Analysis of Ios 9.3.3 Jailbreak & Security Enhancements of Ios 10
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apple Business Manager Overview Overview
Getting Started Guide Apple Business Manager Overview Overview Contents Apple Business Manager is a web-based portal for IT administrators to deploy Overview iPhone, iPad, iPod touch, Apple TV, and Mac all from one place. Working Getting Started seamlessly with your mobile device management (MDM) solution, Apple Configuration Resources Business Manager makes it easy to automate device deployment, purchase apps and distribute content, and create Managed Apple IDs for employees. The Device Enrollment Program (DEP) and the Volume Purchase Program (VPP) are now completely integrated into Apple Business Manager, so organizations can bring together everything needed to deploy Apple devices. These programs will no longer be available starting December 1, 2019. Devices Apple Business Manager enables automated device enrollment, giving organizations a fast, streamlined way to deploy corporate-owned Apple devices and enroll in MDM without having to physically touch or prepare each device. • Simplify the setup process for users by streamlining steps in Setup Assistant, ensuring that employees receive the right configurations immediately upon activation. IT teams can now further customize this experience by providing consent text, corporate branding or modern authentication to employees. • Enable a higher level of control for corporate-owned devices by using supervision, which provides additional device management controls that are not available for other deployment models, including non-removable MDM. • More easily manage default MDM servers by setting a default server that’s based on device type. And you can now manually enroll iPhone, iPad, and Apple TV using Apple Configurator 2, regardless of how you acquired them. Content Apple Business Manager enables organizations to easily buy content in volume. -
Iso 10 Download Create an ISO File for Windows 10
iso 10 download Create an ISO file for Windows 10. Unlike in previous versions of Windows, you’ll need to use the media creation tool to create an ISO file to install Windows 10. Make sure you have a license to install Windows 10, and then follow these steps: On the Windows 10 download page, download the media creation tool by selecting Download tool now , then run the tool. In the tool, select Create installation media (USB flash drive, DVD, or ISO) for another PC > Next . Select the language, architecture, and edition of Windows, you need and select Next . Select ISO file > Next , and the tool will create your ISO file for you. To use the ISO file as a backup for your PC or on another PC, burn it onto a DVD. Iso 10 download. Final iOS 10 / 10.3 / 10.2.1 / 10.2 / 10.1.1 / 10.1 download IPSW links are available to install on iPhone 7, 7 Plus, 6s, 6s Plus, 6, 6 Plus, SE, 5s, 5c, 5, iPad 4 and over, and iPod touch 6th-generation. This final build is available to everyone worldwide. iOS 10 is Apple’s latest major update for iPhone, iPad and iPod touch devices, bringing in a number of new features to one of the world’s most popular mobile platform. For a full list of features on what’s new in iOS 10, you can check out our separate detailed post on it here. The following guide will help you download and install iOS 10 / 10.2.1 / 10.2 / 10.1.1 / 10.1 / 10.0.1 / 10.0.2 / 10.0.3 on your compatible iPhone, iPad or iPod touch device the right way, covering both OTA update method as well as clean install method using iTunes. -

Differential Privacy Overview
Differential Privacy There are situations where Apple can improve the user experience by getting insight from what many of our users are doing, for example: What new words are trending and might make the most relevant suggestions? What websites have problems that could affect battery life? Which emoji are chosen most often? The challenge is that the data which could drive the answers to those questions—such as what the users type on their keyboards—is personal. A privacy-preserving system Apple has adopted and further developed a technique known in the academic world as local differential privacy to do something really exciting: gain insight into what many Apple users are doing, while helping to preserve the privacy of individual users. It is a technique that enables Apple to learn about the user community without learning about individuals in the community. Differential privacy transforms the information shared with Apple before it ever leaves the user’s device such that Apple can never reproduce the true data. The differential privacy technology used by Apple is rooted in the idea that statistical noise that is slightly biased can mask a user’s individual data before it is shared with Apple. If many people are submitting the same data, the noise that has been added can average out over large numbers of data points, and Apple can see meaningful information emerge. Differential privacy is used as the first step of a system for data analysis that includes robust privacy protections at every stage. The system is opt-in and designed to provide transparency to the user. -

Iphone Shortcuts (Ios
Messages (e-mail) Miscellaneous TRAINING | COACHING | SEMINARS | VIDEO Check for new mail: Pull downward on New! Press Home Button to Unlock: you now top message. need to press the Home Button instead of swiping New! Unsubscribe from email lists: at across screen to unlock your iPhone. the top of emails, you can tap “unsubscribe”, and New! Swipe Right to see “Today”: swipe right to confirm, to unsubscribe from mailing lists. left to view your “Today” view. New! Filter email: While viewing list of New! Easily Rename Folders: if you have an emails, tap “Filter” icon in bottom left corner of iPhone 6s or newer, you can use 3D touch to re- screen. Tap “Filtered by:” in bottom center to select name folders. Press and hold the folder > tap filters. “Rename”. Shake to Undo Typing: shake your iPhone to New! Search in Notifications: the “Today” view Real-World Technology Training for Modern Professionals undo text you just typed. and “Notifications” now have a Search field at the Notify Me: If you are waiting for a top of the screen to allow you to search within them response to an important e-mail, use the new “Notify New! Search iCloud Easily: your iCloud Drive Me” feature. contents are now available in “Spotlight Search” (if Quick Mail Navigation: by swiping to the right you do not want to see iCloud in Search, turn off in on a message in your inbox, you now see the option Settings. “Mark as Read/Unread”. Swipe slowly to the left and New! Take Action on a Notification: tap and see options for “Flag”, “Trash” and “More”. -

Cydia Apk Ios 10
Cydia apk ios 10 Continue Jailbreaks have been a little lacking in recent years, but today we can tell you that if you are on iOS 10 firmware, we have news of a jailbreak for you. Its called Helix jailbreak, its semi-untethered and it was brought to us by Tihmstar, a famous developer. This is a steady jailbreak and is based on a feat called V0rtex.iOS 10 firmware was supposed to be the beginning of the end for jailbreak and, for a long time, it seemed to be. Apple introduced a number of new features, including security features that for a while hindered the development of jailbreak. So, given all the security that iOS 10 includes, how does Helix jailbreak work? Helix is built using an exploit that gets around security features in iOS 10, allowing free and easy access to Cydia. It's a safe jailbreak to use, so read on to find out how to get it. Supported versions of iOS 10: The following versions of iOS 10 support cydia download :iOS 10iOS 10.0.1iOS 10.0.2iOS 10.3.1iOS 10 .3.2iOS 10.3.3iOS 10.3.4H3lix Jailbreak:Helix aka H3lix jailbreak is available on both 32-bit and 64-bit devices. Remember that it's semi-untethered so it will need reactivation whenever you restart your iPhone or iPad. Downloading is simple though so check the links to download and install Helix on either 32-bit or 64-bit devices. H3lix JailbreakYalu Jailbreak:Yalu was one of the first jailbreak tool for iOS 10 firmware. -

