Domestic Terrorism: an Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
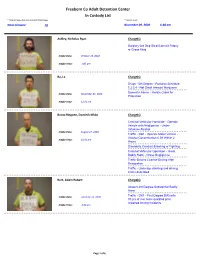
In Custody List **Total Inmates Does Not Include ICE Detainees **Current As Of: Total Inmates: 28 November 09, 2020 6:48 Am
Freeborn Co Adult Detenton Center In Custody List **Total Inmates does not include ICE Detainees **Current as of: Total Inmates: 28 November 09, 2020 6:48 am Ashley, Nicholas Ryan Charge(s) Burglary-3rd Deg-Steal/Commit Felony or Gross Misd Intake Date: October 15, 2020 Intake Time: 1:05 pm Ba, La Charge(s) Drugs - 5th Degree - Possess Schedule 1,2,3,4 - Not Small Amount Marijuana Domestic Abuse - Violate Order for Intake Date: November 01, 2020 Protection Intake Time: 12:21 am Boots-Ringoen, Dominik Nikko Charge(s) Criminal Vehicular Homicide - Operate Vehicle with Negligence - Under Influence Alcohol Intake Date: August 27, 2020 Traffic - DWI - Operate Motor Vehicle - Alcohol Concentration 0.08 Within 2 Intake Time: 10:31 pm Hours Disorderly Conduct-Brawling or Fighting Criminal Vehicular Operation - Great Bodily Harm - Gross Negligence Traffic-Drivers License-Driving After Revocation Traffic - Underage drinking and driving; Crime described Burt, Adam Robert Charge(s) Assault-3rd Degree-Substantial Bodily Harm Traffic - DWI - First-Degree DWI;w/in Intake Date: February 14, 2020 10 yrs of 3 or more qualified prior impaired driving incidents Intake Time: 4:43 pm Page 1 of 6 Everet, Michael Leonard Charge(s) Harassment; Restraining Order - Violate and knows of temporary or restraining order Intake Date: November 06, 2020 Intake Time: 5:53 pm Fishel, Adam Dwayne Charge(s) Fleeing a Peace Officer in a Motor Vehicle Traffic - DWI - Operate Motor Vehicle - Intake Date: November 01, 2020 Alcohol Concentration 0.08 Within 2 Hours Intake Time: -

Fire and Arson Scene Evidence: a Guide for Public Safety Personnel
U.S. Department of Justice Office of Justice Programs National Institute of Justice FireFire andand ArsonArson SceneScene Evidence:Evidence: A Guide for Public Safety Personnel Research Report U.S. Department of Justice Office of Justice Programs 810 Seventh Street N.W. Washington, DC 20531 Janet Reno Attorney General Daniel Marcus Acting Associate Attorney General Mary Lou Leary Acting Assistant Attorney General Julie E. Samuels Acting Director, National Institute of Justice Office of Justice Programs National Institute of Justice World Wide Web Site World Wide Web Site http://www.ojp.usdoj.gov http://www.ojp.usdoj.gov/nij Fire and Arson Scene Evidence: A Guide for Public Safety Personnel Written and Approved by the Technical Working Group on Fire/Arson Scene Investigation June 2000 NCJ 181584 Julie E. Samuels Acting Director David G. Boyd, Ph.D. Deputy Director Richard M. Rau, Ph.D. Project Monitor Opinions or points of view expressed in this document represent a consensus of the authors and do not necessarily reflect the official position of the U.S. Department of Justice. The National Institute of Justice is a component of the Office of Justice Programs, which also includes the Bureau of Justice Assistance, the Bureau of Justice Statistics, the Office of Juvenile Justice and Delinquency Prevention, and the Office for Victims of Crime. Message From the Attorney General ctions taken at the outset of an investigation at a fire and Aarson scene can play a pivotal role in the resolution of a case. Careful, thorough investigation is key to ensuring that potential physical evidence is not tainted or destroyed or potential witnesses overlooked. -

THE CRIME of ARSON Paul Sadler, Jr
Journal of Criminal Law and Criminology Volume 41 | Issue 3 Article 4 1950 The rC ime of Arson Paul Jr. Sadler Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation Paul Jr. Sadler, The rC ime of Arson, 41 J. Crim. L. & Criminology 290 (1950-1951) This Article is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. THE CRIME OF ARSON Paul Sadler, Jr. The following article is from a thesis the author prepared while pursuing his studies in Social Relations at Harvard University, from which he received his A.B. degree in June, -1950. Mr. Sadler is currently employed as a fire investigator adjuster for the General Adjustment Bureau, Inc., Boston, Mass.-EDrroR. I The crime of arson is an extraordinarily complex one by its definition alone. Its complexity makes many difficulties to the student. It also gives the perpetrator some advantages. To begin with, arson, like murder and most admirality crimes, exists in several degrees of indict- ment. These degrees are wholly dependent upon the type and use of the structure or property burned, degree of involvement of participants, and often the time of day in which the crime is committed.' But what degrees now exist are only created by modern statutory defini- tion over and above the original common law of England, which law, in comparison with 20th century statutes, seems very defective in scope. -

