Paideia, Vol. 6, Issue 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Postsecondary Success, Debt, and Philanthropy's Role
Postsecondary Success, Debt, and Philanthropy’s Role June 20, 2017 Agenda 8:30am – 9:00am Breakfast 9:00am – 9:20am Welcoming Remarks • Stephanie Bell-Rose, Senior Managing Director and Head, TIAA Institute • Chris Page, Executive Vice President, Rockefeller Philanthropy Advisors 9:20am – 10:00 am The Facts About Student Debt: Presentation and Discussion • Sandy Baum, Higher Education Economist and Senior Fellow, Urban Institute 10:00am – 10:10am Break 10:10am – 11:30am Panel Discussion • Rick Calero, Senior Managing Director, Strategic Initiatives, TIAA; Aspen Finance Leaders Fellow • Daniel Greenstein, Director of Education, Postsecondary Success in the United States, Bill & Melinda Gates Foundation • Gail Mellow, President, LaGuardia Community College • Zakiya Smith, Strategy Director for Finance and Federal Policy, Lumina Foundation • Amy Holmes, Senior Philanthropic Advisor and Manager, Rockefeller Philanthropy Advisors (moderator) 11:30am – 12:00pm Questions and Discussion 12:00pm – 1:00pm Optional networking lunch (boxed lunch available) Postsecondary Success, Debt, and Philanthropy’s Role June 20, 2017 Speaker Bios Sandy Baum, Higher Education Economist and Senior Fellow, the Urban Institute Sandy Baum is a senior fellow at the Urban Institute and professor emerita of economics at Skidmore College. Dr. Baum earned her B.A. in sociology at Bryn Mawr College, where she is currently a member of the Board of Trustees, and her Ph.D. in economics at Columbia University. She has written and spoken extensively on issues relating to college access, college pricing, student aid policy, student debt, affordability, and other aspects of higher education finance. Dr. Baum has co-authored the College Board’s annual publications Trends in Student Aid and Trends in College Pricing since 2002. -

Intellectual Property Theft and Its Impact on the US-China Relationship Amy Holmes
CONTRIBUTOR BIO AMY HOLMES is a fourth year Political Science major graduating in June 2019. She will graduate with a Pre-Law concentration and French and Global Politics minors. At Cal Poly, Amy is the Executive Editor of Paideia, Political Science Club President, a member of the Pi Sigma Alpha honors society, and a member of the Phi Alpha Delta pre-law fraternity. Originally from England, Amy grew up in Yucaipa, California. Her academic interests in international affairs stem from her international upbringing. She studies intellectual property law and international affairs, and this fall she will move on to law school. Amy’s personal interests include baking, reading, and traveling. By Ethan Gunnlaugsson 137 Intellectual Property Theft and its Impact on the US-China Relationship Amy Holmes Abstract Growing in frequency in recent years, theft of United States intellectual property by China has become a serious concern for the US government. This theft impacts many areas of US life including increased cost of goods, diffculty participating in international trade, and increased national security concerns. This paper looks at three areas of intellectual property theft: patent theft, copyright theft, and trade secret theft, using specifc examples of each. In examining each of these examples, we discuss the implications of this theft for US citizens as well as the relationship between the United States and Chinese governments. This paper concludes that Chinese intellectual property theft has a signifcant negative impact on the relationship -

Shaun Higgins
KSPS Community Advisory Board Minutes – 4/12/18 CAB members attending in person: Shaun Higgins (Chair), Becka Shelley (Vice Chair), Emily Geddes (Secretary - minutes), Consuelo Larrabee, James Albrecht, Vanessa Strange Members attending by video conferencing: Bob Morrison Members absent: Terrie Ashby-Scott, Joyce Griffin-Sobel KSPS staff attending: Cary Balzer (Program Director), Gary Stokes (General Manager – partly in person, partly by phone), Dawn Bayman (Director of DeveloPment) Ann Hurst (Chair, Friends of KSPS Board of Directors – by video conferencing) Public attendees: none Opening Business A quorum being present, the meeting was called to order at 4:00 pm. The minutes from the 3/8/18 meeting were aPProved (motion: Consuelo, second: James). Emily will forward them to Dawn to be Posted on the KSPS website, in compliance with Corporation for Public Broadcasting (CPB) requirements, and to Linda Finney, Friends of KSPS board secretary, in comPliance with the bylaws. Program Manager Report Cary mentioned several upcoming programs of interest including: • Royal Wedding Watch, airing May 14-18 leading uP to the live broadcast of the royal wedding on Saturday, May 19. • Season 4 of Grantchester later this summer. This will be the final season starring James Norton. • In Principle, a new conservative Political talk show featuring the team of columnist Michael Gerson and commentator Amy Holmes, which will air weekly starting Friday, APril 13. • A new half-hour public affairs series called Firing Line with Margaret Hoover: a “new generation” of the original Firing Line with William F. Buckley, Jr. that will incorPorate clips from the original series. The FNX (First Nations ExPerience) launch on channel 19 went well. -

BC Law Magazine Fall/Winter 2009 Boston College Law School
Boston College Law School Digital Commons @ Boston College Law School Boston College Law School Magazine 10-1-2009 BC Law Magazine Fall/Winter 2009 Boston College Law School Follow this and additional works at: http://lawdigitalcommons.bc.edu/bclsm Part of the Legal Education Commons Recommended Citation Boston College Law School, "BC Law Magazine Fall/Winter 2009" (2009). Boston College Law School Magazine. Book 35. http://lawdigitalcommons.bc.edu/bclsm/35 This Magazine is brought to you for free and open access by Digital Commons @ Boston College Law School. It has been accepted for inclusion in Boston College Law School Magazine by an authorized administrator of Digital Commons @ Boston College Law School. For more information, please contact [email protected]. helping the wrongly deported | meet the new faculty | report on giving BOSTON COLLEGE LAW SCHOOL MAGAZINE | FALL / WINTER 2009 Student anjali nair ’12 wrote a winning essay Introducing our enhanced online magazine www.bc.edu/bclawmagazine gettingstudent essays that made the case for in admission BCBC LawNetLawNet make the connection Want a paperless way to stay connected? BC Law’s new alumni online community allows our graduates to connect www.bc.edu/lawnet like never before. But please, don’t take our word for it. Having trouble signing on? Contact [email protected] Register now and experience some of the exciting features for yourself ! Alumni Directory Career Resources My Profile Event Registration Class Notes Chapter Webpages Yellow Pages Try our new Facebook application! Learn more at www.bc.edu/lawnet ad2.indd 1 12/4/09 4:28:45 PM Contents F a l l / w i n T e r 2 0 0 9 V o l u m e 1 8 | n u m b e r 1 DEPARTMENTS 2 In Limine 3 Behind the Columns 4 In Brief 10 Legal Currents Civil Unions for All A provocative option JUvenile JUstiCe er SS Lessons from Israel re 24 ST 30 Point of View clyde berg 31 Faculty sCholAr’s forUm FEATURES William Homans’ biography profile: Kent Greenfield 12 Winning Words BenChmArks admission essays that scored big. -

Views with the Nation's Leading Thinkers and Newsmakers
Amy Holmes Acclaimed Political Commentator and Host of PBS's “In Principle” Amy Holmes is a familiar face with an unconventional voice in political news. As an on-air political analyst, Amy dissects and debates the issues of the day, appearing regularly on CNN, MSNBC, Fox News, and PBS. She is co-host of the new PBS weekly show, In Principle, where she will be conducting serious, thought provoking, in- depth interviews with the nation's leading thinkers and newsmakers. She is the former host of the daily MSNBC morning show Way Too Early and was a news anchor on Glenn Beck’s TheBlaze TV and a host of TheBlaze’s Real News. In addition to working with TheBlaze and MSNBC, she co-hosted The Washington Times and Talk Radio Network's America’s Morning News, a nationally-syndicated morning radio show heard coast-to-coast by over 1.5 million listeners daily. She has interviewed national newsmakers including Donald Trump, Donald Rumsfeld, Karl Rove, leading senators, congressmen, and governors—alongside best-selling authors and celebrities including Oscar-winning director Oliver Stone. Amy won the "Thurgood Marshall Community Leader" Award for covering both the 2006 and 2008 political seasons for CNN, appearing regularly on the network’s top rated shows including AC360, Larry King Live, Wolf Blitzer’s Situation Room, CNN’s Election Center, and CNN International’s weekly political roundup. Exclusively represented by Leading Authorities speakers bureau, Amy is whip smart, projecting a warm and accessible style that has earned her guest spots on ABC’s The View, and HBO’s Real Time with Bill Maher. -
Peter You'll Be Amazed by All There Is to See!!! Barbara Please Know That
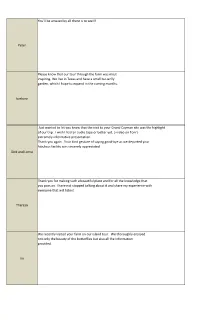
You'll be amazed by all there is to see!!! Peter Please know that our tour through the farm was most inspiring. We live in Texas and have a small butterfly garden, which I hope to expand in the coming months. barbara Just wanted to let you know that the visit to your Grand Cayman site was the highlight of our trip. I wish I had an audio tape or better yet, a video on Toni's extremely informative presentation. Thank you again. Your kind gesture of saying good‐bye as we departed your fabulous facility was sincerely appreciated. Dick and Lorna Thank you for making such a beautiful place and for all the knowledge that you pass on. I have not stopped talking about it and share my experience with everyone that will listen! Theresa We recently visited your farm on our island tour. We thoroughly enjoyed not only the beauty of the butterflies but also all the information provided. Irv We enjoyed our visit with our parents & grandparents. The butterfly's came right over and sat on our fingers. Wyatt & Alyson I thought you have a very beautiful and informitive web site. keep up the good work. Tammy Levy I look forward to seeing your online giftshop. Sandra Hadley We were at the Butterfly farm in St. Martin earlier this month. We have always wanted to stop there, but we always seem to think the beaches are more important. We had a marvelous experience. We actually spent 2 days visiting the farm. It is a remarkable place. Our grandson loves butterflies, so I took about 50 pictures to share with him. -
Jury Convicts Man in Killing
Project1:Layout 1 6/10/2014 1:13 PM Page 1 Olympics: USA men’s boxing has revival in Tokyo /B1 THURSDAY T O D A Y C I T R U S C O U N T Y & n e x t m o r n i n g HIGH 84 Numerous LOW storms. Localized flooding possible. 73 PAGE A4 www.chronicleonline.com AUGUST 5, 2021 Florida’s Best Community Newspaper Serving Florida’s Best Community $1 VOL. 126 ISSUE 302 SO YOU KNOW I The Florida Depart- ment of Health Jury convicts man in killing has ceased the daily COVID-19 re- ports that have been used to track Michael Ball, 64, faces possibility of life in prison for shooting of neighbor changes in the MIKE WRIGHT It’s as simple as prison. Sentenc- video recording of an in- video. “I hate it but he number of corona- Staff writer that,” Ball said. ing was set for terview detectives con- didn’t give me no virus cases and A four-man, Sept. 15. ducted with Ball at the choice.” deaths in the state. A Beverly Hills man on two-woman jury Ball, 64, was county jail after the Ball said he had just trial for second-degree held Ball respon- charged in the shooting. finished cleaning the murder in the shooting sible, convicting March 25, 2020, During the interview, handgun when he stuffed NEWS death of a neighbor said him as charged death of 32-year- Ball repeatedly states he it in his waistband, cov- he was afraid for his life Wednesday eve- old Tyler Dorbert shot Dorbert out of fear ered with a sweatshirt, BRIEFS when he pulled the ning at the conclu- Michael on a street outside based on an assault that and went outside to get trigger. -

Program for the 2014 Annual Meeting Theme: “Disagreement, Debate, Discussion”
Thursday, Jan. 2, Digital History Workshop, LAC Tours, Teaching Workshop 29 Program for the 2014 Annual Meeting Theme: “Disagreement, Debate, Discussion” (Re)Calibrating a World History Survey at a Public HBCU WORKSHOP Charles V. Reed, Elizabeth City State University History at an Urban Two-Year College Thursday, January 2, 9:00 a.m.–12:00 p.m. Emily Sohmer Tai, Queensborough Community College, City How to Get Started in Digital History University of New York Marriott Wardman Park, Delaware Suite Preserving History: The Value of History Education for a Career- Minded Generation See www.historians.org/annual for further information. David J. Trowbridge, Marshall University 9:50–10:30 a.m. Thinking about Gen Ed as Part of a Larger System LOCAL ARRANGEMENTS COMMITTEE Chair: Richard Bond, Virginia Wesleyan College TOURS Panel: History Teaching at/on an AAC&U-LEAP Campus Kenneth Nivison, Southern New Hampshire University Thursday, January 2, 9:30 a.m.–12:30 p.m. System-Wide Learning Outcomes at a Texas Community College Jonathan A. Lee, San Antonio College Tour 1: Up Close with Original Civil War Photos Marriott Wardman Park, Park Tower Room 8226 Pressures for Transferability Marianne S. Wokeck, Indiana University-Purdue University Tour leader: Helena Zinkham, director, Prints and Photographs Division, Indianapolis Library of Congress Participants will tour the Library of Congress Prints and Photographs Division 10:45–11:30 a.m. Approaches to History Pedagogy in General in the Madison Building. The division holds thousands of images relating to Education Curricula the Civil War, including glass negatives, ambrotype and tintype portraits, and Chair: Nancy L. -

VB Heg 2K10 Page 1 of 108 Heg Disad
VB Heg 2k10 Page 1 of 108 Heg Disad Heg Disad ..............................................................................................................................................................1 1NC Shell ...............................................................................................................................................................3 1NC Shell ...............................................................................................................................................................4 1NC Shell ...............................................................................................................................................................5 Ux—Leadership Now .............................................................................................................................................6 Ux—Leadership Now .............................................................................................................................................7 Ux—Economy/Dollar..............................................................................................................................................8 Ux—Latin America .................................................................................................................................................9 Ux—Now Key.......................................................................................................................................................10 Links—Military Presence......................................................................................................................................11 -

College of Wooster Miscellaneous Materials: a Finding Tool
College of Wooster Miscellaneous Materials: A Finding Tool Denise Monbarren August 2021 Box 1 #GIVING TUESDAY Correspondence [about] #GIVINGWOODAY X-Refs. Correspondence [about] Flyers, Pamphlets See also Oversized location #J20 Flyers, Pamphlets #METOO X-Refs. #ONEWOO X-Refs #SCHOLARSTRIKE Correspondence [about] #WAYNECOUNTYFAIRFORALL Clippings [about] #WOOGIVING DAY X-Refs. #WOOSTERHOMEFORALL Correspondence [about] #WOOTALKS X-Refs. Flyers, Pamphlets See Oversized location A. H. GOULD COLLECTION OF NAVAJO WEAVINGS X-Refs. A. L. I. C. E. (ALERT LOCKDOWN INFORM COUNTER EVACUATE) X-Refs. Correspondence [about] ABATE, GREG X-Refs. Flyers, Pamphlets See Oversized location ABBEY, PAUL X-Refs. ABDO, JIM X-Refs. ABDUL-JABBAR, KAREEM X-Refs. Clippings [about] Correspondence [about] Flyers, Pamphlets See Oversized location Press Releases ABHIRAMI See KUMAR, DIVYA ABLE/ESOL X-Refs. ABLOVATSKI, ELIZA X-Refs. ABM INDUSTRIES X-Refs. ABOLITIONISTS X-Refs. ABORTION X-Refs. ABRAHAM LINCOLN MEMORIAL SCHOLARSHIP See also: TRUSTEES—Kendall, Paul X-Refs. Photographs (Proof sheets) [of] ABRAHAM, NEAL B. X-Refs. ABRAHAM, SPENCER X-Refs. Clippings [about] Correspondence [about] Flyers, Pamphlets ABRAHAMSON, EDWIN W. X-Refs. ABSMATERIALS X-Refs. Clippings [about] Press Releases Web Pages ABU AWWAD, SHADI X-Refs. Clippings [about] Correspondence [about] ABU-JAMAL, MUMIA X-Refs. Flyers, Pamphlets ABUSROUR, ABDELKATTAH Flyers, Pamphlets ACADEMIC AFFAIRS COMMITTEE X-Refs. ACADEMIC FREEDOM AND TENURE X-Refs. Statements ACADEMIC PROGRAMMING PLANNING COMMITTEE X-Refs. Correspondence [about] ACADEMIC STANDARDS COMMITTEE X-Refs. ACADEMIC STANDING X-Refs. ACADEMY OF AMERICAN POETRY PRIZE X-Refs. ACADEMY SINGERS X-Refs. ACCESS MEMORY Flyers, Pamphlets ACEY, TAALAM X-Refs. Flyers, Pamphlets ACKLEY, MARTY Flyers, Pamphlets ACLU Flyers, Pamphlets Web Pages ACRES, HENRY Clippings [about] ACT NOW TO STOP WAR AND END RACISM X-Refs. -

On the Hill Possible
The Shakespeare Theatre Company gratefully acknowledges the generous support of the following companies and friends who helped make Will on the Hill possible: LEAD SPONSOR FROM THE CO-CHAIRS: On, Monday, June 15, the Shakespeare Theatre Company held its 13th annual Will on the Hill event. The most successful event to date, we MEDIA SPONSOR EXECUTIVE SPONSORS welcomed a phenomenal cast and distinguished Members of Congress, national media personalities, corporate VIPs, and senior Hill staff to Sidney Harman Hall and raised over $500,000 for the Company’s year-round education and community engagement programs. Following the pre-performance reception with the Who’s Who of DIRECTOR SPONSORS Washington, the evening’s guests settled in for the show. The Will on the Hill performance was preceded by a disco-style take on the Nick & wrestling scene from As You Like It prepared by the Company’s Maria Allard star Text Alive! class from West Springfield High School—a key demonstration of the programs supported by Will on the Hill’s Stephen & fundraising efforts. Lisa Ryan The illustrious cast of Peter Byrne’s original play, Midsummer Madness, then took the stage, featuring Helen Hayes Award-Winning STC Affiliated Artist Edward Gero Henry( IV, Parts 1 and 2), Samira Wiley (Orange is the New Black), and Tony Award® Nominee Brandon PRODUCER Uranowitz (An American in Paris). Fellow cast members included Senators Chris Coons and Patrick Leahy, Fox News’ Rich Edson, NPR’s Aflac • Peter Cherukuri • CLS Strategies • Nissan • Sovereign Strategy Limited Robert Siegel, The Washington Post’s Dana Milbank, The Weekly Vulcan Materials Company • Jonathan and Lynn Yarowsky Standard’s Kelly Jane Torrance, and nearly 20 U.S. -

C O M P a Ñ Ía S D E M U D a N Z a : ¿ Q U Ié
1 2 Índice Exceso de regulación: ¿Cuándo hay suficientes leyes? ................................... 5 Guía ...................................................................................................................... 7 Cuadro de Pensar con acrósticos ................................................................... 13 Compañías de mudanza: ¿Quién escoge quién le hace la mudanza? .....15 Guía .................................................................................................................... 17 Cuadro de Más, menos e interesante PMI ................................................... 24 Protección de especies en peligro: ¿El efecto salvaje de una buena idea? .................................................................25 Guía .................................................................................................................... 26 Cuadro K-W-L .................................................................................................. 32 Interesado en un Lyft: ¿Regulando su viaje?............................................33 Guía .................................................................................................................... 35 Cuadro de Más, menos e interesante PMI ................................................... 41 Guerra contra las mujeres: ¿Realidad o fábula?......................................43 Guía .................................................................................................................... 45 Actividad de respuestas incrustadas ...........................................................