Information Supplement: Third-Party Security Assurance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fiserv Cashless Payment Innovations for Merchants, Insurers Receive 2020 Payments Awards
Fiserv Cashless Payment Innovations for Merchants, Insurers Receive 2020 Payments Awards December 18, 2020 Solutions enable cashless payments at the point of sale and remotely Warsaw, Poland, 18 December 2020 – Fiserv, a leading global provider of payments and financial services technology, has won two 2020 Payments Awards thanks to the company’s innovative and pioneering approach to cashless payments. “First and foremost, these awards recognise the work of the entire team, as well as the innovative mindset and courage of our partners. Both awards are not only a source of great pride, but also serve as additional incentive for further growth. I am glad to be able to work with trendsetters shaping the world of cashless payments,” said Krzysztof Polończyk, President of First Data Polska, now Fiserv. The Payments Innovation of the Year Award was presented for the SoftPOS PIN on Mobile solution from Fiserv, a technology developed in conjunction with Visa, Samsung and PayCore. The solution enables cashless payment acceptance by merchants on their own devices, such as smartphones or tablets, for any payment amount and without the need for additional equipment. The solution, which is currently being piloted in Poland, opens up the possibility of increased use of mobile devices as payment terminals worldwide. “The popularity of non-cash payments in Poland continues to grow. We already have over a million terminals in Poland, and connecting smartphones and tablets to this huge network will not only increase the share of cashless transactions, but above all will have a positive impact on the cash flow of merchants, small businesses and service providers,” says Rafał Galiński, Products Development Director at First Data Polska, now Fiserv. -

Fintech & Bank
VOLUME 3 | 2018 THE CENTER OF COMMERCE Fintech & Bank FUsionThere Are Certain Things In Life That You Expect To Be Boring. Technology relevant to the consumer,” says Nigel So, banks have stepped up, have started There are Motyer, who heads up First Data’s Direct to “shake off” the old stodgy perceptions Acquiring Business in EMEA and sits and are beginning to innovate in on the Board of Directors at First Data response to consumer needs. Recently, certain things Europe. “Why did PayPal® become so major banks collaborated to create their all-pervasive? Because it was the only own fintech P2P platform called Zelle®, method of payment that you had on which allows account holders to transfer Fintech in life that eBay – and the consumer loved eBay.” cash instantly over apps or online. you expect to Consumers also love a new way to pay Meanwhile, the fintech world is actively their friends and family, via person-to- seizing ground once monopolized by person micropayments. Early versions banks. SoFi® is an online company that Bank Fusion be boring. allowed for easy payments via text provides personal loans, mortgages, messages. Now, person-to-person and student loan refinancing, mostly For example, rice cakes, micropayments live on a platform nearly targeting Millennials.5 GreenSky® offers waiting rooms, stories indistinguishable from social media, a instant loans for home improvements,6 about rocks – and certain no-go zone for banks.4 and Avant® offers loans to consumers things that you hope will with low credit scores.7 be boring like visits to the “Banks, traditionally, were very slow dentist and travel by plane. -
2020 Q1 Mid Cap Growth Factsheet
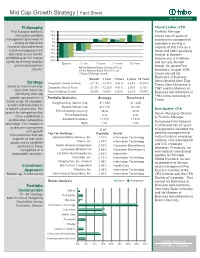
Mid Cap Growth Strategy | Fact Sheet as of 03/31/2020 Philosophy Chuck Lauber, CFA First National believes 15% Portfolio Manager that active portfolio 10% Chuck has 25 years of management grounded in 5% investment management strong fundamental 0% experience serving a research and adherence -5% majority of that time as a to risk management will -10% Small and Mid Cap Equity add value to our clients' -15% Analyst at Koesten portfolios over full market -20% Hirschmann & Crabtree cycles by limiting volatility -25% Quarter 1 Year 3 Years 5 Years 10 Years and Security Benefit and increasing their Group. He joined First First National Bank (Gross of Fees) returns. First National Bank (Net of Fees) National in August 2006. Russell Midcap Growth Chuck earned his Bachelors in Business Quarter 1 Year 3 Years 5 years 10 Years Strategy Administration from East Composite (Gross of Fees) -21.19% -11.41% 4.91% 4.63% 10.67% Texas State University in Seeks to maximize long- Composite (Net of Fees) -21.37% -12.32% 4.01% 3.78% 9.73% 1987 and his Masters of term total return, by Russell Midcap Growth -20.04% -9.45% 6.53% 5.61% 10.89% Business Administration in identifying mid-cap 1993 at the University of growth companies in a Portfolio Statistics Strategy Benchmark Texas. broad range of economic Weighted Avg. Market Cap $17.63B $17.26B sectors and industries in Median Market Cap $11.81B $7.24B a bottom-up process. We Kurt Spieler, CFA Price/Earnings (ex-neg) 26.0x 23.0x search for companies that Senior Managing Director Price/Book Ratio 4.1x 4.4x have established a & Portfolio Manager Standard Deviation 17.78% 17.43% sustainable competitive Kurt joined First National Beta 1.01 1.00 advantage. -

