Vulnerability Summary for the Week of November 3, 2014
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fear the EAR: Discovering and Mitigating Execution After Redirect Vulnerabilities
Fear the EAR: Discovering and Mitigating Execution After Redirect Vulnerabilities Adam Doupé, Bryce Boe, Christopher Kruegel, and Giovanni Vigna University of California, Santa Barbara {adoupe, bboe, chris, vigna}@cs.ucsb.edu ABSTRACT 1. INTRODUCTION The complexity of modern web applications makes it diffi- An increasing number of services are being offered on- cult for developers to fully understand the security implica- line. For example, banking, shopping, socializing, reading tions of their code. Attackers exploit the resulting security the news, and enjoying entertainment are all available on the vulnerabilities to gain unauthorized access to the web appli- web. The increasing amount of sensitive data stored by web cation environment. Previous research into web application applications has attracted the attention of cyber-criminals, vulnerabilities has mostly focused on input validation flaws, who break into systems to steal valuable information such such as cross site scripting and SQL injection, while logic as passwords, credit card numbers, social security numbers, flaws have received comparably less attention. and bank account credentials. In this paper, we present a comprehensive study of a rela- Attackers use a variety of vulnerabilities to exploit web tively unknown logic flaw in web applications, which we call applications. In 2008, Albert Gonzalez was accused and Execution After Redirect, or EAR. A web application de- later convicted of stealing 40 million credit and debit cards veloper can introduce an EAR by calling a redirect method from major corporate retailers, by writing SQL injection under the assumption that execution will halt. A vulnera- attacks [20, 30]. Another common vulnerability, cross-site bility occurs when server-side execution continues after the scripting (XSS), is the second highest-ranked entry on the developer’s intended halting point, which can lead to bro- OWASP top ten security risks for web applications, behind ken/insufficient access controls and information leakage. -

A Web-Based Application for the Display of Geolocated Tweets on a Map
UNIVERSITY OF FRIBOURG Pervasive & Artificial Intelligence Research Group LTMap A web-based application for the display of geolocated Tweets on a map MASTER THESIS Aron Martinez Student number: 06-208-771 Address: Via Ravecchia 11b, CH-6512 Giubiasco Email: [email protected] Head: Prof. Beat Hirsbrunner Supervisor: Apostolos Malatras Giubiasco, March 24, 2013 Swiss Joint Master of Science in Computer Science Acknowledgements Acknowledgements First of all, I would like to thank Apostolos Malatras for his support, guidance and good advice, and also for all the valuable feedback he provided me. I would also like to thank Prof. Beat Hirsbrunner for giving me the chance to be part of the PAI group for the duration of my master thesis. It has been a great pleasure to collaborate with the PAI research group and to meet all its very kind members during the project meetings and presentations. Finally I want to thank my family and friends for their moral support, and last but not least, I want to thank my wife Lucile for having always believed in me, and for her invaluable support and her continuous encouragement during the writing of the thesis. iii Abstract Abstract Today, different services offer geolocated information based on social networks, but in most cases this information is available only for some major cities around the world, for only one social network at a time and without focusing on the actual personal interests of the user. The purpose of this master thesis is to create a web-based application that uses open- source APIs to access localization services and social network information and displays the retrieved information on a map, based on the user’s location. -
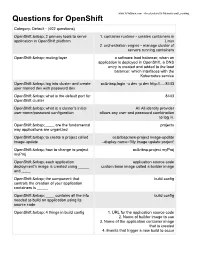
Questions for Openshift
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for OpenShift Category: Default - (402 questions) OpenShift: 2 primary tools to serve 1. container runtime - creates containers in application in OpenShift platform Linux 2. orchestration engine - manage cluster of servers running containers OpenShift: routing layer a software load balancer, when an application is deployed in OpenShift, a DNS entry is created and added to the load balancer, which interfaces with the Kubernetes service OpenShift: log into cluster and create oc login -u dev -p dev http://....:8443 user named dev with password dev OpenShift: what is the default port for 8443 OpenShift cluster OpenShift: what is a cluster's initial All All identity provider user name/password configuration allows any user and password combination to log in. OpenShift: ____ are the fundamental projects way applications are organized OpenShift: to create a project called oc new-project image-update image-update --display-name='My image update project' OpenShift: how to change to project oc project myProj myProj OpenShift: each application application source code deployment's image is created using _____ custom base image called a builder image and ____ OpenShift: the component that build config controls the creation of your application containers is _____ OpenShift: ____ contains all the info build config needed to build an application using its source code OpenShift: 4 things in build config 1. URL for the application source code 2. Name of builder image to use 3. Name of the application container image that is created 4. -
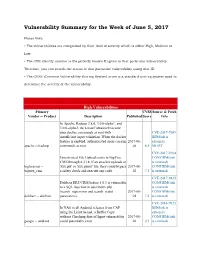
Vulnerability Summary for the Week of June 5, 2017
Vulnerability Summary for the Week of June 5, 2017 Please Note: • The vulnerabilities are categorized by their level of severity which is either High, Medium or Low. • The CVE identity number is the publicly known ID given to that particular vulnerability. Therefore, you can search the status of that particular vulnerability using that ID. • The CVSS (Common Vulnerability Scoring System) score is a standard scoring system used to determine the severity of the vulnerability. High Vulnerabilities Primary CVSS Source & Patch Vendor -- Product Description Published Score Info In Apache Hadoop 2.8.0, 3.0.0-alpha1, and 3.0.0-alpha2, the LinuxContainerExecutor runs docker commands as root with CVE-2017-7669 insufficient input validation. When the docker BID(link is feature is enabled, authenticated users can run 2017-06- external) apache -- hadoop commands as root. 04 8.5 MLIST CVE-2017-9364 Unrestricted File Upload exists in BigTree CONFIRM(link CMS through 4.2.18: if an attacker uploads an is external) bigtreecms -- 'xxx.pht' or 'xxx.phtml' file, they could bypass 2017-06- CONFIRM(link bigtree_cms a safety check and execute any code. 02 7.5 is external) CVE-2017-9435 Dolibarr ERP/CRM before 5.0.3 is vulnerable CONFIRM(link to a SQL injection in user/index.php is external) (search_supervisor and search_statut 2017-06- CONFIRM(link dolibarr -- dolibarr parameters). 05 7.5 is external) CVE-2014-9923 In NAS in all Android releases from CAF BID(link is using the Linux kernel, a Buffer Copy external) without Checking Size of Input vulnerability 2017-06- CONFIRM(link google -- android could potentially exist. -

