Debugging Z/OS COBOL Programs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cloud Enabling CICS
Front cover Cloud Enabling IBM CICS Discover how to quickly cloud enable a traditional IBM 3270-COBOL-VSAM application Use CICS Explorer to develop and deploy a multi-versioned application Understand the benefits of threshold policy Rufus Credle Isabel Arnold Andrew Bates Michael Baylis Pradeep Gohil Christopher Hodgins Daniel Millwood Ian J Mitchell Catherine Moxey Geoffrey Pirie Inderpal Singh Stewart Smith Matthew Webster ibm.com/redbooks International Technical Support Organization Cloud Enabling IBM CICS December 2014 SG24-8114-00 Note: Before using this information and the product it supports, read the information in “Notices” on page vii. First Edition (December 2014) This edition applies to CICS Transaction Server for z/OS version 5.1, 3270-COBOL-VSAM application. © Copyright International Business Machines Corporation 2014. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . vii Trademarks . viii IBM Redbooks promotions . ix Preface . xi Authors. xii Now you can become a published author, too! . .xv Comments welcome. .xv Stay connected to IBM Redbooks . xvi Part 1. Introduction . 1 Chapter 1. Cloud enabling your CICS TS applications . 3 1.1 Did you know?. 4 1.2 Business value . 4 1.3 Solution overview . 5 1.4 Cloud computing in a CICS TS context. 6 1.5 Overview of the cloud-enabling technologies in CICS TS V5 . 11 1.5.1 Platform overview . 12 1.5.2 Application overview . 13 Chapter 2. GENAPP introduction. 15 2.1 CICS TS topology . 16 2.2 Application architecture. 17 2.2.1 GENAPP in a single managed region. -
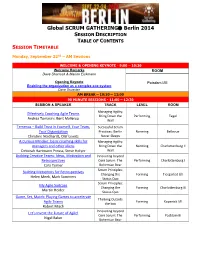
Global SCRUM GATHERING® Berlin 2014
Global SCRUM GATHERING Berlin 2014 SESSION DESCRIPTION TABLE OF CONTENTS SESSION TIMETABLE Monday, September 22nd – AM Sessions WELCOME & OPENING KEYNOTE - 9:00 – 10:30 Welcome Remarks ROOM Dave Sharrock & Marion Eickmann Opening Keynote Potsdam I/III Enabling the organization as a complex eco-system Dave Snowden AM BREAK – 10:30 – 11:00 90 MINUTE SESSIONS - 11:00 – 12:30 SESSION & SPEAKER TRACK LEVEL ROOM Managing Agility: Effectively Coaching Agile Teams Bring Down the Performing Tegel Andrea Tomasini, Bent Myllerup Wall Temenos – Build Trust in Yourself, Your Team, Successful Scrum Your Organization Practices: Berlin Norming Bellevue Christine Neidhardt, Olaf Lewitz Never Sleeps A Curious Mindset: basic coaching skills for Managing Agility: managers and other aliens Bring Down the Norming Charlottenburg II Deborah Hartmann Preuss, Steve Holyer Wall Building Creative Teams: Ideas, Motivation and Innovating beyond Retrospectives Core Scrum: The Performing Charlottenburg I Cara Turner Bohemian Bear Scrum Principles: Building Metaphors for Retrospectives Changing the Forming Tiergarted I/II Helen Meek, Mark Summers Status Quo Scrum Principles: My Agile Suitcase Changing the Forming Charlottenburg III Martin Heider Status Quo Game, Set, Match: Playing Games to accelerate Thinking Outside Agile Teams Forming Kopenick I/II the box Robert Misch Innovating beyond Let's Invent the Future of Agile! Core Scrum: The Performing Postdam III Nigel Baker Bohemian Bear Monday, September 22nd – PM Sessions LUNCH – 12:30 – 13:30 90 MINUTE SESSIONS - 13:30 -

Enabling Devops on Premise Or Cloud with Jenkins
Enabling DevOps on Premise or Cloud with Jenkins Sam Rostam [email protected] Cloud & Enterprise Integration Consultant/Trainer Certified SOA & Cloud Architect Certified Big Data Professional MSc @SFU & PhD Studies – Partial @UBC Topics The Context - Digital Transformation An Agile IT Framework What DevOps bring to Teams? - Disrupting Software Development - Improved Quality, shorten cycles - highly responsive for the business needs What is CI /CD ? Simple Scenario with Jenkins Advanced Jenkins : Plug-ins , APIs & Pipelines Toolchain concept Q/A Digital Transformation – Modernization As stated by a As established enterprises in all industries begin to evolve themselves into the successful Digital Organizations of the future they need to begin with the realization that the road to becoming a Digital Business goes through their IT functions. However, many of these incumbents are saddled with IT that has organizational structures, management models, operational processes, workforces and systems that were built to solve “turn of the century” problems of the past. Many analysts and industry experts have recognized the need for a new model to manage IT in their Businesses and have proposed approaches to understand and manage a hybrid IT environment that includes slower legacy applications and infrastructure in combination with today’s rapidly evolving Digital-first, mobile- first and analytics-enabled applications. http://www.ntti3.com/wp-content/uploads/Agile-IT-v1.3.pdf Digital Transformation requires building an ecosystem • Digital transformation is a strategic approach to IT that treats IT infrastructure and data as a potential product for customers. • Digital transformation requires shifting perspectives and by looking at new ways to use data and data sources and looking at new ways to engage with customers. -

Integrating the GNU Debugger with Cycle Accurate Models a Case Study Using a Verilator Systemc Model of the Openrisc 1000
Integrating the GNU Debugger with Cycle Accurate Models A Case Study using a Verilator SystemC Model of the OpenRISC 1000 Jeremy Bennett Embecosm Application Note 7. Issue 1 Published March 2009 Legal Notice This work is licensed under the Creative Commons Attribution 2.0 UK: England & Wales License. To view a copy of this license, visit http://creativecommons.org/licenses/by/2.0/uk/ or send a letter to Creative Commons, 171 Second Street, Suite 300, San Francisco, California, 94105, USA. This license means you are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must give the original author, Jeremy Bennett of Embecosm (www.embecosm.com), credit; • For any reuse or distribution, you must make clear to others the license terms of this work; • Any of these conditions can be waived if you get permission from the copyright holder, Embecosm; and • Nothing in this license impairs or restricts the author's moral rights. The software for the SystemC cycle accurate model written by Embecosm and used in this document is licensed under the GNU General Public License (GNU General Public License). For detailed licensing information see the file COPYING in the source code. Embecosm is the business name of Embecosm Limited, a private limited company registered in England and Wales. Registration number 6577021. ii Copyright © 2009 Embecosm Limited Table of Contents 1. Introduction ................................................................................................................ 1 1.1. Why Use Cycle Accurate Modeling .................................................................... 1 1.2. Target Audience ................................................................................................ 1 1.3. Open Source ..................................................................................................... 2 1.4. Further Sources of Information ......................................................................... 2 1.4.1. -

13347 CICS Introduction and Overview
CICS Introduction and Overview Ezriel Gross Circle Software Incorporated August 13th, 2013 (Tue) 4:30pm – 5:30pm Session 13347 Agenda What is CICS and Who Uses It Pseudo Conversational Programming CICS Application Services CICS Connectivity CICS Resource Definitions CICS Supplied Transactions CICS Web Services CICS The Product What is CICS? CICS is an online transaction processing system. Middleware between the operating system and business applications. Manages the user interface. Retrieves and modifies data. Handles the communication. CICS Customers Banks Mortgage Account Reconciliations Payroll Brokerage Houses Stock Trading Trade Clearing Human Resources Insurance Companies Policy Administration Accounts Receivables Claims Processing Batch Versus Online Programs The two ways to process input are batch and online. Batch requests are saved then processed sequentially. After all requests are processed the results are transmitted. Used for order entry processing such as warehouse applications. Online requests are received randomly and processed immediately. Results are transmitted as soon as they are available. Response time tends to be sub-second. Used for applications – such as: Credit Card Authorization. Transaction Processing Requirements Large volume of business transactions to be rapidly and accurately processed Multiple users, single/sysplex or distributed With potentially: – A huge number of users – Simultaneous access to data – A large volume of data residing in multiple database types – Intense security and data integrity controls necessary The access to the data is such that: – Each user has the perception of being the sole user of the system – A set of changes is guaranteed to be logically consistent. If a failure occurs, any intermediate results are undone before the system becomes available again – A completed set of changes is immediately visible to other users A Business Transaction A transaction has a 4-character id. -

Code Profilers Choosing a Tool for Analyzing Performance
Code Profilers Choosing a Tool for Analyzing Performance Freescale Semiconductor Author, Rick Grehan Document Number: CODEPROFILERWP Rev. 0 11/2005 A profiler is a development tool that lets you look inside your application to see how each component—each routine, each block, sometimes each line and even each instruction—performs. You can find and correct your application’s bottlenecks. How do they work this magic? CONTENTS 1. Passive Profilers ...............................................3 6. Comparing Passive and Active 1.1 How It Is Done—PC Sampling ................4 Profilers .................................................................9 1.2 It Is Statistical ................................................4 6.1 Passive Profilers—Advantages ...............9 6.2 Passive Profilers—Disadvantages .........9 2. Active Profilers ...................................................4 6.3 Active Profilers—Advantages ................10 2.1 Methods of Instrumentation .....................5 6.4 Active Profilers—Disadvantages ..........11 3. Source Code Instrumentation ...................5 7. Conclusion .........................................................12 3.1 Instrumenting by Hand ..............................5 8. Addendum: Recursion and 4. Object Code Instrumentation ....................5 Hierarchies ........................................................12 4.1 Direct Modification .......................................6 4.2 Indirect Modification ...................................7 5. Object Instrumentation vs. Source Instrumentation -

Debugging and Profiling with Arm Tools
Debugging and Profiling with Arm Tools [email protected] • Ryan Hulguin © 2018 Arm Limited • 4/21/2018 Agenda • Introduction to Arm Tools • Remote Client Setup • Debugging with Arm DDT • Other Debugging Tools • Break • Examples with DDT • Lunch • Profiling with Arm MAP • Examples with MAP • Obtaining Support 2 © 2018 Arm Limited Introduction to Arm HPC Tools © 2018 Arm Limited Arm Forge An interoperable toolkit for debugging and profiling • The de-facto standard for HPC development • Available on the vast majority of the Top500 machines in the world • Fully supported by Arm on x86, IBM Power, Nvidia GPUs and Arm v8-A. Commercially supported by Arm • State-of-the art debugging and profiling capabilities • Powerful and in-depth error detection mechanisms (including memory debugging) • Sampling-based profiler to identify and understand bottlenecks Fully Scalable • Available at any scale (from serial to petaflopic applications) Easy to use by everyone • Unique capabilities to simplify remote interactive sessions • Innovative approach to present quintessential information to users Very user-friendly 4 © 2018 Arm Limited Arm Performance Reports Characterize and understand the performance of HPC application runs Gathers a rich set of data • Analyses metrics around CPU, memory, IO, hardware counters, etc. • Possibility for users to add their own metrics Commercially supported by Arm • Build a culture of application performance & efficiency awareness Accurate and astute • Analyses data and reports the information that matters to users insight • Provides simple guidance to help improve workloads’ efficiency • Adds value to typical users’ workflows • Define application behaviour and performance expectations Relevant advice • Integrate outputs to various systems for validation (e.g. -

Introduction-To-Mainframes.Pdf
Mainframe The term ‘MainFrame’ brings to mind a giant room of electronic parts that is a computer, referring to the original CPU cabinet in a computer of the mid-1960’s. Today, Mainframe refers to a class of ultra-reliable large and medium-scale servers designed for carrier-class and enterprise-class systems operations. Mainframes are costly, due to the support of symmetric multiprocessing (SMP) and dozens of central processors existing within in a single system. Mainframes are highly scalable. Through the addition of clusters, high-speed caches and volumes of memory, they connect to terabyte holding data subsystems. Mainframe computer Mainframe is a very large and expensive computer capable of supporting hundreds, or even thousands, of users simultaneously. In the hierarchy that starts with a simple microprocessor at the bottom and moves to supercomputers at the top, mainframes are just below supercomputers. In some ways, mainframes are more powerful than supercomputers because they support more simultaneous programs. But supercomputers can execute a single program faster than a mainframe. The distinction between small mainframes and minicomputers is vague, depending really on how the manufacturer wants to market its machines. Modern mainframe computers have abilities not so much defined by their single task computational speed (usually defined as MIPS — Millions of Instructions Per Second) as by their redundant internal engineering and resulting high reliability and security, extensive input-output facilities, strict backward compatibility with older software, and high utilization rates to support massive throughput. These machines often run for years without interruption, with repairs and hardware upgrades taking place during normal operation. -

CICS Transaction Server for OS/390 Installation Guide
CICS® Transaction Server for OS/390® Installation Guide Release 3 GC33-1681-30 CICS® Transaction Server for OS/390® Installation Guide Release 3 GC33-1681-30 Note! Before using this information and the product it supports, be sure to read the general information under “Notices” on page xi. Third edition (June 1999) This edition applies to Release 3 of CICS Transaction Server for OS/390, program number 5655-147, and to all subsequent versions, releases, and modifications until otherwise indicated in new editions. Make sure you are using the correct edition for the level of the product. This edition replaces and makes obsolete the previous edition, SC33-1681-00. The technical changes for this edition are summarized under ″Summary of changes″ and are indicated by a vertical bar to the left of a change. Order publications through your IBM representative or the IBM branch office serving your locality. Publications are not stocked at the address given below. At the back of this publication is a page entitled “Sending your comments to IBM”. If you want to make comments, but the methods described are not available to you, please address them to: IBM United Kingdom Laboratories, Information Development, Mail Point 095, Hursley Park, Winchester, Hampshire, England, SO21 2JN. When you send information to IBM, you grant IBM a nonexclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 1989, 1999. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. -

CA Datacom CICS Services Best Practices Guide
CA Datacom® CICS Services Best Practices Guide Version 14.02 This Documentation, which includes embedded help systems and electronically distributed materials (hereinafter referred to as the “Documentation”), is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

Enterprise PL/I for Z/OS V5.3 Compiler and Runtime Migration Guide Part 1
Enterprise PL/I for z/OS Version 5 Release 3 Compiler and Run-Time Migration Guide IBM GC27-8930-02 Note Before using this information and the product it supports, be sure to read the general information under “Notices” on page 181. Third Edition (September 2019) This edition applies to Version 5 Release 3 of Enterprise PL/I for z/OS, 5655-PL5, and to any subsequent releases until otherwise indicated in new editions or technical newsletters. Make sure you are using the correct edition for the level of the product. Order publications through your IBM representative or the IBM branch office serving your locality. Publications are not stocked at the address below. A form for readers' comments is provided at the back of this publication. If the form has been removed, address your comments to: IBM Corporation, Department H150/090 555 Bailey Ave San Jose, CA, 95141-1099 United States of America When you send information to IBM, you grant IBM a nonexclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Because IBM® Enterprise PL/I for z/OS® supports the continuous delivery (CD) model and publications are updated to document the features delivered under the CD model, it is a good idea to check for updates once every three months. © Copyright International Business Machines Corporation 1999, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Tables.................................................................................................................. xi Figures............................................................................................................... xiii About this book....................................................................................................xv Using your documentation........................................................................................................................ -

Ready to Innovate?
ReadyThe Visual COBOL 5.0to Azure innovate? DevOps and Serverless Computing Walkthrough June 2019 The Visual COBOL 5.0 Azure DevOps and Serverless Computing Walkthrough 2 Visual COBOL 5.0— blue sky thinking Ready to build your Cloud story? This is primarily a how-to technical guide that enables COBOL and non- COBOL developers to modernize legacy applications using the Cloud— it’s all about bridging the old with the new. New to Visual COBOL? This is your guided tour of everything it can do towards modernizing core COBOL applications. Already on board? This is the update that explains how to take your applications beyond the next level and on to the Cloud. What will you learn? Much of this Guide focuses on the technical, practical aspect of creating next-gen apps from COBOL code. Among other new skills, you will discover how to… • Bring a COBOL application into Visual Studio or Eclipse • Edit, compile and debug COBOL applications using the IDE • Modernize COBOL apps using .NET and C# • Create and deploy a COBOL microservice as a Serverless application in the Cloud • Build, test and publish your application via a DevOps pipeline • Understand the latest native Cloud technologies The Visual COBOL 5.0 Azure DevOps and Serverless Computing Walkthrough 3 What’s new in Visual COBOL 5.0? This latest update of our unrivalled development experience significantly extends Visual COBOL’s capabilities. It brings the Cloud closer, enabling access to DevOps and Serverless computing for COBOL systems. For Micro Focus, Visual COBOL 5.0 is where meet our customers’ need for application modernization using the Cloud.