Details on IOS 10 Earpods Apple Watch S2 Better and Powerreserve
More Details On IOS 10, EarPods, Apple Watch S2 Better And PowerReserve 1 / 4 More Details On IOS 10, EarPods, Apple Watch S2 Better And PowerReserve 2 / 4 Contact your service provider for more details. Check apple.com/lae/watch/cellular/ for participating wireless carriers and eligibility.. watchOS 6 brings new features to Apple Watch: Activity Trends, App Store on your wrist, Cycle Tracking, and a stunning new selection of watch faces. ... It's easier than ever to access the information that matters to you. ... 6 requires iPhone 6s or later with iOS 13 or later, and one of the following Apple Watch models:.. To set up and use your Apple Watch, you need an iPhone with the latest version of iOS. watchOS 6 is compatible with Apple Watch Series 1 ... This is a list and comparison of devices designed and marketed by Apple Inc. that run a Unix-like operating system named iOS and iPadOS. The devices include ... I Love Hitler : Hitler’s Childhood More details on iOS 10, EarPods, Apple Watch S2 better and PowerReserve ... How to use Power Reserve on your Apple Watch — The Apple .... If you see a red iPhone icon on your Apple Watch, or you're trying to pair and can't find the 'i' icon, try to connect your devices again.. With Apple Watch Series 3, you can make calls, get texts, and listen to music right from ... And stay connected to the people and information you care about. ... The Breathe app can help you better manage everyday stress. ... Apple Watch Series 5 and Apple Watch Series 3 require an iPhone 6s or later with iOS 13 or later. -
Changing Email Settings on Apple's Ios 10
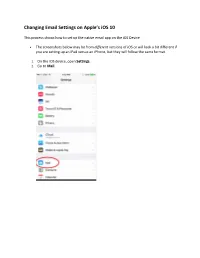
Changing Email Settings on Apple’s iOS 10 This process shows how to set up the native email app on the iOS Device. • The screenshots below may be from different versions of iOS or will look a bit different if you are setting up an iPad versus an iPhone, but they will follow the same format. 1. On the iOS device, open Settings. 2. Go to Mail. Changing the Account: 3. Click on Accounts from the main Mail window. This may show GRM or other mail apps that you use as well (Gmail, Yahoo, iCloud, etc.) 4. From the Accounts window, select the specific account for your GRM email address from this screen. 5. Verify that the Incoming Mail Server Host Name is mail.grm.net 6. Verify the Username is your FULL email address. 7. If you are viewing this document after changing your password, enter your new password in the Password field. a. If you have not changed your password since migrating to the new email platform, it is highly recommended that you change your password. For instructions on how to change your email password, go to www.grm.net/email and click on the "How to Change Your Password" link. 8. Click on the Outgoing Mail Server to verify / change the various sever settings. 9. Click on the Primary Server option for GRM.net. (It may not necessarily named a mail.grm.net) 10. From the Outgoing Mail Server settings window: o Verify this Server is marked as On. o Verify the Outgoing Mail Server Host Name is set to mail.grm.net. -
Installing Cisco Jabber on Your Ios Device
Installing Cisco Jabber on Your iOS Device In this tutorial, we will walk through installing Cisco Jabber on your iOS mobile device. What’s covered in this tutorial (click on the title to jump to the section) Installing Jabber ............................................................................................................................................ 1 Set up Cisco Jabber on Apple Watch ........................................................................................................ 5 Questions? .................................................................................................................................................... 6 Installing Jabber 1. First, open the App Store on your device. 1 Updated Wednesday, August 1, 2018 2. Search for “Cisco Jabber” and click “Get.” 3. Then tap “Install." 4. Open Jabber from your home screen. Allow for notifications, if you would like to receive them, and tap “Accept.” 2 Updated Wednesday, August 1, 2018 5. You may be prompted to read about the New Look and Feel. Swipe right on your device and tap “Get Started Now.” If you plan on making calls with Jabber, you will want to allow the app access to your microphone. 3 Updated Wednesday, August 1, 2018 6. When you are prompted to enter your username, use your NJIT email address and tap “Continue.” 7. Then, enter your UCID and password and tap “Sign In.” 4 Updated Wednesday, August 1, 2018 8. You will see the familiar Jabber menu located at the bottom of your screen. Set up Cisco Jabber on Apple Watch • If Cisco Jabber -

Say Hello to Iphone
Say hello to iPhone A quick look at iPhone This guide describes iOS 11 for: iPhone 8 Plus iPhone 8 iPhone SE iPhone 7 Plus iPhone 7 iPhone 5s iPhone 6s Plus iPhone 6s iPhone 6 Plus iPhone 6 Your features and apps may vary depending on the model of iPhone you have, and on your location, language, and carrier. Note: Apps and services that send or receive data over a cellular network may incur additional fees. Contact your carrier for information about your iPhone service plan and fees. See also Apple Support article: Identify your iPhone model Compare iPhone models website iOS Feature Availability website iPhone 8 Plus FaceTime HD camera Side button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Dual wide-angle and telephoto rear cameras Quad-LED True Tone flash See also Turn on iPhone Set up iPhone Charge and monitor the battery iPhone 8 FaceTime HD camera Side button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Rear camera Quad-LED True Tone flash See also Turn on iPhone Set up iPhone Charge and monitor the battery iPhone 7 Plus FaceTime HD camera Sleep/Wake button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Dual wide-angle and telephoto rear cameras Quad-LED True Tone flash See also Turn on iPhone Set up iPhone Charge and monitor the battery iPhone 7 FaceTime HD camera Sleep/Wake button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Rear camera Quad-LED True Tone flash -

VS-1049 Certified Iphone Apps Developer Sample Material
Certified iPhone Apps Developer Sample Material VS-1049 Certified iPhone Apps Developer 1. IOS INTRODUCTION iOS (formerly iPhone OS) is a mobile operating system created and developed by Apple Inc. exclusively for its hardware. It is the operating system that presently powers many of the company's mobile devices, including the iPhone, iPad, and iPod Touch. It is the second most popular mobile operating system globally after Android. Originally unveiled in 2007 for the iPhone, iOS has been extended to support other Apple devices such as the iPod Touch (September 2007) and the iPad (January 2010). As of January 2017, Apple's App Store contains more than 2.2 million iOS applications, 1 million of which are native for iPads. These mobile apps have collectively been downloaded more than 130 billion times. The iOS user interface is based upon direct manipulation, using multi-touch gestures. Interface control elements consist of sliders, switches, and buttons. Interaction with the OS includes gestures such as swipe, tap, pinch, and reverse pinch, all of which have specific definitions within the context of the iOS operating system and its multi-touch interface. Internal accelerometers are used by some applications to respond to shaking the device (one common result is the undo command) or rotating it in three dimensions (one common result is switching between portrait and landscape mode). Apple has been significantly praised for incorporating thorough accessibility functions into iOS, enabling users with vision and hearing disabilities to properly use its products. Major versions of iOS are released annually. The current version, iOS 11, was released on September 19, 2017. -
OMRON App Compatibility Matrix 172021.Xlsx
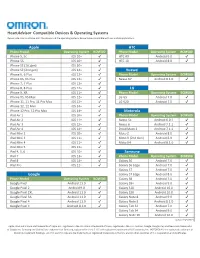
HeartAdvisor Compatible Devices & Operating Systems Please note: You must have both the device and the operating systems below to be compatible with our mobile applications. Apple HTC Phone Model Operating System BCM500 Phone Model Operating System BCM500 iPhone 5, 5c iOS 10+ ✔ HTC A9 Android 6.0 ✔ iPhone 5S iOS 10+ ✔ HTC 10 Android 8.0 ✔ iPhone SE (1st gen) iOS 10+ ✔ iPhone SE (2nd gen) iOS 14+ ✔ Huawei iPhone 6, 6 Plus iOS 12+ ✔ Phone Model Operating System BCM500 iPhone 6S, 6S Plus iOS 12+ ✔ Nexus 6P Android 8.1.0 ✔ iPhone 7, 7 Plus iOS 12+ ✔ iPhone 8, 8 Plus iOS 12+ ✔ LG iPhone X, XR iOS 11+ ✔ Phone Model Operating System BCM500 iPhone XS, XS Max iOS 12+ ✔ LG G5 Android 7.0 ✔ iPhone 11, 11 Pro, 11 Pro Max iOS 13+ ✔ LG V20 Android 7.0 ✔ iPhone 12, 12 Mini iOS 14+ ✔ iPhone 12 Pro, 12 Pro Max iOS 14+ ✔ Motorola iPad Air 1 iOS 10+ ✔ Phone Model Operating System BCM500 iPad Air 2 iOS 11+ ✔ Nexus 5x Android 6.0.1 ✔ iPad Air 3 iOS 12+ ✔ Nexus 6 Android 7.1.1 ✔ iPad Air 4 iOS 14+ ✔ Droid Maxx 2 Android 7.1.1 ✔ iPad Mini 2 iOS 10+ ✔ Moto Z Android 8.0 ✔ iPad Mini 3 iOS 11+ ✔ Moto X (2nd Gen) Android 6.0 ✔ iPad Mini 4 iOS 11+ ✔ Moto X4 Android 8.1.0 ✔ iPad Mini 5 iOS 12+ ✔ iPad 4, 5, 6 iOS 10+ ✔ Samsung iPad 7 iOS 13+ ✔ Phone Model Operating System BCM500 iPad 8 iOS 14+ ✔ Galaxy S6 Android 7.0 ✔ iPad Pro iOS 11+ ✔ Galaxy S6 Edge Android 7.0 ✔ Galaxy S7 Android 7.0 ✔ Google Galaxy S7 Edge Android 8.0 ✔ Phone Model Operating System BCM500 Galaxy S8 Android 7.0 ✔ Google Pixel Android 11.0 ✔ Galaxy S9+ Android 9.0 ✔ Google Pixel 2 Android 9.0 ✔ Galaxy S10 Android 10.0 ✔ Google Pixel 2XL Android 11.0 ✔ Galaxy S20 Android 10.0 ✔ Google Pixel 3A Android 11.0 ✔ Galaxy Note 8 Android 9.0 ✔ Google Pixel 4 Android 11.0 ✔ Galaxy Note 9 Android 8.1.0 ✔ Google Pixel C Android 8.1.0 ✔ Galaxy Tab S2 Android 7.0 ✔ Galaxy Tab S4 Android 9.0 ✔ Galaxy Note 10 Android 10.0 ✔ updated 3/5/2021 Apple, iPad and iPhone are trademarks of Apple Inc., registered in the U.S. -
Internal Structure of Ios and Building Tools for Ios Apps
International Journal Of Computer Science And Applications Vol. 6, No.2, Apr 2013 ISSN: 0974-1011 (Open Access) Available at: www.researchpublications.org Internal structure of iOS and Building tools for iOS apps Miss Priyanka V. Kanoi Miss Payal N. ingole 2nd yr Information and Technology 3rd yr Computer sc and Engineering JDIET , Yavatmal JDIET, Yavatmal [email protected] [email protected] operating system: "iPhone OS".In June 2010, Apple rebranded Abstract : iOS is world’s most advanced operating system. With iPhone OS as "iOS". The trademark "IOS" had been used by its easy-to-use interface, amazing features, and rock-solid Cisco for over a decade for its operating system, IOS, used on stability, iOS is the foundation of iPhone, iPad, and iPod touch. It its routers. To avoid any potential lawsuit, Apple licensed the is the most user friendly operating system. With better GUI "IOS" trademark from Cisco. Apple provides major updates to performance. iOS consists of four layers – cocoa touch layer, the iOS operating system approximately once a year over media layer, core service layer, core OS layer. Some of the developmental tools used for preparing iOS apps include iTunes and also, since iOS version 5.0, over the air. The latest XCODE, Instruments and developer library. With thousands of major update is iOS 6, publicly announced on June 11, 2012 apps in practically every category, iOS is the platform for the and released on September 12, 2012. Over 200 new features world’s largest collection of mobile apps. And every app starts debut in iOS 6, including Apple's new Passbook service, with the right DNA.