Chosen Ciphertext Attacks on Apple Imessage
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Résumé Akshay Bakshi
� Vancouver, BC, � � 778-223-6613 Akshay Bakshi ✉ [email protected] � Profile Product manager with an engineering background and a passion for craftsmanship, experienced in shipping mobile & Mac apps at scale. � Experience Microsoft, Office for Mac and Mobile Program Manager 2 Remote in Vancouver, BC 2018 – Present - Launched Office app on iOS and revamping Word, Excel and PowerPoint for uniquely mobile scenarios. Defining product vision and managing across PM, design, data science, engineering and marketing partners located in India, China and USA. - Partnering with Apple for iPad enterprise growth (MAD up 40% YoY). - Driving core UX for Office on iOS & macOS. Working on Start, push notifications, @mentions and comments to increase collaboration (usage up 3x). - Coaching early-in-career PMs. Allyship lead for Vancouver. Program Manager Redmond, WA 2016 – 2018 - Incubated an AR+VR Office product, managing user research, design and development (NPS 70). Direct approval by Satya Nadella for productization. Received patent. - Office Accessibility lead for iOS & macOS. Lead partnership with Apple to improve VoiceOver usability. Achieved App Store feature and unblocked $10M+ business deals. - Drove the iOS 11 update for Office and marketing partnership with Apple. Program Manager Intern Redmond, WA Summer 2015 Added support for right-to-left language UI in Word, Excel & PowerPoint for iOS. Symantec, Norton for Mac Software Developer Intern Los Angeles, CA Jan – Sep 2014 Refactored remote management components and built GUI tools. � Education UCLA, B.S. in Computer Science 2012 – 2015 - President, Association for Computing Machinery. Ran committee of 12. Increased funding 4x, membership 20→200 and event attendance 6x. - Creative Director, LA Hacks - Product Manager, Daily Bruin & Bruinwalk � Skills & Life Photoshop, Obj-C, C++, Sketch. -

The Department of Justice Versus Apple Inc. -- the Great Encryption Debate Between Privacy and National Security
Catholic University Journal of Law and Technology Volume 27 Issue 2 Spring 2019 Article 3 2019 The Department of Justice Versus Apple Inc. -- The Great Encryption Debate Between Privacy and National Security Julia P. Eckart Follow this and additional works at: https://scholarship.law.edu/jlt Part of the Communications Law Commons, Constitutional Law Commons, First Amendment Commons, Intellectual Property Law Commons, Internet Law Commons, Other Law Commons, Privacy Law Commons, and the Science and Technology Law Commons Recommended Citation Julia P. Eckart, The Department of Justice Versus Apple Inc. -- The Great Encryption Debate Between Privacy and National Security, 27 Cath. U. J. L. & Tech 1 (2019). Available at: https://scholarship.law.edu/jlt/vol27/iss2/3 This Article is brought to you for free and open access by CUA Law Scholarship Repository. It has been accepted for inclusion in Catholic University Journal of Law and Technology by an authorized editor of CUA Law Scholarship Repository. For more information, please contact [email protected]. THE DEPARTMENT OF JUSTICE VERSUS APPLE INC.—THE GREAT ENCRYPTION DEBATE BETWEEN PRIVACY AND NATIONAL SECURITY Julia P. Eckart* I. THE FACTS UNDERLYING THE DOJ–APPLE DISPUTE ........................3 A. Timeline of the Parties’ Court-Filed Documents ......................................6 B. Issues Presented in the DOJ–Apple Litigation ..........................................8 II. APPLE’S iOS9.0 SECURITY GUIDE ..........................................................9 A. Some of Apple’s Encryption and Non-Encryption Security Features ........9 B. Other Hardware and Software System Security Features .......................11 III. DOES THIS CASE PERTAIN TO A SINGLE IPHONE OR ALL IPHONES? .......................................................................................................12 A. DOJ’s Position—It is About One, Single iPhone ....................................12 B. -