Download the Digital Magazine At: Firstdata.Com/Connected
VOLUME 3 | 2018 THE CENTER OF COMMERCE the innovators CASE STUDY: 2 QSR Company INFORMATION QSR customer upgrades their fraud COVER detection to enable a new mobile RESULTS: application launch PROBLEM: When this customer launched a new version of their mobile app, they saw fraud spikes that decrease & ANALYTICS called for new tools. 80% in fraud. SOLUTION: The Advanced offering of Fraud Detect was implemented with a machine learning QSR- industry model, a rules engine, and Case 14 SOLUTIONS Manager. First Data also implemented a capability $200K allowing this customer to test the model at saved after fees. DATA AT THE SPEED OF COMMERCE different scoring thresholds. The innovators Building the new retail frontier. 19 bonus: SPECIAL section Unlocking Merchant Innovation Using machine learning to combat fraud. Shopping is about to get interesting. 8 Mobility Hits Its Groove 44 Fintech & Bank Fusion 10 Outsmarting Fraudsters 47 The Power of Partnerships 12 Rewards Revolution 48 Payments Everywhere 35 The New Big Data 50 Gen-Z Rising 39 Food for Thought 54 Financial Literacy in the Gig Economy 40 Tackling the Pay Gap download the digital magazine At: FirstData.com/Connected Not sure about you, but our dogs are always finding innovative new ways to get our attention. Through this issue of Connected, we take a look at how partnerships, changing consumer landscapes, and fraud breakthroughs are fetching innovative ideas across industries – Labonardo da Vinci and Thomas Pugison would be so pleased. As you’re reading, keep an eye out for the pooches and pups hidden throughout the pages and count them up. -

Fiserv 16X9 Arial Template
USING THE PAST TO MANAGE PAYMENT FRAUD RISK FORTUNE Magazine World's Most Admired Companies® © 2018 Fiserv, Inc. or its affiliates. | CONFIDENTIAL – LIMITED 2014 | 2015 | 2016 | 2017 | 2018 Speakers Andrew Davies VP, Global Market Strategy, Financial Crimes Risk Management, Fiserv Andrew Davies has 25 years experience in financial services and risk management with particular focus on AML, fraud, risk management, settlement risk and payment processing. He is responsible for working with Fiserv customers around the world to design and deploy effective financial crime risk management solutions. Andrew has experience working for and with organizations like Nomura, The Federal Reserve Bank of New York, the Continuous Linked Settlement Bank, ING, Sun Life, Manulife Financial, Citizens Bank, Deutsche Bank and the Bank of Tokyo-Mitsubishi, among others. FORTUNE Magazine World's Most Admired Companies® © 2018 Fiserv, Inc. or its affiliates. | CONFIDENTIAL – LIMITED 2014 | 2015 | 2016 | 2017 | 2018 Speakers Dave Richardson Senior Manager Fraud & ATM Operations First National Bank of Omaha Dave brings 19 years experience in fraud prevention field as it relates to various on-line channels, primarily within the financial services industry. He has successfully created a best-in-class fraud prevention team responsible for monitoring and mitigating fraud against consumer, business, and commercial bank accounts. He is an expert at building out tools to prevent losses through ACH, wire, ATM, and mobile channels. Also, he has developed risk control guidance for mobile banking deposit products, on-line money movement, business mobile banking, and enterprise-wide transaction monitoring. His approach focuses on the impacts of fraud prevention to the customer experience. -

2019 Commerce and Payments Year In
2019 Commerce and Fintech Year in Review Fiserv Data & Analytics FORTUNE Magazine World's Most Admired Companies® 1 © 2019 Fiserv, Inc. or its affiliates. 2014 | 2015 | 2016 | 2017 | 2018 | 2019 Top Trends of 2019 Holiday shopping Resurrection Open banking in 01 kickoff 05 retailers 09 the US Amazon’s brand Upping the brand Banking 02 partnerships 06 experience 10 disruption Amazon Go Delivery fulfillment Neo and challenger 03 expansion 07 frenzy 11 bank lessons Walmart’s shifting Revamping the QSR Voice 04 eCommerce strategy 08 drive thru 12 banking FORTUNE Magazine World's Most Admired Companies® 2 © 2019 Fiserv, Inc. or its affiliates. 2014 | 2015 | 2016 | 2017 | 2018 | 2019 YoY Growth YoY Growth Pre-Holiday Thanksgiving + Black Friday Total 15% Spend 11.9% 11.5% 10% Through Black Friday, the 2019 holiday season looks to be off to a solid start, 7.1% and reminiscent of patterns we saw in 5.7% 2017. 5.1% 5% 2.6% 0% 2017 2018 2019 Note: Figures include Brick & Mortar and eCommerce channels. Source: Fiserv aggregated same-store consumer spending data. FORTUNE Magazine World's Most Admired Companies® 3 © 2019 Fiserv, Inc. or its affiliates. 2014 | 2015 | 2016 | 2017 | 2018 | 2019 Thanksgiving + Black Friday YoY Growth Total Retail = 7.5% 17.2% Growth by 14.4% Category 10.6% With tremendous momentum from eCommerce, Furniture, DIY, and Sporting Goods led all retail categories for growth 7.7% during Thanksgiving and Black Friday. 6.2% 5.6% 5.4% Furniture / Building Sporting General Clothing & Electronics & Specialty Furnishings Materials & Goods Merchandise Accessories Appliances Retailers DIY Note: Figures include Brick & Mortar and eCommerce channels. -

WALGREENS (Strong Performing Location) 3825 Durand Avenue Racine, WI 53405 (Milwaukee MSA) TABLE of CONTENTS
NET LEASE INVESTMENT OFFERING WALGREENS (Strong Performing Location) 3825 Durand Avenue Racine, WI 53405 (Milwaukee MSA) TABLE OF CONTENTS TABLE OF CONTENTS I. Executive Profile II. Location Overview III. Market & Tenant Overview Executive Summary Photographs Demographic Report Investment Highlights Drone Photographs Market Overview Property Overview Aerial Tenant Overview Site Plan Maps NET LEASE INVESTMENT OFFERING DISCLAIMER STATEMENT DISCLAIMER The information contained in the following Offering Memorandum is proprietary and strictly confidential. STATEMENT: It is intended to be reviewed only by the party receiving it from The Boulder Group and should not be made available to any other person or entity without the written consent of The Boulder Group. This Offering Memorandum has been prepared to provide summary, unverified information to prospective purchasers, and to establish only a preliminary level of interest in the subject property. The information contained herein is not a substitute for a thorough due diligence investigation. The Boulder Group has not made any investigation, and makes no warranty or representation. The information contained in this Offering Memorandum has been obtained from sources we believe to be reliable; however, The Boulder Group has not verified, and will not verify, any of the information contained herein, nor has The Boulder Group conducted any investigation regarding these matters and makes no warranty or representation whatsoever regarding the accuracy or completeness of the information provided. All potential buyers must take appropriate measures to verify all of the information set forth herein. NET LEASE INVESTMENT OFFERING EXECUTIVE SUMMARY EXECUTIVE The Boulder Group is pleased to exclusively market for sale a single tenant net leased Walgreens located within the SUMMARY: Milwaukee MSA in Racine, Wisconsin. -

Schedule of Investments(A) March 31, 2021 (Unaudited)
Schedule of Investments(a) March 31, 2021 (Unaudited) Shares Value Shares Value Common Stocks & Other Equity Interests–99.60% Electrical Components & Equipment–3.35% Aerospace & Defense–0.49% Hubbell, Inc. 21,713 $ 4,057,943 Curtiss-Wright Corp. 10,338 $ 1,226,087 Rockwell Automation, Inc. 16,189 4,297,208 8,355,151 Apparel Retail–1.42% Ross Stores, Inc. 29,468 3,533,508 Electronic Equipment & Instruments–2.15% (b) Keysight Technologies, Inc. 37,390 5,361,726 Apparel, Accessories & Luxury Goods–0.75% Tapestry, Inc. 45,472 1,873,901 Environmental & Facilities Services–1.72% Republic Services, Inc. 43,052 4,277,216 Application Software–6.18% (b) Aspen Technology, Inc. 9,886 1,426,846 Financial Exchanges & Data–2.43% Citrix Systems, Inc. 12,132 1,702,848 Intercontinental Exchange, Inc. 31,186 3,482,853 Manhattan Associates, Inc.(b) 32,246 3,785,035 Tradeweb Markets, Inc., Class A 34,622 2,562,028 Paylocity Holding Corp.(b) 13,296 2,391,020 6,044,881 Q2 Holdings, Inc.(b) 11,477 1,149,995 Synopsys, Inc.(b) 19,925 4,937,017 Food Distributors–1.43% Sysco Corp. 45,350 3,570,859 15,392,761 Gas Utilities–2.40% Asset Management & Custody Banks–1.02% Atmos Energy Corp. 37,397 3,696,693 Northern Trust Corp. 24,104 2,533,571 Southwest Gas Holdings, Inc. 33,060 2,271,553 Auto Parts & Equipment–1.06% 5,968,246 Visteon Corp.(b) 21,592 2,633,144 General Merchandise Stores–1.01% Automotive Retail–2.88% Dollar General Corp. -

Dodge & Cox Stock Fund Fact Sheet Dated June 30, 2021
June 30, 2021 TICKER SYMBOL Stock Fund DODGX Objectives . The Fund seeks long-term growth of principal and income. A secondary objective is to achieve a reasonable current income. Strategy . The Fund invests primarily in a diversified portfolio of U.S. equity securities. In selecting investments, the Fund typically invests in companies that, in Dodge & Cox’s opinion, appear to be temporarily undervalued by the stock market but have a favorable outlook for long-term growth. The Fund focuses on the underlying financial condition and prospects of individual companies, including future earnings, cash flow, and dividends. Various other factors, including financial strength, economic condition, competitive advantage, quality of the business franchise, and the reputation, experience, and competence of a company’s management are weighed against valuation in selecting individual securities. Risks . The Fund is subject to market risk, meaning holdings in the Fund may decline in value for extended periods due to the financial prospects of individual companies or due to general market and economic conditions. Please read the prospectus for specific details regarding the Fund’s risk profile. General Information Asset Allocation Net Asset Value Per Share $239.56 Total Net Assets (billions) $89.2 Expense Ratio 0.52% Equity Portfolio Turnover Rate (1/1/21 to 6/30/21, unannualized) 9% Securities: 98.3% 30-Day SEC Yield(a) 1.04% Active Share(b) 84% Number of Companies 66 Fund Inception 1965 No sales charges or distribution fees Net Cash Investment Manager: Dodge & Cox, San Francisco. Managed by the U.S. Equity & Other:(f) 1.7% Investment Committee, whose nine members’ average tenure at Dodge & Cox is 23 years. -