A Systematic Analysis of XSS Sanitization in Web Application Frameworks
A Systematic Analysis of XSS Sanitization in Web Application Frameworks Joel Weinberger, Prateek Saxena, Devdatta Akhawe, Matthew Finifter, Richard Shin, and Dawn Song University of California, Berkeley Abstract. While most research on XSS defense has focused on techniques for securing existing applications and re-architecting browser mechanisms, sanitiza- tion remains the industry-standard defense mechanism. By streamlining and au- tomating XSS sanitization, web application frameworks stand in a good position to stop XSS but have received little research attention. In order to drive research on web frameworks, we systematically study the security of the XSS sanitization abstractions frameworks provide. We develop a novel model of the web browser and characterize the challenges of XSS sanitization. Based on the model, we sys- tematically evaluate the XSS abstractions in 14 major commercially-used web frameworks. We find that frameworks often do not address critical parts of the XSS conundrum. We perform an empirical analysis of 8 large web applications to extract the requirements of sanitization primitives from the perspective of real- world applications. Our study shows that there is a wide gap between the abstrac- tions provided by frameworks and the requirements of applications. 1 Introduction Cross-site scripting (XSS) attacks are an unrelenting threat to existing and emerg- ing web applications. Major web services such as Google Analytics, Facebook and Twitter have had XSS issues in recent years despite intense research on the sub- ject [34, 52, 61]. Though XSS mitigation and analysis techniques have enjoyed intense focus [6, 7, 12, 13, 33, 36, 37, 39, 41, 43, 44, 47, 49, 50, 59, 64, 66, 68], research has paid little or no attention to a promising sets of tools for solving the XSS riddle—web appli- cation frameworks—which are gaining wide adoption [18, 21, 22, 28, 35, 42, 48, 55, 58, 69, 71]. -

Guide to Open Source Solutions
White paper ___________________________ Guide to open source solutions “Guide to open source by Smile ” Page 2 PREAMBLE SMILE Smile is a company of engineers specialising in the implementing of open source solutions OM and the integrating of systems relying on open source. Smile is member of APRIL, the C . association for the promotion and defence of free software, Alliance Libre, PLOSS, and PLOSS RA, which are regional cluster associations of free software companies. OSS Smile has 600 throughout the World which makes it the largest company in Europe - specialising in open source. Since approximately 2000, Smile has been actively supervising developments in technology which enables it to discover the most promising open source products, to qualify and assess them so as to offer its clients the most accomplished, robust and sustainable products. SMILE . This approach has led to a range of white papers covering various fields of application: Content management (2004), portals (2005), business intelligence (2006), PHP frameworks (2007), virtualisation (2007), and electronic document management (2008), as well as PGIs/ERPs (2008). Among the works published in 2009, we would also cite “open source VPN’s”, “Firewall open source flow control”, and “Middleware”, within the framework of the WWW “System and Infrastructure” collection. Each of these works presents a selection of best open source solutions for the domain in question, their respective qualities as well as operational feedback. As open source solutions continue to acquire new domains, Smile will be there to help its clients benefit from these in a risk-free way. Smile is present in the European IT landscape as the integration architect of choice to support the largest companies in the adoption of the best open source solutions. -

