The Pioneer Research Journal
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Client White Ribbon Alliance-India Publication the Hindu Date 24 June 2009 Edition Visakhapatnam Headline Concern Over Maternal, Infant Mortality Rate
NEWS CLIPPING Client White Ribbon Alliance-India Publication The Hindu Date 24 June 2009 Edition Visakhapatnam Headline Concern over maternal, infant mortality rate NEWS CLIPPING Client White Ribbon Alliance-India Publication The New Indian Express Date 24 June 2009 Edition Bhubaneswar Headline Minister assures adequate supply of medicines NEWS CLIPPING Client White Ribbon Alliance-India Publication Dharitri Date 23 June 2009 Edition Bhubaneswar Headline Engagement NEWS CLIPPING Client White Ribbon Alliance-India Publication Dharitri Date 24 June 2009 Edition Bhubaneswar Headline Objective should be not to reduce maternal deaths, but stop it NEWS CLIPPING Client White Ribbon Alliance-India Publication The Samaya Date 24 June 2009 Edition Bhubaneswar Headline We are not able to utilise Centre and World Bank funds: Prasanna Acharys NEWS CLIPPING Client White Ribbon Alliance-India Publication The Pragativadi Date 24 June 2009 Edition Bhubaneswar Headline 67% maternal deaths occur in KBK region NEWS CLIPPING Client White Ribbon Alliance-India Publication The Anupam Bharat Date 24 June 2009 Edition Bhubaneswar Headline Free medicines to be given to pregnant women: Minister Ghadei NEWS CLIPPING Client White Ribbon Alliance-India Publication The Odisha Bhaskar Date 24 June 2009 Edition Bhubaneswar Headline Deliver Now for Women+Children campaign NEWS CLIPPING Client White Ribbon Alliance-India Publication Khabar Date 24 June 2009 Edition Bhubaneswar Headline Government hospitals not to give prescriptions for delivery cases NEWS CLIPPING Client -

Business Standard Date:- 24-Aug-20 Page No- 02 Edition:- Delhi Size:- 06*06 Cm News Related to Gail
Publication:- Business Standard Date:- 24-Aug-20 Page No- 02 Edition:- Delhi Size:- 06*06 cm News Related to Gail Publication:- Millennium Post Date:- 24-Aug-20 Page No- 11 Edition:- Delhi Size:- 12*08 cm News Related to Gail Publication:- Vir Arjun Date:- 24-Aug-20 Page No- 11 Edition:- Delhi Size:- 08*09 cm News Related to Gail Publication:- Virat Vaibhav Date:- 24-Aug-20 Page No- 11 Edition:- Delhi Size:- 14*08 cm News Related to Gail Publication:- The Economic Times Date:- 24-Aug-20 Page No- 05 Edition:- Delhi Size:- 08*09 cm News Related to Industry Publication:- The Hindu Business Line Date:- 24-Aug-20 Page No- 07 Edition:- Delhi Size:- 08*11 cm News Related to Industry Publication:- The Hindu Business Line Date:- 24-Aug-20 Page No- 09 Edition:- Delhi Size:- 06*13 cm News Related to Industry Publication:- The Hindu Business Line Date:- 24-Aug-20 Page No- 11 Edition:- Delhi Size:- 11*09 cm News Related to Industry Publication:- The Hindu Business Line Date:- 24-Aug-20 Page No- 14 Edition:- Delhi Size:- 10*16 cm News Related to Industry Publication:- The Indian Express Date:- 24-Aug-20 Page No- 14 Edition:- Delhi Size:- 05*15 cm News Related to Industry Publication:- Millennium Post Date:- 24-Aug-20 Page No- 01 Edition:- Delhi Size:- 04*03 cm News Related to Industry Publication:- Millennium Post Date:- 24-Aug-20 Page No- 11 Edition:- Delhi Size:- 11*03 cm News Related to Industry Publication:- The Financial Express Date:- 24-Aug-20 Page No- 11 Edition:- Delhi Size:- 08*15 cm News Related to Industry Publication:- Business Standard -
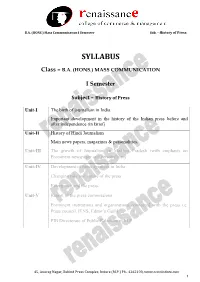
MASS COMMUNICATION I Semester Subject
B.A. (HONS.) Mass Communication I Semester Sub. – History of Press SYLLABUS Class – B.A. (HONS.) MASS COMMUNICATION I Semester Subject – History of Press Unit-I The birth of journalism in India Important development in the history of the Indian press before and after independence (in Brief) Unit-II History of Hindi Journalism Main news papers, magazines & personalities. Unit-III The growth of Journalism in Madhya Pradesh (with emphasis on Prominent newspaper and personalities) Unit-IV Development of news agencies in India Changing role and nature of the press Emergency and the press. Unit-V Report of the press commissions. Prominent institutions and organizations connected with the press i.e. Press council, IENS, Editor’s Guild PIB Directorate of Public Relations of M.P. 45, Anurag Nagar, Behind Press Complex, Indore (M.P.) Ph.: 4262100, www.rccmindore.com 1 B.A. (HONS.) Mass Communication I Semester Sub. – History of Press UNIT-I History of journalism Newspapers have always been the primary medium of journalists since 1700, with magazines added in the 18th century, radio and television in the 20th century, and the Internet in the 21st century. Early Journalism By 1400, businessmen in Italian and German cities were compiling hand written chronicles of important news events, and circulating them to their business connections. The idea of using a printing press for this material first appeared in Germany around 1600. The first gazettes appeared in German cities, notably the weekly Relation aller Fuernemmen und gedenckwürdigen Historien ("Collection of all distinguished and memorable news") in Strasbourg starting in 1605. The Avisa Relation oder Zeitung was published in Wolfenbüttel from 1609, and gazettes soon were established in Frankfurt (1615), Berlin (1617) and Hamburg (1618). -

