October 2006
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet... the Final Frontier. an Ethnographic Account. Exploring the Cultural Space of the Net from the Inside. Mit CD-Rom
Schriftenreihe der Abteilung "Organisation und Technikgenese" des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung FS II 2000- Internet… The Final Frontier: An Ethnographic Account Exploring the cultural space of the Net from the inside Sabine Helmers, Ute Hoffmann & Jeanette Hofmann Projektgruppe Kulturraum Internet http://duplox.wz-berlin.de Institute for Social Sciences Technical University Berlin and Social Science Research Center Berlin (WZB) Reichpietschufer 50, D-10785 Berlin Telefon (030) 25491-0, Fax (030) 25491-684 Abstract The research project "The Internet as a space for interaction", which completed its mission in Autumn 1998, studied the constitutive features of network culture and network organisation. Special emphasis was given to the dynamic interplay of technical and social conventions regarding both the Net's organisation as well as its change. The ethnographic perspective chosen studied the Internet from the inside. Research concentrated upon three fields of study: the hegemonial operating technology of net nodes (UNIX) the network's basic transmission technology (the Internet Protocol IP) and a popular communication service (Usenet). The project's final report includes the results of the three branches explored. Drawing upon the development in the three fields it is shown that changes that come about on the Net are neither anarchic nor arbitrary. Instead, the decentrally organised Internet is based upon technically and organisationally distributed forms of coordination -

Internet Hall of Fame Announces 2013 Inductees
Internet Hall of Fame Announces 2013 Inductees Influential engineers, activists, and entrepreneurs changed history through their vision and determination Ceremony to be held 3 August in Berlin, Germany [Washington, D.C. and Geneva, Switzerland -- 26 June 2013] The Internet Society today announced the names of the 32 individuals who have been selected for induction into the Internet Hall of Fame. Honored for their groundbreaking contributions to the global Internet, this year’s inductees comprise some of the world’s most influential engineers, activists, innovators, and entrepreneurs. The Internet Hall of Fame celebrates Internet visionaries, innovators, and leaders from around the world who believed in the design and potential of an open Internet and, through their work, helped change the way we live and work today. The 2013 Internet Hall of Fame inductees are: Pioneers Circle – Recognizing individuals who were instrumental in the early design and development of the Internet: David Clark, David Farber, Howard Frank, Kanchana Kanchanasut, J.C.R. Licklider (posthumous), Bob Metcalfe, Jun Murai, Kees Neggers, Nii Narku Quaynor, Glenn Ricart, Robert Taylor, Stephen Wolff, Werner Zorn Innovators – Recognizing individuals who made outstanding technological, commercial, or policy advances and helped to expand the Internet’s reach: Marc Andreessen, John Perry Barlow, Anne-Marie Eklund Löwinder, François Flückiger, Stephen Kent, Henning Schulzrinne, Richard Stallman, Aaron Swartz (posthumous), Jimmy Wales Global Connectors – Recognizing individuals from around the world who have made significant contributions to the global growth and use of the Internet: Karen Banks, Gihan Dias, Anriette Esterhuysen, Steven Goldstein, Teus Hagen, Ida Holz, Qiheng Hu, Haruhisa Ishida (posthumous), Barry Leiner (posthumous), George Sadowsky “This year’s inductees represent a group of people as diverse and dynamic as the Internet itself,” noted Internet Society President and CEO Lynn St. -

Interview Teus Hagen, Oprichter Van Internetvoorloper Eunet
Interview Teus Hagen, oprichter van Internetvoorloper EUnet ‘De anarchie van de beginperiode was het leukst’ Als voorzitter van de verenigingen voor gebruikers van Unix- computers in Europa en Nederland liep Teus Hagen voorop in het creëren van Europese computernetwerken. Hij haalde het Europese centrum van het EUnet in 1982 naar Amsterdam en legde de basis voor dominantie van de hoofdstad in Europees internet. Loopbaan 1975-1985 Hoofd computerlaboratorium Centrum voor Wiskunde en Informatica., 1985-1986 Softwareontwikkelaar Ace 1986-1997 Onderzoeker Océ-R&D Verder: 1978-heden Oprichter, voorzitter en erelid Nederlandse Unix Gebruikersgroep NLUUG 1980-1989 Oprichter en voorzitter European Unix Users Group 1982-1984 Oprichter en voorzitter EUnet 1997-2007 Bestuurder (voorzitter) en algemeen directeur Stichting NLnet2013 Opname in Internet Hall of Fame Foto’s: Frank Groeliken Tekst: Peter Olsthoorn 1 Teus Hagen toont een eerste adresboek met alle aangesloten partijen op Eunet. Maart 1983, met adressen, telefoonnummers, e-mail adressen en Eunet knooppunten. “Dat zou vandaag de dag niet meer kunnen gezien de omvang van het aantal aangesloten hosts op internet, maar ook niet vanwege privacy. Dit bewijst ook dat we ons in het begin niet bekommerden om privacy en beveiliging. Dat waren geen onderwerpen, want er waren geen bedreigingen. Leuk is dat degenen die zich er toen mee bezighielden ook nu nog meedoen, en vaak actief bezig zijn met privacy en beveiliging. We zijn ons daar veel meer zorgen om gaan maken.” (Hagen draagt een T-shirt van de Electronic Frontier Foundation – EFF – een organisatie die zich sterk maakt voor privacy, met krachtig verzet tegen de NSA-spionage) Boeiend begin in kleine kring? “De beginperiode was anarchistisch en voor mij eigenlijk de leukste periode. -

Internet... the Final Frontier. Eine Ethnographie. Schlußbericht Des Projekts 'Interaktionsraum Internet. Netzkultur Und Ne
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Research Papers in Economics econstor www.econstor.eu Der Open-Access-Publikationsserver der ZBW – Leibniz-Informationszentrum Wirtschaft The Open Access Publication Server of the ZBW – Leibniz Information Centre for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112 Provided in cooperation with: Wissenschaftszentrum Berlin für Sozialforschung (WZB) Suggested citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (1998) : Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation, Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit- Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112, http:// hdl.handle.net/10419/49813 Nutzungsbedingungen: Terms of use: Die ZBW räumt Ihnen als Nutzerin/Nutzer das unentgeltliche, The ZBW grants you, the user, the non-exclusive right to use räumlich unbeschränkte und zeitlich auf die Dauer des Schutzrechts the selected work free of charge, territorially unrestricted and beschränkte einfache Recht ein, das ausgewählte Werk im Rahmen within the time limit of the term of the property rights according der unter to the terms specified at → http://www.econstor.eu/dspace/Nutzungsbedingungen → http://www.econstor.eu/dspace/Nutzungsbedingungen nachzulesenden vollständigen Nutzungsbedingungen zu By the first use of the selected work the user agrees and vervielfältigen, mit denen die Nutzerin/der Nutzer sich durch die declares to comply with these terms of use. -
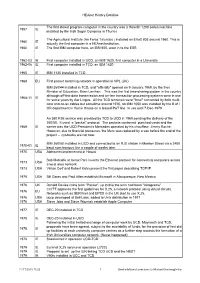
00 Heanet Dateline
HEAnet History Dateline The first stored program computer in the country was a Holerith 1200 series machine 1957 IE installed by the Irish Sugar Company in Thurles The Agricultural Institute (An Foras Taluntais ) installed an Elliott 803 around 1960. This is 1960 IE actually the first computer in a HEAnet institution. 1960 IE The first IBM computer here, an IBM 650, went in to the ESB 1962-03 IE First computer installed in UCD, an IBM 1620, first computer in a University 1962-06 IE First computer installed in TCD, an IBM 1620 1965 IE IBM 1130 installed in TCD 1968 EU First packet switching network in operation in NPL (UK) IBM 360/44 installed in TCD, and "officially" opened on 9 January,1969, by the then Minister of Education, Brian Lenihan. This was the first time-sharing system in the country although off-line data transmission and on-line transaction processing systems were in use 1968-11 IE for some years by Aer Lingus. All the TCD terminals were "local" connected by both multi- core and co-ax cables but sometime around 1970, an IBM 1050 was installed by the B of I OR department in Hume House on a leased P&T line. In use until 7-Dec-1979 An 360 RJE service was provided by TCD to UCD in 1969 pending the delivery of the 360/50. It used a "packet" protocol. The packets contained punched cards and the 1969 IE carrier was the UCD President's Mercedes operated by his chauffeur, Jimmy Roche. However, due to financial pressures, the Merc was replaced by a van before the end of the project - cut-backs are not new. -

BY Kathleen Stansberry, Janna Anderson and Lee Rainie
FOR RELEASE OCTOBER 28, 2019 BY Kathleen Stansberry, Janna Anderson and Lee Rainie FOR MEDIA OR OTHER INQUIRIES: Lee Rainie, Director, Internet and Technology Research Kathleen Stansberry, Elon’s Imagining the Internet Center Shawnee Cohn, Communications Manager 202.419.4372 www.pewresearch.org RECOMMENDED CITATION Pew Research Center, October 2019, “Experts Optimistic About the Next 50 Years of Digital Life” 1 PEW RESEARCH CENTER About Pew Research Center Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping America and the world. It does not take policy positions. It conducts public opinion polling, demographic research, content analysis and other data-driven social science research. The Center studies U.S. politics and policy; journalism and media; internet, science and technology; religion and public life; Hispanic trends; global attitudes and trends; and U.S. social and demographic trends. All of the center’s reports are available at www.pewresearch.org. Pew Research Center is a subsidiary of The Pew Charitable Trusts, its primary funder. For this project, Pew Research Center worked with Elon University’s Imagining the Internet Center, which helped conceive the research and collect and analyze the data. © Pew Research Center 2019 www.pewresearch.org 2 PEW RESEARCH CENTER Experts Are Optimistic About the Next 50 Years of Life Online The year 1969 was a pivot point in culture, science and technology. On Jan. 30, the Beatles played their last show. On July 20, the world watched in awe as Neil Armstrong and Edwin “Buzz” Aldrin become the first humans to walk on the moon. -

Experts Optimistic About the Next 50 Years of Digital Life
EMBARGOED UNTIL 12 P.M. EDT, OCT. 28, 2019 Read the full report: https://www.elon.edu/u/imagining/surveys/x-2-internet-50th-2019/ Media Contact: Owen Covington, Elon University [email protected] Experts Optimistic About the Next 50 Years of Digital Life On the 50th anniversary of the first host-to-host computer connection of ARPANET, experts predict digital life will primarily change humans’ existence for the better over the next 50 years, but they also warn of the need to better serve individuals’ rights, security, safety and equality ELON, N.C. (Oct. 28, 2019) – Experts say digital life will mostly bring positive Changes over the next 50 years, but they warn these benefits will only happen if people embrace reforms allowing better cooperation, security, basic rights and economic fairness, according to a new report by Elon University’s Imagining the Internet Center and Pew Research. “The Next 50 Years of Digital Life” report, part of a 15-years-plus series about the future of the internet, features insights from 530 teChnology pioneers, innovators, developers, business and poliCy leaders, researchers and activists. In celebration of the Oct. 29, 2019, 50th anniversary of the first computer-to- computer connection of the Internet’s precursor, the ARPANET, they were asked to respond to a series of questions about how individuals’ lives might be affected by the evolution of the internet over the next 50 years. Overall, 72% of these respondents said they hope and expect that the next 50 years might bring significant change for the better; 25% say they fear there could be significant change for the worse and 3% said they expect there will be no significant change. -
Nlnet Foundation Annual Report 2017
Annual // Report 2017 Since 1997 NLnet foundation (after its historical contribution to the early internet inside and outside of Europe) has been financially supporting organizations and people that contribute to an open information society It funds those with ideas to fi# the safety$ robustness and pri%acy of the internet The articles of association for the NLnet foundation state' "to promote the exchange of electronic information and all that is related or beneficial to that purpose" Stichting NLnet is a recognised philantropic non(profit foundation according to the Netherlands Ta# Authority (*elastingdienst) The internet has no borders$ and neither does NLnet It operates internationally$ and is dri%en by donations from indi%iduals and from pri%ate and public organisations NLnet is independent$ and all pro+ects are based on open standards$ open source soft"are$ hardware and content Annual Report NLnet Foundation 2017 1 Introduction L.S., 2017 was a year of celebration for NLnet. It was an incredible 35 years ago this year when NLnet's history started with an informal announce ent to a s all grou" of com"!ter people. At the $!ropean %NIX users Spring e'ent in (aris )e!s Hagen re'ealed the E%net, on the face of it a s all initiati'e that would howe'er have ajor conse,!ences. )he Netherlands national center for athe atics, CWI, would act as the central node. A few years down the line the h! ble U%-( infrastruct!re would !nleash the open internet outside of the %SA, and one can e,!ally say it was a critical win for the global adoption of %NI& / which was b!t one of many operating syste s in use at the ti e. -

Netizens: an Anthology Part II - the Past: Where Has It All Come From?
Netizens: An Anthology Part II - The Past: Where Has It All Come From? Chapter 5 The Vision of Interactive Computing And the Future by Michael Hauben What is the reality behind all the talk about the so called “Information Superhighway”? This is an important question which U.S. government policy makers seem to be ignoring. However, understanding the history of the current global computer networks is a crucial step towards building the network of the future. There is a vision that guided the origin and development of the Internet, Usenet and other associated physical and logical networks. What is that vision? While the global computer networks are basically young – the ARPANET started in 1969 – their 25 plus years of growth has been substantial. The ARPANET was the experimental network connecting the mainframe computers of universities and other contractors funded and encouraged by the Advanced Research Projects Agency of the U.S. Department of Defense. The ARPANET started out as a research test bed for computer networking, communication protocols, computer and data resource sharing, etc. However, what it developed into was something surprising. The widest use of the ARPANET was for computer facilitated human-human communication using electronic mail (e-mail) and discussion lists. (Popular lists included Human-Nets, Wine-Tasters and Sci-Fi Lovers lists.) The human communications achievements of ARPANET research continue to be today’s most popular usage of the Net by a growing number and variety of people through e-mail, Usenet discussion groups, mailing lists, internet relay chat, and so on. The ARPANET was the product of previous U.S. -

Inleiding 1: 25 Jaar Internet Met Het CWI, Eunet En Nlnet
Inleiding 1: 25 jaar internet met het CWI, EUnet en NLnet Europees internet begon in feite in 1982 De 17e november 1988 is officieel de dag dat Europa de eerste aansluiting op internet kreeg. Plaats delict: het Centrum voor Wiskunde & Informatica in de Amsterdamse Watergraafsmeer. Dat is het simpele feit, te simpel blijkt. Want, niet enkel volgde er een internetrevolutie, er ging ook het nodige aan vooraf. Pioniers zoals Teus Hagen, Ted Lindgreen, Daniel Karremans, Rob Blokzijl en Piet Beertema en anderen droegen deze belangwekkende Amsterdamse geschiedenis. ’This is to let you know that we have changed the status of this network to connected.’ Deze mededeling kreeg Piet Beertema van het CWI in zijn postbus om 8:28 uur (Oost-Amerikaanse tijd), 14.28 uur in Nederland. Afzender: Rick Adams van het ‘seismo’, het Center for Seismic Studies in Northern Virginia. Krap 10 jaar later werd Adams steenrijk van de verkoop van de eerste Amerikaanse commerciële internetprovider. Beertema en collega’s niet. De statusmededeling aan Beertema ging de jonge geschiedenis in als eerste e-mail tussen Europa en de VS. Klopt niets van. “Dat is echt een broodje aap-verhaal. We hadden al zes of zeven jaar e-mail. Het is vechten tegen de bierkaai om dat verhaal te ontzenuwen”, beaamt Beertema. Het was wel de eerste directe Europese connectie met internet. Al sinds 1982 konden bedrijven en universiteiten op het Europese netwerk van Unix-computers, EUnet genaamd, communiceren met de eerste vormen van het internet in de VS. Mailen, discussies voeren en bestanden uitwisselen met internet was voor 1988 al zes jaar mogelijk. -

Internet... the Final Frontier. an Ethnographic Account. Exploring
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: an ethnographic account: exploring the cultural space of the Net from the inside WZB Discussion Paper, No. FS II 00-101 Provided in Cooperation with: WZB Berlin Social Science Center Suggested Citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (2000) : Internet... the final frontier: an ethnographic account: exploring the cultural space of the Net from the inside, WZB Discussion Paper, No. FS II 00-101, Wissenschaftszentrum Berlin für Sozialforschung (WZB), Berlin This Version is available at: http://hdl.handle.net/10419/49787 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents