Proof of Concept on Utilization of Blockchain Technology in KYC
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Annual Results for 3QFY2016
Matsui Securities Co., Ltd. (First Section of TSE: 8628) Annual Results for 3QFY2016 January 2017 Table of Contents Section 1 Financial Summary 6 Section 2 Results of Operation 16 Section 3 Recent Developments 23 1 Results of Operation ◆ Equity trading value / Market share ◆ Equity commission rate Excluding “Margin Trading Service for (JPY tn) Margin Trading Service for Day-trades (bp) Day-trades” 15 15% 12 13.5% 13.8% 12.4% 12.7% 12.2% 10.0 10.0 9.6 9.9 9.8 12 12% 10 8 9 9.6 9% 9.2 8.9 8.6 8.4 6 6% 6 4.8 4.7 4.4 4.3 5.4 5.3 5.3 3.9 3 4.6 4.5 3% 4 0 0% 2 3Q 4Q 1Q 2Q 3Q 3Q 4Q 1Q 2Q 3Q FY15 FY16 FY15 FY16 ◆ Margin balance / Market share ◆ Net financial income ratio (JPY bn) 5.0% 400 9.2% 9.1% 10% 9.0% 8.9% 4.2% 8.3% 3.8% 3.9% 8% 4.0% 3.6% 3.7% 300 308 6% 3.0% 200 258 241 224 231 4% 2.0% 100 2% 1.0% 0 0% 0.0% 3Q 4Q 1Q 2Q 3Q 3Q 4Q 1Q 2Q 3Q FY15 FY16 FY15 FY16 2 Financial Results ◆ Operating revenue ◆ Ordinary income (JPY mn) (JPY mn) 10,000 10,000 8,071 7,823 8,000 7,463 8,000 6,981 6,284 6,000 6,000 5,057 4,569 4,084 3,860 4,000 4,000 3,296 2,000 2,000 0 0 3Q 4Q 1Q 2Q 3Q 3Q 4Q 1Q 2Q 3Q FY15 FY16 FY15 FY16 1 ◆ Net income / ROE ◆ Ordinary income ratio (JPY mn) 10,000 20% 80% 63% 58% 8,000 14.3% 55% 15% 60% 55% 52% 12.5% 12.4% 11.6% 6,000 10.0% 10% 40% 4,000 3,273 2,865 2,828 2,673 2,277 5% 20% 2,000 0 0% 0% 3Q 4Q 1Q 2Q 3Q 3Q 4Q 1Q 2Q 3Q FY15 FY16 FY15 FY16 Note 1: Annualized on each quarter 3 Financial Highlights ◆ Operating revenues up JPY 700 million QoQ • Commissions were up JPY 590 million due to increase of equity trading value excluding -

FTSE Japan ESG Low Carbon Select
2 FTSE Russell Publications 19 August 2021 FTSE Japan ESG Low Carbon Select Indicative Index Weight Data as at Closing on 30 June 2021 Constituent Index weight (%) Country Constituent Index weight (%) Country Constituent Index weight (%) Country ABC-Mart 0.01 JAPAN Ebara 0.17 JAPAN JFE Holdings 0.04 JAPAN Acom 0.02 JAPAN Eisai 1.03 JAPAN JGC Corp 0.02 JAPAN Activia Properties 0.01 JAPAN Eneos Holdings 0.05 JAPAN JSR Corp 0.11 JAPAN Advance Residence Investment 0.01 JAPAN Ezaki Glico 0.01 JAPAN JTEKT 0.07 JAPAN Advantest Corp 0.53 JAPAN Fancl Corp 0.03 JAPAN Justsystems 0.01 JAPAN Aeon 0.61 JAPAN Fanuc 0.87 JAPAN Kagome 0.02 JAPAN AEON Financial Service 0.01 JAPAN Fast Retailing 3.13 JAPAN Kajima Corp 0.1 JAPAN Aeon Mall 0.01 JAPAN FP Corporation 0.04 JAPAN Kakaku.com Inc. 0.05 JAPAN AGC 0.06 JAPAN Fuji Electric 0.18 JAPAN Kaken Pharmaceutical 0.01 JAPAN Aica Kogyo 0.07 JAPAN Fuji Oil Holdings 0.01 JAPAN Kamigumi 0.01 JAPAN Ain Pharmaciez <0.005 JAPAN FUJIFILM Holdings 1.05 JAPAN Kaneka Corp 0.01 JAPAN Air Water 0.01 JAPAN Fujitsu 2.04 JAPAN Kansai Paint 0.05 JAPAN Aisin Seiki Co 0.31 JAPAN Fujitsu General 0.01 JAPAN Kao 1.38 JAPAN Ajinomoto Co 0.27 JAPAN Fukuoka Financial Group 0.01 JAPAN KDDI Corp 2.22 JAPAN Alfresa Holdings 0.01 JAPAN Fukuyama Transporting 0.01 JAPAN Keihan Holdings 0.02 JAPAN Alps Alpine 0.04 JAPAN Furukawa Electric 0.03 JAPAN Keikyu Corporation 0.02 JAPAN Amada 0.01 JAPAN Fuyo General Lease 0.08 JAPAN Keio Corp 0.04 JAPAN Amano Corp 0.01 JAPAN GLP J-REIT 0.02 JAPAN Keisei Electric Railway 0.03 JAPAN ANA Holdings 0.02 JAPAN GMO Internet 0.01 JAPAN Kenedix Office Investment Corporation 0.01 JAPAN Anritsu 0.15 JAPAN GMO Payment Gateway 0.01 JAPAN KEWPIE Corporation 0.03 JAPAN Aozora Bank 0.02 JAPAN Goldwin 0.01 JAPAN Keyence Corp 0.42 JAPAN As One 0.01 JAPAN GS Yuasa Corp 0.03 JAPAN Kikkoman 0.25 JAPAN Asahi Group Holdings 0.5 JAPAN GungHo Online Entertainment 0.01 JAPAN Kinden <0.005 JAPAN Asahi Intecc 0.01 JAPAN Gunma Bank 0.01 JAPAN Kintetsu 0.03 JAPAN Asahi Kasei Corporation 0.26 JAPAN H.U. -

