A Debate on Teaching Computing Science
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction Development Lifecycle Model
DeveIopment of a Comprehensive Software Engineering Environment Thomas C. Hartrum Gary B. Lamont Department of Electrical and Computer Engineering Department of Electrical and Computer Engineering School of Engineering School of Engineering Air Force Institute of Technology Air Force Institute of Technology Wright-Patterson AFB, Dayton, Ohio, 45433 Wright-Patterson AFB, Dayton, Ohio, 45433 Abstract The concept of an integrated software development environment The generation of a set of tools for the software lifecycle is a recur- can be realized in two distinct levels. The first level deals with the ring theme in the software engineering literature. The development of access and usage mechanisms for the interactive tools, while the sec- such tools and their integration into a software development environ- ond level concerns the preservation of software development data and ment is a difficult task at best because of the magnitude (number of the relationships between the products of the different software life variables) and the complexity (combinatorics) of the software lifecycle cycle stages. The first level requires that all of the component tools process. An initial development of a global approach was initiated at be resident under one operating system and be accessible through a AFIT in 1982 as the Software Development Workbench (SDW). Also common user interface. The second level dictates the need to store de- other restricted environments have evolved emphasizing Ada and di5 velopment data (requirements specifications, designs, code, test plans tributed processing. Continuing efforts focus on tool development, and procedures, manuals, etc.) in an integrated data base that pre- tool integration, human interfacing (graphics; SADT, DFD, structure serves the relationships between the products of the different life cy- charts, ...), data dictionaries, and testing algorithms. -

Software Development Career Pathway
Career Exploration Guide Software Development Career Pathway Information Technology Career Cluster For more information about NYC Career and Technical Education, visit: www.cte.nyc Summer 2018 Getting Started What is software? What Types of Software Can You Develop? Computers and other smart devices are made up of Software includes operating systems—like Windows, Web applications are websites that allow users to contact management system, and PeopleSoft, a hardware and software. Hardware includes all of the Apple, and Google Android—and the applications check email, share documents, and shop online, human resources information system. physical parts of a device, like the power supply, that run on them— like word processors and games. among other things. Users access them with a Mobile applications are programs that can be data storage, and microprocessors. Software contains Software applications can be run directly from a connection to the Internet through a web browser accessed directly through mobile devices like smart instructions that are stored and run by the hardware. device or through a connection to the Internet. like Firefox, Chrome, or Safari. Web browsers are phones and tablets. Many mobile applications have Other names for software are programs or applications. the platforms people use to find, retrieve, and web-based counterparts. display information online. Web browsers are applications too. Desktop applications are programs that are stored on and accessed from a computer or laptop, like Enterprise software are off-the-shelf applications What is Software Development? word processors and spreadsheets. that are customized to the needs of businesses. Popular examples include Salesforce, a customer Software development is the design and creation of Quality Testers test the application to make sure software and is usually done by a team of people. -

Verification and Formal Methods
Verification and Formal Methods: Practice and Experience J. C. P. Woodcock University of York, UK and P. G. Larsen Engineering College of Aarhus, Denmark and J. C. Bicarregui STFC Rutherford Appleton Laboratory, UK and J. S. Fitzgerald Newcastle University, UK We describe the state of the art in the industrial use of formal verification technology. We report on a new survey of the use of formal methods in industry, and compare it with the most significant surveys carried out over the last 20 years. We review the literature on formal methods, and present a series of industrial projects undetaken over the last two decades. We draw some observations from these surveys and records of experience. Based on this, we discuss the issues surrounding the industrial adoption of formal methods. Finally, we look to the future and describe the development of a Verified Software Repository, part of the worldwide Verified Software Initiative. We introduce the initial projects being used to populate the repository, and describe the challenges they address. Categories and Subject Descriptors: D.2.4 [Software/Program Verification]: Assertion check- ers, Class invariants, Correctness proofs, Formal methods, Model checking, Programming by contract; F.3.1 [Specifying and Verifying and Reasoning about Programs]: Assertions, Invariants, Logics of programs, Mechanical verification, Pre- and post-conditions, Specification techniques; F.4.1 [Mathematical Logic]: Mechanical theorem proving; I.2.2 [Automatic Pro- gramming]: Program verification. Additional Key Words and Phrases: Experimental software engineering, formal methods surveys, Grand Challenges, Verified Software Initiative, Verified Software Repository. 1. INTRODUCTION Formal verification, for both hardware and software, has been a topic of great sig- nificance for at least forty years. -

Revealing the Secrets of David Parnas
Revealing the Secrets of David Parnas H. Conrad Cunningham Department of Computer and Information Science University of Mississippi March 7, 2014 Those of us in the fast-changing field of computing often dismiss anything writ- ten more than five years ago as obsolete. Yet several decades-old papers by David L. Parnas [1, 4, 5, 6, 7, 8] are as timely as those published in recent issues of the top journals. Parnas articulates the timeless software design concepts known as information hiding and abstract interfaces. Most programmers would describe a module as a unit of code such as a sub- routine or class. Parnas focuses on the programmers rather than the programs. He defines a module as \a work assignment given to a programmer or group of programmers" as a part of a larger software development project [7]. His goals are to enable programmers to develop each module independently, change one module without affecting other modules, and comprehend the overall system by examining one module at a time [5]. Programmers often design a software system by breaking the required pro- cessing into steps and making each step a module. Instead, Parnas uses in- formation hiding to decompose the system into modules that satisfy his goals (2); each module keeps its own secreta design decision about some aspect of the system (e.g., choice of a data structure). A modules design decision can change but none of the other modules should be affected. If some aspect is unlikely to change, the design can distribute this knowledge across several modules and the interfaces among them. -

Object Oriented Programming
No. 52 March-A pril'1990 $3.95 T H E M TEe H CAL J 0 URN A L COPIA Object Oriented Programming First it was BASIC, then it was structures, now it's objects. C++ afi<;ionados feel, of course, that objects are so powerful, so encompassing that anything could be so defined. I hope they're not placing bets, because if they are, money's no object. C++ 2.0 page 8 An objective view of the newest C++. Training A Neural Network Now that you have a neural network what do you do with it? Part two of a fascinating series. Debugging C page 21 Pointers Using MEM Keep C fro111 (C)rashing your system. An AT Keyboard Interface Use an AT keyboard with your latest project. And More ... Understanding Logic Families EPROM Programming Speeding Up Your AT Keyboard ((CHAOS MADE TO ORDER~ Explore the Magnificent and Infinite World of Fractals with FRAC LS™ AN ELECTRONIC KALEIDOSCOPE OF NATURES GEOMETRYTM With FracTools, you can modify and play with any of the included images, or easily create new ones by marking a region in an existing image or entering the coordinates directly. Filter out areas of the display, change colors in any area, and animate the fractal to create gorgeous and mesmerizing images. Special effects include Strobe, Kaleidoscope, Stained Glass, Horizontal, Vertical and Diagonal Panning, and Mouse Movies. The most spectacular application is the creation of self-running Slide Shows. Include any PCX file from any of the popular "paint" programs. FracTools also includes a Slide Show Programming Language, to bring a higher degree of control to your shows. -

Rivest, Shamir, and Adleman Receive 2002 Turing Award, Volume 50
Rivest, Shamir, and Adleman Receive 2002 Turing Award Cryptography and Information Se- curity Group. He received a B.A. in mathematics from Yale University and a Ph.D. in computer science from Stanford University. Shamir is the Borman Profes- sor in the Applied Mathematics Department of the Weizmann In- stitute of Science in Israel. He re- Ronald L. Rivest Adi Shamir Leonard M. Adleman ceived a B.S. in mathematics from Tel Aviv University and a Ph.D. in The Association for Computing Machinery (ACM) has computer science from the Weizmann Institute. named RONALD L. RIVEST, ADI SHAMIR, and LEONARD M. Adleman is the Distinguished Henry Salvatori ADLEMAN as winners of the 2002 A. M. Turing Award, Professor of Computer Science and Professor of considered the “Nobel Prize of Computing”, for Molecular Biology at the University of Southern their contributions to public key cryptography. California. He earned a B.S. in mathematics at the The Turing Award carries a $100,000 prize, with University of California, Berkeley, and a Ph.D. in funding provided by Intel Corporation. computer science, also at Berkeley. As researchers at the Massachusetts Institute of The ACM presented the Turing Award on June 7, Technology in 1977, the team developed the RSA 2003, in conjunction with the Federated Computing code, which has become the foundation for an en- Research Conference in San Diego, California. The tire generation of technology security products. It award was named for Alan M. Turing, the British mathematician who articulated the mathematical has also inspired important work in both theoret- foundation and limits of computing and who was a ical computer science and mathematics. -

FUNDAMENTALS of COMPUTING (2019-20) COURSE CODE: 5023 502800CH (Grade 7 for ½ High School Credit) 502900CH (Grade 8 for ½ High School Credit)
EXPLORING COMPUTER SCIENCE NEW NAME: FUNDAMENTALS OF COMPUTING (2019-20) COURSE CODE: 5023 502800CH (grade 7 for ½ high school credit) 502900CH (grade 8 for ½ high school credit) COURSE DESCRIPTION: Fundamentals of Computing is designed to introduce students to the field of computer science through an exploration of engaging and accessible topics. Through creativity and innovation, students will use critical thinking and problem solving skills to implement projects that are relevant to students’ lives. They will create a variety of computing artifacts while collaborating in teams. Students will gain a fundamental understanding of the history and operation of computers, programming, and web design. Students will also be introduced to computing careers and will examine societal and ethical issues of computing. OBJECTIVE: Given the necessary equipment, software, supplies, and facilities, the student will be able to successfully complete the following core standards for courses that grant one unit of credit. RECOMMENDED GRADE LEVELS: 9-12 (Preference 9-10) COURSE CREDIT: 1 unit (120 hours) COMPUTER REQUIREMENTS: One computer per student with Internet access RESOURCES: See attached Resource List A. SAFETY Effective professionals know the academic subject matter, including safety as required for proficiency within their area. They will use this knowledge as needed in their role. The following accountability criteria are considered essential for students in any program of study. 1. Review school safety policies and procedures. 2. Review classroom safety rules and procedures. 3. Review safety procedures for using equipment in the classroom. 4. Identify major causes of work-related accidents in office environments. 5. Demonstrate safety skills in an office/work environment. -

Job Description - Software Engineer I
Job Description - Software Engineer I Department: Engineering - 2013-03 Exemption Status: Non-Exempt Summary: This position is responsible for software development in multi-application, multi-server, and hosted environments. The candidate will primarily provide system/configuration support with a focus in helping the needs of both internal and external customers. He or she will participate in all facets of software and system development life-cycle. The most qualified candidate for this role will have experience working with business intelligence in the public safety and/or public health software fields and have formal software education and/or a ton of practical experience. We develop primarily in C#, .NET, SQL, SSRS and mobile. Anyone that might fit well at FirstWatch must be hard-working, people-oriented, friendly, patient, a fast learner, think quickly on their feet, take initiative and responsibility, and LOVE providing our customers great and honest customer service. This person will need to maintain a high quality productivity level within a fast paced environment. This position shares responsibility (rotates) with other engineering staff for 24×7 on call duties and so must be able to thrive in this environment. Responsibilities: - Maintain and modify the software and system configurations of production, staged, and test applications. - Interface with different stakeholders to determine and propose appropriate and effective technology solutions to meet business and technical objectives. - Develop interfaces, applications and other technical solutions to support the business needs through the planning, analysis, design, development, implementation and maintenance phases of the software and systems development lifecycle. - Create system requirements, technical specifications, and test plans. -

Welcome to AI Matters 5(1)
AI MATTERS, VOLUME 5, ISSUE 1 5(1) 2019 Welcome to AI Matters 5(1) Amy McGovern, co-editor (University of Oklahoma; [email protected]) Iolanda Leite, co-editor (Royal Institute of Technology (KTH); [email protected]) DOI: 10.1145/3320254.3320255 Issue overview receiving the 2018 ACM A.M. Turing Award! Welcome to the first issue of the fifth vol- ume of the AI Matters Newsletter! This issue opens with some news on a new SIGAI Stu- Submit to AI Matters! dent Travel Scholarship where we aim to en- Thanks for reading! Don’t forget to send courage students from traditionally underrep- your ideas and future submissions to AI resented geographic locations to apply and at- Matters! We’re accepting articles and an- tend SIGAI supported events. We also sum- nouncements now for the next issue. De- marize the fourth AAAI/ACM SIGAI Job Fair, tails on the submission process are avail- which continues to grow with the increasing able at http://sigai.acm.org/aimatters. popularity of AI. In our interview series, Marion Neumann interviews Tom Dietterich, an Emer- itus Professor at Oregon State University and one of the pioneers in Machine Learning. Amy McGovern is co- In our regular columns, we have a summary editor of AI Matters. She of recent and upcoming AI conferences and is a Professor of com- events from Michael Rovatsos. Our educa- puter science at the Uni- tional column this issue is dedicated to “biduc- versity of Oklahoma and tive computing”, one of Prolog’s most distinc- an adjunct Professor of tive features. -

Formal Methods
SE 5302: Formal Methods Course Instructor: Parasara Sridhar Duggirala, Ph.D. Catalog Description. 3 credits. This course is designed to provide students with an introduction to formal methods as a framework for the specification, design, and verification of software-intensive embedded systems. Topics include automata theory, model checking, theorem proving, and system specification. Examples are driven by cyber-physical systems. The course is addressed to students in engineering who have had at least a year of software or embedded systems design experience. Pre- Requisites: SE 5100 or SE 5101 or SE 5102 and at least one year of software or embedded systems design experience. Course Delivery Method. The course will be offered online, asynchronously, in small recorded modules according to the course schedule and syllabus. Direct and live communication with the instructor will be available each week, according to the class schedule, for discussion, questions, examples, and quizzes. Attendance at live sessions is required, and you must notify the instructor in advance if you cannot attend. A social networking tool called Slack will be used to communicate with students and the instructor between live sessions. Course Objective. This course is designed to provide students with an introduction to formal methods as a framework for the specification, design, and verification of software- intensive embedded systems. Topics include automata theory, model checking, theorem proving, and system specification. Examples are driven by control systems and software systems. Anticipated Student Outcomes. By the end of the course, a student will be able to (1) Gain familiarity with current system design flows in industry used for embedded system design, implementation and verification. -
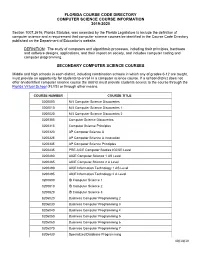
Florida Course Code Directory Computer Science Course Information 2019-2020
FLORIDA COURSE CODE DIRECTORY COMPUTER SCIENCE COURSE INFORMATION 2019-2020 Section 1007.2616, Florida Statutes, was amended by the Florida Legislature to include the definition of computer science and a requirement that computer science courses be identified in the Course Code Directory published on the Department of Education’s website. DEFINITION: The study of computers and algorithmic processes, including their principles, hardware and software designs, applications, and their impact on society, and includes computer coding and computer programming. SECONDARY COMPUTER SCIENCE COURSES Middle and high schools in each district, including combination schools in which any of grades 6-12 are taught, must provide an opportunity for students to enroll in a computer science course. If a school district does not offer an identified computer science course the district must provide students access to the course through the Florida Virtual School (FLVS) or through other means. COURSE NUMBER COURSE TITLE 0200000 M/J Computer Science Discoveries 0200010 M/J Computer Science Discoveries 1 0200020 M/J Computer Science Discoveries 2 0200305 Computer Science Discoveries 0200315 Computer Science Principles 0200320 AP Computer Science A 0200325 AP Computer Science A Innovation 0200335 AP Computer Science Principles 0200435 PRE-AICE Computer Studies IGCSE Level 0200480 AICE Computer Science 1 AS Level 0200485 AICE Computer Science 2 A Level 0200490 AICE Information Technology 1 AS Level 0200495 AICE Information Technology 2 A Level 0200800 IB Computer -

Oral History Interview with Severo Ornstein and Laura Gould
An Interview with SEVERO ORNSTEIN AND LAURA GOULD OH 258 Conducted by Bruce H. Bruemmer on 17 November 1994 Woodside, CA Charles Babbage Institute Center for the History of Information Processing University of Minnesota, Minneapolis Severo Ornstein and Laura Gould Interview 17 November 1994 Abstract Ornstein and Gould discuss the creation and expansion of Computer Professionals for Social Responsibility (CPSR). Ornstein recalls beginning a listserve at Xerox PARC for those concerned with the threat of nuclear war. Ornstein and Gould describe the movement of listserve participants from e-mail discussions to meetings and forming a group concerned with computer use in military systems. The bulk of the interview traces CPSR's organizational growth, fundraising, and activities educating the public about computer-dependent weapons systems such as proposed in the Strategic Defense Initiative (SDI). SEVERO ORNSTEIN AND LAURA GOULD INTERVIEW DATE: November 17, 1994 INTERVIEWER: Bruce H. Bruemmer LOCATION: Woodside, CA BRUEMMER: As I was going through your oral history interview I began to wonder about your political background and political background of the people who had started the organization. Can you characterize that? You had mentioned in your interview that you had done some antiwar demonstrations and that type of thing which is all very interesting given also your connection with DARPA. ORNSTEIN: Yes, most of the people at DARPA knew this. DARPA was not actually making bombs, you understand, and I think in the interview I talked about my feelings about DARPA at the time. I was strongly against the Vietnam War and never hid it from anyone. I wore my "Resist" button right into the Pentagon and if they didn't like it they could throw me out.