Global Strategy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Future of Business Using Enterprise Server
Market Review Market Review Paper by Bloor Author David Norfolk Publish date June 2021 The Future of Business …using Enterprise Server 3.0 Services A company has to stay“ in business while modernising its systems and any modernisation must have a clearly documented business case and properly managed risk. What this means is that migrating a working system to a new platform may not be a good use of resources, especially as alternative modernisation options (such as the provision of cloud APIs or Application Programming Interfaces) are available. ” Executive summary he Future of Business will Well, the nub of the business issue we be largely built on the past, spotlight here is that migration to Cloud T for existing companies. is often recommended simplistically as Modernisation of what you have already, a platform for future business, almost as presumably “fit for current purpose” (or you a fashion option, with implied promises wouldn’t be in business) avoids waste and of ultimate agility, elastic capabilities mitigates certain classes of risk (although, without limits and low cost; but the if not done properly, it can add new risks). actuality is often different – and never Modernisation, of course, implies fit for quite being able to complete a migration evolution and change – once modernised, off Enterprise Server 3.0, because the you will be making further changes to business realities won’t let you, is accommodate new business. probably the most expensive scenario Modernisation of what For big enterprises, the world still runs of all. Cloud provides a wide choice of you have already,“ on very large, very resilient, servers – often platforms, some with innovative and presumably “fit for current referred to as “mainframes”, although attractive characteristics, but three truths Bloor prefers the term Enterprise Server remain important: purpose” (or you wouldn’t be in business) avoids 3.0. -

Popular Employer Names Number of Data Profiles Blackrock, Inc. 43
S.No Popular Employer Names Number of Data Profiles 1. Blackrock, Inc. 43 2. BMC Software, Inc. 55 3. BNP Paribas Inc. 113 4. BRISTLECONE India Ltd 57 5. British Telecom 131 6. Broadcom Corporation 59 7. Broadridge Financial Solutions, Inc. 44 8. Bureau Veritas 47 9. CA Technologies 65 10. CA, Inc. 39 11. Cairn India 45 12. Calsoft Pvt Ltd 44 13. Capgemini 1,309 14. Capgemini Consulting 578 15. Capita india 82 16. Capital Iq, Inc. 41 17. Caterpillar, Inc. 75 18. CBRE Group 60 19. CenturyLink 47 20. Cerner Corporation 65 21. CGI Group Inc. 300 22. Cipla Medpro Manufacturing 43 23. Cisco Systems (India) Private Limited 57 24. Cisco Systems Inc 396 25. Citibank 235 26. Citigroup, Inc. 53 27. CitiusTech 59 28. Citrix Systems Inc 40 29. CMC Group 102 30. Cognizant 1,374 31. Cognizant Technology Solutions Corp 1,715 32. Collabera Inc. 74 33. Computer Sciences Corporation (CSC) 653 34. Concentrix Corporation 159 35. Convergys Corporation 113 36. Credit Suisse 90 37. Crisil 117 38. CTS Corporation 109 39. Cummins India Ltd 70 40. Cvent, Inc. 46 41. Cybage 201 42. Daimler India Commercial Vehicles Pvt Ltd 61 43. Dell, Inc. 516 44. Deloitte 414 45. Deloitte & Touche LLP 107 46. Deloitte Consulting LLP 282 47. Deloitte Support Services India Private Ltd 94 48. Deloitte Touche Tohmatsu (DTT) 79 49. Deutsche Bank 235 50. Dimension Data 63 51. Directi 44 52. Dr Reddy's Laboratories Ltd 85 53. Dun & Bradstreet Corp 50 54. E.I. Du Pont De Nemours & Co (DuPont) 47 55. -

Sponsorship (Opportunities for Participation)
Sponsorship (Opportunities for partiCipation) Connect with Asia’s largest Agile and Lean Software Conference delegates. Naresh Jain, Chair and Sponsor liaison [email protected] Presented by http://2014.agileindia.org 1/30/14 ©2014, Agile Software Community of India. 1 WelCome to Agile India 2014 Following the grand success of Agile India 2013 and Agile India 2012 Conferences, the Agile Software Community of India (ASCI) is planning a muCh bigger event, with more than 100 Sessions over 4 days. Similar to last year, we plan to bring together thought leaders from all over the globe to India. The Indian software development Community is a hotbed for Agile and Lean movement. Number of organizations embraCing Agile is growing exponentially over the last 6 years. As there organizations are implementing Agile, they are faCed with many Questions and Challenges. This conference creates an exceptional opportunity for developers, testers, managers, exeCutives, and those who Care about the software industry to Come together to have the Conversations neCessary to push the movement forward. Join us! ASCI expeCts to host up to 1500 passionate attendees in Bengaluru, India, on February 26 – MarCh 1, 2014. SpeCial events are planned to showCase this grand, international ConferenCe on Agile Software Development. Your presenCe with us will help Create an international event. I invite you to partiCipate and tell your story at this international gathering. This is an opportunity to stand out on an international stage. Naresh Jain Founder & Conference Chair Agile Software Community of India http://agileindia.org http://2014.agileindia.org 1/30/14 ©2014, Agile Software Community of India. -

