English Apple Inc. Software License Agreement For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Podcast Presentation
3/18/2009 Today’s Goals Podcasts: Understanding, 1. What is a podcast? Creating, and Deploying them 2. How do I get podcasts? 3. How do I play podcasts? 4. Why should I care about podcasts for Dr. Rick Jerz ediducation? 5. How do I produce my own audio podcasts? [email protected] 6. How do I deliver (deploy) my own podcasts? www.rjerz.com 1 © 2009 rjerz.com 2 © 2009 rjerz.com Demos 1) What is a Podcast? • It must be nothing, since the “podcast” is not in my dictionary. • It is something only children do. • It has something to do with fishing. • It is a radio talk show. • It a music file. • It is a TV program. • It is a lecture. 3 © 2009 rjerz.com 4 © 2009 rjerz.com Podcast Definition1 Rick’s Podcast Definition • Podcasting is a new format for distributing A method of obtaining (subscribing) audio and video content via the Internet. Actually, podcasting is just multimedia computer files (episodes), usually content enclosed into an RSS file. audio (mp3) or video (m4v), from a • RSS means Really Simple Syndication. RSS is a catalog (RSS feed, XML) on the special format based on XML. In fact, RSS Internet (website), and having them feeds are XML files containing data according to the RSS specification, and usually located automatically delivered to your on a website. computer and then to your iPod (or • XML: an HTML‐like file for handling data. other multimedia player) • HTML: Hyper Text Markup Language 1 ‐ http://www.rss‐specification.com/sitemap.htm 5 © 2009 rjerz.com 6 © 2009 rjerz.com 1 3/18/2009 2) How do I get podcasts? iTunes: An Aggregator -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

Automated Testing Clinic Follow-Up: Capybara-Webkit Vs. Poltergeist/Phantomjs | Engineering in Focus
Automated Testing Clinic follow-up: capybara-webkit vs. polter... https://behindthefandoor.wordpress.com/2014/03/02/automated-... Engineering in Focus the Fandor engineering blog Automated Testing Clinic follow-up: capybara-webkit vs. poltergeist/PhantomJS with 2 comments In my presentation at the February Automated Testing SF meetup I (Dave Schweisguth) noted some problems with Fandor’s testing setup and that we were working to fix them. Here’s an update on our progress. The root cause of several of our problems was that some of the almost 100 @javascript scenarios in our Cucumber test suite weren’t running reliably. They failed occasionally regardless of environment, they failed more on slower CPUs (e.g. MacBook Pros only a couple of years old), when they failed they sometimes hung forever, and when we killed them they left behind webkit-server processes (we were using the capybara-webkit driver) which, if not cleaned up, would poison subsequent runs. Although we’ve gotten pretty good at fixing flaky Cucumber scenarios, we’d been stumped on this little handful. We gave up, tagged them @non_ci and excluded them from our build. But they were important scenarios, so we had to run them manually before deploying. (We weren’t going to just not run them: some of those scenarios tested our subscription process, and we would be fools to deploy a build that for all we knew wouldn’t allow new users to subscribe to Fandor!) That made our release process slower and more error-prone. It occurred to me that I could patch the patch and change our deployment process to require that the @non_ci scenarios had been run (by adding a git tag when those scenarios were run and checking for it when deploying), but before I could put that in to play a new problem appeared. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -
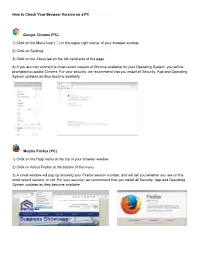
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Copyrighted Material
05_096970 ch01.qxp 4/20/07 11:27 PM Page 3 1 Introducing Cascading Style Sheets Cascading style sheets is a language intended to simplify website design and development. Put simply, CSS handles the look and feel of a web page. With CSS, you can control the color of text, the style of fonts, the spacing between paragraphs, how columns are sized and laid out, what back- ground images or colors are used, as well as a variety of other visual effects. CSS was created in language that is easy to learn and understand, but it provides powerful control over the presentation of a document. Most commonly, CSS is combined with the markup languages HTML or XHTML. These markup languages contain the actual text you see in a web page — the hyperlinks, paragraphs, headings, lists, and tables — and are the glue of a web docu- ment. They contain the web page’s data, as well as the CSS document that contains information about what the web page should look like, and JavaScript, which is another language that pro- vides dynamic and interactive functionality. HTML and XHTML are very similar languages. In fact, for the majority of documents today, they are pretty much identical, although XHTML has some strict requirements about the type of syntax used. I discuss the differences between these two languages in detail in Chapter 2, and I also pro- vide a few simple examples of what each language looks like and how CSS comes together with the language to create a web page. In this chapter, however, I discuss the following: ❑ The W3C, an organization that plans and makes recommendations for how the web should functionCOPYRIGHTED and evolve MATERIAL ❑ How Internet documents work, where they come from, and how the browser displays them ❑ An abridged history of the Internet ❑ Why CSS was a desperately needed solution ❑ The advantages of using CSS 05_096970 ch01.qxp 4/20/07 11:27 PM Page 4 Part I: The Basics The next section takes a look at the independent organization that makes recommendations about how CSS, as well as a variety of other web-specific languages, should be used and implemented. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Macos at CCSU – What’S New?
MacOS at CCSU – What’s New? MacOS is faster, more secure, and has several new features: 1. Jamf Computer Management and Self-Service Software Installations 2. Encryption and VPN for Laptops 3. Password Reset Procedures and Synchronization with NOMAD 4. Automatic Weekly Maintenance 5. Music, Video, Podcast and Safari Updates Jamf Computer Management & Self-Service Software Installations Jamf is a tool that allows the IT department to manage policies, updates and software on Mac computers. It allows us to keep the software on your computer updated to protect against security threats. Jamf also allows us to set policies to keep your account and computer safe, such as auto locking your computer after 15 minutes of inactivity. In addition, Jamf provides a Self-Service Software Installation tool that allows you to install CCSU-licensed software on your computer when needed. To access Self-Service, click on the icon in the Dock. If you do not see the icon, then open it from the Applications folder. To install an application from Self-Service, simply click on the Install button. Applications available to install include Adobe Creative Cloud, Chrome, Jabber, Webex, SPSS, Firefox, and more. MacOS Laptops If you use a MacBook Pro as your primary CCSU-issued computer, there are some added features: VPN (Virtual Private Network) The VPN connects your MacBook Drive Encryption to the campus network even when off campus. The connection to the The hard drive of your laptop is encrypted for campus network allows direct added security. Encryption uses your BlueNet access to resources such as Secure account as the credentials, so it is important to Apps (secureapps.ccsu.edu) for review the information on Page 2 to ensure the access to Banner, WebNow, encryption password stays synchronized. -

Comparing Javascript Engines
Comparing Javascript Engines Xiang Pan, Shaker Islam, Connor Schnaith Background: Drive-by Downloads 1. Visiting a malicious website 2. Executing malicious javascript 3. Spraying the heap 4. Exploiting a certain vulnerability 5. Downloading malware 6. Executing malware Background: Drive-by Downloads 1. Visiting a malicious website 2. Executing malicious javascript 3. Spraying the heap 4. Exploiting a certain vulnerability 5. Downloading malware 6. Executing malware Background: Drive-by Downloads Background: Drive-by Downloads Setup: Making the prototype null while in the prototype creates a pointer to something random in the heap. Background: Drive-by Downloads Environment: gc( ) is a function call specific to Firefox, so the attacker would want to spray the heap with an exploit specific to firefox. Background: Drive-by Downloads Obfuscation: If the browser executing the javascript it firefox,the code will proceed to the return statement. Any other browser will exit with an error due to an unrecognized call to gc( ). Background: Drive-by Downloads Download: The return will be to a random location in the heap and due to heap-spraying it will cause shell code to be executed. Background: Goal of Our Project ● The goal is to decode obfuscated scripts by triggering javascript events ● The problem is when triggering events, some errors, resulting from disparity of different engines or some other reasons, may occur and terminate the progress ● We need to find ways to eliminate the errors and Ex 1therefore generate more de-obfuscated scripts <script> function f(){ //some codes gc(); var x=unescape(‘%u4149%u1982%u90 […]’)); eval(x); } </script> Ex 2 <script type="text/javascript" src="/includes/jquery/jquery.js"></script> Project Overview - Part One ● Modify WebKit engine so that it can generate error informations. -

EMERGING TECHNOLOGIES Skype and Podcasting: Disruptive Technologies for Language Learning
Language Learning & Technology September 2005, Volume 9, Number 3 http://llt.msu.edu/vol9num3/emerging/ pp. 9-12 EMERGING TECHNOLOGIES Skype and Podcasting: Disruptive Technologies for Language Learning Robert Godwin-Jones Virginia Comonwealth University New technologies, or new uses of existing technologies, continue to provide unique opportunities for language learning. This is in particular the case for several new network options for oral language practice. Both Skype and podcasting can be considered "disruptive technologies" in that they allow for new and different ways of doing familiar tasks, and in the process, may threaten traditional industries. Skype, the "people's telephone," is a free, Internet-based alternative to commercial phone service, while podcasting, the "radio for the people," provides a "narrowcasting" version of broadcast media. Both have sparked intense interest and have large numbers of users, although it is too soon to toll the bell for telephone companies and the radio industry. Skype and podcasting have had a political aspect to their embrace by early adopters -- a way of democratizing institutions -- but as they reach the mainstream, that is likely to become less important than the low cost and convenience the technologies offer. Both technologies offer intriguing opportunities for language professionals and learners, as they provide additional channels for oral communication. Skype and Internet Telephony Skype is a software product which provides telephone service through VoIP (Voice over IP), allowing your personal computer to act like a telephone. A microphone attached to the computer is necessary and headphones are desirable (to prevent echoes of the voice of your conversation partner). It is not the only such tool, nor the first, but because it provides good quality (through highly efficient compression) and is free, it has become widely used. -

How Do I Clear My Web Browser's Cache, Cookies, and History? Notes
How do I clear my web browser's cache, cookies, and history? Notes: If you don't see instructions below for your specific version or browser, search your browser's Help menu for "clear cache". If you're unsure what browser version you're using, from the Help menu, select About [browser name]. In Internet Explorer and Firefox, if you don't see the menu bar, press Alt. When troubleshooting issues with any web site, after clearing your browser's cache and cookies, exit your browser completely before attempting to access the site again. In Windows, close all your browser windows; in Mac OS X, quit (Command-q) your browser. On this page: About cache, cookies, and history Android Chrome Firefox Internet Explorer 8 and higher Mobile Safari for iOS (iPhone, iPod touch, iPad) Opera Safari About cache, cookies, and history Each time you access a file through your web browser, the browser caches (stores) it. By doing this, the browser doesn't have to newly retrieve files (including any images) from the remote web site each time you click Back or Forward. You should periodically clear the cache to allow your browser to function more efficiently. A cookie is a file created by a web browser, at the request of a web site, that is then stored on a computer. These files typically store user-specific information such as selections in a form, shopping cart contents, or authentication data. Browsers will normally clear cookies that reach a certain age, but clearing them manually may solve problems with web sites or your browser.