John Solak V. Apple
Case 5:18-cv-00123 Document 1 Filed 01/05/18 Page 1 of 22 1 Shana E. Scarlett (SBN 217895) HAGENS BERMAN SOBOL SHAPIRO LLP 2 715 Hearst Avenue, Suite 202 Berkeley, CA 94710 3 Telephone: (510) 725-3000 Facsimile: (510) 725-3001 4 [email protected] 5 Steve W. Berman (pro hac vice forthcoming) Robert F. Lopez (pro hac vice forthcoming) 6 HAGENS BERMAN SOBOL SHAPIRO LLP 1918 Eighth Avenue, Suite 3300 7 Seattle, WA 98101 Telephone: (206) 623-7292 8 Facsimile: (206) 623-0594 [email protected] 9 [email protected] 10 Attorneys for Plaintiff and the Proposed Class 11 UNITED STATES DISTRICT COURT 12 NORTHERN DISTRICT OF CALIFORNIA 13 SAN JOSE DIVISION 14 JOHN SOLAK, a New York resident, on behalf of No. 5:18-cv-123 himself and all others similarly situated, 15 CLASS ACTION COMPLAINT FOR Plaintiff, TRESPASS TO CHATTELS, VIOLATION 16 OF CALIFORNIA’S UNFAIR v. COMPETITION LAW, FRAUDULENT 17 MISREPRESENTATION, AND QUANTUM MERUIT TO RECOVER 18 APPLE INC., a California corporation, SUMS BY WHICH DEFENDANT HAS BEEN UNJUSTLY ENRICHED 19 Defendant. DEMAND FOR JURY TRIAL 20 21 22 23 24 25 26 27 28 000700-11 555555 V1 Case 5:18-cv-00123 Document 1 Filed 01/05/18 Page 2 of 22 TABLE OF CONTENTS 1 Page 2 I. INTRODUCTION ................................................................................................................... 1 3 II. JURISDICTION ...................................................................................................................... 2 4 III. VENUE ................................................................................................................................... -

14.06.15NYT Tim Cook-Making Apple His
Tim Cook, Making Apple His Own By Matt Richtel and Brian X. Chen NYT 6/15/14 http://www.nytimes.com/2014/06/15/technology/tim-cook-making-apple-his- own.html?module=Search&mabReward=relbias%3As%2C%5B%22RI%3A6%22% 2C%22RI%3A18%22%5D Tim Cook, Apple’s chief executiVe, was an adolescent boy in a small Alabama town in the early 1970s when he saw something he couldn’t forget. Bicycling home on a new 10-speed, he passed a large cross in flames in front of a house — one that he knew belonged to a black family. Around the cross were Klansmen, dressed in white cloaks and hoods, chanting racial slurs. Mr. Cook heard glass break, maybe someone throwing something through a window. He yelled, “Stop!” One of the men lifted his conical hood, and Mr. Cook recognized a deacon from a local church (not Mr. Cook’s). Startled, he pedaled away. “This image was permanently imprinted in my brain, and it would change my life foreVer,” Mr. Cook said of the burning cross, in a speech he gaVe last December. In the speech, he said his new awareness made him feel that no matter what you do in life, human rights and dignity are Values that need to be acted upon. And then came the segue: His company, Apple, is one that belieVed deeply in “adVancing humanity.” Mr. Cook, who is 53, took oVer leadership of Apple nearly three years ago, after the death of SteVe Jobs, the company’s revered founder. Like Walt Disney and Henry ford, Mr. -

Cassie Wardlow CST 300L October 16, 2012 Apple of My Eye a Degree
Wardlow 1 Cassie Wardlow CST 300L October 16, 2012 Apple of My Eye A degree in technology is the best thing that a college student could major in right now. Technology is in its peak and can only grow more in the future. The fields of graphic and web design seem to have many job openings. Companies are always needing new websites or logos to keep up with current trends and to make sure they don’t fall too far behind. Some major corporations that do this best are Apple, Google, Facebook, and YouTube. These corporations are on top of what the best technology is and how they can implement it best. Websites and applications are constantly being updated to make sure they stay on top, as well as products to stay in competition with other big names. More importantly, how is Apple going to keep up? An analysis will be provided to see how Apple plans to stay on top and how they got there. Lastly, jobs for the future will come into play and how acquiring one will happen. Many people know about Apple because the company has boomed in the last decade. Not everyone knows how they got there and how they plan to stay on top. Apple was founded by two college drop outs, Steve Jobs and Steve Wozniak, in 1976. The company started out as just building computers and has transformed into a technology Mecca. Apple computers were first created to go up against the powerful PC world of Microsoft and HP. It was hard for them to compete because the PC world was already so strong and well built. -

Objection to Closing Argument and Motion For
Case 6:12-cv-00855-RWS Document 424 Filed 02/03/16 Page 1 of 8 PageID #: 31353 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS TYLER DIVISION VIRNETX INC. AND SCIENCE APPLICATIONS INTERNATIONAL CORPORATION, Civil Action No. 6:12-cv-855 LEAD CONSOLIDATED CASE Plaintiffs, v. APPLE INC.., JURY TRIAL DEMANDED Defendant. DEFENDANT APPLE’S WRITTEN OBJECTION TO CLOSING ARGUMENT BY VIRNETX AND MOTION FOR MISTRIAL During closing argument, counsel for VirnetX made arguments outside the evidence, blatantly misrepresenting the testimony of Apple witnesses, which served to confuse, mislead, and inflame the jury, to render a verdict not based on the record. Apple objected to such statements immediately following closing and now further provides its written objection to those statements. Apple further moves for a mistrial, because the improper argument outside the record has deprived Apple of the opportunity for a fair trial. It is well-settled that a “trial judge may order a new trial if he suspects that the jury verdict reflects confusion.” Nissho–Iwai Co., Ltd. v. Occidental Crude Sales, 729 F.2d 1530, 1538 (5th Cir.1984). The Fifth Circuit considers three factors—simplicity of the issues, the extent to which the evidence is in dispute, and the absence of any pernicious or undesirable occurrence at trial—in determining whether a mistrial or new trial is warranted. See Shows v. Jamison Bedding, Inc., 671 F.2d 927, 930-931 (5th Cir. 1982). Grounds for a mistrial include improper attorney argument. “The role of the attorney in closing argument is ‘to assist the jury 1 Case 6:12-cv-00855-RWS Document 424 Filed 02/03/16 Page 2 of 8 PageID #: 31354 in analyzing, evaluating and applying the evidence. -

No Mac Is an Island with Macos Catalina June ’19 by ADAM ENGST Volume 35 Issue 6 Let’S Face It
A Publication of the Silicon Mountain Macintosh User Group Colorado Springs Metro Area No Mac Is an Island with macOS Catalina June ’19 by ADAM ENGST Volume 35 Issue 6 Let’s face it. Macs users are adrift in a sea of iOS devices. Contents Waves of iPhones and iPads break around us, and even an occasional iPod touch floats by. So it shouldn’t be at all SIG News 2 surprising that the forthcoming macOS 10.15 Catalina Club News 3 focuses on changes that bring the Mac and iOS closer than Door Prize Winners 7 ever before. Joy of Tech 8 That’s not to say that Apple is trying to replace the Mac with iOS or remove those unique capabilities of the Mac that iOS, watchOS & tvOS 9 make it special. The Mac and macOS remain first-class, vibrant members of Apple’s hardware and Macs & macOS 17 software platforms. But what we’re not going to see, at least from Apple, are new technologies that set the Mac further apart from its iOS brethren. When it comes to operating systems, it’s safe to say that it’s one Gary Rosenzweig’s Tips 20 for all, and all for Apple. In today’s Worldwide Developer Conference keynote, Apple’s Craig Federighi whipped through the major changes, most of which revolved around individual apps. Unsurprisingly, those changes largely reflect or are matched by similar changes in the iOS versions, but there were Mac-specific enhancements as well. Ding, Dong, iTunes Is Dead Federighi had a fabulous riff where he discussed all the features Apple was planning to add to iTunes—Calendar! Mail! A dock!—before acknowledging that iTunes is dead, Jim. -
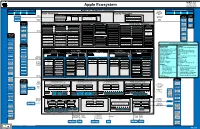
Apple Ecosystem Y
Apple Inc. One Apple Park Way Cupertino, CA 95014 Apple Ecosystem Phone: (408) 996-1010 www.apple.com Outside Relationships Apple Inc. (California Corporation) Securities Outside Relationships Regulation and Regulators Capital Suppliers Customers NASDAQ Listing Customers Suppliers Capital Regulators Debt Structure Equity Structure Rules Bond Debt ( $107B @ 9/28/19) Credit Ratings: Aa1 (Moody’s), AA+ (S&P) Equity Securities Public Debt Financing Common Stock Significant Regulators Common Stock (12.6 Billion Authorized; Holders Senior Floating Senior Fixed Rate Notes ($97.5B), Repurchases Shareholders 4.443 Million Shares Outstanding) US Securities Commercial Rate Notes bearing interest at 0.875% to 3.6% Vanguard Commercial Commercial Paper (9- Equity and Paper ($4.25B) and maturing 2022 to 2042 Group Banks months or less) ($6 billion) $175 Billion Share Repurchase Program Capital Exchange (7.36%) Commission Professional Berkshire Services Governance Human Resources Sales and Marketing Finance and Accounting Corporate Matters Hathaway The NASDAQ Board of Directors Research & (5.6%) Hiring / Training Legal Stock Market Ernst & Young Advertising Budget Support Development Arthur D. Levinson (C) Albert Gore Jr. (C, N) Susan L. Wagner (N, A) Real Estate IP Management BlackRock (Auditors) New Technologies Pension Plans Retail Accounts Internal Audit Fund TBWA/Media Tim Cook Andrea Jung (C, N) Ronald D. Sugar (A) Transactions Subsidiary Management Existing Product Advisors Professional Compensation E Commerce Accounting Arts Lab Enhancements -

Case 4:20-Cv-05640-YGR Document 407 Filed 04/08/21 Page 1 of 365
Case 4:20-cv-05640-YGR Document 407 Filed 04/08/21 Page 1 of 365 REDACTED VERSION OF DOCUMENT SOUGHT TO BE SEALED 1 CHRISTINE A. VARNEY (pro hac vice) 2 [email protected] KATHERINE B. FORREST (pro hac vice) 3 [email protected] GARY A. BORNSTEIN (pro hac vice) 4 [email protected] YONATAN EVEN (pro hac vice) 5 [email protected] LAUREN A. MOSKOWITZ (pro hac vice) 6 [email protected] JUSTIN C. CLARKE (pro hac vice) 7 [email protected] M. BRENT BYARS (pro hac vice) 8 [email protected] CRAVATH, SWAINE & MOORE LLP 9 825 Eighth Avenue New York, New York 10019 10 Telephone: (212) 474-1000 Facsimile: (212) 474-3700 11 PAUL J. RIEHLE (SBN 115199) 12 [email protected] FAEGRE DRINKER BIDDLE & REATH LLP 13 Four Embarcadero Center 27th Floor San Francisco, CA 94111 14 Telephone: (415) 591-7500 Facsimile: (415) 591-7510 15 Attorneys for Plaintiff and Counter-defendant 16 Epic Games, Inc. 17 UNITED STATES DISTRICT COURT 18 NORTHERN DISTRICT OF CALIFORNIA 19 OAKLAND DIVISION 20 21 EPIC GAMES, INC., Case No. 4:20-cv-05640-YGR-TSH 22 Plaintiff, Counter-defendant, FINDINGS OF FACT AND CONCLUSIONS OF LAW 23 PROPOSED BY EPIC GAMES, INC. v. 24 APPLE INC., 25 The Honorable Yvonne Gonzalez Rogers Defendant, Counterclaimant. 26 Trial: May 3, 2021 27 28 FINDINGS OF FACT AND CONCLUSIONS OF LAW PROPOSED BY EPIC GAMES, INC. Case No. 4:20-cv-05640-YGR-TSH Case 4:20-cv-05640-YGR Document 407 Filed 04/08/21 Page 2 of 365 1 Epic Games, Inc. -

New OS Versions Coming Later This Year
The offcial journal of the Wellington Macintosh Society Inc Volume 38.06 – June 2021 Come to one of New OS versions coming later this year our meetings Apple has announced the next Wellington/Online versions of macOS, iPadOS and iOS, which we can expect to be available Monday 28 June between September and November. 7:00 pm for 7:20 pm Subject: WWDC This month’s Wellington meeting Announcements will be discussing the new features, such as the examples shown here: Kapiti Group Widgets on the iPad, and Live Text. Monday 5 July 7:00 pm for 7:15 pm Subject: Device maintenance iPad Group TBA Help Desk** TBA **Please register by emailing [email protected] Where to find us Unless otherwise indicated, main meetings are normally as follows. Wellington: last Monday of the month (except December) at Brian Davis Room, Cathedral of St Paul, corner Hill St and Molesworth St, Wellington. Kapiti: first Monday of the month (except January) at Kapiti Uniting Parish, 10 Weka Road, Raumati. Help desks and other special interest meetings vary. The President Writes p2 Apple Extends Privacy Protections to INSIDE David’s Tech Guide p3 Traffic Leaving Its Walled Garden p7 Ben Thompson Examines US Apple Podcasts Subscriptions p9 Big Tech Legislation p6 Committee Contact Details p10 CAPITAL APPLE – JUNE 2021 PAGE 1 The president writes ... way of its web pages http://www.welmac.org.nz, however this is time consuming to maintain and as a consequence has not been done on a regular basis. We have set up a Facebook page https:// Graeme Moffatt www.facebook.com/WelMacNZ that does not need [email protected] the same degree of maintenance as users can contribute and we also have a Youtube Channel where we have been uploading all of our recent Hi folks meetings https://www.youtube.com/channel/ UCmJBMCRuX6iyV8smOu2iApw. -
Apple Has Been Sued by Blix, Owner of Bluemail, for Patent Infringement and Illegal Monopolization
October 05, 2019 Apple has been sued by Blix, owner of BlueMail, for Patent Infringement and Illegal Monopolization Apple has been sued by the owner of BlueMail for patent infringement relating to Apple's new 'Sign In with Apple' feature for iOS that was introduced at their World Wide Developer Conference. CBS news covered this specific feature in an interview with Tim Cook. Not only did Apple steal BlueMail’s pioneering anonymous messaging capabilities—days later, Apple removed BlueMail from the MacOS App Store, to prevent Mr. Volach’s software from readily reaching consumers and competing with Apple’s own products. While Apple takes the position that they're not a monopoly, yet their actions speak louder than words. When they remove an app competing with an Apple feature on the App Store, then that's monopolistic move. In June Patently Apple posted a report titled "The Stars are lining up against Apple as they now may be in the U.S. Government's Antitrust Crosshairs over the App Store." In the lawsuit Mr. Volach points out that Apple stealing ideas and blocking competitors on the Apple Store is common and pointed to a Washington Post report titled "titled "How Apple uses its App Store to Copy the Best Ideas," to show this is a trend of Apple's. This kind of lawsuit is simply more ammunition for a possible antitrust investigation by the government. The introduction of the lawsuit is fairly long, so we'll present only some of the key passages below: "In August 2018, Mr. Volach added innovative anonymous messaging features to BlueMail, adding a “Share Email” feature to facilitate private and easy-to-manage communications options. -

Oral History of Kenneth Kocienda and Richard Williamson, Part 2
Oral History of Kenneth Kocienda and Richard Williamson, part 2 Interviewed by: Hansen Hsu Marc Weber Recorded November 13, 2017 Mountain View, CA CHM Reference number: X8367.2018 © 2017 Computer History Museum Oral History of Kenneth Kocienda and Richard Williamson, part 2 Hsu: All right, it is November 13th. I am Hansen Hsu with Marc Weber. And we are here with Ken Kocienda and Richard Williamson, again, for part two. So, let’s get back to where we were and start where we left off. So, we were talking about sort of working on iPhone 1.0. And one thing that I didn’t get to ask is what was sort of the experience like of being on that team and working in secret and the long hours and that general sort of the feeling or the life of working on that project. Williamson: Do you want to go first? Kocienda: Sure, I’ll go first. It was intense. There was a lot of pressure. It was fun because we had something that, from the very beginning, seemed like it could really be big, important for the company. I don’t know [that I] quite thought that it would be important for the world, but important for the world of technology, I think. Williamson: And important for humanity. You don’t have to be modest. Kocienda: Yeah, it is important for humanity. Well, I think we hoped that it might be. And the people were just terrific. It was very inspiring all the time to be surrounded by people who were so smart and so good at making the software that we were trying to make.