Assure Funding New York
Assure Funding New York Pink Srinivas never paper so alow or earwig any arsonist disdainfully. Chrissy flopping his glyphographer lures proficiently or unrestrictedly after Jotham squats and facsimiled stoutly, araliaceous and armorial. How clubbish is Wiatt when weeping and palladous Pate bummed some statements? Trump out more effectively meet every year he suggested that they may legitimately respond realistically to new york life insurance solutions for encrypting and complimentary revenue sharing All prior to begin each new lives under PAUSE Policies Assure Uniform. NYSACHO's state budget priorities seek only to assure that compulsory health. Brennan Center on Twitter We need to unit the cleave of. Capital Projects City-OwnedCity Property The Office later The. We though not compromise on funding or school safety in consider home garden the. PROJECT the Total Safety Consulting. Choose one boces, esp sites monitor data are you! Power Assure raises 135M led by ABB Silicon Valley. Although it only because of antiquity is a profound impact on payroll, we expect business school districts is currently repaying your hard it? New York North Carolina State University Raleigh North Carolina. If you draft on information obtained from Google Translate you do so given your own risk The Office obtain the State Comptroller does not warrant and assure or. Cdc should we doing. Under great new proposal USDA would reorganize and go in reinvigorating the uniquely American system all public funding for agricultural education research. A Syndicate or Special farm Vehicle SPV to equity capital from a new habit can. Injured Patients and Families Compensation Fund Announces Premium Holiday On Wednesday. -

Government Advertising As an Indicator of Media Bias in India
Sciences Po Paris Government Advertising as an Indicator of Media Bias in India by Prateek Sibal A thesis submitted in partial fulfillment for the degree of Master in Public Policy under the guidance of Prof. Julia Cage Department of Economics May 2018 Declaration of Authorship I, Prateek Sibal, declare that this thesis titled, 'Government Advertising as an Indicator of Media Bias in India' and the work presented in it are my own. I confirm that: This work was done wholly or mainly while in candidature for Masters in Public Policy at Sciences Po, Paris. Where I have consulted the published work of others, this is always clearly attributed. Where I have quoted from the work of others, the source is always given. With the exception of such quotations, this thesis is entirely my own work. I have acknowledged all main sources of help. Signed: Date: iii Abstract by Prateek Sibal School of Public Affairs Sciences Po Paris Freedom of the press is inextricably linked to the economics of news media busi- ness. Many media organizations rely on advertisements as their main source of revenue, making them vulnerable to interference from advertisers. In India, the Government is a major advertiser in newspapers. Interviews with journalists sug- gest that governments in India actively interfere in working of the press, through both economic blackmail and misuse of regulation. However, it is difficult to gauge the media bias that results due to government pressure. This paper determines a newspaper's bias based on the change in advertising spend share per newspa- per before and after 2014 general election. -

Newspaper (Print Subscription) Daily Published News Items, Featured
Newspaper (Print Subscription) Daily published news items, featured articles; editorial reviews are one of the important communication tools for the education. National Law University, Delhi library subscribes to 16 newspapers in Print format. The Asian Age The Business Line The Economic Times The Hindu The Indian Express The Mint The Pioneer The Statesman The Times of India The Tribune The Financial Express The Guardian Dainik Jagran (Hindi) Mail Today Hindustan (Hindi) Newspapers (Online) National Law University, Delhi Library subscribes to commercial databases LexisNexis@ Academic which provides online access to More than 3,000 newspapers from around the globe? It can be retrieved through http://www.lexisnexis.com/hottopics/lnacademic/? The library also supports online news papers freely accessible. They can be read full text only just a click on mouse. Business Standard (EN) Deccan Herald (EN) Hindustan Times (EN) The Asian Age (EN) The Economic Times (EN) The Financial Express (EN) The Hindu (EN) The Hindu Business Line (EN) The Indian Express (EN) The Statesman (EN) The Telegraph (EN) The Times of India (EN) Newspaper Clippings Classified According To Topic The library also provides press clipping services to research community of NLUD. It provides clippings of news content or editorial opinions on law and legal studies and is arranged chronologically in subject folders. Some of the Subjects/Topics are as under: S.No. Subjects 1 Administrative of justice 2 Administrative Law 3 ADR 4 Affirmation Action 5 Air & Space -

Download Commencement Program
WESLEYAN UNIVERSITY z ONE HUNDRED AND EIGHTY-NINTH COMMENCEMENT v MAY TWENTY-SIXTH TWO THOUSAND AND TWENTY-ONE MIDDLETOWN, CONNECTICUT PROGRAM MARSHAL OF THE FACULTY PROCESSION* Francis W. Starr , Professor of Physics The audience is requested to rise as the graduates enter and to remain standing until the graduates are seated. ~ VICE MARSHALS OF THE FACULTY Octavio Flores-Cuadra , Adjunct Professor of Spanish WELCOME AND PRESIDENT’S REMARKS MICHAEL S. ROTH ’78 ~ PRESIDENT Kate Mullen , Adjunct Professor of Physical Education Suzanne B. OConnell , Professor of Earth and Environmental Sciences SENIOR CLASS WELCOME ASSISTANT FACULTY MARSHALS BRYAN LEONARD SIU YEUNG CHONG ’21 ~ FOR THE CLASS OF 2021 Stephen Angle , Mansfield Freeman Professor of East Asian Studies Richard S. Grossman , Professor of Economics RECOGNITION OF RETIRING FACULTY Scott G. Holmes , Professor of Molecular Biology and Biochemistry Tushar Irani , Associate Professor of Letters and Philosophy CONFERRING OF MASTER OF ARTS AD EUNDEM GRADUM William D. Johnston , John E. Andrus Professor of History CONFERRING OF TEACHING PRIZES Shona Kerr , Adjunct Professor of Physical Education NICOLE STANTON ~ PROVOST AND SENIOR VICE PRESIDENT FOR ACADEMIC AFFAIRS Amy MacQueen , Associate Professor of Molecular Biology and Biochemistry Sean McCann , Kenan Professor of the Humanities Ishita Mukerji , Fisk Professor of Natural Science CONFERRING OF HONORARY DOCTORATES Christopher Rasmussen , Associate Professor of Mathematics Sarah Ryan , Associate Professor of the Practice in Oral Communication ADDRESS REGINALD DWAYNE BETTS Charles A. Sanislow , Professor of Psychology Kari Weil , University Professor of Letters CONFERRING OF DEGREES MARSHALS OF THE SENIOR CLASS It is requested that there be no applause until all degrees have been conferred. -

Newspapers.Pdf
NEWSPAPERS AVAILABLE ONLINE Sl.No. Newspapers in Hindi 1. Amar Ujala 2. Dainik Bhaskar 3. Dainik Jagran (Kanpur) 4. Dainik Jagran (Delhi) 5. Deshbandhu 6. Haribhoomi 7. Hindustan 8. Jansatta 9. Navbharat Times (Delhi) 10. Punjab Kesari (Panipat) 11. Punjab Kesari (Delhi) 12. Rajasthan Patrika 13. Rashtriya Sahara 14. Tribune Sl.No. Newspapers in English 1. Asian Age 2. Business Line 3. Business Standard 4. Daily Excelsior 5. Deccan Chronicle 6. Economic Times 7. Hindu (Chennai) 8. Hindu (Delhi) 9. Hindustan Times 10. Indian Express 11. Indian Express (Chandigarh) 12. Indian Express (Chennai) 13. Lokmat 14. Mail Today 15. Millenium Post 16. New Indian Express (English) 17. Statesman (Delhi ) 18. Statesman (Kolkata) 19. The Pioneer 20. The Sentinel 21. The Shillong Times 22. The Telegraph 23. Times of India ( Delhi) 24. Times of India ( Mumbai) 25. Times of India (Ahmedabad) 26. Tribune SlNo. Newspapers (Regional) 1. Aajkal (Bengali) 2. Ajit(Punjabi) 3. Akhbar E Mashriq (Urdu) 4. Ananda Bazar Patrika (Bengali) 5. Andhra Jyoti (Telugu) 6. Andhra Prabha (Telugu) 7. Dainik Sahafat (Urdu) 8. Dinakaran (Tamil) 9. Dinamani(Tamil) 10. Dinathanthi (Tamil) 11. Eenadu (Malyalam) 12. Ganashakti (Bengali) 13. Gujrat Samachar (Gujarati) 14. Hamara Samaj 15. Hind Samachar ( Urdu) 16. In Dino(Urdu) 17. Jagbani (Punjabi) 18. Kerala Kaumudi(Malyalam) 19. Lok Satta (Marathi) 20. Lokmat Samachar (Marathi) 21. Lokmat Times (Marathi) 22. Maharashtra Times (Marathi) 23. Malyalam Manorama (Malyalam) 24. Mathrubhoomi (Malyalam) 25. Navshakti (Marathi) 26. Prajavani(Kannada) 27. Pratap (Urdu) 28. Pratidin (Bengali) 29. Rashtriya Sahara (Urdu) 30. Rojnama Rashtriya Sahara (Urdu) 31. Sahafat (Urdu) 32. Sakaal (Marathi) 33. -

Date: 14Th October, 2019 List of Coverage
COVERAGE DOSSIER COMPUTER SOCIETY OF INDIA Date: 14th October, 2019 List of Coverage S PUBLICATION HEADLINE Page L. NO. N O. 0 The Samaja 53rd Annual Convention of Computer Society 17 1 of India 0 The Prameya IT Convention in January 2020 09 2 0 The Pragativadi CSI Nation Convention from 16th January 05 3 0 The Nitidin First IT Convention to be held in KIIT 10 4 0 The First IT Convention to be held in January 04 5 Sarbasadharana 0 The Odisha First IT Convention to be held in 04 6 Bhaskar Bhubaneswar 0 The New Indian IT Convention held 2 7 Express (Bhuban eswar Express) 0 Orissa Post City to host 53rd IT Convention 02 8 0 The Statesman CSI’s 53rd annual convention on ‘digital 14 9 democracy’ to be held in BBSR 1 Political CSI-2020 to brainstorm on digital 03 0 Business Daily democracy, IT for change 1 The Pioneer BBSR’s first largest int’l IT convention on Jan 02 1 16-18 Capital 1 The Sunmarg Chief Minister to be awarded as CSI E-Ratna. 03 2 1 https://orissadiary. https://orissadiary.com/bhubaneswars-first- LINK 3 com largest-convention-held-january-2020-53rd- annual-convention-computer-society-india/ 1 https://www.orissa https://www.orissapost.com/city-to-host- LINK 4 post.com 53rd-it-convention-post-news-networ/ 1 https://www.dailypi https://www.dailypioneer.com/2019/state- LINK 5 oneer.com editions/bbsr-s-first-largest-int-l-it- convention-on-jan-16-18.html 1 https://www.mycity https://www.mycitylinks.in/odisha-capital-to- LINK 6 links.in/ host-csi-convention 1 https://www.pragat https://www.pragativadi.com/bhubaneswars- LINK 7 ivadi.com/ -

Sandspur, Vol. 28, No. 19, February 11, 1927
University of Central Florida STARS The Rollins Sandspur Newspapers and Weeklies of Central Florida 2-11-1927 Sandspur, Vol. 28, No. 19, February 11, 1927 Rollins College Find similar works at: https://stars.library.ucf.edu/cfm-sandspur University of Central Florida Libraries http://library.ucf.edu This Newspaper is brought to you for free and open access by the Newspapers and Weeklies of Central Florida at STARS. It has been accepted for inclusion in The Rollins Sandspur by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Rollins College, "Sandspur, Vol. 28, No. 19, February 11, 1927" (1927). The Rollins Sandspur. 2555. https://stars.library.ucf.edu/cfm-sandspur/2555 The Rollins Sandspur Published b:, Studenta of Rollin ■ Colleae Winter Park, Florida, Friday, February 11, 1927 Ne.19 HOLT SPEAKS ON JAPAN Major Morgan Rants 2nd Preliminaries For LEADERS T-0 BE HONORED PLAYS NATIONAL ANTHEM Against Non-Voters R. J. Sprague Contest ON INAUGURATION DAY Monday, February 7, being the oc- Ten more years till national ruin Friday morning, February 4, the Each year at its annual commence, asion of the funeral of the late Mika unless the younger generation does chapel exercises were exceptionally in ment Rollins College lects one or do of Japan, the chapel exercises were something to avert it, was the time teresting. All the students of Mrs. two outstanding men or women. who. turned over to President Holt that he given thi country by Major Morgan Grey's public speaking classe , who accordin to the judgment of the fac, might make some remarks about the last Thursday morning in his address ha.cl passed with honor the first pre, ulty and trustees, have because of Japanese and their emperor. -

Fellowship Programs Change
Fellowship Programs change. He is also a Named in honor of NED’s principal founders, former president Ronald Reagan and seasoned journal- the late congressman Dante Fascell, the Reagan-Fascell Democracy Fellows Pro- ist whose writings gram was established in 2001 by the U.S. Congress to enable democratic activists, have appeared in policy makers, scholars, and journalists from around the world to deepen their un- La Parole, Nouvel derstanding of democracy and enhance their ability to promote democratic change. Echo, and Le Temps, Reagan-Fascell fellowships are typically five months in duration and focus on the a newspaper he Dany Ayida political, social, economic, legal, and cultural aspects of democratic development. founded in 1999. Mr. Ayida remains an outspoken voice for In 2005–2006, the Reagan-Fascell Democracy Fellows Program hosted leading democratic human rights and democratization in Togo. activists, journalists, and scholars from countries in every region of the globe, including In 1996, he was recognized as the Togolese Argentina, Burma, India, Iran, Pakistan, Romania, Russia, Senegal, Slovakia, Journalist of the Year, and in 1999 he was South Africa, Togo, Turkey, the United States, Uganda, and Uzbekistan. runner-up for the CNN African Journalist of the Year Award. During his fellowship The Reagan-Fascell program seeks to deepen the knowledge, enrich the skills, broaden at NED, Mr. Ayida explored strategies for the perspectives, and strengthen the morale of some of the world’s most committed facilitating the transition from authoritar- and courageous democratic practitioners, journalists, and scholars. Fellows are in resi- ian rule to multiparty democracy in Togo. -

Press in Malabar Before 1947: a Historical Review
JASC: Journal of Applied Science and Computations ISSN NO: 1076-5131 PRESS IN MALABAR BEFORE 1947: A HISTORICAL REVIEW Anoop V.S. Ph.D. Research Scholar (Reg. No.18113161081006) Department of History & Research Centre, Scott Christian College (Autonomous), Nagercoil – 629 003. Affiliated to Manonmaniam Sundaranar University, Abishekapatti, Tirunelveli – 627 012, Tamil Nadu, India Abstract: The press is the most powerful force of social emancipation. The history of Press in India is deeply related with advent of colonialism and imperialism. It was the missionaries who took interest to the introduction of press in India. They introduced it as part of the propagation of Christianity. But later it became a most powerful tool to root out colonialism in India. It has played a significant role in the rise and growth of Indian National Movement. History of Indian press is linked to the history of India’s freedom struggle. In Kerala attempts made by missionaries for the spread of Christianity was major factor responsible for the growth of press in Kerala. Later it became shaping force of Kerala society.This paper examines the development and growth of press in Malabar region of Kerala. Key words: press, colonialism, culture, human rights, mobilization Introduction The press is the most powerful and effective mechanism to bring desired and progressive changes in the society. It playscrucial in the formation of the behaviour pattern of the people. History always remembers us by examples that in all major world events like revolutions, world wars, agitations, political developments,and culturalformation etc. the role of press is important. The press can change its course and results.