Energy Efficiency in Office Computing Environments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evaluating and Optimizing I/O Virtualization in Kernel-Based Virtual Machine (KVM)
Evaluating and Optimizing I/O Virtualization in Kernel-based Virtual Machine (KVM) Binbin Zhang1, Xiaolin Wang1, Rongfeng Lai1, Liang Yang1, Zhenlin Wang2, Yingwei Luo1, and Xiaoming Li1 1 Dept. of Computer Science and Technology, Peking University, Beijing, China, 100871 2 Dept. of Computer Science, Michigan Technological University, Houghton, USA {wxl,lyw}@pku.edu.cn, [email protected] Abstract. I/O virtualization performance is an important problem in KVM. In this paper, we evaluate KVM I/O performance and propose several optimiza- tions for improvement. First, we reduce VM Exits by merging successive I/O instructions and decreasing the frequency of timer interrupt. Second, we simplify the Guest OS by removing redundant operations when the guest OS operates in a virtual environment. We eliminate the operations that are useless in the virtual environment and bypass the I/O scheduling in the Guest OS whose results will be rescheduled in the Host OS. We also change NIC driver’s con- figuration in Guest OS to adapt the virtual environment for better performance. Keywords: Virtualization, KVM, I/O Virtualization, Optimization. 1 Introduction Software emulation is used as the key technique in I/O device virtualization in Ker- nel-based Virtual Machine (KVM). KVM uses a kernel module to intercept I/O re- quests from a Guest OS, and passes them to QEMU, an emulator running on the user space of Host OS. QEMU translates these requests into system calls to the Host OS, which will access the physical devices via device drivers. This implementation of VMM is simple, but the performance is usually not satisfactory because multiple environments are involved in each I/O operation that results in multiple context switches and long scheduling latency. -

Oracle Solaris: the Carrier-Grade Operating System Technical Brief
An Oracle White Paper February 2011 Oracle Solaris: The Carrier-Grade Operating System Oracle White Paper—Oracle Solaris: The Carrier-Grade OS Executive Summary.............................................................................1 ® Powering Communication—The Oracle Solaris Ecosystem..............3 Integrated and Optimized Stack ......................................................5 End-to-End Security ........................................................................5 Unparalleled Performance and Scalability.......................................6 Increased Reliability ........................................................................7 Unmatched Flexibility ......................................................................7 SCOPE Alliance ..............................................................................7 Security................................................................................................8 Security Hardening and Monitoring .................................................8 Process and User Rights Management...........................................9 Network Security and Encrypted Communications .......................10 Virtualization ......................................................................................13 Oracle VM Server for SPARC .......................................................13 Oracle Solaris Zones .....................................................................14 Virtualized Networking...................................................................15 -

Tampere University Research Portal
Tampereen teknillinen yliopisto. Julkaisu 800 Tampere University of Technology. Publication 800 Francis Tam Service Availability Standards for Carrier-Grade Platforms: Creation and Deployment in Mobile Networks Thesis for the degree of Doctor of Technology to be presented with due permission for public examination and criticism in Tietotalo Building, Auditorium TB222, at Tampere University of Technology, on the 15th of May 2009, at 12 noon. Tampereen teknillinen yliopisto - Tampere University of Technology Tampere 2009 ISBN 978-952-15-2134-8 (printed) ISBN 978-952-15-2158-4 (PDF) ISSN 1459-2045 Abstract The rapid development of the mobile network industry has raised considerably the expectations and requirements of the whole chain of stakeholders, from the end users through the mobile network operators and ultimately to the network equipment providers. A key expectation from an end user is service availability, which is a perception that services are continuously operational even in the presence of failures in the mobile network. Network equipment providers have been using carrier-grade platforms to provide various support functions including high availability as reusable assets for products creation. The term carrier-grade refers to a class of systems used in public telecommunications network that deliver up to five nines or six nines (99.999% or 99.9999%) availability. The convergence of communications and information technology in the industry has led to more competition and pressure to reduce development efforts. By creating a service availability standard, Commercial Off-The-Shelf (COTS) software can be bought and integrated into a carrier-grade platform, enabling a company to focus on the core business and concentrate the resource investment onto new innovations. -

Virtualizing Your Network: Benefits & Challenges
Network Monitoring Technology Virtualizing Your Network: Benefits & Challenges What is Virtualization? factory or process plant. Virtualization can give this software Gartner Research1 defined network virtualization as the a longer operating lifecycle time, and can save both costs process of combining hardware and software network and intellectual property. resources and functionality into a single virtual network. This offers access to routing features and data streams that can provide newer, service-aware, resilient solutions; newer security services that are native within network elements; support for subscriber-aware policy control for peer-to- peer traffic management; and application-aware, real-time session control for converged voice and video applications with guaranteed bandwidth on-demand. For the most part, when we speak of virtualization, we speak of hardware virtualization. That means that we create, on a host machine, a virtual machine that looks like another computer with an operating system and software. The software on the virtual machine is separate from the host machine’s resources, and as far as it is concerned, it is running on its own computer (that we call the guest). Both in information technology (IT) and in operational technology (OT) environments the benefits of virtualization have led to its rapid adoption. This white paper is not a prescriptive guide to network virtualization, rather it is a high-level overview focused on the benefits and challenges of network virtualization. While it will Desktop virtualization separates the logical desktop from review the benefits, it will also cover the specific challenges the actual hardware. Virtual desktop infrastructure (VDI) network administrators and their respective businesses should permits the user to interact with the computer through understand to cost-effectively apply this technology to gain another host computer or device on a network connection. -

Wireless Network Virtualization: Ensuring Carrier Grade Availability
™ AN INTEL COMPANY Wireless Network Virtualization: Ensuring Carrier Grade Availability WHEN IT MATTERS, IT RUNS ON WIND RIVER WIRELESS NETWORK VIRTUALIZATION: ENSURING CARRIER GRADE AVAILABILITY EXECUTIVE SUMMARY The wireless industry’s battle to acquire new subscribers and retain existing ones is accelerating the need for new services. Profit margins are under pressure from the increased infrastructure and operations costs required to satisfy the growing demand. Network functions virtualization (NFV), a rapidly growing initiative in telecom networks, promises to revolutionize how networks are architected and managed. It allows communications service providers (CSPs) to virtualize network functions and consolidate them on standard off-the-shelf servers. Although 4G LTE is effective at meeting the increasing bandwidth demands at lower costs than its predecessors, its mobile base station, E-UTRAN Node B (eNB), located at the edge of the radio access network (RAN), is underutilized at certain times of the day and has grown in complexity, resulting in higher downtime and field maintenance costs. As a result, the eNB is a good candidate for NFV. Cloud-RAN (C-RAN) is the virtualization of the eNB’s control plane and data plane functions, consolidating it in one or more data centers. The result is significantly higher equipment utilization, cost-efficient redundancy to achieve high availability, and lower operations and maintenance costs. However, to realize these benefits, the foundation for virtualized eNBs must be a robust, carrier grade NFV platform that incorporates advanced fault management features. Poor implementation results in lower quality execution with excessive outage and maintenance costs. Wind River® Titanium Cloud is the industry’s first NFV-ready solution that incorporates advanced carrier grade fault, security, performance, and network management features. -

Carrier Grade Virtualization
Carrier Grade Virtualization Leveraging virtualization in Carrier Grade Systems Abstract Network Equipment Providers (NEPs) have been building networking infrastructure equipment able to deliver “carrier grade” services, typically mission-critical services such as voice telephony. In decades past, NEPs have achieved high degrees of availability through purpose-built hardware and software implementations. Today they increasingly build on COTS (Commercial Off The Shelf) hardware and Open Source Software (OSS), freeing their engineering resources to focus on core telephony competencies. The move to COTS and OSS requires that these hardware and software components be available from an ecosystem of suppliers, and that they interoperate seamlessly. Bodies such as The Linux Foundation (LF), the Service Availability Forum (SA Forum) and PICMG have defined standards and specifications such as carrier grade OSes (CGLinux), Service Availability Forum APIs and AdvancedTCA hardware to target carrier grade applications. Recent advances have made virtualization appealing for carrier class equipment by permitting significant cost reduction through consolidation of workloads and of physical hardware. Virtualization also transparently lets NEPs and other OEMs (Original Equipment Manufacturers) leverage multi-core processors to run legacy software designed for uniprocessor hardware. However, virtualization needs to meet specific requirements to enable network equipment deploying this technology to meet industry expectations for carrier grade systems. This -

Carrier Grade Linux Requirements Definition
Carrier Grade Linux Requirements Definition The Linux Foundation Version 5.0 1796 18th Street S u i t e C Prepared by the Carrier Grade Linux Working Group San Francisco CA 94107, USA Copyright (c) 2005, 2006, 2007, 2011 by The Linux +1 (415) 723 - 9 7 0 9 Foundation. This material may be distributed only subject to the terms and conditions set forth in the Open Publication License, v1.0 or later (the latest version is available at http://www.opencontent.org/opl.shtml/). Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder. Linux is a Registered Trademark of Linus Torvalds. Other company, product, or service names may be the trademarks of others. CONTRIBUTORS TO THE CGL 5.0 REQUIREMENTS DEFINITION INCLUDE (IN ALPHABETICAL ORDER): Last Name First Name Company Anderson Matt HP Anderson Tim MontaVista Software Awad Majid Intel Aziz Khalid HP Badovinatz Peter IBM Bozarth Brad Cisco Cauchy Dan MontaVista Software Chacron Eric Alcatel Chen Terence Intel Cherry John OSDL Christopher Johnson Sun Microsystems Cihula Jospeh Intel Cress Andrew Intel Dague Sean IBM Dake Steven MontaVista Software Flaxa Ralf Novell Fleischer Julie Intel Fleischer Julie OSDL Fox Kevin Sun Microsystems Gross Mark Intel Haddad Ibrahim Ericsson Heber Troy HP Howell David P. Intel Hu Michael Radisys Ikebe Takashi NTT Ishitsuka Seiichi NEC Jagana Venkata IBM Johnson Christopher P. Sun Microsystems Kevin Fox Sun Microsystems Kimura Masato NTT Comware Krauska Joel Cisco Kukkonen Mika Nokia La Monte.H.P Yarrol Timesys Lavonius Ville Nokia Liu Bing Wei Intel Lynch Rusty Intel * MacDonald Joe Wind River Systems Manas Saksena Timesys Nakayama Mitsuo NEC Peter-Gonzalez Inaky Intel Pourzandi Makan Ericsson Rossi Frederic Eicsson Saksena Manas Timesys Sakuma Junichi OSDL Saskena Manas Timesys Seiler Glenn Wind River Systems Smarduch Mario Motorola Takamiya Noriaki NTT Software Weijers Gé Witham Timothy D. -

Network Virtualization for Dummies®, Vmware Special Edition Published by John Wiley & Sons, Inc
These materials are © 2016 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized use is strictly prohibited. Network Virtualization VMware Special Edition by Mora Gozani These materials are © 2016 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized use is strictly prohibited. Network Virtualization For Dummies®, VMware Special Edition Published by John Wiley & Sons, Inc. 111 River St. Hoboken, NJ 07030‐5774 www.wiley.com Copyright © 2016 by John Wiley & Sons, Inc., Hoboken, New Jersey No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748‐6011, fax (201) 748‐6008, or online at http://www.wiley.com/go/permissions. Trademarks: Wiley, For Dummies, the Dummies Man logo, The Dummies Way, Dummies.com, Making Everything Easier, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or its affiliates in the United States and other countries, and may not be used without written permission. VMware, vSphere, and vRealize are registered trademarks and VMware NSX and VMware vRealize Operations, and vRealize Automation are trademarks of VMware, Inc. All other trademarks are the property of their respective owners. John Wiley & Sons, Inc., is not associ- ated with any product or vendor mentioned in this book. -

Read Book Hyper-V Network Virtualization Cookbook Ebook
HYPER-V NETWORK VIRTUALIZATION COOKBOOK PDF, EPUB, EBOOK Ryan Boud | 228 pages | 02 Dec 2014 | Packt Publishing Limited | 9781782177807 | English | Birmingham, United Kingdom Hyper-V Network Virtualization Cookbook PDF Book In , Slack faced a problem: the load on its backend servers had increased by 1,x. The Best Tech Newsletter Anywhere Join , subscribers and get a daily digest of news, geek trivia, and our feature articles. Case studies How Slack rearchitected its system to achieve zero downtime and improve latency, reliability and availability In , Slack faced a problem: the load on its backend servers had increased by 1,x. For one thing, VPN servers are located all over the world. We still need to add the other hard drives. Each IDE Controller only has two slots available for adding drives. Networking Fundamentals Read how we developed our new breakthrough NLP-powered feature. The Best Tech Newsletter Anywhere Join , subscribers and get a daily digest of news, geek trivia, and our feature articles. Here is how to change what gets switched back on. Now navigate to the exported virtual machine and be sure to select folder that your virtual machine was exported into. Since we launched in , our articles have been read more than 1 billion times. Security and privacy are big concerns these days, particularly when it comes to dealing with sensitive information on the internet. The wizard allows the disk geometry to be changed, which can be handy if a drive has become close to full and a little more breathing room is needed. By submitting your email, you agree to the Terms of Use and Privacy Policy. -
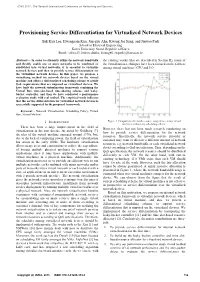
Provisioning Service Differentiation for Virtualized Network Devices
ICNS 2011 : The Seventh International Conference on Networking and Services Provisioning Service Differentiation for Virtualized Network Devices Suk Kyu Lee, Hwangnam Kim, Jun-gyu Ahn, Kwang Jae Sung, and Jinwoo Park School of Electrical Engineering Korea University, Seoul, Republic of Korea Email: {sklee25, hnkim, dubhe, kjsung80, jwpark}@korea.ac.kr Abstract— In order to efficiently utilize the network bandwidth the existing works (that are described in Section II), many of and flexibly enable one or more networks to be combined or the virtualization techniques have been focused on the fairness subdivided into virtual networks, it is essential to virtualize among virtual machines’ CPU and I/O. network devices and then to provide service differentiation for the virtualized network devices. In this paper, we propose a virtualizing method for network devices based on the virtual machine and offers a differentiated scheduling scheme to satisfy QoS requirements that are imposed on virtualized devices. We have built the network virtualization framework combining the Virtual Box, time-slot-based time-sharing scheme, and leaky- bucket controller, and then we have conducted a performance evaluation study with real testbed. The empirical study indicates that the service differentiation for virtualized network devices is successfully supported by the proposed framework. Keywords - Network Virtualization, Scheduling Policy, Virtual Box, Virtual Machine I. INTRODUCTION Figure 1. Comparison of network resource usage between two virtual machines without any scheduling scheme. There has been a large improvement in the field of However, there has not been much research conducting on virtualization in the past decade. As noted by Goldberg [7], how to provide service differentiation for the network the idea of the virtual machine emerged around 1970s, but, resources. -

Virtualization Basics: Understanding Techniques and Fundamentals
Virtualization Basics: Understanding Techniques and Fundamentals Hyungro Lee School of Informatics and Computing, Indiana University 815 E 10th St. Bloomington, IN 47408 [email protected] ABSTRACT example of growing involvement in virtualization technolo- Virtualization is a fundamental part of cloud computing, gies with the cloud. Early technologies and developments especially in delivering Infrastructure as a Service (IaaS). in the virtualization have been accomplished by some com- Exploring different techniques and architectures of the vir- panies such as IBM from 1967 and VMware from 1998. In tualization helps us understand the basic knowledge of virtu- open source communities, Xen, KVM, Linux-vServer, LXC alization and the server consolidation in the cloud with x86 and others have supported virtualization in different plat- architecture. This paper describes virtualization technolo- forms with different approaches. In this paper, x86 archi- gies, architectures and optimizations regarding the sharing tecture virtualization will be discussed with these historical CPU, memory and I/O devices on x86 virtual machine mon- changes. itor. In cloud computing, Infrastructure-as-a-Service (IaaS) pro- vides on-demand virtual machine instances with virtualiza- Categories and Subject Descriptors tion technologies. IaaS has been broadly used to provide re- C.0 [General]: Hardware/software interface; C.4 [Performance quired compute resources in shared resource environments. of systems]: Performance attributes; D.4.7 [Operating Amazon Web Services (AWS), Google Compute Engine, Mi- Systems]: Organization and design crosoft Windows Azure, and HP Cloud offer commercial cloud services. OpenStack, Eucalyptus, SaltStack, Nimbus, General Terms and many others provide private open source cloud plat- Performance, Design forms with community support in development. -

Data Center Server Virtualization Solution Using Microsoft Hyper-V
St. Cloud State University theRepository at St. Cloud State Culminating Projects in Information Assurance Department of Information Systems 5-2017 Data Center Server Virtualization Solution Using Microsoft yH per-V Sujitha Dandu St Cloud State University, [email protected] Follow this and additional works at: https://repository.stcloudstate.edu/msia_etds Recommended Citation Dandu, Sujitha, "Data Center Server Virtualization Solution Using Microsoft yH per-V" (2017). Culminating Projects in Information Assurance. 23. https://repository.stcloudstate.edu/msia_etds/23 This Starred Paper is brought to you for free and open access by the Department of Information Systems at theRepository at St. Cloud State. It has been accepted for inclusion in Culminating Projects in Information Assurance by an authorized administrator of theRepository at St. Cloud State. For more information, please contact [email protected]. Datacenter Server Virtualization Solution Using Microsoft Hyper-V by Sujitha Dandu A Starred Paper Submitted to the Graduate Faculty of St. Cloud State University in Partial Fulfillment of the Requirements for the Degree of Master of Information Assurance February, 2017 Starred Paper Committee: Dr. Dennis Guster, Chairperson Dr. Susantha Herath Dr. Balasubramanian Kasi 2 Abstract Cloud Computing has helped businesses scale within minutes and take their services to their customers much faster. Virtualization is considered the core-computing layer of a cloud setup. All the problems a traditional data center environment like space, power, resilience, centralized data management, and rapid deployment of servers as per business need have been solved with the introduction of Hyper-V (a server virtualization solution from Microsoft). Now companies can deploy multiple servers and applications with just a click and they can also centrally manage the data storage.