Expectations & Experiences
Expectations & Experiences Channels and New Entrants Summary Presentation of the Quarterly U.S. Consumer Trends Survey 2020 2020 Expectations & Experiences: Channels and New Entrants is a quarterly U.S. consumer trends survey sponsored by Fiserv. One of the longest running surveys of its kind, Expectations & Experiences builds on years of consumer survey data. The survey provides insight into people’s financial attitudes and needs, enabling organizations to design and drive adoption of services that improve consumer financial health, loyaltyFORTUNE World's and Most Admired satisfaction. Companies® 2 © 2020 Fiserv, Inc. or its affiliates. | CONFIDENTIAL – INTERNAL 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 Research Method SURVEY • Self-administered online survey METHOD • 19 minutes (median length) FIELD • February 28–March 17, 2020 PERIOD Data collection was largely completed before the WHO declared the novel coronavirus ! outbreak a pandemic on March 11 and the U.S. declared a national emergency on March 13 • Resides in U.S. SCREENING • 18+ years old • Has a checking account CRITERIA • Used checking account to pay bill or make a purchase in past 30 days • GenPop SAMPLE • Final n=3,003 • The data were weighted to ensure that relevant demographic characteristics of the sample matched those of the U.S. general population. All respondents (not only those who met the qualifying criteria) were weighted to U.S. Census WEIGHTING Bureau demographic profiles for the U.S. population, age 18+ on education, age, gender, race, income, region, household size and number of hours spent on the Internet (with targets for this variable coming from Nielsen Scarborough) FORTUNE World's Most Admired Companies® 3 © 2020 Fiserv, Inc. -

Item 8 MEETING DATE: November 20, 2019
Board of Retirement Regular Meeting Sacramento County Employees’ Retirement System Agenda Item 8 MEETING DATE: November 20, 2019 SUBJECT: Monthly Investment Manager Activity, Compliance, and Watch List Report – October 2019 Deliberation Receive SUBMITTED FOR: X Consent and Action and File RECOMMENDATION Staff recommends the Board receive and file the Monthly Investment Manager Activity, Compliance, and Watch List report for October 2019. PURPOSE This item complies with SCERS’ investment policy statement reporting requirements and contributes to the effective management and oversight of investment activities. DISCUSSION SCERS’ investment manager transactions have been reviewed for compliance with their respective investment guidelines and objectives. No compliance violations have been found. As of October 31, 2019, investment managers on the Watch List include: 1. AQR Capital Management (Diversifying Absolute Return) Staff and the investment consultants will continue to monitor the performance and/or organizational concerns for SCERS’ investment managers and update the Watch List accordingly. ATTACHMENTS 1. Monthly Investment Manager Activity, Compliance, and Watch List Report – October 2019 2. Watch List with Commentary Report – October 2019 November 20, 2019 Page 2 of 2 Agenda Item 8 Prepared by: /S/ ___________________________ Brian Miller Investment Officer Reviewed by: /S/ /S/ ____________________________ ____________________________ Steve Davis Eric Stern Chief Investment Officer Chief Executive Officer SACRAMENTO COUNTY EMPLOYEES' -

Torrayresolute Concentrated Large Growth
QUARTERLY COMMENTARY March 31, 2020 Before reviewing the results of the first quarter, we would like to say that our thoughts are with all those directly and indirectly impacted by COVID-19. We are particularly grateful to the healthcare workers and first responders who are putting their lives at risk for our well-being. During this strange period of self-quarantine, it has been particularly helpful to speak with our clients and partners as we all learn to navigate an unfamiliar environment. We would like you to know that our team has been able to maintain operations without interruption and as always, we welcome your questions and observations. We look forward to hearing from you and wish that you remain safe and well. TorrayResolute Concentrated Large Growth Market Overview It would not be hyperbole to say the beginning of 2020 is proving to be among the most challenging periods for investors ever. The rapid spread of the coronavirus pandemic continues to produce historic market volatility, leaving investors with few scientific facts or economic precedents on which to base their decisions. It is something of a cliché to say that markets hate uncertainty, but true, nonetheless. It took just 17 trading days between February 19th and March 13th to bring the longest running bull market (11 years) to a conclusive end. In contrast to the financial crisis of ’08 and ’09, the monetary and fiscal The magnitude and duration of response has been swift and decisive. While the efficacy of these measures the economic downturn are not will be borne out in the coming weeks and months, the market’s direction will only dependent on how quickly be largely dictated by the trajectory of the disease.