Windows 2000 Services That Can Be Disabled
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

RAID, LVM, WSS, Verschlüsselung)
Hochschule Wismar University of Applied Sciences Technology, Business and Design Fakultät für Ingenieurwissenschaften, Bereich EuI Projektarbeit Aufbereitung besonderer Speicherkonfigurationen als analysefähiges Material (RAID, LVM, WSS, Verschlüsselung) Eingereicht am: 6. Juli 2019 von: Melanie Wetzig Sven Lötgering Tom Gertenbach Stefan Depping Inhaltsverzeichnis Inhaltsverzeichnis 1 Vorüberlegungen4 1.1 Motivation und Zielstellung.......................4 1.2 Anforderung an den Ermittlungsprozess.................4 1.3 Einordnung in Ermittlungsprozess....................6 1.4 Write-Blocker...............................6 1.5 Software..................................7 1.5.1 Rohdatenformat (RAW).....................7 1.5.2 Expert Witness Format (EWF).................8 1.5.3 Advanced Forensic Format (AFF)................8 1.5.4 Xmount..............................8 2 Rechtliche Betrachtung9 2.1 Einleitung.................................9 2.2 Private Ermittlungen........................... 10 2.3 Behördliche Ermittlungen........................ 11 2.4 Zusammenfassung............................. 11 3 Speichermedien 13 3.1 Einleitung................................. 13 3.2 Magnetspeicher.............................. 13 3.2.1 Speicherung auf einer HDD................... 14 3.2.2 Löschen von Daten auf einer HDD............... 15 3.2.3 Forensische Relevanz....................... 15 3.3 Flash-Speicher............................... 15 3.3.1 Speicherung auf einer Solid-State-Drive (SSD)......... 16 3.3.2 Löschen von Daten auf einer SSD............... -

SLDXA /T /L1 – SLX Component List
SLDXA /T /L1 – SLX Component List SLDXA.exe ver 1.0 Copyright (c) 2004-2006 SJJ Embedded Micro Solutions, LLC All Rights Reserved SLXDiffC.exe ver 2.0 / SLXtoTXTC.exe ver 2.0 www.sjjmicro.com Processing... File1 to TXT file. Opening XSL File Reading RTF for final conversion F:\SLXTEST\LOCKDOWN_DEMO2.SLX has the following Components Total Count is: 577 -------------------------------------------------- .NET Framework 1.1 - Security Update KB887998 Accessibility Control Panel Accessibility Core ACPI Fixed Feature Button Active Directory Service Interface (ADSI) Core Active Directory Service Interface (ADSI) LDAP Provider Active Directory Service Interface (ADSI) Windows NT Provider Active Template Library (ATL) Add Hardware Control Panel Add/Remove Programs Control Panel Administration Support Tools Administrator Account Advanced Configuration and Power Interface (ACPI) PC Analog TV Application Compatibility Core Audio Codecs Audio Control Panel Base Component Base Performance Counters Base Support Binaries CD-ROM Drive Certificate Request Client & Certificate Autoenrollment Certificate User Interface Services Class Install Library - Desk Class Install Library - Mdminst Class Install Library - Mmsys Class Install Library - Msports Class Install Library - Netcfgx Class Install Library - Storprop Class Install Library - System Devices Class Installer - Computer Class Installer - Disk drives Class Installer - Display adapters Class Installer - DVD/CD-ROM drives Class Installer - Floppy disk controllers Class Installer - Floppy disk drives -

Active @ UNDELETE Users Guide | TOC | 2
Active @ UNDELETE Users Guide | TOC | 2 Contents Legal Statement..................................................................................................4 Active@ UNDELETE Overview............................................................................. 5 Getting Started with Active@ UNDELETE........................................................... 6 Active@ UNDELETE Views And Windows......................................................................................6 Recovery Explorer View.................................................................................................... 7 Logical Drive Scan Result View.......................................................................................... 7 Physical Device Scan View................................................................................................ 8 Search Results View........................................................................................................10 Application Log...............................................................................................................11 Welcome View................................................................................................................11 Using Active@ UNDELETE Overview................................................................. 13 Recover deleted Files and Folders.............................................................................................. 14 Scan a Volume (Logical Drive) for deleted files..................................................................15 -

11.7 the Windows 2000 File System
830 CASE STUDY 2: WINDOWS 2000 CHAP. 11 11.7 THE WINDOWS 2000 FILE SYSTEM Windows 2000 supports several file systems, the most important of which are FAT-16, FAT-32, and NTFS (NT File System). FAT-16 is the old MS-DOS file system. It uses 16-bit disk addresses, which limits it to disk partitions no larger than 2 GB. FAT-32 uses 32-bit disk addresses and supports disk partitions up to 2 TB. NTFS is a new file system developed specifically for Windows NT and car- ried over to Windows 2000. It uses 64-bit disk addresses and can (theoretically) support disk partitions up to 264 bytes, although other considerations limit it to smaller sizes. Windows 2000 also supports read-only file systems for CD-ROMs and DVDs. It is possible (even common) to have the same running system have access to multiple file system types available at the same time. In this chapter we will treat the NTFS file system because it is a modern file system unencumbered by the need to be fully compatible with the MS-DOS file system, which was based on the CP/M file system designed for 8-inch floppy disks more than 20 years ago. Times have changed and 8-inch floppy disks are not quite state of the art any more. Neither are their file systems. Also, NTFS differs both in user interface and implementation in a number of ways from the UNIX file system, which makes it a good second example to study. NTFS is a large and complex system and space limitations prevent us from covering all of its features, but the material presented below should give a reasonable impression of it. -

Veeam Backup 7 Release Notes
VEEAM BACKUP & REPLICATION 7.0 RELEASE NOTES This Release Notes document provides last-minute information about Veeam Backup & Replication 7.0, including system requirements, installation and upgrade procedure, as well as relevant information on technical support, documentation, online resources and so on. The current version of Veeam Backup & Replication 7.0 is available for download at: http://www.veeam.com/vmware-esx-backup/download.html starting from August 15, 2013. See next: • System Requirements • Known Issues • Installing Veeam Backup & Replication • Uninstalling Veeam Backup & Replication • Upgrading Veeam Backup & Replication • Licensing • Updating Veeam Backup & Replication License • Technical Documentation References • Technical Support • Contacting Veeam Software 1 | Veeam Backup & Replication 7.0.0.690 | RELEASE NOTES System Requirements VMware Infrastructure Platforms • vSphere 5.0, 5.1 • vSphere 4.x • Infrastructure 3.5 (VI3.5) Hosts • ESXi 5.0, 5.1 • ESX(i) 4.x • ESX(i) 3.5 Software • vCenter Server 5.0, 5.1 (optional) • vCenter Server 4.x (optional) • Virtual Center 2.5 (optional) VMware Virtual Machines Virtual Hardware • All types of virtual hardware are supported. • Virtual machines with disks engaged in SCSI bus sharing are not supported, because VMware does not support snapshotting such VMs. • RDM virtual disks in physical mode, Independent disks and disks connected via in-guest iSCSI initiator are not supported, and are skipped from processing automatically. OS • All operating systems supported by VMware. • Application-aware -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Jim Allchin on Longhorn, Winfs, 64-Bit and Beyond Page 34 Jim
0805red_cover.v5 7/19/05 2:57 PM Page 1 4 Scripting Solutions to Simplify Your Life Page 28 AUGUST 2005 WWW.REDMONDMAG.COM MrMr WindowsWindows Jim Allchin on Longhorn, WinFS, 64-Bit and Beyond Page 34 > $5.95 05 • AUGUST Make Room for Linux Apps Page 43 25274 867 27 Active Directory Design Disasters Page 49 71 Project1 6/16/05 12:36 PM Page 1 Exchange Server stores & PSTs driving you crazy? Only $399 for 50 mailboxes; $1499 for unlimited mailboxes! Archive all mail to SQL and save 80% storage space! Email archiving solution for internal and external email Download your FREE trial from www.gfi.com/rma Project1 6/16/05 12:37 PM Page 2 Get your FREE trial version of GFI MailArchiver for Exchange today! GFI MailArchiver for Exchange is an easy-to-use email archiving solution that enables you to archive all internal and external mail into a single SQL database. Now you can provide users with easy, centralized access to past email via a web-based search interface and easily fulfill regulatory requirements (such as the Sarbanes-Oxley Act). GFI MailArchiver leverages the journaling feature of Exchange Server 2000/2003, providing unparalleled scalability and reliability at a competitive cost. GFI MailArchiver for Exchange features Provide end-users with a single web-based location in which to search all their past email Increase Exchange performance and ease backup and restoration End PST hell by storing email in SQL format Significantly reduce storage requirements for email by up to 80% Comply with Sarbanes-Oxley, SEC and other regulations. -

Acronis® Disk Director® 12 User's Guide
User Guide Copyright Statement Copyright © Acronis International GmbH, 2002-2015. All rights reserved. "Acronis", "Acronis Compute with Confidence", "Acronis Recovery Manager", "Acronis Secure Zone", Acronis True Image, Acronis Try&Decide, and the Acronis logo are trademarks of Acronis International GmbH. Linux is a registered trademark of Linus Torvalds. VMware and VMware Ready are trademarks and/or registered trademarks of VMware, Inc. in the United States and/or other jurisdictions. Windows and MS-DOS are registered trademarks of Microsoft Corporation. All other trademarks and copyrights referred to are the property of their respective owners. Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder. Distribution of this work or derivative work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder. DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. Third party code may be provided with the Software and/or Service. The license terms for such third-parties are detailed in the license.txt file located in the root installation directory. You can always find the latest up-to-date list of the third party code and the associated license terms used with the Software and/or Service at http://kb.acronis.com/content/7696 Acronis patented technologies Technologies, used in this product, are covered and protected by one or more U.S. -

When Windows 2000 Or Windows Server 2003 Is Introduced
IMPORTANT INFORMATION FOR PRIMERGY CUSTOMERS July 11th, 2007 FUJITSU, LTD. NOTICE: Any server using an Intel Xeon 7100 or higher model CPU and has either Windows 2000, Windows 2000 Server, or Windows 2003 Server installed may encounter a “blue screen.” The problem occurs when the operating system running on a computer with a fast processor and a large L3 cache encounters a timing problem with asynchronous hardware. Although Fujitsu has not received any reports of this problem to date, there is a possibility that PRIMERGY server products may be affected. Problem: Any computer running any edition of Windows 2000, Windows 2000 Server, or Windows 2003 with an Intel Xeon processor (model 7100 or higher) that utilizes a large L3 cache may generate a “blue screen.” An error similar to: STOP 0x0000008E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED or STOP 0x0000001E(parameter1, parameter2, parameter3, parameter4) KERNEL_MODE_EXCEPTION_NOT_HANDLED may be displayed with Windows 2003-based and Windows 2000-based computers, respectively. Affected Operating Systems: Microsoft® Windows® 2000 Server Microsoft® Windows® 2000 Advanced Server Microsoft® Windows Server® 2003, Standard Edition (*) Microsoft® Windows Server® 2003, Enterprise Edition (*) (*)This problem has been corrected in Service Pack 1 for Windows Server 2003. Therefore Windows 2003 Server SP1 is not affected by this problem. Affected Fujitsu PRIMERGY models: The following models use Intel Xeon 7100 or higher processors. PRIMERGY Models, Product Codes, and CPU z PRIMERGY RX600 S3 (SAS), Product codes PGR603D* and PGR603B* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) z PRIMERGY RX600 S3, Product codes PGR6038* and PGR6036* ¾ Dual Core Intel® Xeon® Processor 7140M (3.40GHz)/7120M (3GHz) * Changes by type. -
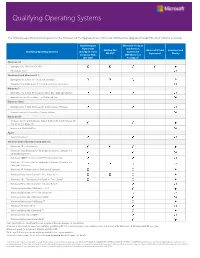
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 2000 Accessibility Options
© 2004 Microsoft Corporation Step By Step Tutorials for Microsoft® Windows 2000 Accessibility Options Step by Step Tutorials for Microsoft Windows 2000 Accessibility Options Table of Contents Overview .................................................................................................................................. 4 Using the Accessibility Wizard ............................................................................................... 6 Opening Accessibility Wizard ............................................................................................... 7 Changing the Font Size of Text on the Screen ...................................................................... 9 Switching to a Lower Screen Resolution to Increase the Size of Items on the Screen ....... 10 Changing the Size of Items on the Screen ........................................................................... 11 Disabling Personalized Menus ............................................................................................ 13 Setting Options for People Who Are Blind or Have Difficulty Seeing Things on the Screen ............................................................................................................................................. 14 Setting Options for People Who Are Deaf or Have Difficulty Hearing Sounds from the Computer ............................................................................................................................. 16 Setting Options for People Who Have Difficulty Using the Keyboard