(Ex Controversies and CW) Index Equity Fund
Report and Financial Statements For the year ended 31st December 2020 State Street AUT Japan Screened (ex Controversies and CW) Index Equity Fund (formerly State Street Japan Equity Tracker Fund) State Street AUT Japan Screened (ex Controversies and CW) Index Equity Fund Contents Page Manager's Report* 1 Portfolio Statement* 5 Director's Report to Unitholders* 25 Manager's Statement of Responsibilities 26 Statement of the Depositary’s Responsibilities 27 Report of the Depositary to the Unitholders 27 Independent Auditors’ Report 28 Comparative Table* 31 Financial statements: 32 Statement of Total Return 32 Statement of Change in Net Assets Attributable to Unitholders 32 Balance Sheet 33 Notes to the Financial Statements 34 Distribution Tables 45 Directory* 46 Appendix I – Remuneration Policy (Unaudited) 47 Appendix II – Assessment of Value (Unaudited) 49 * These collectively comprise the Manager’s Report. State Street AUT Japan Screened (ex Controversies and CW) Index Equity Fund Manager’s Report For the year ended 31st December 2020 Authorised Status The State Street AUT Japan Screened (ex Controversies and CW) Index Equity Fund (the “Fund”) is an Authorised Unit Trust Scheme as defined in section 243 of the Financial Services and Markets Act 2000 and it is a UCITS Retail Scheme within the meaning of the FCA Collective Investment Schemes sourcebook. The unitholders are not liable for the debts of the Fund. The Fund's name was changed to State Street AUT Japan Screened (ex Controversies and CW) Index Equity Fund on 18th December 2020 (formerly State Street Japan Equity Tracker Fund). Investment Objective and Policy The objective of the Fund is to replicate, as closely as possible, and on a “gross of fees” basis, the return of the Japan equity market as represented by the FTSE Japan ex Controversies ex CW Index (the “Index”) net of unavoidable withholding taxes. -
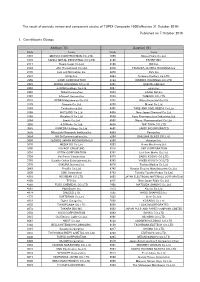
Published on 7 October 2016 1. Constituents Change the Result Of
The result of periodic review and component stocks of TOPIX Composite 1500(effective 31 October 2016) Published on 7 October 2016 1. Constituents Change Addition( 70 ) Deletion( 60 ) Code Issue Code Issue 1810 MATSUI CONSTRUCTION CO.,LTD. 1868 Mitsui Home Co.,Ltd. 1972 SANKO METAL INDUSTRIAL CO.,LTD. 2196 ESCRIT INC. 2117 Nissin Sugar Co.,Ltd. 2198 IKK Inc. 2124 JAC Recruitment Co.,Ltd. 2418 TSUKADA GLOBAL HOLDINGS Inc. 2170 Link and Motivation Inc. 3079 DVx Inc. 2337 Ichigo Inc. 3093 Treasure Factory Co.,LTD. 2359 CORE CORPORATION 3194 KIRINDO HOLDINGS CO.,LTD. 2429 WORLD HOLDINGS CO.,LTD. 3205 DAIDOH LIMITED 2462 J-COM Holdings Co.,Ltd. 3667 enish,inc. 2485 TEAR Corporation 3834 ASAHI Net,Inc. 2492 Infomart Corporation 3946 TOMOKU CO.,LTD. 2915 KENKO Mayonnaise Co.,Ltd. 4221 Okura Industrial Co.,Ltd. 3179 Syuppin Co.,Ltd. 4238 Miraial Co.,Ltd. 3193 Torikizoku co.,ltd. 4331 TAKE AND GIVE. NEEDS Co.,Ltd. 3196 HOTLAND Co.,Ltd. 4406 New Japan Chemical Co.,Ltd. 3199 Watahan & Co.,Ltd. 4538 Fuso Pharmaceutical Industries,Ltd. 3244 Samty Co.,Ltd. 4550 Nissui Pharmaceutical Co.,Ltd. 3250 A.D.Works Co.,Ltd. 4636 T&K TOKA CO.,LTD. 3543 KOMEDA Holdings Co.,Ltd. 4651 SANIX INCORPORATED 3636 Mitsubishi Research Institute,Inc. 4809 Paraca Inc. 3654 HITO-Communications,Inc. 5204 ISHIZUKA GLASS CO.,LTD. 3666 TECNOS JAPAN INCORPORATED 5998 Advanex Inc. 3678 MEDIA DO Co.,Ltd. 6203 Howa Machinery,Ltd. 3688 VOYAGE GROUP,INC. 6319 SNT CORPORATION 3694 OPTiM CORPORATION 6362 Ishii Iron Works Co.,Ltd. 3724 VeriServe Corporation 6373 DAIDO KOGYO CO.,LTD. 3765 GungHo Online Entertainment,Inc. -