The Alt-Right on Campus: What Students Need to Know
THE ALT-RIGHT ON CAMPUS: WHAT STUDENTS NEED TO KNOW About the Southern Poverty Law Center The Southern Poverty Law Center is dedicated to fighting hate and bigotry and to seeking justice for the most vulnerable members of our society. Using litigation, education, and other forms of advocacy, the SPLC works toward the day when the ideals of equal justice and equal oportunity will become a reality. • • • For more information about the southern poverty law center or to obtain additional copies of this guidebook, contact [email protected] or visit www.splconcampus.org @splcenter facebook/SPLCenter facebook/SPLConcampus © 2017 Southern Poverty Law Center THE ALT-RIGHT ON CAMPUS: WHAT STUDENTS NEED TO KNOW RICHARD SPENCER IS A LEADING ALT-RIGHT SPEAKER. The Alt-Right and Extremism on Campus ocratic ideals. They claim that “white identity” is under attack by multicultural forces using “politi- An old and familiar poison is being spread on col- cal correctness” and “social justice” to undermine lege campuses these days: the idea that America white people and “their” civilization. Character- should be a country for white people. ized by heavy use of social media and memes, they Under the banner of the Alternative Right – or eschew establishment conservatism and promote “alt-right” – extremist speakers are touring colleges the goal of a white ethnostate, or homeland. and universities across the country to recruit stu- As student activists, you can counter this movement. dents to their brand of bigotry, often igniting pro- In this brochure, the Southern Poverty Law Cen- tests and making national headlines. Their appear- ances have inspired a fierce debate over free speech ter examines the alt-right, profiles its key figures and the direction of the country. -

Filling Terrorism Gaps: Veos, Evaluating Databases, and Applying Risk Terrain Modeling to Terrorism RH Hagan
PNNL-25727 Filling Terrorism Gaps: VEOs, Evaluating Databases, and Applying Risk Terrain Modeling to Terrorism RH Hagan August 2016 PNNL-25727 Filling Terrorism Gaps: VEOs, Evaluating Databases, and Applying Risk Terrain Modeling to Terrorism RH Hagan August 2016 Prepared for the U.S. Department of Energy under Contract DE-AC05-76RL01830 Pacific Northwest National Laboratory Richland, Washington 99352 PNNL-25727 Abstract This paper aims to address three issues: the lack of literature differentiating terrorism and violent extremist organizations (VEOs), terrorism incident databases, and the applicability of Risk Terrain Modeling (RTM) to terrorism. Current open source literature and publicly available government sources do not differentiate between terrorism and VEOs; furthermore, they fail to define them. Addressing the lack of a comprehensive comparison of existing terrorism data sources, a matrix comparing a dozen terrorism databases is constructed, providing insight toward the array of data available. RTM, a method for spatial risk analysis at a micro level, has some applicability to terrorism research, particularly for studies looking at risk indicators of terrorism. Leveraging attack data from multiple databases, combined with RTM, offers one avenue for closing existing research gaps in terrorism literature. iii Acknowledgments The author would like to sincerely thank several individuals for their contributions to this research. My mentor, Chrissie Noonan, for her guidance and support throughout this process, Carolyn Cramer for her operational support and insight, Alex Stephan, Lead for the Special Programs and Scientific Studies Team at PNNL, George Muller for his support and direction, Hannah Trump for her substantial help with the appendices, and Dan Fortin, Sam Chatterjee, and Thomas Johansen for the constant discussions. -

Identifying Enemies Among Us: Evolving Terrorist Threats and the Continuing Challenges of Domestic Intelligence Collection and Information Sharing
CHILDREN AND FAMILIES The RAND Corporation is a nonprofit institution that helps improve policy and EDUCATION AND THE ARTS decisionmaking through research and analysis. ENERGY AND ENVIRONMENT HEALTH AND HEALTH CARE This electronic document was made available from www.rand.org as a public service INFRASTRUCTURE AND of the RAND Corporation. TRANSPORTATION INTERNATIONAL AFFAIRS LAW AND BUSINESS Skip all front matter: Jump to Page 16 NATIONAL SECURITY POPULATION AND AGING PUBLIC SAFETY Support RAND SCIENCE AND TECHNOLOGY Purchase this document TERRORISM AND Browse Reports & Bookstore HOMELAND SECURITY Make a charitable contribution For More Information Visit RAND at www.rand.org Explore the RAND Corporation View document details Limited Electronic Distribution Rights This document and trademark(s) contained herein are protected by law as indicated in a notice appearing later in this work. This electronic representation of RAND intellectual property is provided for non- commercial use only. Unauthorized posting of RAND electronic documents to a non-RAND website is prohibited. RAND electronic documents are protected under copyright law. Permission is required from RAND to reproduce, or reuse in another form, any of our research documents for commercial use. For information on reprint and linking permissions, please see RAND Permissions. This product is part of the RAND Corporation conference proceedings series. RAND conference proceedings present a collection of papers delivered at a conference or a summary of the conference. The material herein has been vetted by the conference attendees and both the introduction and the post-conference material have been re- viewed and approved for publication by the sponsoring research unit at RAND. -