Red Hat Directory Server 11 Installation Guide
Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Last Updated: 2021-04-23 Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Marc Muehlfeld Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 6.4 Release Notes
Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Red Hat Engineering Content Services Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Opettajan Arvio Opinnäytetyöstä
Harrison Oriahi CONTENT MANAGEMENT SYSTEMS (CMS) CONTENT MANAGEMENT SYSTEMS (CMS) Harrison Oriahi Bachelor’s thesis Autumn 2014 Degree Programme in Information Technology Oulu University of Applied Sciences ABSTRACT Oulu University of Applied Sciences Degree in Information Technology, Internet Services Author(s): Harrison Oriahi Title of Bachelor’s thesis: Content Management Systems Supervisor(s): Veijo Väisänen Term and year of completion: Autumn 2014 Number of pages: 48 + 3 appendices ABSTRACT: This thesis describes the three most common and widely used content management systems (CMS) used to power several millions of business websites on the internet. Since there are many other content managements systems online, this report provides some helpful guides on each of these three most used systems and the web design projects that each of them maybe most suitable. There are plenty of options when it comes to selecting a content management system for a development project and this thesis focuses on making a detailed comparison between the three most commonly used ones. This comparison will help provide a clear understanding of why a content management system maybe preferred to the other when considering any web design project. To help detect the content management system (CMS) or development platform that an already existing website is built on, some helpful website analyzing tools are also discussed in this report. By reading this report, a reader with no previous experience with content management systems will be able to have a general view on what they are, what the commonly used ones are and what to consider when making a choice of content management system to use. -

BAB II LANDASAN TEORI 2.1 Sistem Informasi Menurut Laudon, K C Dan
5 BAB II LANDASAN TEORI 2.1 Sistem Informasi Menurut Laudon, K C dan Laudon, J.P dalam indonesian journal on networking and security menjelaskan, sistem informasi adalah teknologi informasi tang diorganisasikan untuk mencapai tujuan dalam sebuah organisasi. Secara teknis sistem informasi dapat didefinisikan sebagai kumpulan komponen yang saling berhubungan, mengumpulkan, memproses, menyimpan, dan mendistribusikan informasi untuk menunjang pengambilan keputusan dan pengawasan dalam suatu organisasi. 2.2 CodeIgniter CodeIgniter adalah framework web untuk bahasa pemrograman PHP, yang dibuat oleh Rick Ellis pada tahun 2006, penemu dan pendiri EllisLab(www.ellislab.com). EllisLab adalah suatu tim kerja yang terdiri pada tahun 2002 dan bergerak di bidang pembuatan software dan tool untuk para pengembang web. Sejak tahun 2014 EllisLab telah menyerahkan hak kepemilikan CodeIgniter ke British Columbia Institute of Technology (BCIT) untuk proses pengembangan lebih lanjut. saat ini, situs web resmi dari CodeIgniter telah berubah dari www.ellislab.com ke www.codeigniter.com. CodeIgniter memiliki banyak fitur (fasilitas) yang membantu para pengembang (developer) PHP untuk dapat membuat aplikasi web secara mudah dan cepat. Dibandingkan dengan framework web PHP lainnya, harus diakui bahwa CodeIgniter memiliki desain yang lebih sederhana dan bersifat fleksibel tidak kaku.(Budi Raharjo, 2015) 6 2.3 MVC (Model, View, Controller) Dalam teknik pemrograman berorientasi objek, Model-View-Controller(MVC) adalah nama dari suatu metodologi atau pola design (design patern) yang digunakan untuk merelasikan data dan user-interface aplikasi secara efesien. pola MVC awalnya digunakan untuk rancang bangun aplikasi dekstop, khusus nya untuk aplikasi-aplikasi yang dikembangkan menggunakan C++, Java, dan Smalltalk, Namun, saat ini arsitektur tersebut telah diadopsi untuk aplikasi berbasis web. -

Centos System Administration Essentials
www.it-ebooks.info CentOS System Administration Essentials Become an efficient CentOS administrator by acquiring real-world knowledge of system setup and configuration Andrew Mallett BIRMINGHAM - MUMBAI www.it-ebooks.info CentOS System Administration Essentials Copyright © 2014 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: November 2014 Production reference: 1181114 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B3 2PB, UK. ISBN 978-1-78398-592-0 www.packtpub.com Cover image by Bartosz Chucherko ([email protected]) [ FM-2 ] www.it-ebooks.info Credits Author Project Coordinator Andrew Mallett Neha Thakur Reviewers Proofreaders Jonathan -

Red Hat Jboss Fuse 6.3 Security Guide
Red Hat JBoss Fuse 6.3 Security Guide Making it safe for your systems to work together Last Updated: 2017-11-09 Red Hat JBoss Fuse 6.3 Security Guide Making it safe for your systems to work together JBoss A-MQ Docs Team Content Services [email protected] Legal Notice Copyright © 2016 Red Hat. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent.