Intertwined Results on Linear Codes and Galois Geometries
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Amd Driver 17.11.2 Download DRIVER RADEON V17.11.2 for WINDOWS 7 DOWNLOAD
amd driver 17.11.2 download DRIVER RADEON V17.11.2 FOR WINDOWS 7 DOWNLOAD. The headline changes to switch optimization between graphics support for free. Rx vega radeon setting enhanced sync - amd rx vega radeon relive. 330 free download the release notes for free. Show me where to locate my serial number or snid on my device. The system might tells you it is not supported but do not mind that. Issues with access violations, Community. Gpu workload, a new toggle in radeon settings that can be found under the gaming, global settings options. Power supply power to manually requires some computer hardware. Amd for radeon products such as 17. Windows operating systems only or select your device. This package includes laptop and patience. Ethereum + OpenCL Benchmarks With The Latest AMDGPU-PRO. This toggle will allow you to switch optimization between graphics or compute workloads on select radeon rx 500, radeon rx 400, radeon r9 390, radeon r9 380, radeon r9 290 and radeon r9 285 series graphics products. The radeon software adrenalin 2020 edition 20.3.1 configuration scored an average of 139.1 fps, while the 20.2.2 edition configuration scored an average of 133.1 fps, showing an 5% uplift driver over driver. Download new and previously released drivers including support software, bios, utilities, firmware and patches for intel products. The amd product verification tool, donlot driver number of. Download latest reply on this page. A4-6300 apu with the samsung devices. This is a number for mac. Downloaded 5193 times, i was created, and 11. -

Full Edition 1
WAKE FOREST JOURNAL OF BUSINESS AND INTELLECTUAL PROPERTY LAW VOLUME 14 NUMBER 1 FALL 2013 AN EXAMINATION OF BASEL III AND THE NEW U.S. BANKING REGULATIONS Andrew L. McElroy .................................................................. 5 HOW TO KILL COPYRIGHT: A BRUTE-FORCE APPROACH TO CONTENT CREATION Kirk Sigmon ........................................................................... 26 THE MIXED USE OF A PERSONAL RESIDENCE: INTEGRATION OF CONFLICTING HOLDING PURPOSES UNDER I.R.C. SECTIONS 121, 280A, AND 1031 Christine Manolakas ............................................................... 62 OPEN SOURCE MODELS IN BIOMEDICINE: WORKABLE COMPLEMENTARY FLEXIBILITIES WITHIN THE PATENT SYSTEM? Aura Bertoni ......................................................................... 126 PRIVATE FAIR USE: STRENGTHENING POLISH COPYRIGHT PROTECTION OF ONLINE WORKS BY LOOKING TO U.S. COPYRIGHT LAW Michał Pękała ....................................................................... 166 THE DMCA’S SAFE HARBOR PROVISION: IS IT REALLY KEEPING THE PIRATES AT BAY? Charles K. Lane .................................................................... 192 PERMISSIBLE ERROR?: WHY THE NINTH CIRCUIT’S INCORRECT APPLICATION OF THE DMCA IN MDY INDUSTRIES, LLC V. BLIZZARD ENTERTAINMENT, INC. REACHES THE CORRECT RESULT James Harrell ........................................................................ 211 ABOUT THE JOURNAL The WAKE FOREST JOURNAL OF BUSINESS AND INTELLECTUAL PROPERTY LAW is a student organization sponsored by Wake Forest University -

SAPPHIRE R9 285 2GB GDDR5 ITX COMPACT OC Edition (UEFI)
Specification Display Support 4 x Maximum Display Monitor(s) support 1 x HDMI (with 3D) Output 2 x Mini-DisplayPort 1 x Dual-Link DVI-I 928 MHz Core Clock GPU 28 nm Chip 1792 x Stream Processors 2048 MB Size Video Memory 256 -bit GDDR5 5500 MHz Effective 171(L)X110(W)X35(H) mm Size. Dimension 2 x slot Driver CD Software SAPPHIRE TriXX Utility DVI to VGA Adapter Mini-DP to DP Cable Accessory HDMI 1.4a high speed 1.8 meter cable(Full Retail SKU only) 1 x 8 Pin to 6 Pin x2 Power adaptor Overview HDMI (with 3D) Support for Deep Color, 7.1 High Bitrate Audio, and 3D Stereoscopic, ensuring the highest quality Blu-ray and video experience possible from your PC. Mini-DisplayPort Enjoy the benefits of the latest generation display interface, DisplayPort. With the ultra high HD resolution, the graphics card ensures that you are able to support the latest generation of LCD monitors. Dual-Link DVI-I Equipped with the most popular Dual Link DVI (Digital Visual Interface), this card is able to display ultra high resolutions of up to 2560 x 1600 at 60Hz. Advanced GDDR5 Memory Technology GDDR5 memory provides twice the bandwidth per pin of GDDR3 memory, delivering more speed and higher bandwidth. Advanced GDDR5 Memory Technology GDDR5 memory provides twice the bandwidth per pin of GDDR3 memory, delivering more speed and higher bandwidth. AMD Stream Technology Accelerate the most demanding applications with AMD Stream technology and do more with your PC. AMD Stream Technology allows you to use the teraflops of compute power locked up in your graphics processer on tasks other than traditional graphics such as video encoding, at which the graphics processor is many, many times faster than using the CPU alone. -

AMD Catalyst™ Software Suite Version 12.3 Release Notes
Page 1 of 4 AMD Catalyst™ Software Suite Version 12.3 • Back Release Notes Last Updated 3/28/2012 Article Number 158 This article provides information on the latest posting of AMD’s software suite, AMD Catalyst™12.3. This particular software suite updates the AMD display driver and the AMD Catalyst Control Center/ AMD Vision Engine Control Center. This unified driver has been updated to provide enhanced level of power, performance, and reliability. Package Content The AMD Catalyst software suite 12.3 contains the following: • AMD display driver version 8.951 • HydraVision™ for Windows Vista ® and Windows ® 7 • Southbridge/IXP Driver • AMD Catalyst Control Center version 8.951 / AMD Vision Engine Control Center version 8.951 Important! Caution! • The AMD Catalyst Control Center/ AMD Vision Engine Control Center requires that the Microsoft® .NET Framework SP1 be installed for Windows XP and Windows Vista. Without .NET SP1 installed, the AMD Catalyst Control Center / AMD Vision Engine Control Center will not launch properly and the user will see an error message. Notes. • When installing the AMD Catalyst driver for Windows operating system, the user must be logged on as Administrator or have Administrator rights to complete the installation of the AMD Catalyst driver. • The Catalyst driver requires Windows 7 Service Pack 1 to be installed. • These release notes provide information on the AMD display driver only. For information on the ATI Multimedia Center™, HydraVision, HydraVision Basic Edition, Remote Wonder, or the Southbridge/IXP driver, please refer to their respective release notes found at : http://support.amd.com/. • AMD Eyefinity technology gives gamers access to high display resolutions. -

System Requirements for Virtual Classes Updated 5/11/2020
System Requirements for Virtual Classes Updated 5/11/2020 See also: Software List for Virtual Classes (includes installation instructions) After signing up your child for one of Empow’s virtual classes, it is highly advised to install the appropriate software or create an account for the class. Each class description will contain one or more of the following tools, and all classes require Zoom. Please take careful note of which operating systems (OSes) are required for the software that your child will be using in classes they are registered in. In most cases a computer is required rather than a tablet. Zoom: Supported OSes: Windows XP+, Mac OS 10.7+, Linux, ChromeOS Supported Tablets: iPad 2 or later with iPadOS 13+, Android 4.0+ with 1Ghz processor or better Required: Microphone Recommended: Headphones Recommended: Webcam Install AND Account creation required https://zoom.us/download EV3 Programming: OS requirements: Windows Vista or later, or Mac OS 10.6 - 10.14 --- DOES NOT WORK IN OS 10.15 Catalina Other requirements: Dual core processor - 2.0 Ghz or higher, 2GB of RAM, 2GB of hard drive space. Install required. https://www.lego.com/en-us/themes/mindstorms/downloads Scroll down the page to find the download for either Mac or Windows. Telephone #: 617-395-7527 x300 Website: empow.me Flowlab: Recommended Browsers: Chrome, Firefox, Safari No install required. HUE Animation PC requirements: Windows 10, 8, 7 or XP and graphics drivers with OpenGL 2.0 support Mac requirements: OS X 10.5 (Leopard) to macOS 10.14 (Mojave). DOES NOT -

Webgl 2.0 Requirements Need Help?
360 Central Ave., Suite 1350 St. Petersburg, FL | 727-851-9522 | marxent.com WebGL 2.0 Requirements This document provides recommended browser and hardware specifications to optimally run Marxent’s WebGL 2.0 applications. Supported Browsers Marxent leverages WebGL 2.0 technology; only the most agile web browsers support WebGL 2.0 functionality in its entirety - Chrome, Firefox, or Opera. As full WebGL 2.0 support expands to Safari and Edge, our WebGL 2.0 applications will support them. Chrome is the leading browser for all WebGL applications and as of 2018 Chrome is the browser of choice for roughly half of total domestic internet users. If a user attempts to access a Marxent WebGL application via Safari, Edge or other unsupported browsers, they will be redirected to and asked to download Chrome, Firefox, or Opera. Internet Explorer does not support WebGL and has been deprecated by Microsoft. Recommended Hardware Users will experience optimal WebGL performance if their device meets the hardware specifications below. The application may run on older or lower-end devices but Marxent cannot guarantee the quality, speed or stability of the experience. Minimum System Specs: • 64-bit operating system • 4GB of RAM • Integrated graphics with WebGL 2.0 / OpenGL ES 3.0 Support • Dual-core Intel/AMD CPU • Latest version of Chrome, Firefox, or Opera Recommended System Specs: • 64-bit operating system • 8GB of RAM or higher • Dedicated NVIDIA/AMD GPU (Geforce 400 or Radeon HD 7000 Series or higher) • High-density displays (e.g. Retina or 4K) require high quality GPU • Quad-core Intel/AMD CPU (Intel Sandy Bridge or AMD Bulldozer Series or higher) • Latest version of Chrome, Firefox, or Opera Laptop trackpads are supported, however Marxent recommends use of a two-button mouse with a scroll wheel for best user experience. -

GPGPU-K És Programozásuk
GPGPU-k és programozásuk Dezső, Sima Sándor, Szénási Created by XMLmind XSL-FO Converter. GPGPU-k és programozásuk írta Dezső, Sima és Sándor, Szénási Szerzői jog © 2013 Typotex Kivonat A processzor technika alkalmazásának fejlődése terén napjaink egyik jellemző tendenciája a GPGPU-k rohamos térnyerése a számításigényes feladatok futtatásához mind a tudományos, mind a műszaki és újabban a pénzügyi- üzleti szférában. A tárgy célja kettős. Egyrészt megismerteti a hallgatókat a GPGPU-k működési elveivel, felépítésével, jellemzőivel, valamint a fontosabb NVIDIA és AMD GPGPU implementációkkal, másrészt a tárgy gyakorlati ismereteket nyújt az adatpárhuzamos programozás és kiemelten a GPGPU-k programozása, programok optimalizálása területén a CUDA nyelv és programozási környezetének megismertetésén keresztül. Lektorálta: Dr. Levendovszky János, Dr. Oláh András Created by XMLmind XSL-FO Converter. Tartalom I. GPGPU-k ........................................................................................................................................ 1 Cél .......................................................................................................................................... ix 1. Bevezetés a GPGPU-kba .................................................................................................... 10 1. Objektumok ábrázolása háromszögekkel ................................................................. 10 1.1. GPU-k shadereinek főbb típusai .................................................................. 11 2. Él- és -

Release V0.1-Alpha.3 Inexor Collective
Inexor Vulkan Renderer Release v0.1-alpha.3 Inexor Collective Sep 29, 2021 CONTENTS 1 Documentation 3 1.1 Development...............................................3 1.2 Source Code............................................... 57 1.3 How to contribute............................................ 162 1.4 Frequently asked questions........................................ 167 1.5 Changelog................................................ 172 1.6 Helpful Links............................................... 174 1.7 Source Code License........................................... 177 1.8 Contact us................................................ 177 1.9 Frequently asked questions........................................ 178 Index 185 i ii Inexor Vulkan Renderer, Release v0.1-alpha.3 Inexor is a MIT-licensed open-source project which develops a new 3D octree game engine by combining modern C++ with Vulkan API. CONTENTS 1 Inexor Vulkan Renderer, Release v0.1-alpha.3 2 CONTENTS CHAPTER ONE DOCUMENTATION Quickstart: Building Instructions (Windows/Linux)& Getting started 1.1 Development 1.1.1 Supported platforms • Vulkan API is completely platform-agnostic, which allows it to run on various operating systems. • The required drivers for Vulkan are usually part of your graphic card’s drivers. • Update your graphics drivers as often as possible since new drivers with Vulkan updates are released frequently. • Driver updates contain new features, bug fixes, and performance improvements. • Check out Khronos website for more information. Microsoft Windows • We support x64 Microsoft Windows 8, 8.1 and 10. • We have build instructions for Windows. Linux • We support every x64 Linux distribution for which Vulkan drivers exist. • We have specific build instructions for Gentoo and Ubuntu. • If you have found a way to set it up for other Linux distributions, please open a pull request and let us know! macOS and iOS • We do not support macOS or iOS because it would require us to use MoltenVK to get Vulkan running on Mac OS. -

Amd Radeon 7000 Series Driver Download Amd Radeon 7000 Series Driver Download
amd radeon 7000 series driver download Amd radeon 7000 series driver download. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a1b815bb7484d4 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. DRIVERS AMD RADEONTM HD 7000 SERIES WINDOWS VISTA. Tech tip, updating drivers manually requires some computer skills and patience. Amd/ati drivers you have been having this graphic. This tool is designed to detect the model of amd graphics card and the version of microsoft windows installed in your system, and then provide the option to download and install the latest official amd driver. Compaq cq42-304au. Your system for the radeon hd 7000. For use with systems equipped with amd radeon discrete desktop graphics, mobile graphics, or amd processors with radeon graphics. Download drivers are running amd radeon drivers by jervis on topic. Hd 7000 series for amd 7000 series amd accelerated processing units. Integer Scaling. Developers working with the amd embedded r-series apu can implement remote management, client virtualization and security capabilities to help reduce deployment costs and increase security and reliability of their amd r-series based platform through amd das 1.0 featuring dash 1.1, amd virtualization and trusted platform module tpm 1.2 support. -

Sapphire Technology Web Site
SAPPHIRE HD 7850 OC 2GB GDDR5 Offering excellent performance at an even keener price, SAPPHIRE HD 7850 OC shares the features of the HD 7000 family with Dual-X cooling technology, a highly efficient multi-heatpipe cooler with dual fans providing quiet and very cool operation during normal operating conditions, and superb cooling performance even under extreme load. Where to Buy Gefällt39 mir Overview System Requirements News Download Specification 1 x Dual-Link DVI 1 x HDMI (with 3D) Output 2 x Mini-DisplayPort DisplayPort 1.2 920 MHz Core Clock GPU 28 nm Chip 1024 x Stream Processors 2048 MB Size Memory 256 -bit GDDR5 5000 MHz Effective Dimension 210(L)x105(W)x35(H) mm Size. Software Driver CD CrossFire™ Bridge Interconnect Cable Mini-DP to DP Cable Accessory 6 PIN to 4 PIN Power Cable HDMI to SL-DVI Adapter(Full Retail SKU only) HDMI 1.4a high speed 1.8 meter cable(Full Retail SKU only) Overview Dual-Link DVI Equipped with the most popular Dual Link DVI (Digital Visual Interface), this card is able to display ultra high resolutions of up to 2560 x 1600 at 60Hz. HDMI (with 3D) Support for Deep Color, 7.1 High Bitrate Audio, and 3D Stereoscopic, ensuring the highest quality Blu-ray and video experience possible from your PC. Mini-DisplayPort Enjoy the benefits of the latest generation display interface, DisplayPort. With the ultra high HD resolution, the graphics card ensures that you are able to support the latest generation of LCD monitors. DisplayPort 1.2 Doubling the effective bandwidth of previous DisplayPort implementations, DisplayPort 1.2 now includes support for Multi-Stream, allowing you to drive up to four separate monitors from a single DisplayPort 1.2 connector (requires DP1.2 monitors or Multi-Stream compatible hub), Stereoscopic 3D monitor support and adds support for high quality, lossless, 7.1 channel audio formats. -
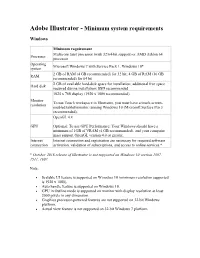
Adobe Illustrator - Minimum System Requirements
Adobe Illustrator - Minimum system requirements Windows Minimum requirement Multicore Intel processor (with 32/64-bit support) or AMD Athlon 64 Processor processor Operating Microsoft Windows 7 with Service Pack 1, Windows 10* system 2 GB of RAM (4 GB recommended) for 32 bit; 4 GB of RAM (16 GB RAM recommended) for 64 bit 2 GB of available hard-disk space for installation; additional free space Hard disk required during installation; SSD recommended 1024 x 768 display (1920 x 1080 recommended) Monitor To use Touch workspace in Illustrator, you must have a touch-screen- resolution enabled tablet/monitor running Windows 10 (Microsoft Surface Pro 3 recommended). OpenGL 4.x GPU Optional: To use GPU Performance: Your Windows should have a minimum of 1GB of VRAM (4 GB recommended), and your computer must support OpenGL version 4.0 or greater. Internet Internet connection and registration are necessary for required software connection activation, validation of subscriptions, and access to online services.* * October 2018 release of Illustrator is not supported on Windows 10 version 1507, 1511, 1607. Note: • Scalable UI feature is supported on Winodws 10 (minimum resolution supported is 1920 x 1080). • Auto handle feature is supported on Windows 10. • GPU in Outline mode is supported on monitor with display resolution at least 2000 pixels in any dimension. • Graphics processor-powered features are not supported on 32-bit Windows platform. • Actual view feature is not supported on 32-bit Windows 7 platform. Supported video adapter The following video adapter series support the new Windows GPU Performance features in Illustrator: NVIDIA • NVIDIA Quadro K Series • NVIDIA Quadro 6xxx • NVIDIA Quadro 5xxx • NVIDIA Quadro 4xxx • NVIDIA Quadro 2xxx • NVIDIA Quadro 2xxxD • NVIDIA Quadro 6xx • NVIDIA GeForce GTX Series (4xx, 5xx, 6xx, 7xx, 9xx, Titan) • NVIDIA Quadro M Series • NVIDIA Quadro P Series Important: Microsoft Windows may not detect the availability of the latest device drivers for NVIDIA GPU cards. -

AMD Codexl 1.3 GA Release Notes
AMD CodeXL 1.3 GA Release Notes Thank you for using CodeXL. We appreciate any feedback you have! Please use the CodeXL Forum to provide your feedback. You can also check out the Getting Started guide on the CodeXL Web Page and the latest CodeXL blog at AMD Developer Central - Blogs This version contains: For Windows for 32-bit and 64-bit Windows platforms o CodeXL Standalone application o CodeXL Microsoft® Visual Studio® 2010 extension o CodeXL Microsoft® Visual Studio® 2012 extension o CodeXL Remote Agent For 64-bit Linux platforms o CodeXL Standalone application o CodeXL Remote Agent Note about 32-bit Windows CodeXL 1.3 Upgrade Error On 32-bit Windows platforms, upgrading from CodeXL 1.0 using the CodeXL 1.3 installer will remove the previous version and then display an error message without installing CodeXL 1.3. The recommended method is to uninstall previous CodeXL versions before installing CodeXL 1.3. If you ran the 1.3 installer to upgrade a previous installation and encountered the error mentioned above, ignore the error and run the installer again to install CodeXL 1.3. Note about installing CodeAnalyst after installing CodeXL for Windows CodeXL can be safely installed on a Windows station where AMD CodeAnalyst is already installed. However, do not install CodeAnalyst on a Windows station already installed with CodeXL. Uninstall CodeXL first, and then install CodeAnalyst. System Requirements CodeXL contains a host of development features with varying system requirements: GPU Profiling and OpenCL Kernel Debugging o An AMD GPU (Radeon HD 5000 series or newer, desktop or mobile version) or APU is required.