute of Standards and Technology Arden L. Bement, Jr., Director This page intentionally left blank Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-43 Natl.