Network Virtualization: State of the Art and Research Challenges N.M
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evaluating and Optimizing I/O Virtualization in Kernel-Based Virtual Machine (KVM)
Evaluating and Optimizing I/O Virtualization in Kernel-based Virtual Machine (KVM) Binbin Zhang1, Xiaolin Wang1, Rongfeng Lai1, Liang Yang1, Zhenlin Wang2, Yingwei Luo1, and Xiaoming Li1 1 Dept. of Computer Science and Technology, Peking University, Beijing, China, 100871 2 Dept. of Computer Science, Michigan Technological University, Houghton, USA {wxl,lyw}@pku.edu.cn, [email protected] Abstract. I/O virtualization performance is an important problem in KVM. In this paper, we evaluate KVM I/O performance and propose several optimiza- tions for improvement. First, we reduce VM Exits by merging successive I/O instructions and decreasing the frequency of timer interrupt. Second, we simplify the Guest OS by removing redundant operations when the guest OS operates in a virtual environment. We eliminate the operations that are useless in the virtual environment and bypass the I/O scheduling in the Guest OS whose results will be rescheduled in the Host OS. We also change NIC driver’s con- figuration in Guest OS to adapt the virtual environment for better performance. Keywords: Virtualization, KVM, I/O Virtualization, Optimization. 1 Introduction Software emulation is used as the key technique in I/O device virtualization in Ker- nel-based Virtual Machine (KVM). KVM uses a kernel module to intercept I/O re- quests from a Guest OS, and passes them to QEMU, an emulator running on the user space of Host OS. QEMU translates these requests into system calls to the Host OS, which will access the physical devices via device drivers. This implementation of VMM is simple, but the performance is usually not satisfactory because multiple environments are involved in each I/O operation that results in multiple context switches and long scheduling latency. -

Virtualizing Your Network: Benefits & Challenges
Network Monitoring Technology Virtualizing Your Network: Benefits & Challenges What is Virtualization? factory or process plant. Virtualization can give this software Gartner Research1 defined network virtualization as the a longer operating lifecycle time, and can save both costs process of combining hardware and software network and intellectual property. resources and functionality into a single virtual network. This offers access to routing features and data streams that can provide newer, service-aware, resilient solutions; newer security services that are native within network elements; support for subscriber-aware policy control for peer-to- peer traffic management; and application-aware, real-time session control for converged voice and video applications with guaranteed bandwidth on-demand. For the most part, when we speak of virtualization, we speak of hardware virtualization. That means that we create, on a host machine, a virtual machine that looks like another computer with an operating system and software. The software on the virtual machine is separate from the host machine’s resources, and as far as it is concerned, it is running on its own computer (that we call the guest). Both in information technology (IT) and in operational technology (OT) environments the benefits of virtualization have led to its rapid adoption. This white paper is not a prescriptive guide to network virtualization, rather it is a high-level overview focused on the benefits and challenges of network virtualization. While it will Desktop virtualization separates the logical desktop from review the benefits, it will also cover the specific challenges the actual hardware. Virtual desktop infrastructure (VDI) network administrators and their respective businesses should permits the user to interact with the computer through understand to cost-effectively apply this technology to gain another host computer or device on a network connection. -

Energy Efficiency in Office Computing Environments
Fakulät für Informatik und Mathematik Universität Passau, Germany Energy Efficiency in Office Computing Environments Andreas Berl Supervisor: Hermann de Meer A thesis submitted for Doctoral Degree March 2011 1. Reviewer: Prof. Hermann de Meer Professor of Computer Networks and Communications University of Passau Innstr. 43 94032 Passau, Germany Email: [email protected] Web: http://www.net.fim.uni-passau.de 2. Reviewer: Prof. David Hutchison Director of InfoLab21 and Professor of Computing Lancaster University LA1 4WA Lancaster, UK Email: [email protected] Web: http://www.infolab21.lancs.ac.uk Abstract The increasing cost of energy and the worldwide desire to reduce CO2 emissions has raised concern about the energy efficiency of information and communica- tion technology. Whilst research has focused on data centres recently, this thesis identifies office computing environments as significant consumers of energy. Office computing environments offer great potential for energy savings: On one hand, such environments consist of a large number of hosts. On the other hand, these hosts often remain turned on 24 hours per day while being underutilised or even idle. This thesis analyzes the energy consumption within office computing environments and suggests an energy-efficient virtualized office environment. The office environment is virtualized to achieve flexible virtualized office resources that enable an energy-based resource management. This resource management stops idle services and idle hosts from consuming resources within the office and consolidates utilised office services on office hosts. This increases the utilisation of some hosts while other hosts are turned off to save energy. The suggested architecture is based on a decentralized approach that can be applied to all kinds of office computing environments, even if no centralized data centre infrastructure is available. -

Network Virtualization for Dummies®, Vmware Special Edition Published by John Wiley & Sons, Inc
These materials are © 2016 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized use is strictly prohibited. Network Virtualization VMware Special Edition by Mora Gozani These materials are © 2016 John Wiley & Sons, Inc. Any dissemination, distribution, or unauthorized use is strictly prohibited. Network Virtualization For Dummies®, VMware Special Edition Published by John Wiley & Sons, Inc. 111 River St. Hoboken, NJ 07030‐5774 www.wiley.com Copyright © 2016 by John Wiley & Sons, Inc., Hoboken, New Jersey No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748‐6011, fax (201) 748‐6008, or online at http://www.wiley.com/go/permissions. Trademarks: Wiley, For Dummies, the Dummies Man logo, The Dummies Way, Dummies.com, Making Everything Easier, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or its affiliates in the United States and other countries, and may not be used without written permission. VMware, vSphere, and vRealize are registered trademarks and VMware NSX and VMware vRealize Operations, and vRealize Automation are trademarks of VMware, Inc. All other trademarks are the property of their respective owners. John Wiley & Sons, Inc., is not associ- ated with any product or vendor mentioned in this book. -

Read Book Hyper-V Network Virtualization Cookbook Ebook
HYPER-V NETWORK VIRTUALIZATION COOKBOOK PDF, EPUB, EBOOK Ryan Boud | 228 pages | 02 Dec 2014 | Packt Publishing Limited | 9781782177807 | English | Birmingham, United Kingdom Hyper-V Network Virtualization Cookbook PDF Book In , Slack faced a problem: the load on its backend servers had increased by 1,x. The Best Tech Newsletter Anywhere Join , subscribers and get a daily digest of news, geek trivia, and our feature articles. Case studies How Slack rearchitected its system to achieve zero downtime and improve latency, reliability and availability In , Slack faced a problem: the load on its backend servers had increased by 1,x. For one thing, VPN servers are located all over the world. We still need to add the other hard drives. Each IDE Controller only has two slots available for adding drives. Networking Fundamentals Read how we developed our new breakthrough NLP-powered feature. The Best Tech Newsletter Anywhere Join , subscribers and get a daily digest of news, geek trivia, and our feature articles. Here is how to change what gets switched back on. Now navigate to the exported virtual machine and be sure to select folder that your virtual machine was exported into. Since we launched in , our articles have been read more than 1 billion times. Security and privacy are big concerns these days, particularly when it comes to dealing with sensitive information on the internet. The wizard allows the disk geometry to be changed, which can be handy if a drive has become close to full and a little more breathing room is needed. By submitting your email, you agree to the Terms of Use and Privacy Policy. -
Provisioning Service Differentiation for Virtualized Network Devices
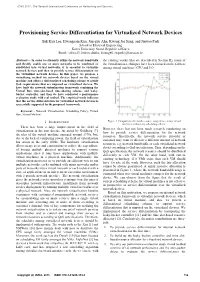
ICNS 2011 : The Seventh International Conference on Networking and Services Provisioning Service Differentiation for Virtualized Network Devices Suk Kyu Lee, Hwangnam Kim, Jun-gyu Ahn, Kwang Jae Sung, and Jinwoo Park School of Electrical Engineering Korea University, Seoul, Republic of Korea Email: {sklee25, hnkim, dubhe, kjsung80, jwpark}@korea.ac.kr Abstract— In order to efficiently utilize the network bandwidth the existing works (that are described in Section II), many of and flexibly enable one or more networks to be combined or the virtualization techniques have been focused on the fairness subdivided into virtual networks, it is essential to virtualize among virtual machines’ CPU and I/O. network devices and then to provide service differentiation for the virtualized network devices. In this paper, we propose a virtualizing method for network devices based on the virtual machine and offers a differentiated scheduling scheme to satisfy QoS requirements that are imposed on virtualized devices. We have built the network virtualization framework combining the Virtual Box, time-slot-based time-sharing scheme, and leaky- bucket controller, and then we have conducted a performance evaluation study with real testbed. The empirical study indicates that the service differentiation for virtualized network devices is successfully supported by the proposed framework. Keywords - Network Virtualization, Scheduling Policy, Virtual Box, Virtual Machine I. INTRODUCTION Figure 1. Comparison of network resource usage between two virtual machines without any scheduling scheme. There has been a large improvement in the field of However, there has not been much research conducting on virtualization in the past decade. As noted by Goldberg [7], how to provide service differentiation for the network the idea of the virtual machine emerged around 1970s, but, resources. -

Virtualization Basics: Understanding Techniques and Fundamentals
Virtualization Basics: Understanding Techniques and Fundamentals Hyungro Lee School of Informatics and Computing, Indiana University 815 E 10th St. Bloomington, IN 47408 [email protected] ABSTRACT example of growing involvement in virtualization technolo- Virtualization is a fundamental part of cloud computing, gies with the cloud. Early technologies and developments especially in delivering Infrastructure as a Service (IaaS). in the virtualization have been accomplished by some com- Exploring different techniques and architectures of the vir- panies such as IBM from 1967 and VMware from 1998. In tualization helps us understand the basic knowledge of virtu- open source communities, Xen, KVM, Linux-vServer, LXC alization and the server consolidation in the cloud with x86 and others have supported virtualization in different plat- architecture. This paper describes virtualization technolo- forms with different approaches. In this paper, x86 archi- gies, architectures and optimizations regarding the sharing tecture virtualization will be discussed with these historical CPU, memory and I/O devices on x86 virtual machine mon- changes. itor. In cloud computing, Infrastructure-as-a-Service (IaaS) pro- vides on-demand virtual machine instances with virtualiza- Categories and Subject Descriptors tion technologies. IaaS has been broadly used to provide re- C.0 [General]: Hardware/software interface; C.4 [Performance quired compute resources in shared resource environments. of systems]: Performance attributes; D.4.7 [Operating Amazon Web Services (AWS), Google Compute Engine, Mi- Systems]: Organization and design crosoft Windows Azure, and HP Cloud offer commercial cloud services. OpenStack, Eucalyptus, SaltStack, Nimbus, General Terms and many others provide private open source cloud plat- Performance, Design forms with community support in development. -

Data Center Server Virtualization Solution Using Microsoft Hyper-V
St. Cloud State University theRepository at St. Cloud State Culminating Projects in Information Assurance Department of Information Systems 5-2017 Data Center Server Virtualization Solution Using Microsoft yH per-V Sujitha Dandu St Cloud State University, [email protected] Follow this and additional works at: https://repository.stcloudstate.edu/msia_etds Recommended Citation Dandu, Sujitha, "Data Center Server Virtualization Solution Using Microsoft yH per-V" (2017). Culminating Projects in Information Assurance. 23. https://repository.stcloudstate.edu/msia_etds/23 This Starred Paper is brought to you for free and open access by the Department of Information Systems at theRepository at St. Cloud State. It has been accepted for inclusion in Culminating Projects in Information Assurance by an authorized administrator of theRepository at St. Cloud State. For more information, please contact [email protected]. Datacenter Server Virtualization Solution Using Microsoft Hyper-V by Sujitha Dandu A Starred Paper Submitted to the Graduate Faculty of St. Cloud State University in Partial Fulfillment of the Requirements for the Degree of Master of Information Assurance February, 2017 Starred Paper Committee: Dr. Dennis Guster, Chairperson Dr. Susantha Herath Dr. Balasubramanian Kasi 2 Abstract Cloud Computing has helped businesses scale within minutes and take their services to their customers much faster. Virtualization is considered the core-computing layer of a cloud setup. All the problems a traditional data center environment like space, power, resilience, centralized data management, and rapid deployment of servers as per business need have been solved with the introduction of Hyper-V (a server virtualization solution from Microsoft). Now companies can deploy multiple servers and applications with just a click and they can also centrally manage the data storage. -

Evaluating Xen, Vmware, and Openvz Virtualization Platforms for Network Virtualization
Evaluating Xen, VMware, and OpenVZ Virtualization Platforms for Network Virtualization Carlo Fragni, Marcelo D. D. Moreira, Diogo M. F. Mattos, Lu´ıs Henrique M. K. Costa, and Otto Carlos M. B. Duarte Universidade Federal do Rio de Janeiro - GTA/PEE/COPPE - Rio de Janeiro, Brazil Abstract—Network virtualization is a technique that allows Native Linux having multiple concurrent isolated networks sharing physi- 1200 Xen cal network resources. This work analyzes the main available VMWare virtualization platforms, Xen, OpenVZ, and VMware, for net- 1000 OpenVZ work virtualization. We compare their virtualization techniques, achieved performance in virtualizing computational resources 800 and appropriateness for usage in a virtual network environment. 600 To achieve our goal, we conduct experiments to evaluate overhead introduced by the virtualization platforms in comparison to a 400 non-virtualized environment. Throughput (in Mb/s) 200 I. OVERVIEW There has been recently great interest in network virtualiza- 0 tion, since it is considered a main component in many propos- Figure 1. Network reception test using large packet size. als for future internet architectures [1]. Network virtualization II. TESTS grants the ability to run concurrent virtual networks using independent network stacks, adding flexibility to the network. Many tests were made to evaluate overhead introduced by In order to implement network virtualization, a virtualization the virtualization tools in comparison to the non virtualized platform must be used. There are three main -

10 YEARS of OPEN VSWITCH SUCCESS and FAILURE BEN PFAFF WHAT IS OPEN VSWITCH? Controller
10 YEARS OF OPEN VSWITCH SUCCESS AND FAILURE BEN PFAFF WHAT IS OPEN VSWITCH? controller Open source project HV • Software switch Ethernet OVS VM • Portable • Programmable • Fast OPEN VSWITCH SUCCESS • Used in NSX on KVM, Windows, and public cloud • Widely used in Xen, KVM, OpenStack • Incumbent targeted by new projects • Over 5,000 academic citations LET'S CELEBRATE! • 2018: ACM SIGCOMM SOSR Software Systems Award. • 2015: NSDI "Best Paper" Award for "The Design and Implementation of Open vSwitch". KEYS TO SUCCESS PEOPLE, TECHNOLOGY, AND ENVIRONMENT ENVIRONMENT • Open source virtualization was exploding, but there was no good virtual switch. • Open vSwitch was in the right place at the right time. It filled a gap. • Nicira founders had relevant academic and business connections. • Nicira founders provided a valuable vision. PEOPLE • OVS had the best people: Justin Pettit, Jesse Gross, Ethan Jackson. Martin Casado: "You end up putting basically your best development resources... on the open source side of the house, which from a company is kind of difficult to do, because you basically want that best developer to work on the core product on the inside." (on "a16 Podcast: Monetizing Open Source", April 10, 2017.) • Nicira had PhD-type innovators: • Links to academics. • Willing and able to do library research and recognize where it was valuable. • Able to step back and consider larger problems. • Kind (by and large). TECHNOLOGY • We didn't know what Nicira needed, so we built OVS to do anything. • No one would want NSX-specific agents except NSX customers. • Lots of open source projects are aimed at one company's use case. -

KVM) Binbin Zhang, Xiaolin Wang, Rongfeng Lai, Liang Yang, Zhenlin Wang, Yingwei Luo, Xiaoming Li
Evaluating and Optimizing I/O Virtualization in Kernel-based Virtual Machine (KVM) Binbin Zhang, Xiaolin Wang, Rongfeng Lai, Liang Yang, Zhenlin Wang, Yingwei Luo, Xiaoming Li To cite this version: Binbin Zhang, Xiaolin Wang, Rongfeng Lai, Liang Yang, Zhenlin Wang, et al.. Evaluating and Op- timizing I/O Virtualization in Kernel-based Virtual Machine (KVM). IFIP International Conference on Network and Parallel Computing (NPC), Sep 2010, Zhengzhou, China. pp.220-231, 10.1007/978- 3-642-15672-4_20. hal-01054988 HAL Id: hal-01054988 https://hal.inria.fr/hal-01054988 Submitted on 11 Aug 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License Evaluating and Optimizing I/O Virtualization in Kernel-based Virtual Machine (KVM) Binbin Zhang1, Xiaolin Wang1, Rongfeng Lai1, Liang Yang1, Zhenlin Wang2, Yingwei Luo1 and Xiaoming Li1 1) Dept. of Computer Science and Technology, Peking University, Beijing, China, 100871 2) Dept. of Computer Science, Michigan Technological University, Houghton, USA {wxl, lyw}@pku.edu.cn, [email protected] Abstract. I/O virtualization performance is an important problem in KVM. In this paper, we evaluate KVM I/O performance and propose several optimizations for improvement. -

Exercise 1 Course Information
STUDY IN ENGLISH STUDY IN ENGLISH Exercises 4 Oracle VirtualBox Network Virtualization Nebojša Bačanin Džakula, PhD [email protected] Faculty of Technical Sciences, Singidunum University Cloud Computing 2019/20 www.study.singidunum.ac.rs STUDY IN ENGLISH Oracle VirtualBox • Oracle VM VirtualBox is a free, open source, cross- platform application for creating, managing and running virtual machines (VMs). • Virtual machines are computers whose hardware components are emulated by the host computer. • It belongs to the Type-2 (hosted hypervisors). • Download link: https://www.vmware.com/products/workstation- pro.html STUDY IN ENGLISH Oracle VirtualBox • Oracle VirtualBox enables you to set up one or more virtual machines (VMs) on a single physical machine, and use them simultaneously, along with the actual machine. • Each virtual machine can execute its own operating system, including versions of Microsoft Windows, Linux, BSD, and MS-DOS. • We can install and run as many virtual machines as we like – the only practical limits are disk space and memory. STUDY IN ENGLISH Oracle VirtualBox • Download link: https://www.virtualbox.org/wiki/Downloads STUDY IN ENGLISH Oracle VirtualBox Network Virtualization • Oracle VM VirtualBox can virtualize the following types of networking hardware: • AMD PCNet PCI II (Am79C970A) • AMD PCNet FAST III (Am79C973), the default setting • Intel PRO/1000 MT Desktop (82540EM) • Intel PRO/1000 T Server (82543GC) • Intel PRO/1000 MT Server (82545EM) • Paravirtualized network adapter (virtio-net) STUDY IN ENGLISH Oracle VirtualBox Network Virtualization • The PCNet FAST III is the default because it is supported by nearly all operating systems, as well as by the GNU GRUB boot manager.