NACD Public Company Full Board Members
NACD Public Company Full Board Members: Rank | Company Rank | Company Rank | Company Rank | Company A.O. Smith Corp. Analog Devices Bridge Housing Corporation Clearwire Corp. AAA Club Partners Ansys, Inc. Briggs & Stratton Corp. Cliffs Natural Resources Inc. AARP Foundation Apogee Enterprises, Inc. Brightpoint, Inc. Cloud Peak Energy Inc. Aastrom Biosciences, Inc. Apollo Group, Inc. Bristow Group Inc. CME Group Acadia Realty Trust Applied Industrial Technologies, Broadwind Energy CoBiz, Inc. ACI Worldwide, Inc. Inc. Brookdale Senior Living Inc. Coherent, Inc. Acme Packet, Inc. Approach Resources, Inc. Bryn Mawr Bank Corporation Coinstar, Inc. Active Power, Inc. ArcelorMittal Buckeye Partners L.P. Colgate-Palmolive Co. ADA-ES, Inc. Arch Coal, Inc. Buffalo Wild Wings, Inc. Collective Brands, Inc. Adobe Systems, Inc. Archer Daniels Midland Co. Bunge Limited Commercial Metals Co. Advance Auto Parts ARIAD Pharmaceuticals, Inc. CA Holding Community Health Systems Advanced Energy Industries, Inc. Arkansas Blue Cross Blue Shield CACI International, Inc. Compass Minerals Aerosonic Corp. Arlington Asset Investment Corp. Cal Dive International, Inc. Comverse Technology, Inc. Aetna, Inc. Arthur J. Gallagher & Co. Calamos Asset Management, Inc. Conmed Corp. AFC Enterprises, Inc. Asbury Automobile Cameco Corp. Connecticut Water Service, Inc. AG Mortgage Investment Trust Inc. Aspen Technology, Inc. Cameron ConocoPhillips Agilent Technologies Associated Banc-Corp.5 Campbell Soup Co. CONSOL Energy Inc. Air Methods Corp. Assurant, Inc. Capella Education Co. Consolidated Edison Co. Alacer Gold Corp. Assured Guaranty Ltd. Capital One Financial Corp. Consolidated Graphics, Inc. Alaska Air Group, Inc. ATMI Capstead Mortgage Corp. Consolidated Water Co., Ltd. Alaska Communication Systems Atwood Oceanics, Inc. Cardtronics, Inc. Continental Resources, Inc. Group, Inc. Auxilium Pharmaceuticals Inc. -

