Mitre's Att&Ck™ Framework
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Transaction Insight Reference Manual Contents I Admin - Filters - Partner Filter
TIBCO Foresight® Transaction Insight® Reference Manual Software Release 5.2 September 2017 Two-second advantage® Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN LICENSE.PDF) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. This document contains confidential information that is subject to U.S. and international copyright laws and treaties. No part of this document may be reproduced in any form without the written authorization of TIBCO Software Inc. TIBCO and Two-Second Advantage, TIBCO Foresight EDISIM, TIBCO Foresight Instream, TIBCO Foresight Studio, and TIBCO Foresight Transaction Insight are either registered trademarks or trademarks of TIBCO Software Inc. in the United States and/or other countries. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -

INFORMATION TECHNOLOGY CONCEPTS-OPEN - REGIONAL 2019 Page 1 of 8
INFORMATION TECHNOLOGY CONCEPTS-OPEN - REGIONAL 2019 Page 1 of 8 INFORMATION TECHNOLOGY CONCEPTS (391) —OPEN EVENT— REGIONAL – 2019 DO NOT WRITE ON TEST BOOKLET TOTAL POINTS _________ (100 points) Failure to adhere to any of the following rules will result in disqualification: 1. Contestant must hand in this test booklet and all printouts. Failure to do so will result in disqualification. 2. No equipment, supplies, or materials other than those specified for this event are allowed in the testing area. No previous BPA tests and/or sample tests or facsimile (handwritten, photocopied, or keyed) are allowed in the testing area. 3. Electronic devices will be monitored according to ACT standards. No more than sixty (60) minutes testing time Property of Business Professionals of America. May be reproduced only for use in the Business Professionals of America Workplace Skills Assessment Program competition. INFORMATION TECHNOLOGY CONCEPTS-OPEN - REGIONAL 2019 Page 2 of 8 MULTIPLE CHOICE Identify the choice that best completes the statement or answers the question. Mark A if the statement is true. Mark B if the statement is false. 1. Which of the following appears on the right side of any Windows 8 screen when you move your pointer to a right corner? A. Live tile B. Memory Manager C. Charms bar D. System tray 2. Which element of the Windows 7 GUI gives windows a glassy appearance, but also consumes more hardware resources? A. Control panel B. Aero user interface C. Charms interface D. Logic interface 3. The top of a top-down hierarchical structure of subdirectories is called which of the following? A. -

Windows IR Live Forensics Cheat Sheet by Koriley Via Cheatography.Com/12660/Cs/11352
Windows IR Live Forensics Cheat Sheet by koriley via cheatography.com/12660/cs/11352/ Unusual Network Usage Windows Security & System Events To Look For Look at File Shares net view \\127.0.0.1 Security 4720 User Account Created Open Sessions with Machine net session Security 4722 User Account Enabled Session This machine has net use Security 4724 Password Reset Opened Security 4738 User Account Change NetBIOS over TCP/IP Activity nbtstat -S Security 4732 Accout Added or Removed From Group List Listening TCP and UDP Ports netstat -na Security 1102 Audit Log Cleared 5 - Continuous Scrolling every 5 netstat -na 5 System 7030 Basic Service Operations seconds System 7045 Service Was Installed netstat -naob -o flag shows process ID -b flag System 1056 DHCP Server Oddities shows executa ble System 10000 COM Functio nality Inspect Firewall rules netsh advfire wall show System 20001 Device Driver Install ation current pro file System 20002 Remote Access netsh firewall show System 20003 Service Install ation config Search for Other Startup Items Unusual Accounts Users' Autostart dir /s /b "C :\ Docu ments and Unexp ected Users in the lusrmg r.msc Folders Settings\ [user name]\ Start Menu\" Adminis tra tors Group dir /s /b "C :\ Users\ [user List Users net user name]\ Start Menu\" List Members of Admin Group net localgroup adminis tra tors Use WMIC To find wmic startup list full Start Up Programs List Domain Users net user /domain When looking at domain accounts, the command will be run on the domain control ler. A large domain may take some time - redirect to a text file to analyze: net user /domain > domainU ser s.txt By koriley Published 4th April, 2017. -

Hacking Exposed: Melting Down Memory
#RSAC SESSION ID: EXP=W04 HACKING EXPOSED: MELTING DOWN MEMORY George Kurtz Dmitri Alperovitch Elia Zaitsev Co-Founder & President/CEO Co-Founder & CTO Director CrowdStrike Inc. CrowdStrike Inc. Solutions Architecture @George_Kurtz @DAlperovitch CrowdStrike Inc. #RSAC THE HACKING EXPOSED OSCARS ARE BACK #RSAC THE NOMINEES FOR BEST TECHNIQUES ARE… #RSAC CATEGORY: CREDENTIAL THEFT DELIVERY: STRATEGIC WEB COMPROMISE USING SMB TECHNICAL BREAKDOWN #RSAC Variations of remote source Javascript + Dean Edwards Packer obfuscation Tiny image Hidden in JQuery related Javascript files #RSAC DEMO 6 REAL WORLD EXAMPLES #RSAC - Massive BERSERK BEAR credential harvesting campaign - Targeted numerous sectors — Chemical – Sept 2017 — Financial – Sept 2017 — Hospitality – Sept 2017 — Oil & Gas – April 2017 — Technology – April 2017 — Engineering – April 2017 — Education – April 2017 REAL WORLD EXAMPLES #RSAC Another variation used spear-phishing emails. Word Docs contain code that attempts to retrieve doc template from remote source over WebDAV 8 REAL WORLD EXAMPLES #RSAC - Post Harvesting Activity - Offline hash cracking - Pass the hash tools - Public facing services most vulnerable - Webmail - VPN - Remote conferencing software COUNTERMEASURES #RSAC - Implement Two-Factor Authentication (2FA) - Restrict or monitor SMB connectivity to remote servers - Robust password policies (length/duration/reuse) - Restrict or monitor remote user authentication - Leverage threat intel to track known SMB C2s #RSAC CATEGORY: WHITELISTING BYPASS DELIVERY: INSTALLUTIL TECHNICAL -

Monitoring Malicious Powershell Usage Through Log Analysis
Monitoring malicious PowerShell usage through log analysis Jesper Magnusson Computer Science and Engineering, master's level 2019 Luleå University of Technology Department of Computer Science, Electrical and Space Engineering (This page is intentionally left almost blank) Abstract Security has become a hot topic around the world but focuses more on the perime- ter than inside networks which opens up vulnerabilities. Directed cyber-attacks towards the energy sector which leverages this fact has increased and can have dis- astrous effect, even on national level. To counter this, a solution to monitor the usage of the most powerful and popular built-in tool among attackers - PowerShell - was implemented. A test-bed was set up reflecting a corporate network with two separate active directory domains, one for office clients and one for critical infrastructure. It was shown that attackers only needed to overtake the office active directory domain in order for gain easy access to the critical active directory domain. To simulate attacks of this type, a collection of malicious scripts was gathered from which a number of possible scenarios for taking over the office active directory domain via PowerShell was created. Windows has several options for logging executions of PowerShell commands on machines. The one used and deemed most beneficiary was "Module logging" with the addition of a filtered result of process creation logs. To monitor the logs created on the office client from PowerShell executions, a system based on the "ELK stack" was set up. This system gathered, processed, stored and visualized logs along with the result of their analysis. The system analyzed logs with the aid of a custom software called "ESPSA" which based on different parameters and contexts assigned every execution with a risk value indicating the level of maliciousness. -

Oracle Universal Installer and Opatch User's Guide for Windows and UNIX
Oracle® Universal Installer and OPatch User’s Guide 11g Release 2 (11.2) for Windows and UNIX E12255-11 March 2011 Oracle Universal Installer and OPatch User’s Guide, 11g Release 2 (11.2) for Windows and UNIX E12255-11 Copyright © 1996, 2011, Oracle and/or its affiliates. All rights reserved. Primary Author: Michael Zampiceni Contributor: Smitha Viswanathan, Sumant Sankaran, Phi Nguyen This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

Windows Application Reinstallation Guide
WINDOWS APPLICATION REINSTALLATION GUIDE V2021 net-ref.com • [email protected] Windows Application Manual Reinstallation Steps: 1. Ensure all accounts are logged out. (A restart/reboot is the easiest way to ensure this.) 2. Log in to the device with an Administrator account. 3. Open the Windows "Apps & features" control panel and search for NetRef. Last Updated: July 2021 1 4. Click on "NetRef Student" entry and click on the "Uninstall" button. 5. Reboot the computer to ensure all processes are removed from memory. 6. Log in to the device with an administrator account. 7. Install the app under the administrator account. Follow these steps: a. Locate the installer MSI (netref.msi or the custom application provided). b. Right-click on the file. If the option "Run as Administrator" is available, use this option. If not, click on "Install.” Windows Defender may display the below screen. If so, click on "More Last Updated: July 2021 2 Info" and "Run Anyway" to allow the app to install. c. Allow the installer at least 10 - 30 seconds to complete the installation. Note: The installation is a "quiet" installation, there will not be a confirmation dialog box. Last Updated: July 2021 3 8. Verify the app is installed by opening the Windows "Apps & features" control panel and search for "NetRef". You should see "NetRef Student" listed: 9. Open a "Command Prompt" window and enter the commands below: a. echo %username% i. The output of this command will be placed in the "Username" field of the student record in NetRef. b. echo %userdomain% i. -
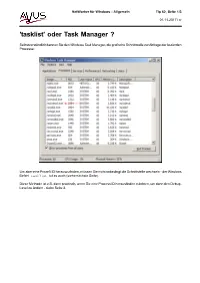
'Tasklist' Oder Task Manager ?
NetWorker für Windows - Allgemein Tip 62, Seite 1/3 01.11.2017 / cr 'tasklist' oder Task Manager ? Selbstverständlich kennen Sie den Windows Task Manager, die grafische Schnittstelle zur Abfrage der laufenden Prozesse: Um aber eine Prozeß ID herauszufinden, müssen Sie nicht unbedingt die Schnittstelle wechseln - der Windows Befehl tasklist tut es auch (siehe nächste Seite). Diese Methode ist z.B. dann praktisch, wenn Sie eine Prozess ID herausfinden möchten, um dann den Debug- Level zu ändern - siehe Seite 3. NetWorker für Windows - Allgemein Tip 62, Seite 2/3 01.11.2017 / cr C:\>tasklist -? TASKLIST [/S system [/U username [/P [password]]]] [/M [module] | /SVC | /V] [/FI filter] [/FO format] [/NH] Description: This tool displays a list of currently running processes on either a local or remote machine. Parameter List: /S system Specifies the remote system to connect to. /U [domain\]user Specifies the user context under which the command should execute. /P [password] Specifies the password for the given user context. Prompts for input if omitted. /M [module] Lists all tasks currently using the given exe/dll name. If the module name is not specified all loaded modules are displayed. /SVC Displays services hosted in each process. /V Displays verbose task information. /FI filter Displays a set of tasks that match a given criteria specified by the filter. /FO format Specifies the output format. Valid values: "TABLE", "LIST", "CSV". /NH Specifies that the "Column Header" should not be displayed in the output. Valid only for "TABLE" and "CSV" formats. /? Displays this help message. Filters: Filter Name Valid Operators Valid Value(s) ----------- --------------- -------------------------- STATUS eq, ne RUNNING | NOT RESPONDING | UNKNOWN IMAGENAME eq, ne Image name PID eq, ne, gt, lt, ge, le PID value SESSION eq, ne, gt, lt, ge, le Session number SESSIONNAME eq, ne Session name CPUTIME eq, ne, gt, lt, ge, le CPU time in the format of hh:mm:ss. -

