A Hybrid Model by Integrating Scrum and Rad
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FUNDAMENTALS of COMPUTING (2019-20) COURSE CODE: 5023 502800CH (Grade 7 for ½ High School Credit) 502900CH (Grade 8 for ½ High School Credit)
EXPLORING COMPUTER SCIENCE NEW NAME: FUNDAMENTALS OF COMPUTING (2019-20) COURSE CODE: 5023 502800CH (grade 7 for ½ high school credit) 502900CH (grade 8 for ½ high school credit) COURSE DESCRIPTION: Fundamentals of Computing is designed to introduce students to the field of computer science through an exploration of engaging and accessible topics. Through creativity and innovation, students will use critical thinking and problem solving skills to implement projects that are relevant to students’ lives. They will create a variety of computing artifacts while collaborating in teams. Students will gain a fundamental understanding of the history and operation of computers, programming, and web design. Students will also be introduced to computing careers and will examine societal and ethical issues of computing. OBJECTIVE: Given the necessary equipment, software, supplies, and facilities, the student will be able to successfully complete the following core standards for courses that grant one unit of credit. RECOMMENDED GRADE LEVELS: 9-12 (Preference 9-10) COURSE CREDIT: 1 unit (120 hours) COMPUTER REQUIREMENTS: One computer per student with Internet access RESOURCES: See attached Resource List A. SAFETY Effective professionals know the academic subject matter, including safety as required for proficiency within their area. They will use this knowledge as needed in their role. The following accountability criteria are considered essential for students in any program of study. 1. Review school safety policies and procedures. 2. Review classroom safety rules and procedures. 3. Review safety procedures for using equipment in the classroom. 4. Identify major causes of work-related accidents in office environments. 5. Demonstrate safety skills in an office/work environment. -
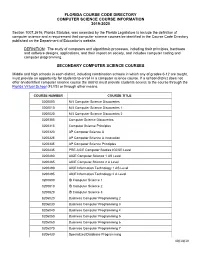
Florida Course Code Directory Computer Science Course Information 2019-2020
FLORIDA COURSE CODE DIRECTORY COMPUTER SCIENCE COURSE INFORMATION 2019-2020 Section 1007.2616, Florida Statutes, was amended by the Florida Legislature to include the definition of computer science and a requirement that computer science courses be identified in the Course Code Directory published on the Department of Education’s website. DEFINITION: The study of computers and algorithmic processes, including their principles, hardware and software designs, applications, and their impact on society, and includes computer coding and computer programming. SECONDARY COMPUTER SCIENCE COURSES Middle and high schools in each district, including combination schools in which any of grades 6-12 are taught, must provide an opportunity for students to enroll in a computer science course. If a school district does not offer an identified computer science course the district must provide students access to the course through the Florida Virtual School (FLVS) or through other means. COURSE NUMBER COURSE TITLE 0200000 M/J Computer Science Discoveries 0200010 M/J Computer Science Discoveries 1 0200020 M/J Computer Science Discoveries 2 0200305 Computer Science Discoveries 0200315 Computer Science Principles 0200320 AP Computer Science A 0200325 AP Computer Science A Innovation 0200335 AP Computer Science Principles 0200435 PRE-AICE Computer Studies IGCSE Level 0200480 AICE Computer Science 1 AS Level 0200485 AICE Computer Science 2 A Level 0200490 AICE Information Technology 1 AS Level 0200495 AICE Information Technology 2 A Level 0200800 IB Computer -