Greater Austin Software/IT Companies
Greater Austin Software/IT Companies www.austinchamber.com LEANDER HUTTO ± 79 Brushy Creek 1431 CEDAR PARK Williamson ROUND ROCK County 620 National Oilwell Varco Emerson Dell Technologies Blizzard Automation Entertainment Solutions HPE 183 Informatica 45 Q2 Software Electronic Arts EX2 Solutions PayPal PFLUGERVILLE eBay Polycom Hoovers (D&B) Travis Future Apple Campus County Apple International Game Domain Area Employers: Nokia Technology Accruent, Amazon, Blackbaud, Indeed, Cisco Systems Visa Magento (Adobe), Trend Micro, & Vrbo. Advisory Board Pearson PlanView (Optum) Conduent 1 620 Solutions Capgemini Stonelake Area Employers: General Motors Bazaarvoice, eMDs, Forecepoint, Tata Macmillan Learning, Microsoft, NI Diebold Nixdorf Wipro & SparkCognition. Lake Travis Kasasa IBM Sailpoint BMC Software Charles Schwab Dell Parmer BigCommerce Technologies Cognizant Campus Build A Sign All Web Leads Insight AT&T Labs Honor Thales Volusion CoreLogic rateGenius 2222 360 Interactions Indeed 183 Rackspace MANOR HotSchedules GateHouse Media (Fourth) 1 Home Depot Tech Center DISCO 130 Spiceworks VMware HostGator 290 35 360 Auctane 2244 Everi Downtown Employers: Walter E. A Cloud Guru, Accenture, Atlassian, Box, Cision , Long Lake BEE Epicor WEST LAKE Cloudflare, CrowdStrike, Dropbox, DXC Technology, CAVE Barton Creek Software Facebook, Fjord Austin, Hypergiant, Khoros, Netspend, HILLS PIMCO, ProCore Technologies, Publicis Sapient, Rapid7, RetailMeNot, RigUp, & Silicon Laboratories. Consero Global Well Sky Cirrus Logic NXP 969 Intel Corp. Under Armour Semiconductors Google Favor LifeSize H-E-B Innovation 71 AMD Enverus uShip SolarWinds Broadcom Oracle Corp. NXP Semiconductors Colorado River 290 SUNSET VALLEY U.S. V.A. Tech Center Cypress Semiconductor SHI Arrive Logistics 1826 71 o Major Employers Realtor.com 35 Software/IT 1 AUSTIN-BERGSTROM INTL AIRPORT City Boundaries 45 Austin City Limit 183 Austin ETJ 0 1.5 3 6 Regional Cities Miles Software/IT Companies Spring 2021 Company Employees Company Employees Accenture 3,500 HotSchedules (Fourth) 233 Accruent 370 IBM Corp. -

15896 Navigating Turbulent Waters V1:Layout 1.Qxd
15896_Navigating Turbulent Waters_v1:Layout 1 14/06/2010 16:15 Page 1 THE TOP 100 EUROPEAN SOFTWARE INDEX NAVIGATING TURBULENT WATERS Software players continue to ride the waves 15896_Navigating Turbulent Waters_v1:Layout 1 14/06/2010 16:15 Page 2 DESPITE THE ECONOMIC STORM, EUROPEAN SOFTWARE CUTS A DASH THROUGH CHOPPY WATERS The European Software The sector has also performed resiliently headquarters of a significant number of through the recession, with most companies the US owned players. market is larger and more maintaining growth – unlike the battered broader TMT sectors, especially Media, or the At a high level the sector is highly profitable than you might adjacent IT hardware and services sectors. concentrated, with the top 10 players think – the Top 100 accounting for 58% of the revenues of the Our European Top 100 list is dominated by Top 100. The largest companies are familiar companies account for US owned companies – 44 of them names, with Microsoft, IBM, Oracle and SAP accounting for €34bn in sales, almost two dominant from a revenue perspective. over €52bn of revenue thirds of the total. Outside these, there are However, this macro picture masks a and €14bn in operating also a number of large European owned strong set of robust “beyond the top 10” players generating significant revenues – European headquartered companies, profit – an industry Germany has the second most valuable representing over €22bn of revenues. set of Software companies in the Top 100 average of over 25% with 11 German companies accounting for Despite the significant global economic margin approximiately €7bn annual revenue. UK slowdown, the Top 100 saw only a slight and France come next, housing the year-on-year revenue decline of c.0.6%, headquarters of companies representing while overall EBITDA margins actually saw a approximately €3bn of European software slight increase of 1%pt within these revenue each. -

Annual Investment Report 2015-2016
South Carolina Retirement System Investment Commission 2015-2016 Annual Investment Report Photos courtesy of the Governor’s Office and the SC National Guard. South Carolina Retirement System Investment Commission Annual Investment Report Fiscal Year Ended June 30, 2016 Capitol Center 1201 Main Street, Suite 1510 Columbia, SC 29201 Edward Giobbe, MBA Chair For the period July 1, 2014 - June 30, 2016 Table of Contents Chair Report .....................................................................................................1 Consultant’s Letter ............................................................................................3 Overview ...........................................................................................................5 Commission ......................................................................................................6 Policy Allocation ...............................................................................................9 Manager Returns (Net of Fees) .......................................................................10 Securities Lending ..........................................................................................14 Expenses ..........................................................................................................15 Risk ..................................................................................................................17 Appendix Appendix A: Summary Schedule of Assets and Derivatives .....................19 Appendix B: Cash & -

August 2014 Software Business Services Internet & Digital Media
The Lighthouse August 2014 Software Business Services Internet & Digital Media A Pharus Advisors, LLC Publication | www.pharus.com August 2014 Software & Business Services Internet & Digital Media Table of Contents 1. Capital Market Trends 3 2. Public Market Valuations 4 3. Public Market Universe 13 4. M&A Transactions 15 5. Recent Transactions 23 6. Pharus Overview 24 If you would like to be included on (or removed from) the distribution list for the Software & Services version of The Lighthouse, please contact Nathan Bullock at: [email protected]. The information contained herein is obtained from sources we believe to be reliable but its accuracy and completeness, and that of the opinions based thereon, is not guaranteed. Pharus Advisors, or one or more of its partners, may have an interest in any of the securities or companies discussed herein. All rights reserved by Pharus Advisors. LLC. 2014 Copyright Pharus Advisors, LLC. Executive Contacts Telephone Email Michael E. Goodman, Co-Founder & Sr. Managing Director 212-904-0102 [email protected] Kenneth M. Harrell, Co- Founder & Sr. Managing Director 212-904-0101 [email protected] Pharus Advisors, LLC | www.pharus.com 2 August 2014 Software & Business Services Internet & Digital Media 1. Capital Market Trends Relative Performance of Major Stock Indices through August 31, 2014 (Base = 100, 7/31/2013) 140 130 120 110 100 90 Dow Jones Industrial Average (^DJI) - Index Value NASDAQ Composite Index (^COMP) - Index Value S&P 500 Index (^SPX) - Index Value Russell 2000 Index (^RUT) - Index Value As of Change % Index 31-Aug-14 1 Year 3 Months 1 Month Dow Jones 17,098.45 15.4% 2.3% 3.2% Nasdaq 4,580.27 27.6% 8.0% 4.8% S&P 500 2,003.37 22.7% 4.1% 3.8% Russell 2000 1,174.35 16.2% 3.5% 4.8% Pharus Advisors, LLC | www.pharus.com 3 August 2014 Software & Business Services Internet & Digital Media 2. -

Participating Addendum Contract #0000000000000000000028963
PARTICIPATING ADDENDUM CONTRACT #0000000000000000000028963 NASPO ValuePoint Software Value Added Reseller (SVAR) Administrated by the State of Arizona (hereinafter “Lead State”) MASTER AGREEMENT SHI International Corporation Master Agreement No: ADSPO16-130651 (hereinafter “Contractor”) And The State of Indiana acting by and through the Indiana State Police (“ISP”) (hereinafter “Participating State/Entity”) 1. Scope: This addendum covers the Software Value Added Reseller contract led by the State of Arizona for use by state agencies and other entities located in the Participating State authorized by that state’s statutes to utilize State contracts with the prior approval of the state’s chief procurement official. 2. Participation: Use of specific NASPO ValuePoint cooperative contracts by agencies, political subdivisions and other entities (including cooperatives) authorized by an individual state’s statutes to use State contracts are subject to the prior approval of the respective State Chief Procurement Official. Issues of interpretation and eligibility for participation are solely within the authority of the State Chief Procurement Official. 3. Participating State Modifications or Additions to Master Agreement: (These modifications or additions apply only to actions and relationships within the Participating Entity.) Participating State/Entity must check one of the boxes below. [__] No changes to the terms and conditions of the Master Agreement are required. [ X ] The following changes are modifying or supplementing the Master Agreement terms and conditions. Exhibit A, hereby attached and incorporated by reference, is the Supplement covering compliance with State laws. The Supplement is incorporated into and made a part of the Master Agreement Number ADSPO16-130651 (Exhibit B) and applies to all transactions under this Participating Addendum. -

Bijlage Overzicht Corporate Governance 4E Kwartaal
! ! ! Overzicht Corporate Governance 4e kwartaal 2014 In deze lijst wordt aangegeven van welke landen we staatsobligaties bezitten die direct op naam staan van het Pensioenfonds TNO. Vervolgens worden daarnaast de beleggingsfondsen genoemd waar we op 31-12-2014 in beleggen. Tot slot staat in de PDF een lange lijst van instellingen en bedrijven waarvan de obligaties direct op naam van het Pensioenfonds TNO staan. (Quasi) staatsobligaties Fixed Income Beleggingsfondsen direct op naam van Pensioenfonds TNO (13/12/2014) Duitsland BlackRock Emerging Market debt (hard Frankrijk currency) Nederland Neuberger Berman Emerging Market debt Mexico (local currency) Slovenië Robeco European High Yield fund Roemenië Ijsland Aandelenbeleggingsfondsen (13/12/2014) Italië Vanguard Inst. Index Fund Chili Vanguard SRI European Stock Index Fund Litouwen Vanguard Emerging Markets Equity Fund Spanje BlackRock Japan Equity fund exclusief controversial weapons BlackRock Pacific ex Japan Equity fund exclusief controversial weapons Obligaties direct op naam van AECOM TECHNOLOGY Pensioenfonds TNO AES Corp/VA AAF Holdings LLC Affinion Group Inc ABEST_9 Aguila 3 SA ABN AMRO BANK NV AIA GROUP LTD Access Midstream Partners LP / ACMP Fin AIB MORTGAGE BANK Accuride Corp Air Canada ACE Cash Express Inc AK Steel Corp ACHMEA HYPOTHEEKBANK NV Alcatel-Lucent USA Inc ACOSTA Alere Inc ACTIVISION BLIZZARD Aleris International Inc ADECCO INTERNATIONAL FINANCIAL SER Algeco Scotsman Global Finance Plc ADT CORP ALLEGIANT TRAVEL CO Advanced Micro Devices Inc Allen Systems Group Inc -
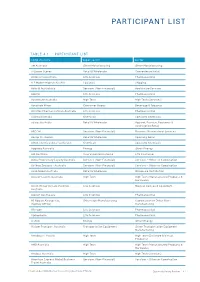
Participant List
PARTICIPANT LIST TABLE 4.1 PARTICIPANT LIST Company name Super sector Sector 3M Australia Other Manufacturing Other Manufacturing 7-Eleven Stores Retail & Wholesale Convenience Retail A Menarini Australia Life Sciences Pharmaceutical A.P.Moller-Maersk AS (AU) Logistics Shipping Abbott Australasia Services (Non-Financial) Healthcare Services AbbVie Life Sciences Pharmaceutical Accenture Australia High Tech High Tech (Services) Accolade Wines Consumer Goods Beverage & Tobacco Actelion Pharmaceuticals Australia Life Sciences Pharmaceutical Adama Australia Chemicals Specialty Chemicals adidas Australia Retail & Wholesale Apparel, Fashion, Footwear & Accessories Retail AECOM Services (Non-Financial) Business/Professional Services Aesop Cosmetics Retail & Wholesale Specialty Retail Afton Chemical Asia Pacific LLC Chemicals Specialty Chemicals Aggreko Australia Energy Other Energy AIA Australia Insurance/Reinsurance Life Insurance Aimia Proprietary Loyalty Australia Services (Non-Financial) Services - Other or Combination Air New Zealand - Australia Services (Non-Financial) Services - Other or Combination Akzo Nobel Australia Retail & Wholesale Wholesale Distribution Alcatel-Lucent Australia High Tech High Tech (Manufactured Products & Hardware) Alcon (Novartis) Laboratories Life Sciences Medical Devices & Equipment Australia Alexion Australasia Life Sciences Pharmaceutical All Nippon Airways Co., Other Non-Manufacturing Combination or Other Non- (Sydney Office) Manufacturing Allergan Life Sciences Pharmaceutical Alphapharm Life Sciences Pharmaceutical -

Annual Report for the Financial Year Ended December 31, 2014
ANNUAL REPORT FOR THE FINANCIAL YEAR ENDED DECEMBER 31, 2014 NXP SEMICONDUCTORS N.V. Forward-looking statements cautioned not to place undue reliance on these forward- This document includes forward-looking statements looking statements, which speak to results only as of the which include statements regarding our business date the statements were made; and, except for any strategy, financial condition, results of operations, and ongoing obligation to disclose material information as market data, as well as any other statements which are required by the United States federal securities laws, we not historical facts. By their nature, forward-looking do not have any intention or obligation to publicly update statements are subject to numerous factors, risks and or revise any forward-looking statements after we uncertainties that could cause actual outcomes and distribute this document, whether to reflect any future results to be materially different from those projected. events or circumstances or otherwise. For a discussion These factors, risks and uncertainties include the of potential risks and uncertainties, please refer to the following: market demand and semiconductor industry risk factors listed in our SEC filings. Copies of our filings conditions, our ability to successfully introduce new are available from our Investor Relations department or technologies and products, the demand for the goods from the SEC website, www.sec.gov. into which our products are incorporated, our ability to generate sufficient cash, raise sufficient capital or Use of fair value measurements refinance our debt at or before maturity to meet both our In presenting the NXP Group’s financial position, fair debt service and research and development and capital values are used for the measurement of various items in investment requirements, our ability to accurately accordance with the applicable accounting standards.