MALICIOUS Threat Names: Generic.Andromeda.6165138E Gen:Variant.Razy.762033
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

INSIDE! Double-Sided DVD Double-Sided
and lots of LINUX LINUX PRO MAGAZINE FREE USB PASSWORD SAFER BOOT DVD other timely Making Secure Boot MANAGER and useful tools work with Linux ISSUE ISSUE 206 Double-Sided DVD JANUARY 2018 JANUARY 2018 JANUARY INSIDE! SAFER Safer Boot Safer UEFI Shim TPM Backup Tools Stacer DDoS Attacks Pi FM Radio Volumio 2 Volumio Radio FM Pi Attacks DDoS Stacer Backup Tools TPM Shim UEFI BOOT Keeping control of the startup process UEFI Tricks Add a custom app that runs from the firmware Automated 5 Backup Tools Pi FM Radio DDoS Attack Stacer Build a stairway Avoiding a denial Clean up your to maker heaven of service nightmare Linux system Issue 206 Jan 2018 FOSSPicks US$ 15.99 CAN$ 17.99 FOSS • qutebrowser 1.0 0 74820 58049 Marke • Storyboarder t • CoreFreq ing • Marketing Free Software Audacity ffmpeg • Fragment synthesizer • Phipps: FOSS Communities Need Equal Rights Tutorials 3 • Digitize Your LPs with Audacity • ffmpeg 01 WWW.LINUXPROMAGAZINE.COM EDITORIAL Welcome TOMORROW’S NEWS Dear Reader, When I started working for this magazine, way back in 2004, of lobbyists and marketing professionals who keep chipping Linux was really picking up momentum. That was back in away at public opinion when everyone else has gone back to those years when every year was supposed to be “the year of their day jobs. the Linux desktop,” and the epic Linux vs. Windows battle Software has no shape or solid edges. The value of a software was revving to a full burn. product is simply what whoever owns it says they will charge One of the best examples of the Linux juggernaut was the city you for it. -

Extron SMP 111 User Guide
User Guide Streaming AV Product SMP 111 Streaming Media Processor 68-2850-01 Rev. C 11 17 Safety Instructions Safety Instructions • English Istruzioni di sicurezza • Italiano WARNING: This symbol, , when used on the product, is intended to AVVERTENZA: Il simbolo, , se usato sul prodotto, serve ad alert the user of the presence of uninsulated dangerous voltage within avvertire l’utente della presenza di tensione non isolata pericolosa the product’s enclosure that may present a risk of electric shock. all’interno del contenitore del prodotto che può costituire un rischio di scosse elettriche. ATTENTION: This symbol, , when used on the product, is intended to alert the user of important operating and maintenance (servicing) ATTENTZIONE: Il simbolo, , se usato sul prodotto, serve ad instructions in the literature provided with the equipment. avvertire l’utente della presenza di importanti istruzioni di funzionamento e manutenzione nella documentazione fornita con l’apparecchio. For information on safety guidelines, regulatory compliances, EMI/EMF compatibility, accessibility, and related topics, see the Extron Safety and Per informazioni su parametri di sicurezza, conformità alle normative, Regulatory Compliance Guide, part number 68-290-01, on the Extron compatibilità EMI/EMF, accessibilità e argomenti simili, fare riferimento website, www.extron.com. alla Guida alla conformità normativa e di sicurezza di Extron, cod. articolo 68-290-01, sul sito web di Extron, www.extron.com. Sicherheitsanweisungen • Deutsch Instrukcje bezpieczeństwa • Polska WARNUNG: Dieses Symbol auf dem Produkt soll den Benutzer darauf aufmerksam machen, dass im Inneren des Gehäuses dieses OSTRZEŻENIE: Ten symbol, , gdy używany na produkt, ma na celu Produktes gefährliche Spannungen herrschen, die nicht isoliert sind und poinformować użytkownika o obecności izolowanego i niebezpiecznego die einen elektrischen Schlag verursachen können. -

BAB VII Tip Dan Trik Ubuntu A. Backup Hasil Install Dari Repository Online
BAB VII Tip dan Trik Ubuntu A. Backup Hasil Install dari Repository Online Menambahkan progrgram aplikasi di Ubuntu adalah hal yang sangat penting, apalagi kalauau memiliiliki koneksi internet. Mendownload filfile progrgram darii repository di internet maupun mengupdate/upgrade Ubuntu bisa dengan mudah dilakukan. Untuk menghindari download file yang sama dari repository online secara berulang-ulang, sebaiknya dilakukan backup file hasil download. Hal ini akan sangat menguntungkan jika anda dikemudian hari menginstall ulang Ubuntu karena Ubuntu menemukan kernel panic atau cuma sekedar berbagi filfile progrgram dengan teman-teman yang lain. Untuk melakukan hal itu diperlukan softaware APTonCD. sebagai infinformasi filfile yayang teltelahah didownload dari repository online disimpan di folfolder /var/cache/apt/archives. Jika aplikasisi APTonCD belum terinstall, lakukan hal berikut untuk menginstall aplikasinya. Buka terminal dan ketikkan perintah di bawah ini. $ sudo apt-get install aptoncd Setelah selesai aktifkan programnya dari menu System - Administration - APTOnCD. Window aplikasi APTOnCD akan terbuka seperti gambar PA.1 gambar PA.1 Selanjutnya klik tombol Create. Program secara otomatis menampilkan informasi paket-paket yang telah didownload dari repository online (gambar PA.2) gambar PA.2 Untuk menambahkan paket lainnya cukup dengan mengklik tombol Add (gambar PA.3). Jika data telah dikumpulkan oleh program, selanjutnya klik Burn... untuk memulai pembuatan ISO CD. gambar PA.3 Pada gambar PA.4 di bawah ini anda akan diminta untuk melakukan beberapa setting, jika file *.iso anda kurang dari 1 CD (<700MB) maka sebaiknya pilih opsi 1 CD, tapi jika melebihi 1 CD (>700MB) silahkan pilih opsi 1 DVD. Selanjutnya pilih lokasi di mana anda akan menyimpan filenya serta isi nama file untuk file iso yang akan dibuat dan klik Apply . -

Web-Based Fingerprinting Techniques
Web-based Fingerprinting Techniques V´ıtor Bernardo and Dulce Domingos LaSIGE, Faculdade de Ciencias,ˆ Universidade de Lisboa, Lisboa, Portugal Keywords: Browser Fingerprinting, Cross-browser Fingerprinting, Device Fingerprinting, Privacy, Fingerprint. Abstract: The concept of device fingerprinting is based in the assumption that each electronic device holds a unique set of physical and/or logical features that others can capture and use to differentiate it from the whole. Web-based fingerprinting, a particular case of device fingerprinting, allows website owners to differentiate devices based on the set of information that browsers transmit. Depending on the techniques being used, a website can track a device based on its browser features (browser fingerprinting) or based on system settings (cross-browser fingerprinting). The latter allows identification of the device even when more than one browser is used. Several different works have introduced new techniques over the last years proving that fingerprinting can be done in multiple ways, but there is not a consolidated work gathering all of them. The current work identifies known web-based fingerprinting techniques, categorizing them as which ones are browser and which are cross-browser and showing real examples of the data that can be captured with each technique. The study is synthesized in a taxonomy, which provides a clear separation between techniques, making it easier to identify the threats to security and privacy inherent to each one. 1 INTRODUCTION far more upsetting than simple cookies. In most cases, web-based fingerprinting is used to Device fingerprinting is based on the assumption that track users activity in sites and bind a device finger- no two devices are exactly alike and that profiles can print to a user profile (together with its preferences, be created by capturing the emanation patterns sent tastes and interests). -
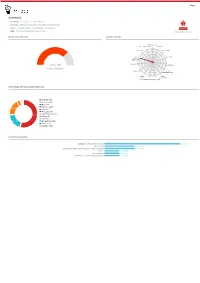
Advanced File Analysis System | Valkyrie
Page 1 Summary File Name: Packing_list_and_Draft_BL.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 948482095bade1c1d72cda2a08b165a47ca128f3 MALWARE MD5: 7828dd5b474006b86ffe30dce57520bc Valkyrie Final Verdict DETECTION SECTION CLASSIFICATION Backdoor(1.74%) Ransomware(0.00%) Bot(0.60%) 81% Worm(3.46%) Exploit(0.00%) 65% 48% Trojan 32% Pua(5.26%) Password Stealer(75.74%) 16% Rootkit(0.00%) Trojan Severity: High Generic(3.43%) Verdict: Malware Spyware(0.00%) Trojan Downloader(4.23%) Remote Trojan Access Dropper(3.60%) Trojan(0.00%V)irus(0.77%) Rogue(1.17%) HIGH LEVEL BEHAVIOR DISTRIBUTION Network (19) Process (128) Misc (47) System (1493) 18.2% Crypto (12) Threading (7) Synchronization (6) 54.0% Device (2) Windows (1) 19.7% File System (543) Services (3) Registry (502) ACTIVITY OVERVIEW Stealing of Sensitive Information 5 (41.67%) Networking 2 (16.67%) Hooking and other Techniques for Hiding Protection 2 (16.67%) Packer 1 (8.33%) Static Anomaly 1 (8.33%) Persistence and Installation Behavior 1 (8.33%) Page 2 Activity Details NETWORKING HTTP traffic contains suspicious features which may be indicative of malware related traffic Show sources Performs some HTTP requests Show sources PACKER The binary likely contains encrypted or compressed data. Show sources STEALING OF SENSITIVE INFORMATION Collects information to fingerprint the system Show sources Steals private information from local Internet browsers Show sources Harvests information related to installed instant messenger clients Show sources Harvests credentials -

Six Years and Counting: Inside the Complex Zacinlo Ad Fraud Operation White Paper
White Paper Six Years and Counting: Inside the Complex Zacinlo Ad Fraud Operation White Paper Authors: Claudiu Cobliș - Security Researcher, Cyber Threat Intelligence Lab Cristian Istrate - Security Researcher Tech Lead, Cyber Threat Intelligence Lab Cornel Punga - Security Researcher, Cyber Threat Intelligence Lab Andrei Ardelean - Security Researcher, Cyber Threat Intelligence Lab [2] White Paper Foreword For more than a decade, adware has helped software creators earn money while bringing free applications to the masses. Headliner games and applications have become widely available to computer and mobile users the world over, with no financial strings attached. This contract between the developer and the consumer, however, is governed by third parties –the advertisers – the entities that absorb the product’s cost in exchange for user-generated information and behavior. Enter the adware era. While generating untold revenue for the companies that run these programs, adware has witnessed constant improvements over the years in both data collection and resilience to removal. The line between adware and spyware has become increasingly fuzzy during recent years as modern adware combines aggressive opt-outs with confusing legal and marketing terms as well as extremely sophisticated persistence mechanisms aimed at taking control away from the user. This whitepaper details an extremely sophisticated piece of spyware that has been running covertly since early 2012, generating revenue for its operators and compromising the privacy of its victims. One of the perks of identifying a new strain of malware is getting to name it. We called this adware family “Zacinlo”, after the final payload, although this might not be the most appropriate name for such a complex piece of code. -

Extron SMP 300 Series User Guide
User Guide Streaming AV Product SMP 300 Series Streaming Media Processor 68-2238-01 Rev. M 03 21 Safety Instructions Copyright © 2016-2021 Extron. All rights reserved. www.extron.com Trademarks All trademarks mentioned in this guide are the properties of their respective owners. The following registered trademarks (®), registered service marks (SM), and trademarks (TM) are the property of RGB Systems, Inc. or Extron (see the current list of trademarks on the Terms of Use page at www.extron.com): Registered Trademarks (®) Extron, Cable Cubby, ControlScript, CrossPoint, DTP, eBUS, EDID Manager, EDID Minder, eLink, Flat Field, FlexOS, Glitch Free, Global Configurator, Global Scripter, GlobalViewer, Hideaway, HyperLane, IP Intercom, IP Link, Key Minder, LinkLicense, LockIt, MediaLink, MediaPort, NAV, NetPA, PlenumVault, PoleVault, PowerCage, PURE3, Quantum, ShareLink, Show Me, SoundField, SpeedMount, SpeedSwitch, StudioStation, System INTEGRATOR, TeamWork, TouchLink, V-Lock, VideoLounge, VN-Matrix, VoiceLift, WallVault, WindoWall, XPA, XTP, XTP Systems, and ZipClip Registered Service Mark(SM) : S3 Service Support Solutions Trademarks (™) AAP, AFL (Accu-RATE Frame Lock), ADSP (Advanced Digital Sync Processing), AVEdge, CableCover, CDRS (Class D Ripple Suppression), Codec Connect, DDSP (Digital Display Sync Processing), DMI (Dynamic Motion Interpolation), Driver Configurator, DSP Configurator, DSVP (Digital Sync Validation Processing), EQIP, Everlast, FastBite, Flex55, FOX, FOXBOX, IP Intercom HelpDesk, MAAP, MicroDigital, Opti-Torque, PendantConnect, ProDSP, QS-FPC (QuickSwitch Front Panel Controller), Room Agent, Scope-Trigger, SIS, Simple Instruction Set, Skew-Free, SpeedNav, Triple-Action Switching, True4K, True8K, Vector™ 4K, WebShare, XTRA, and ZipCaddy FCC Class A Notice This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC rules. -

Notes De Publication Pour Debian 10 (« Buster »), Powerpc 64 Bits (Petit-Boutiste)
Notes de publication pour Debian 10 (« Buster »), PowerPC 64 bits (petit-boutiste) Projet de documentation de Debian (https://www.debian.org/doc/) 3 octobre 2021 Notes de publication pour Debian 10 (« Buster »), PowerPC 64 bits (petit-boutiste) Ce document est libre, vous pouvez le redistribuer et/ou le modifier selon les termes de la Licence Publique Générale GNU publiée par la Free Software Foundation (version 2 ou bien toute autre version ultérieure choisie par vous). Ce document est distribué car potentiellement utile, mais SANS AUCUNE GARANTIE, ni explicite ni im- plicite, y compris les garanties de commercialisation ou d’adaptation dans un but spécifique. Reportez- vous à la Licence Publique Générale GNU pour plus de détails. Vous devez avoir reçu une copie de la Licence Publique Générale GNU en même temps que ce pro- gramme ; si ce n’est pas le cas, écrivez à la Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA. Le texte de la licence peut être trouvé (en langue anglaise) à l’adresse https://www.gnu.org/ licenses/gpl-2.0.html et dans le fichier /usr/share/common-licenses/GPL-2 sur les sys- tèmes Debian. ii Table des matières 1 Introduction 1 1.1 Signaler des bogues au sujet de ce document . 1 1.2 Fournir des comptes-rendus de mise à niveau . 1 1.3 Sources de ce document . 2 2 Nouveautés de Debian 10 3 2.1 Architectures prises en charge . 3 2.2 Quoi de neuf dans la distribution ? . 3 2.2.1 Secure Boot avec UEFI . -

Nokia Browser Download New Version
Nokia browser download new version Download Nokia Browser for Java now from Softonic: % safe and virus free. More than 24 downloads this month. Download Nokia Browser latest version. Nokia Browser for Java, free and safe download. Nokia Browser latest version: Navigate the web quickly on your S40 device. Nokia Browser is a slick web. If you have nokia phone then you can install its new and even old version, Both old and new version have so many features which are really. Download Nokia Browser Latest Version - best software for Windows. Nokia Software Updater: Nokia Software Updater provides you with an easy-to-use tool for. Get the best version of Opera Mini for your phone Nokia users, please share feedback about your new browser on Opera India's Facebook. Browser JavaScript is a feature that allows Opera to automatically fix Any updates will be automatically downloaded and applied the next time a page is Opera version is available, but it will still check for a new version of the file. Download for free to browse faster and save data on your phone or tablet. Discover new content and speed up slow connections with our fast mobile browsers. is the official website of UC Browser. You can download the latest version here. Visit to get the latest installation package for. Xpress Browser - We are creating Visual Studio browser to show how we can Xpress Browser (version) is available for download from our website. UC Browser for Nokia; Download for free to enjoy faster surfing buzz around their new smartphones including Nokia 7, Nokia 8, and Nokia 9 with Android OS, Nokia depended on their own software and OS versions. -

(Amiga; U; Amigaos 1.3; En; Rv:1.8.1.19) Gecko/20081204 Seamonkey/1.1.14 2 Mozilla/5.0
1 Mozilla/5.0 (Amiga; U; AmigaOS 1.3; en; rv:1.8.1.19) Gecko/20081204 SeaMonkey/1.1.14 2 Mozilla/5.0 (AmigaOS; U; AmigaOS 1.3; en-US; rv:1.8.1.21) Gecko/20090303 SeaMonkey/1.1.15 3 Mozilla/5.0 (AmigaOS; U; AmigaOS 1.3; en; rv:1.8.1.19) Gecko/20081204 SeaMonkey/1.1.14 4 Mozilla/5.0 (Android 2.2; Windows; U; Windows NT 6.1; en-US) AppleWebKit/533.19.4 (KHTML, like Gecko) Version/5.0.3 Safari/533.19.4 5 Mozilla/5.0 (BeOS; U; BeOS BeBox; fr; rv:1.9) Gecko/2008052906 BonEcho/2.0 6 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.8.1.1) Gecko/20061220 BonEcho/2.0.0.1 7 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.8.1.10) Gecko/20071128 BonEcho/2.0.0.10 8 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.8.1.17) Gecko/20080831 BonEcho/2.0.0.17 9 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.8.1.6) Gecko/20070731 BonEcho/2.0.0.6 10 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.8.1.7) Gecko/20070917 BonEcho/2.0.0.7 11 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.8.1b2) Gecko/20060901 Firefox/2.0b2 12 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.9a1) Gecko/20051002 Firefox/1.6a1 13 Mozilla/5.0 (BeOS; U; BeOS BePC; en-US; rv:1.9a1) Gecko/20060702 SeaMonkey/1.5a 14 Mozilla/5.0 (BeOS; U; Haiku BePC; en-US; rv:1.8.1.10pre) Gecko/20080112 SeaMonkey/1.1.7pre 15 Mozilla/5.0 (BeOS; U; Haiku BePC; en-US; rv:1.8.1.14) Gecko/20080429 BonEcho/2.0.0.14 16 Mozilla/5.0 (BeOS; U; Haiku BePC; en-US; rv:1.8.1.17) Gecko/20080831 BonEcho/2.0.0.17 17 Mozilla/5.0 (BeOS; U; Haiku BePC; en-US; rv:1.8.1.18) Gecko/20081114 BonEcho/2.0.0.18 18 Mozilla/5.0 (BeOS; U; Haiku BePC; en-US;