Geo-DB Requirement Analysis
2.1.1. Overview Lifecycle 2 Conceptual Database Design 2.1 Requirement analysis -> Text 2.2 Modeling languages Requirement analysis -> Conceptual Model 2.1.1 Overview Conceptual Design 2.1.2 Requirement Analysis (case study) 2.2.1 Basic Modeling Primitives 2.2.2 Modeling Languages: UML and CREATE TABLE Studentin (SID INTEGER PRIMARY KEY, -> Database schema VName CHAR(20) Name CHAR(30)CREATE NOT TABLENULL, Kurs Entity-Relationship Model (ERM) Logical Schema Design Email Char(40));(KID CHAR(10) PRIMARY KEY, Name CHAR(40) NOT NULL, Dauer INTEGER); CREATE TABLE Order 2.2.3 Conceptual DB design: basics ODate DATE soldBy INTEGER FOREIGN KEY REFEREBCES Peronal(PID) 2.2.4 From Requirements to Models CID INTEGER FOREIGN KEY REFERENCES Customer (CID)); Physical Schema Design -> Access paths References: Kemper / Eickler chap 2, Elmasri / Navathe chap. 3 Administration Garcia-Molina / Ullmann / Widom: chap. 2 © HS-2009 Redesign 02-DBS-Conceptual-2 Database Design:Terminology 2.1.2 Requirement Analysis Most important: talk with your customers! Def.: Database Design The process of defining the overall structure of a database, Tasks during RA: i.e. the schema, on different layers of abstraction. Identify essential "real world" information (e.g. Design levels: Conceptual, logical, physical interviews) Remove redundant, unimportant details Includes "Analysis" and "Design" from SE Clarify unclear natural language statements DB Modeling: defining the "static model" using formal or visual languages Fill remaining gaps in discussions Distinguish data and operations DB SE Requirements Requirements Conceptual modeling Analysis Requirement analysis & Conceptual Design aims at Logical modeling Design focusing thoughts and discussions ! Physical modeling Implementation © HS-2009 02-DBS-Conceptual-3 © HS-2009 02-DBS-Conceptual-4 Example: Geo-DB Requirement Analysis The database we develop will contain data about countries, cities, Clarify unclear statements organizations and geographical facts. -

Safety and Security Challenge
SAFETY AND SECURITY CHALLENGE TOP SUPERCOMPUTERS IN THE WORLD - FEATURING TWO of DOE’S!! Summary: The U.S. Department of Energy (DOE) plays a very special role in In fields where scientists deal with issues from disaster relief to the keeping you safe. DOE has two supercomputers in the top ten supercomputers in electric grid, simulations provide real-time situational awareness to the whole world. Titan is the name of the supercomputer at the Oak Ridge inform decisions. DOE supercomputers have helped the Federal National Laboratory (ORNL) in Oak Ridge, Tennessee. Sequoia is the name of Bureau of Investigation find criminals, and the Department of the supercomputer at Lawrence Livermore National Laboratory (LLNL) in Defense assess terrorist threats. Currently, ORNL is building a Livermore, California. How do supercomputers keep us safe and what makes computing infrastructure to help the Centers for Medicare and them in the Top Ten in the world? Medicaid Services combat fraud. An important focus lab-wide is managing the tsunamis of data generated by supercomputers and facilities like ORNL’s Spallation Neutron Source. In terms of national security, ORNL plays an important role in national and global security due to its expertise in advanced materials, nuclear science, supercomputing and other scientific specialties. Discovery and innovation in these areas are essential for protecting US citizens and advancing national and global security priorities. Titan Supercomputer at Oak Ridge National Laboratory Background: ORNL is using computing to tackle national challenges such as safe nuclear energy systems and running simulations for lower costs for vehicle Lawrence Livermore's Sequoia ranked No. -

MAKING DATA MODELS READABLE David C
MAKING DATA MODELS READABLE David C. Hay Essential Strategies, Inc. “Confusion and clutter are failures of [drawing] design, not attributes of information. And so the point is to find design strategies that reveal detail and complexity ¾ rather than to fault the data for an excess of complication. Or, worse, to fault viewers for a lack of understanding.” ¾ Edward R. Tufte1 Entity/relationship models (or simply “data models”) are powerful tools for analyzing and representing the structure of an organization. Properly used, they can reveal subtle relationships between elements of a business. They can also form the basis for robust and reliable data base design. Data models have gotten a bad reputation in recent years, however, as many people have found them to be more trouble to produce and less beneficial than promised. Discouraged, people have gone on to other approaches to developing systems ¾ often abandoning modeling altogether, in favor of simply starting with system design. Requirements analysis remains important, however, if systems are ultimately to do something useful for the company. And modeling ¾ especially data modeling ¾ is an essential component of requirements analysis. It is important, therefore, to try to understand why data models have been getting such a “bad rap”. Your author believes, along with Tufte, that the fault lies in the way most people design the models, not in the underlying complexity of what is being represented. An entity/relationship model has two primary objectives: First it represents the analyst’s public understanding of an enterprise, so that the ultimate consumer of a prospective computer system can be sure that the analyst got it right. -

Value Mapping – Critical Business Architecture Viewpoint
Download this and other resources @ http://www.aprocessgroup.com/myapg Value Mapping – Critical Business Architecture Viewpoint AEA Webinar Series “Enterprise Business Intelligence” Armstrong Process Group, Inc. www.aprocessgroup.com Copyright © 1998-2017, Armstrong Process Group, Inc., All rights reserved 2 About APG APG’s mission is to “Align information technology and systems engineering capabilities with business strategy using proven, practical processes delivering world-class results.” Industry thought leader in enterprise architecture, business modeling, process improvement, systems and software engineering, requirements management, and agile methods Member and contributor to UML ®, SysML ®, SPEM, UPDM ™ at the Object Management Group ® (OMG ®) TOGAF ®, ArchiMate ®, and IT4IT ™ at The Open Group BIZBOK ® Guide and UML Profile at the Business Architecture Guild Business partners with Sparx, HPE, and IBM Guild Accredited Training Partner ™ (GATP ™) and IIBA ® Endorsed Education Provider (EEP ™) AEA Webinar Series – “Enterprise Business Intelligence” – Value Mapping Copyright © 1998-2017, Armstrong Process Group, Inc., All rights reserved 3 Business Architecture Framework Business Architecture Knowledgebase Blueprints provide views into knowledgebase, based on stakeholder concerns Scenarios contextualize expected outcomes of business architecture work Also inform initial selections of key stakeholders and likely concerns AEA Webinar Series – “Enterprise Business Intelligence” – Value Mapping BIZBOK Guide Copyright © 1998-2017, -
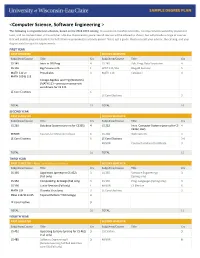
<Computer Science, Software Engineering >
<Computer Science, Software Engineering > The following is a hypothetical schedule, based on the 2018-2019 catalog. It assumes no transferred credits, no requirements waived by placement tests, and no courses taken in the summer. UW-Eau Claire cannot guarantee all courses will be offered as shown, but will provide a range of courses that will enable prepared students to fulfill their requirements in a timely period. This is just a guide. Please consult your advisor, the catalog, and your degree audit for specific requirements. FIRST YEAR FIRST SEMESTER SECOND SEMESTER Subj/Area/Course Title Crs Subj/Area/Course Title Crs CS 145 Intro to OO Prog 4 CS 245 Adv. Prog. Data Structures 4 CS 146 Big Picture in CS 1 WRIT 114/116 Blugold Seminar 5 MATH 112 or Precalculus 4 MATH 114 Calculus I 4 MATH 109 & 113 College Algebra and Trig (Winterim) (MATH 113 – prereq or concurrent enrollment for CS 245 LE Core Electives 6 LE Core Electives 3 TOTAL 15 TOTAL 16 SECOND YEAR FIRST SEMESTER SECOND SEMESTER Subj/Area/Course Title Crs Subj/Area/Course Title Crs CS 260 Database Systems (prereq for CS355) 4 CS 252 Intro. Computer Systems (prereq for CS 4 CS352, 452) MINOR Courses for Minor/Certificate 6 CS 268 Web Systems 3 LE Core Electives 6 LE Core Electives 3-6 MINOR Courses for Minor/Certificate 3 TOTAL 16 TOTAL 15 THIRD YEAR FIRST SEMESTER – Apply for Admission to Major SECOND SEMESTER Subj/Area/Course Title Crs Subj/Area/Course Title Crs CS 335 Algorithms (prereq for CS 452) 3 CS 355 Software Engineering I 3 (Fall only) (Spring only) CS 352 ComputeOrg. -

Design and Implementation of a Standards Based Ecommerce Solution in the Business-To-Business Area
Design and implementation of a standards based eCommerce solution in the business-to-business area Thesis of Andreas Junghans Department of Computer Science Karlsruhe University of Applied Sciences, Germany Written at ISB GmbH, Karlstrasse 52-54, 76133 Karlsruhe 03/01/2000 to 08/31/2000 Supervisor at Karlsruhe University of Applied Sciences: Prof. Klaus Gremminger Co-supervisor: Prof. Dr. Lothar Gmeiner Supervisor at ISB GmbH: Dipl.Inform. Ralph Krause Declaration I have written this thesis independently, solely based on the literature and tools mentioned in the chapters and the appendix. This document - in the current or a similar form - has not and will not be submitted to any other institution apart from the Karlsruhe University of Applied Sciences to receive an academical grade. I would like to thank Ralph Krause and Gerlinde Wiest of ISB GmbH for their support over the last six month, as well as Peter Heil and Frank Nielsen of Heidelberger Druckmaschinen AG for providing informa- tion and suggestions for the requirements analysis. Acknowledgements also go to Christian Schenk for his MiKTEX distribution and the Apache group for their XML tools. Finally, I would like to thank Professor Klaus Gremminger of the Karlsruhe University of Applied Sciences for his supervision of this thesis. Karlsruhe, 3rd of September, 2000 (Andreas Junghans) Contents 1 Introduction 1 1.1 Document conventions ...................................... 1 1.2 Subject of this thesis ....................................... 1 1.3 Rough schedule .......................................... 2 2 Requirements analysis 3 2.1 Tools used ............................................. 3 2.2 Domain requirements ....................................... 3 2.2.1 Clarification of terms ................................... 3 2.2.2 Specific requirements on ”Business to Business” applications ............ -

Requirements Phase
Requirements Phase • Chance of a product being on time and within budget is very slim unless the development team knows what the product should do • To achieve this level the development team must analyze the needs of the client as precisely as possible Ch10 Copyright © 2004 by Eugean 1 Hacopians Requirements Phase • After a clear picture of the problem the development teams can answer the question: – What should the product do? • The process of answering this question lies within the requirements phase Ch10 Copyright © 2004 by Eugean 2 Hacopians Requirements Phase • Common misconceptions are: – During requirement phase the developer must determine what the client wants – The client can be unclear as to what they want – The client may not be able to communicate what they want to the developer • Most clients do not understand the software development process Ch10 Copyright © 2004 by Eugean 3 Hacopians Requirements Elicitation • This process is finding out a client’s requirements • Members of the requirements team must be familiar with the application domain • Requirement analysis is the process of: – Understanding the initial requirements – Refining requirements – Extending requirements Ch10 Copyright © 2004 by Eugean 4 Hacopians Requirements Elicitation • This process starts with several members of the requirements analysis team meeting with several members of the client’s team • It is essential to use the correct terminology or settle on an agreed set – Misunderstanding terminology can result in a faulty product – This could result in -

Data Quality Requirements Analysis and Modeling December 1992 TDQM-92-03 Richard Y
Published in the Ninth International Conference of Data Engineering Vienna, Austria, April 1993 Data Quality Requirements Analysis and Modeling December 1992 TDQM-92-03 Richard Y. Wang Henry B. Kon Stuart E. Madnick Total Data Quality Management (TDQM) Research Program Room E53-320 Sloan School of Management Massachusetts Institute of Technology Cambridge, MA 02139 USA 617-253-2656 Fax: 617-253-3321 Acknowledgments: Work reported herein has been supported, in part, by MITís Total Data Quality Management (TDQM) Research Program, MITís International Financial Services Research Center (IFSRC), Fujitsu Personal Systems, Inc. and Bull-HN. The authors wish to thank Gretchen Fisher for helping prepare this manuscript. To Appear in the Ninth International Conference on Data Engineering Vienna, Austria April 1993 Data Quality Requirements Analysis and Modeling Richard Y. Wang Henry B. Kon Stuart E. Madnick Sloan School of Management Massachusetts Institute of Technology Cambridge, Mass 02139 [email protected] ABSTRACT Data engineering is the modeling and structuring of data in its design, development and use. An ultimate goal of data engineering is to put quality data in the hands of users. Specifying and ensuring the quality of data, however, is an area in data engineering that has received little attention. In this paper we: (1) establish a set of premises, terms, and definitions for data quality management, and (2) develop a step-by-step methodology for defining and documenting data quality parameters important to users. These quality parameters are used to determine quality indicators, to be tagged to data items, about the data manufacturing process such as data source, creation time, and collection method. -