A Schema of Right-Wing Extremism in the United States
ICCT Policy Brief October 2019 DOI: 10.19165/2019.2.06 ISSN: 2468-0486 A Schema of Right-Wing Extremism in the United States Author: Sam Jackson Over the past two years, and in the wake of deadly attacks in Charlottesville and Pittsburgh, attention paid to right-wing extremism in the United States has grown. Most of this attention focuses on racist extremism, overlooking other forms of right-wing extremism. This article presents a schema of three main forms of right-wing extremism in the United States in order to more clearly understand the landscape: racist extremism, nativist extremism, and anti-government extremism. Additionally, it describes the two primary subcategories of anti-government extremism: the patriot/militia movement and sovereign citizens. Finally, it discusses whether this schema can be applied to right-wing extremism in non-U.S. contexts. Key words: right-wing extremism, racism, nativism, anti-government A Schema of Right-Wing Extremism in the United States Introduction Since the public emergence of the so-called “alt-right” in the United States—seen most dramatically at the “Unite the Right” rally in Charlottesville, Virginia, in August 2017—there has been increasing attention paid to right-wing extremism (RWE) in the United States, particularly racist right-wing extremism.1 Violent incidents like Robert Bowers’ attack on the Tree of Life synagogue in Pittsburgh, Pennsylvania in October 2018; the mosque shooting in Christchurch, New Zealand in March 2019; and the mass shooting at a Walmart in El Paso, Texas in August -

Galilee Flowers
GALILEE FLOWERS The Collected Essays of Israel Shamir Israel Adam Shamir GALILEE FLOWERS CONTENTS INTRODUCTION........................................................................................................................... 5 WHY I SUPPORT THE RETURN OF PALESTINIANS.................................................................... 6 PART ONE....................................................................................................................................... 8 THE STATE OF MIND ................................................................................................................. 8 OLIVES OF ABOUD.................................................................................................................... 21 THE GREEN RAIN OF YASSOUF................................................................................................ 23 ODE TO FARRIS ........................................................................................................................ 34 THE BATTLE FOR PALESTINE.................................................................................................. 39 THE CITY OF THE MOON ......................................................................................................... 42 JOSEPH REVISITED................................................................................................................... 46 CORNERSTONE OF VIOLENCE.................................................................................................. 50 THE BARON’S BRAID............................................................................................................... -

FUNDING HATE How White Supremacists Raise Their Money
How White Supremacists FUNDING HATE Raise Their Money 1 RESPONDING TO HATE FUNDING HATE INTRODUCTION 1 SELF-FUNDING 2 ORGANIZATIONAL FUNDING 3 CRIMINAL ACTIVITY 9 THE NEW KID ON THE BLOCK: CROWDFUNDING 10 BITCOIN AND CRYPTOCURRENCIES 11 THE FUTURE OF WHITE SUPREMACIST FUNDING 14 2 RESPONDING TO HATE How White Supremacists FUNDING HATE Raise Their Money It’s one of the most frequent questions the Anti-Defamation League gets asked: WHERE DO WHITE SUPREMACISTS GET THEIR MONEY? Implicit in this question is the assumption that white supremacists raise a substantial amount of money, an assumption fueled by rumors and speculation about white supremacist groups being funded by sources such as the Russian government, conservative foundations, or secretive wealthy backers. The reality is less sensational but still important. As American political and social movements go, the white supremacist movement is particularly poorly funded. Small in numbers and containing many adherents of little means, the white supremacist movement has a weak base for raising money compared to many other causes. Moreover, ostracized because of its extreme and hateful ideology, not to mention its connections to violence, the white supremacist movement does not have easy access to many common methods of raising and transmitting money. This lack of access to funds and funds transfers limits what white supremacists can do and achieve. However, the means by which the white supremacist movement does raise money are important to understand. Moreover, recent developments, particularly in crowdfunding, may have provided the white supremacist movement with more fundraising opportunities than it has seen in some time. This raises the disturbing possibility that some white supremacists may become better funded in the future than they have been in the past. -

The Eco-Terrorist Wave (1970-2016)
THE ECO-TERRORIST WAVE (1970-2016) By João Raphael da Silva Submitted to Central European University Department of International Relations In partial fulfilment of the requirements for the degree of Master of Arts in International Relations Supervisor: Professor Matthijs Bogaards Word Count: Budapest, Hungary 2017 CEU eTD Collection 1 ABSTRACT The present research aims to shed light on the geographical and temporal spread of the ecological typology of terrorism – hereinafter referred as “Eco-Terrorism” – through the lens of the David C. Rapoport’s Wave and Tom Parker and Nick Sitter’s Strain Theories. This typology that has posed high levels of threats to the United States and the European Union member States remains uncovered by these two theoretical frameworks. My arguments are that, first, like many other typologies previously covered by the above-mentioned theories, Eco-Terrorism spread. Second, “Wave”, “Strain” or “Wavy Strain” should be able to explain the pattern followed by Eco-Terrorism. Making use of the “Contagion Effect” as an analytical tool, the present research found that, like in other typologies, as an indirect way of contagion, literary production has played a crucial role in the spread of Eco-Terrorism, with a slight difference on who was writing them. Eventually, they became leaders or members of an organization, but in most of the cases were philosophers and fiction authors. In addition, it was found that the system of organization of the ALF and the ELF contributes to the spread. As a direct way of contagion, aside from training like in other typologies, the spread occurs when members of a certain organization disaffiliate from an organization and found a new one, and sometimes when two organizations act in cooperation. -

Issue Number One. February, 2006. Free. the State Has Always Used Surveillance and Repression Against Those It Considers Threats Or Competition
The Warrior Wind Against a Society of Confinement: “Blow, wild wind, blow!” Issue Number One. February, 2006. Free. The State has always used surveillance and repression against those it considers threats or competition. For the past decade, earth and animal liberationists have faced an escalation of such surveillance and repression. When Jeff “Free” Luers was sentenced in 2001 to over 22 years for vandalizing SUVs, many felt his sentence was an exception or anomaly. Now almost all eco-prisoners are facing similar sentences (Earth Liberation Front prisoner Chris McIntosh was facing a 30 year minimum before taking a plea deal for eight years), and the sentences prisoners face are only climbing higher. To give one example: activists with Arizona Earth First!, recently convicted merely of charges relating to interference with a mountain-lion hunt, are being threatened with sentences Bill Rodgers, drawing by Katie. of over seven years at their March hearing! Federal law enforcement alleges that those arrested on December 7th, two individuals arrested since then, three people named in indictments but not apprehended, as well as unknown others, are all members of a large “eco-terror network” responsible for a series of actions in the northwest from 1996-2001. The actions in question On the Recent Wave of Repression included attacks against genetic engineering, various On December 7th, 2005, one of the largest wilderness “management” programs, meat and lumber roundups of environmental and animal liberation companies, as well as ecocidal development in general. activists in American history began. That day the FBI The Earth Liberation Front and the Animal Liberation arrested six people in four different states and issued Front used communiqués to claim responsibility for Grand Jury subpoenas to others not then taken into some of the actions cited in the government’s indictment. -

Greenpeace, Earth First! and the Earth Liberation Front: the Rp Ogression of the Radical Environmental Movement in America" (2008)
University of Rhode Island DigitalCommons@URI Senior Honors Projects Honors Program at the University of Rhode Island 2008 Greenpeace, Earth First! and The aE rth Liberation Front: The rP ogression of the Radical Environmental Movement in America Christopher J. Covill University of Rhode Island, [email protected] Follow this and additional works at: http://digitalcommons.uri.edu/srhonorsprog Part of the Environmental Sciences Commons Recommended Citation Covill, Christopher J., "Greenpeace, Earth First! and The Earth Liberation Front: The rP ogression of the Radical Environmental Movement in America" (2008). Senior Honors Projects. Paper 93. http://digitalcommons.uri.edu/srhonorsprog/93http://digitalcommons.uri.edu/srhonorsprog/93 This Article is brought to you for free and open access by the Honors Program at the University of Rhode Island at DigitalCommons@URI. It has been accepted for inclusion in Senior Honors Projects by an authorized administrator of DigitalCommons@URI. For more information, please contact [email protected]. Greenpeace, Earth First! and The Earth Liberation Front: The Progression of the Radical Environmental Movement in America Christopher John Covill Faculty Sponsor: Professor Timothy Hennessey, Political Science Causes of worldwide environmental destruction created a form of activism, Ecotage with an incredible success rate. Ecotage uses direct action, or monkey wrenching, to prevent environmental destruction. Mainstream conservation efforts were viewed by many environmentalists as having failed from compromise inspiring the birth of radicalized groups. This eventually transformed conservationists into radicals. Green Peace inspired radical environmentalism by civil disobedience, media campaigns and direct action tactics, but remained mainstream. Earth First’s! philosophy is based on a no compromise approach.