Technical Analysis of the Pegasus Exploits On
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Submission of the Citizen Lab (Munk School of Global Affairs and Public Policy, University of Toronto) to the United Nations
Submission of the Citizen Lab (Munk School of Global Affairs and Public Policy, University of Toronto) to the United Nations Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression on the surveillance industry and human rights February 15, 2019 For all inquiries related to this submission, please contact: Dr. Ronald J. Deibert Director, the Citizen Lab, Munk School of Global Affairs and Public Policy Professor of Political Science, University of Toronto [email protected] Contributors to this report: Siena Anstis, Senior Legal Advisor, Citizen Lab Dr. Ronald J. Deibert, Professor of Political Science; Director, Citizen Lab Jon Penney, Research Fellow, Citizen Lab; Associate Professor and Director, Law & Technology Institute, Schulich School of Law Acknowledgments: We would also like to thank Miles Kenyon (Communications Specialist, Citizen Lab) and Adam Senft (Operations Manager, Citizen Lab) for their support in reviewing this submission. 1 Table of Contents Executive Summary 3 About the Citizen Lab 5 Citizen Lab Research on the Use of Private Surveillance Technology Against Human Rights Actors 6 1. NSO Group’s Pegasus 6 The case of Ahmed Mansoor in the United Arab Emirates 7 Targeting civil society, journalists, politicians, and others in Mexico 7 Mapping Pegasus infections and the case of Omar Abdulaziz in Canada 8 Additional cases of targeting 8 2. Cyberbit’s PC Surveillance System 9 3. FinFisher and FinSpy 9 4. Hacking Team’s Remote Control System 10 Common Trends among Private Companies in the Surveillance Industry 11 1. Sales to states with poor human rights records 11 2. -

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

A Review of Fuzzing Tools and Methods 1 Introduction
A Review of Fuzzing Tools and Methods James Fell, [email protected] Originally published in PenTest Magazine on 10th March 2017 1 Introduction Identifying vulnerabilities in software has long been an important research problem in the field of information security. Over the last decade, improvements have been made to programming languages, compilers and software engineering methods aimed at reducing the number of vulnerabilities in software [26]. In addition, exploit mitigation features such as Data Execution Prevention (DEP) [65] and Address Space Layout Randomisation (ASLR) [66] have been added to operating systems aimed at making it more difficult to exploit the vulnerabilities that do exist. Nevertheless, it is fair to say that all software applications of any significant size and complexity are still likely to contain undetected vulnerabilities and it is also frequently possible for skilled attackers to bypass any defences that are implemented at the operating system level [6, 7, 12, 66]. There are many classes of vulnerabilities that occur in software [64]. Ultimately they are all caused by mistakes that are made by programmers. Some of the most common vulnerabilities in binaries are stack based and heap based buffer overflows, integer overflows, format string bugs, off-by-one vulnerabilities, double free and use-after-free bugs [5]. These can all lead to an attacker hijacking the path of execution and causing his own arbitrary code to be executed by the victim. In the case of software running with elevated privileges this can lead to the complete compromise of the host system on which it is running. -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -

DOCUMENT RESUME ED 052 058 SE 012 062 AUTHOR Kohn, Raymond F. Environmental Education, the Last Measure of Man. an Anthology Of
DOCUMENT RESUME ED 052 058 SE 012 062 AUTHOR Kohn, Raymond F. TITLE Environmental Education, The Last Measure of Man. An Anthology of Papers for the Consideration of the 14th and 15th Conference of the U.S. National Commission for UNESCO. INSTITUTION National Commission for UNESCO (Dept. of State), Washington, D.C. PUB DATE 71 NOTE 199p. EDRS PRICE EDRS Price MF-$0.65 HC-$6.58 DESCRIPTORS Anthologies, *Ecology, *Environment, EnVironmental Education, Environmental Influences, *Essays, *Human Engineering, Interaction, Pollution IDENTIFIERS Unesco ABSTRACT An anthology of papers for consideration by delegates to the 14th and 15th conferences of the United States National Commission for UNESCO are presented in this book. As a wide-ranging collection of ideas, it is intended to serve as background materials for the conference theme - our responsibility for preserving and defending a human environment that permits the full growth of man, physical, cultural, and social. Thirty-four essays are contributed by prominent authors, educators, historians, ecologists, biologists, anthropologists, architects, editors, and others. Subjects deal with the many facets of ecology and the environment; causes, effects, and interactions with man which have led to the crises of today. They look at what is happening to man's "inside environment" in contrast to the physical or outside environment as it pertains to pollution of the air, water, and land. For the common good of preserving the only means for man's survival, the need for world cooperation and understanding is emphatically expressed. (BL) U.S. DEPARTMENT OF HEALTH. EDUCATION & WELFARE OFFICE OF EDUCATION THIS DOCUMENT HAS BEEN REPRO- DUCED EXACTLY AS RECEIVED FROM THE PERSON OR ORGANIZATION ORIG- INATING IT. -
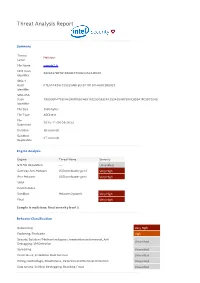
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Wannacry Two Years Later: How Did We Get the Data?
WANNACRY TWO YEARS LATER: HOW DID WE GET THE DATA? WANNACRY TWO YEARS LATER: HOW DID WE GET THE DATA? – © 2019 ARMIS, INC. WANNACRY TWO YEARS LATER: How Did We Get the Data? DNS Cache Probing WannaCry’s Kill Switch Domain The DNS cache probing technique was first introduced in a 2004 paper titled “Snooping the Cache for Fun and Profit." The technique is used to identify domain names in use by users of a specific ISP by identifying poorly configured DNS servers and probing their domain cache. By sending specific queries to these DNS servers, it is possible to ascertain if a specific domain name was previously queried by one (or more) of the ISP’s clients. This results in that domain becoming registered on the DNS server’s domain cache for a limited amount of time, depending on the TTL of the domain. In a recent study, the Citizen Lab group used this technique to identify ISPs in which NSO’s Pegasus spyware was in use. For.our research, we adapted this technique to track ISPs that have WannaCry’s main kill switch domains in their DNS servers’ cache. The technical implementation details of this technique were largely detailed in previous works, but these are the steps we conducted: 1. We set up four servers, in different parts of the world and conducted a full IPv4 scan to create a current database of all the DNS servers worldwide. This resulted in approximately 5 million DNS servers. 2. From this initial list, we needed to identify the servers which supported cache snooping, but in a trustworthy way which would enable us to query their cache for the kill switch domain, and verify whether it is present in the cache. -

October 2011 Vol
NoSQL GREG BURD Hypervisors and Virtual Machines: Implementation Insights on the x86 Architecture DON REVELLE Conference Reports from the 2011 USENIX Annual Technical Conference, HotPar, and more OCTOBER 2011 VOL. 36, NO. 5 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION THE ADVANCED COMPUTING SYSTEMS ASSOCIATION usenix_login_oct11_covers.indd 1 9.9.11 5:55 PM UPCOMING EVENTS 23rd ACM Symposium on Operating Systems 9th USENIX Symposium on Networked Systems Principles (SOSP 2011) Design and Implementation (NSDI ’12) SPONSORED BY ACM SIGOPS IN COOPERATION WITH USENIX SPONSORED BY USENIX IN COOPERATION WITH ACM SIGCOMM AND ACM SIGOPS October 23–26, 2011, Cascais, Portugal April 25–27, 2012, San Jose, CA http://sosp2011.gsd.inesc-id.pt http://www.usenix.org/nsdi12 ACM Symposium on Computer Human Interac- tion for Management of Information Technology 2012 USENIX Federated Conferences Week (CHIMIT 2011) June 12–15, 2012, Boston, MA, USA http://www.usenix.org/fcw12 SPONSORED BY ACM IN ASSOCIATION WITH USENIX December 4–5, 2011, Boston, MA 2012 USENIX Annual Technical Conference http://chimit.acm.org/ (USENIX ATC ’12) June 13–15, 2012, Boston, MA 25th Large Installation System Administration http://www.usenix.org/atc12 Conference (LISA ’11) Paper titles and abstracts due January 10, 2012 SPONSORED BY USENIX IN COOPERATION WITH LOPSA December 4–9, 2011, Boston, MA 21st USENIX Security Symposium http://www.usenix.org/lisa11 (USENIX Security ’12) August 6–10, 2012, Bellevue, WA ACM/IFIP/USENIX 12th International Middleware Conference (Middleware 2011) -

Software Vulnerabilities Principles, Exploitability, Detection and Mitigation
Software vulnerabilities principles, exploitability, detection and mitigation Laurent Mounier and Marie-Laure Potet Verimag/Université Grenoble Alpes GDR Sécurité – Cyber in Saclay (Winter School in CyberSecurity) February 2021 Software vulnerabilities . are everywhere . and keep going . 2 / 35 Outline Software vulnerabilities (what & why ?) Programming languages (security) issues Exploiting a sofwtare vulnerability Software vulnerabilities mitigation Conclusion Example 1: password authentication Is this code “secure” ? boolean verify (char[] input, char[] passwd , byte len) { // No more than triesLeft attempts if (triesLeft < 0) return false ; // no authentication // Main comparison for (short i=0; i <= len; i++) if (input[i] != passwd[i]) { triesLeft-- ; return false ; // no authentication } // Comparison is successful triesLeft = maxTries ; return true ; // authentication is successful } functional property: verify(input; passwd; len) , input[0::len] = passwd[0::len] What do we want to protect ? Against what ? I confidentiality of passwd, information leakage ? I control-flow integrity of the code I no unexpected runtime behaviour, etc. 3 / 35 Example 2: make ‘python -c ’print "A"*5000’‘ run make with a long argument crash (in recent Ubuntu versions) Why do we need to bother about crashes (wrt. security) ? crash = consequence of an unexpected run-time error not trapped/foreseen by the programmer, nor by the compiler/interpreter ) some part of the execution: I may take place outside the program scope/semantics I but can be controled/exploited by an attacker (∼ “weird machine”) out of scope execution runtime error crash normal execution possibly exploitable ... security breach ! ,! may break all security properties ... from simple denial-of-service to arbitrary code execution Rk: may also happen silently (without any crash !) 4 / 35 Back to the context: computer system security what does security mean ? I a set of general security properties: CIA Confidentiality, Integrity, Availability (+ Non Repudiation + Anonymity + . -

Intrinsic Propensity for Vulnerability in Computers? Arbitrary Code Execution in the Universal Turing Machine
Intrinsic Propensity for Vulnerability in Computers? Arbitrary Code Execution in the Universal Turing Machine Pontus Johnson KTH Royal Institute of Technology Stockholm, Sweden [email protected] Abstract and Weyuker in [4], “Turing’s construction of a universal computer in 1936 provided reason to believe that, at least in The universal Turing machine is generally considered to be principle, an all-purpose computer would be possible, and the simplest, most abstract model of a computer. This paper was thus an anticipation of the modern digital computer.” Or, reports on the discovery of an accidental arbitrary code execu- in the words of Stephen Wolfram [16], ‘what launched the tion vulnerability in Marvin Minsky’s 1967 implementation whole computer revolution is the remarkable fact that uni- of the universal Turing machine. By submitting crafted data, versal systems with fixed underlying rules can be built that the machine may be coerced into executing user-provided can in effect perform any possible computation.” Not only code. The article presents the discovered vulnerability in de- the universality, but also the simplicity of the universal Tur- tail and discusses its potential implications. To the best of our ing machine has attracted interest. In 1956, Claude Shannon knowledge, an arbitrary code execution vulnerability has not explored some minimal forms of the universal Turing ma- previously been reported for such a simple system. chine [13], and posed the challenge to find even smaller such machines. That exploration has continued to this day [16]. 1 Introduction A common strategy for understanding a problem is to re- duce it to its minimal form. -

Automated Malware Analysis Report For
ID: 310931 Sample Name: 44S5D444F55G8222Y55UU44S4S.vbs Cookbook: default.jbs Time: 07:32:12 Date: 07/11/2020 Version: 31.0.0 Red Diamond Table of Contents Table of Contents 2 Analysis Report 44S5D444F55G8222Y55UU44S4S.vbs 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Startup 4 Malware Configuration 4 Yara Overview 4 Sigma Overview 4 Signature Overview 4 AV Detection: 5 Data Obfuscation: 5 Persistence and Installation Behavior: 5 Malware Analysis System Evasion: 5 HIPS / PFW / Operating System Protection Evasion: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 7 URLs 7 Domains and IPs 8 Contacted Domains 8 Contacted URLs 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 9 General Information 9 Simulations 10 Behavior and APIs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 11 General 11 File Icon 12 Network Behavior 12 TCP Packets 12 HTTP Request Dependency Graph 12 HTTP Packets 12 Code Manipulations 13 Statistics 13 Behavior 13 System Behavior 14 Analysis Process: wscript.exe PID: 6124 Parent PID: 3388 14 Copyright null 2020 Page 2 of 15 General 14 File Activities 14 File Created 14 File Written 14 Registry Activities 15 Analysis Process: wscript.exe PID: 5560 Parent PID: 6124 15 General 15 File Activities 15 Disassembly 15 Code Analysis 15 Copyright null 2020 Page 3 of