Artificial Intelligence Program 1
Artificial Intelligence Program 1 Artificial Intelligence Program Reid Simmons, Director of the BSAI program (NSH 3213) 15-122 Principles of Imperative Computation 10 (students without credit or a waiver for 15-112, Jean Harpley, Program Coordinator (NSH 1517) Fundamentals of Programming and Computer www.cs.cmu.edu/bs-in-artificial-intelligence (http://www.cs.cmu.edu/bs-in- Science, must take 15-112 before 15-122) artificial-intelligence/) 15-150 Principles of Functional Programming 10 15-210 Parallel and Sequential Data Structures and 12 Overview Algorithms 15-213 Introduction to Computer Systems 12 Carnegie Mellon University has led the world in artificial intelligence 15-251 Great Ideas in Theoretical Computer Science 12 education and innovation since the field was created. It's only natural, then, that the School of Computer Science would offer the nation's first bachelor's degree in Artificial Intelligence, which started in Fall 2018. Artificial Intelligence The new BSAI program gives students the in-depth knowledge needed to transform large amounts of data into actionable decisions. The program All of the following three AI core courses: Units and its curriculum focus on how complex inputs — such as vision, language 07-180 Concepts in Artificial Intelligence 5 and huge databases — can be used to make decisions or enhance human 15-281 Artificial Intelligence: Representation and 12 capabilities. The curriculum includes coursework in computer science, Problem Solving math, statistics, computational modeling, machine learning and symbolic computation. Because Carnegie Mellon is devoted to AI for social good, 10-315 Introduction to Machine Learning (SCS Majors) 12 students will also take courses in ethics and social responsibility, with the plus one of the following AI core courses: option to participate in independent study projects that change the world for 16-385 Computer Vision 12 the better — in areas like healthcare, transportation and education. -

Business Requirements Analysis Document (BRAD) - Trading Partner Performance Management, Release 1.0.0
Business Requirements Analysis Document (BRAD) - Trading Partner Performance Management, Release 1.0.0 Business Requirements Analysis Document (BRAD) For Trading Partner Performance Management BRAD: 1.0.0 BRG: Trading Partner Performance Management Work Group Date: 7-Nov-2008, Approved 7-Nov-2008, Approved All contents copyright © GS1 2008 Page 1 of 81 Business Requirements Analysis Document (BRAD) - Trading Partner Performance Management, Release 1.0.0 Document Summary Document Item Current Value Document Number 10713 Document Title Business Requirements Analysis Document (BRAD) Date Last Modified 7-Nov-2008 Status Approved Work Group / Chairperson Trading Partner Performance Management / Matt Johnson BRAD Template Version 2.4 Change Request Reference Date of CR Submission to GSMP: CR Submitter(s): Refer to Change Request (CR) Number(s): 13 - Jul – 2007 John Ryu, GS1 07-000283 Document Change History Date of Vers Changed By Reason for Summary of CR # Model Change ion Change Change Build # 31–Oct-2007 0.1.0 John Ryu Initial Draft Section 15 07-000283 N/A 3-Mar–2008 0.2.0 John Ryu Added agreed measures Section 15 Not N/A Matt Johnson Applicable 25-Mar-2008 0.2.2 John Ryu Based on Dallas F2F meeting Section 15 N/A N/A 9-Apr-2008 0.3.0 John Ryu Finalizing for GSMP Meeting on 20080414 Section 15 N/A N/A 11-Apr-2008 0.3.1 John Ryu Based on 20080409 teleconference Section 15 N/A N/A Matt Johnson 22-Apr-2008 0.3.2 John Ryu Based on Brussels F2F Meeting Section 15 N/A N/A 1-May-2008 0.3.3 John Ryu Posting for 60 Day Public Review Section 15 N/A N/A Start May 1 and End on June 30.