Using SMART for Customized Monitoring of Windows Services
Using SMART for Customized Monitoring of Windows Services Gregory A. Pluta Larry Brumbaugh William Yurcik National Center for Supercomputing Applications (NCSA) University of Illinois at Urbana-Champaign {gpluta,ljbrumb,byurcik}@ncsa.uiuc.edu ABSTRACT We focus on examining and working with an important category of computer software called Services, which are provided as a part of newer Microsoft Windows operating systems. A typical Windows user transparently utilizes many of these services but is frequently unaware of their existence. Since some services have the potential to create significant problems when they are executing, it is important for a system administrator to identify which services are running on the network, the types of processing done by each service, and any interrelationships among the various services. This information can then be used to improve the overall integrity of both the individual computer where a questionable service is running and in aggregate an entire network of computers. NCSA has developed an application called SMART (Services Monitoring And Reporting Tool) that can be used to identify and display all services currently running in the network. A commercial program called Hyena remotely monitors the services on all computers attached to the network and exports this information to SMART. SMART produces various outputs that the system administrator can analyze and then determine appropriate actions to take. In particular, SMART provides a color coordinated user interface to quickly identify and classify both potentially hazardous services and also unknown services. Keywords: Windows services, Windows processes, host intrusion detection systems (IDS), host monitoring, network security monitoring, security situational awareness 1. -

VZ Orientation: Rowan: Tasklist 1/31/18, 9�43 AM
VZ Orientation: Rowan: Tasklist 1/31/18, 943 AM WARNING: YOU ARE ACCESSING THE NON-PRODUCTION SYSTEM Rowan Orientation Sign Out You are signed in as Rihab Saadeddine NEW STUDENT CHECKLIST MY ACCOUNT FAQS SEND A MESSAGE Tasklist Now that you have been admitted to Rowan University you probably have many things on your mind. To assist you during this exciting time we hope this checklist will help you stay organized. Each checklist item is important to your successful transition to college life. Please read and complete each item with attention to the given dates, and please contact the appropriate departments if you have any questions. Use this online checklist to track your progress through these important tasks. Check off each item when you have completed or finished reviewing the step. If the "complete by" date has passed, please complete the step as soon as possible! HOW TO USE YOUR CHECKLIST: Contact. Click on the question mark to see the office responsible for this item and how to contact them for more information if needed. Manual Step. After you have completed this step, mark as complete by clicking on the checkbox. Pending Step. This step will become available at a later date or after you have completed all required prerequisite steps. Tasklist (Freshman) Enrollment Confirmation - Completion Date (01/31/2018) Help! Admissions: 856-256-4200, 877-RU-ROWAN, or [email protected] This item is required of all students! When to do it: Upon offer of admission (by May 1) What to do: Confirm that your major is listed correctly. -

Your Social Media Tasklist
Your social media tasklist Everything you need to supercharge your social media, step by step. CRAWL WALK RUN DAILY Monitor Check for any messages in your inbox, posts to your profile or comments on your posts and reply. Prompt response rates will build trust and promote your social profiles as a reliable and accessible forum for your researchers to ask questions. Post Don’t wait! Anything time sensitive – event details, current issues or hot topic related should be posted on the day you know about it. WEEKLY Schedule With the help of management tools such as Tweetdeck, you can schedule your daily posts ahead of time. Do this once at the beginning of the week and you won’t need to write daily updates, but your researchers will see updates every day. Monitor Once you’ve identified who the influencers are in your social network, monitor their activity and listen to their conversations to stay up to speed with hot topics in your field. Look for relevant hashtags such as #libchat or search by topic. Research Follow-up on a topic you are interested in that you have seen posts on. Read blogs, news articles and visit websites. Increase your knowledge of the topics you know your researchers are interested in will make you more relevant. Network Join in conversations that are happening within your network. By being active in your community, you can raise your profile and that of your institution. MONTHLY Schedule Using a content calendar, plan in your posts for the month. You can theme these around events or themes that you know are important in the lives of the researchers you talk to.