FTSE Publications
2 FTSE Russell Publications 20 May 2020 FTSE Japan Indicative Index Weight Data as at Closing on 31 March 2020 Constituent Index weight (%) Country Constituent Index weight (%) Country Constituent Index weight (%) Country 77 Bank 0.03 JAPAN Denso Corporation 0.45 JAPAN Isetan Mitsukoshi Holdings 0.06 JAPAN ABC-Mart 0.04 JAPAN Dentsu Inc 0.13 JAPAN Isuzu Motors 0.1 JAPAN Acom 0.05 JAPAN DIC 0.06 JAPAN Ito En 0.09 JAPAN Advantest Corp 0.24 JAPAN Disco 0.17 JAPAN Itochu Corp 0.87 JAPAN Aeon 0.48 JAPAN DMG Mori Seiki 0.03 JAPAN Itochu Techno Solutions 0.08 JAPAN AEON Financial Service 0.04 JAPAN Dowa Holdings 0.04 JAPAN Itoham Yonekyu Holdings 0.02 JAPAN Aeon Mall 0.05 JAPAN East Japan Railway 0.84 JAPAN Iyo Bank 0.04 JAPAN AGC 0.14 JAPAN Ebara 0.06 JAPAN Izumi Co Ltd 0.03 JAPAN Aica Kogyo 0.05 JAPAN Eisai 0.6 JAPAN J Front Retailing 0.06 JAPAN Ain Pharmaciez 0.05 JAPAN Electric Power Development 0.1 JAPAN Japan Airlines 0.06 JAPAN Air Water 0.08 JAPAN Ezaki Glico 0.07 JAPAN Japan Airport Terminal 0.06 JAPAN Aisin Seiki Co 0.13 JAPAN FamilyMart 0.13 JAPAN Japan Aviation Electronics 0.02 JAPAN Ajinomoto Co 0.28 JAPAN Fancl Corp 0.05 JAPAN Japan Exchange Group 0.29 JAPAN Alfresa Holdings 0.1 JAPAN Fanuc 0.8 JAPAN Japan Petroleum Exploration 0.02 JAPAN Alps Alpine 0.06 JAPAN Fast Retailing 0.65 JAPAN Japan Post Bank 0.12 JAPAN Amada 0.08 JAPAN FP Corporation 0.05 JAPAN Japan Post Holdings 0.32 JAPAN Amano Corp 0.05 JAPAN Fuji Electric 0.09 JAPAN Japan Post Insurance 0.07 JAPAN ANA Holdings 0.08 JAPAN Fuji Media Holdings 0.01 JAPAN Japan Steel -

DTC Important Notice
#: 6183-10 Date: February 4, 2010 To: All Participants Category: Dividends From: Tax Reporting Service Attention: Managing Partner/Officer, Cashier, Dividend Mgr., Tax Mgr. Subject: Citibank - ADRs that the bank, as ADR depositary for these issues, has determined if they met the criteria for the reduced U.S. tax rate as “qualified dividends” for tax year 2009. The Depository Trust Company received the attached correspondence containing Tax Information. If applicable, please consult your tax advisor to ensure proper treatment of this event. Important Legal Information: The Depository Trust Company (“DTC”) does not represent or warrant the accuracy, adequacy, timeliness, completeness or fitness for any particular purpose of the information contained in this communication, which is based in part on information obtained from third parties and not independently verified by DTC and which is provided as is. The information contained in this communication is not intended to be a substitute for obtaining tax advice from an appropriate professional advisor. In providing this communication, DTC shall not be liable for (1) any loss resulting directly or indirectly from mistakes, errors, omissions, interruptions, delays or defects in such communication, unless caused directly by gross negligence or willful misconduct on the part of DTC, and (2) any special, consequential, exemplary, incidental or punitive damages. To ensure compliance with Internal Revenue Service Circular 230, you are hereby notified that: (a) any discussion of federal tax issues contained or referred to herein is not intended or written to be used, and cannot be used, for the purpose of avoiding penalties that may be imposed under the Internal Revenue Code; and (b) as a matter of policy, DTC does not provide tax, legal or accounting advice and accordingly, you should consult your own tax, legal and accounting advisor before engaging in any transaction. -

SBI Holdings, Inc. 2012 Information Meeting
Strategic Business Innovator SBI Holdings, Inc. 2012 Information Meeting May 28 Tokyo June 1 Nagoya June 4 Osaka June 5 Fukuoka The items in this document are provided as information related to the business strategy of the SBI Group companies and not as an invitation to invest in the stock or securities issued by each company. None of the Group companies guarantees the completeness of this document in terms of information and future business strategy. The content of this document is subject to revision or cancellation without warning. Note: Fiscal Year (“FY”) ends March 31 of the following year 1 I. Summary of Business Results for FY2011 II. 13 Year History of the SBI Group Since Its Foundation III. The Business Strategy to Become the “World’s SBI” and the New Organizational Structure to Support the Strategy IV. Review of SBI's Share Price and Corporate Value 2 I. Summary of Business Results for FY2011 3 FY201FY20111 ConsolidatedConsolidated PerformancePerformance Achieved a year-on-year increase of 19.9% in net income, excluding the impact from the tax revisions (JPY million) FY2010 FY2011 YoY change Full year Full year (%) (Apr. 2010 – Mar. 2011) (Apr. 2011 – Mar. 2012) Operating 141,081 145,074 +2.8 Revenues Operating *1 8,932 7,575 -15.2 Income Ordinary 3,525 4,860 +37.8 Income *2, 3 Net Income 4,534 3,200 -29.4 *1 SBI Insurance recorded a JPY 3.5bn loss for operating income. *2 JPY 8.6bn was recorded as extraordinary income from the sale of SBI VeriTrans *3 In accordance with the tax revisions, a JPY 2.2bn loss was recorded as income taxes-deferred. -

Toshiba Corp. V. Automotive Industries Pension Trust Fund (U.S. Supreme
No. ___ IN THE Supreme Court of the United States ———— TOSHIBA CORPORATION, Petitioner, v. AUTOMOTIVE INDUSTRIES PENSION TRUST FUND; NEW ENGLAND TEAMSTERS & TRUCKING INDUSTRY PENSION FUND, Respondents. ———— On Petition for a Writ of Certiorari to the United States Court of Appeals for the Ninth Circuit ———— APPENDIX TO PETITION FOR A WRIT OF CERTIORARI ———— CHRISTOPHER M. CURRAN Counsel of Record NICOLE ERB ERIC GRANNON JAIME M. CROWE REUBEN J. SEQUEIRA WHITE & CASE LLP 701 Thirteenth Street, N.W. Washington, DC 20005 (202) 626-3600 [email protected] Counsel for Petitioner October 15, 2018 WILSON-EPES PRINTING CO., INC. – (202) 789-0096 – WASHINGTON, D. C. 20002 TABLE OF CONTENTS Page APPENDICES Appendix A: Court of Appeals Opinion Opinion, Stoyas v. Toshiba Corp., 896 F.3d 933 (9th Cir. 2018) (No. 16-56058) .............. 1a Appendix B: Order Staying Mandate Order, Stoyas v. Toshiba Corp., No. 16- 56058, 2018 U.S. App. LEXIS 22084 (9th Cir. Aug. 8, 2018) ........................................ 38a Appendix C: District Court Opinion Order re: Defendant’s Motion to Dismiss & Plaintiffs’ Motion to Strike Wada Declaration, Stoyas v. Toshiba Corp., 191 F. Supp. 3d 1080 (C.D. Cal. 2016) (No. 2:15-cv-04194-DDP-JC) ...................................... 40a Appendix D: Amended Complaint and Selected Exhibit Amended & Consolidated Class Action Complaint for Violation of the Securities Laws of the United States and Japan, Stoyas v. Toshiba Corp., 191 F. Supp. 3d 1080 (C.D. Cal. 2016) (No. 2:15-cv-04194- DDP-JC), ECF No. 34 ......................................... 78a ii TABLE OF CONTENTS - CONTINUED Page Exhibit 8 to Amended & Consolidated Class Action Complaint, Receipt of Investigation Report from Executive Liability Investigation Committee, Filing of Action for Compensatory Damages Against Former Company Executives, an Action Filed in the U.S., and Other Matters, Stoyas v. -

Review of Operations P28 at a Glance P30 in the Industry P32 Retail P36 Wholesale P40 Investment P42 Asset Management P46 Systems and Research
Review of Operations p28 At a Glance p30 In the Industry p32 Retail p36 Wholesale p40 Investment p42 Asset Management p46 Systems and Research DAIWA SECURITIES GROUP ANNUAL REPORT 200 2 R e v i e w o f O p e r at i o n s At a Glance: Core Business Segments of the Daiwa Securities Group Retail Ordinary Income (¥ billion) 120 101.0 The Group’s retail securities firm boasts a top-class customer base in Japan, to which it provides a wide range of financial products and ser- 80 74.4 71.0 vices, mainly to individual investors and unlisted companies. One of the company’s advantages in the retail market is its ability to provide custom- 7.3 ers with two in-house customer service courses. Its “Daiwa Consulting” 40.4 40 course provides access to sales personnel that offer high value-added ser- vices, while its “Daiwa Direct” course provides highly convenient online 18.3 brokerage services. 0 05 06 07 08 09 (Fiscal year) Wholesale Ordinary Income (¥ billion) 200 141.5 With a global network based on domestic and overseas operating offices, 100 92.8 68.7 the Group’s wholesale securities firm‘s customer base comprises Japanese and foreign institutional investors, business corporations, and financial ser- 1.4 vices companies. The company offers a broad range of services to suit the 0 needs of its customers, including sales and trading, investment banking, and research. -100 -200 -167.4 05 06 07 08 09 (Fiscal year) Investment Daiwa PI Partners makes selective investments in such areas as monetary Daiwa Corporate Investment operates venture capital, buyout investment claims and private equity. -

Vanguard FTSE International Index Funds Annual
Annual Report | October 31, 2020 Vanguard FTSE International Index Funds Vanguard FTSE All-World ex-US Index Fund Vanguard FTSE All-World ex-US Small-Cap Index Fund See the inside front cover for important information about access to your fund’s annual and semiannual shareholder reports. Important information about access to shareholder reports Beginning on January 1, 2021, as permitted by regulations adopted by the Securities and Exchange Commission, paper copies of your fund’s annual and semiannual shareholder reports will no longer be sent to you by mail, unless you specifically request them. Instead, you will be notified by mail each time a report is posted on the website and will be provided with a link to access the report. If you have already elected to receive shareholder reports electronically, you will not be affected by this change and do not need to take any action. You may elect to receive shareholder reports and other communications from the fund electronically by contacting your financial intermediary (such as a broker-dealer or bank) or, if you invest directly with the fund, by calling Vanguard at one of the phone numbers on the back cover of this report or by logging on to vanguard.com. You may elect to receive paper copies of all future shareholder reports free of charge. If you invest through a financial intermediary, you can contact the intermediary to request that you continue to receive paper copies. If you invest directly with the fund, you can call Vanguard at one of the phone numbers on the back cover of this report or log on to vanguard.com. -

There for You BASIC COMMITMENT of the TOSHIBA GROUP
TOSHIBA ANNUAL REPORT 2001 Year ended March 31, 2001 there for you BASIC COMMITMENT OF THE TOSHIBA GROUP We, the Toshiba Group companies, based on our total commitment to people and to the future, are determined to help create a higher quality of life for all people, and to do our part to help ensure that progress continues within the world community. COMMITMENT TO PEOPLE We endeavor to serve the needs of all people, especially our customers, shareholders, and employees, by implementing forward-looking corporate strategies while carrying out responsible and responsive business activities. As good corporate citizens, we actively contribute to further the goals of society. COMMITMENT TO THE FUTURE By continually developing innovative technologies centering on the fields of Electronics and Energy, we strive to create products and services that enhance human life, and which lead to a thriving, healthy society. We constantly seek new approaches that help realize the goals of the world community, including ways to improve the global environment. Committed to People, Committed to the Future. FINANCIAL HIGHLIGHTS 1 TO OUR SHAREHOLDERS 2 FEATURE 6 Value chain 8 Innovative technologies 10 Initiative 12 TOSHIBA AND THE ENVIRONMENT 14 BOARD OF DIRECTORS, EXECUTIVE OFFICERS AND STATUTORY AUDITORS 16 REVIEW OF OPERATIONS AND FINANCIAL SECTION 17 MANAGEMENT’S DISCUSSION AND ANALYSIS 33 CONSOLIDATED FINANCIAL STATEMENTS 40 GLOBAL NETWORK 62 CONSOLIDATED SUBSIDIARIES 64 INVESTOR REFERENCE 65 FORWARD-LOOKING STATEMENTS This annual report contains forward-looking statements concerning Toshiba’s future plans, strategies and performance. These forward-looking statements are not historical facts, rather they represent assumptions and beliefs based on economic, financial and competitive data currently available. -

Respondents(Eng)
2005 JCGR JCGIndex Survey Responding Companies http://www.jcgr.org/ TSE Code Company Indutry T1334 Maruha Group Inc. Fishery, Agriculture & Forestry T1801 Taisei Corp. Construction T1802 Obayashi Corp. Construction T1814 Daisue Construction Co., Ltd. Construction T1816 Ando Corp. Construction T1822 Daiho Corp. Construction T1824 Maeda Corp. Construction T1834 Odakyu Construction Co., Ltd. Construction T1835 Totetsu Kogyo Co., Ltd. Construction T1861 Kumagai Gumi Co., Ltd. Construction T1881 NIPPO Corp. Construction T1925 Daiwa House Industry Co., Ltd. Construction T1928 Sekisui House, Ltd. Construction T1950 Nippon Densetsu Kogyo Co., Ltd. Construction T1954 Nippon Koei Co., Ltd. Services T1967 Yamato Corp. Construction T1980 Dai-Dan Co., Ltd. Construction T2051 Nosan Corp. Foods T2052 Kyodo Shiryo Co., Ltd. Foods T2107 Toyo Sugar Refining Co., Ltd. Foods T2201 Morinaga & Co., Ltd. Foods T2202 Meiji Seika Kaisha, Ltd. Foods T2206 Ezaki Glico Co., Ltd. Foods T2267 Yakult Honsha Co., Ltd. Foods T2282 Nippon Meat Packers, Inc. Foods T2284 Itoham Foods Inc. Foods T2290 Yonekyu Corp. Foods T2322 NEC Fielding, Ltd. Services T2501 Sapporo Holdings Ltd. Foods T2502 Asahi Breweries, Ltd. Foods T2533 Oenon Holdings, Inc. Foods T2536 Mercian Corp. Foods T2579 Coca-Cola West Japan Co., Ltd. Foods T2590 Dydo Drinco, Inc. Foods T2591 Calpis Co., Ltd. Foods T2597 Unicafe Inc. Foods T2599 Japan Foods Co., Ltd. Foods T2602 The Nisshin Oillio Group, Ltd. Foods T2671 F.D.C. Products Inc. Retail Trade T2698 Can Do Co., Ltd. Retail Trade T2734 Sala Corp. Retail