Information Technology Audit Armed Forces of Malta
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PO Box. 42, Malta International Airport, Luqa LQA 5001 T : (+356)
Response Document to Notices of Proposed Amendment No. 2008-17A and NPA No. 2008-17B Comments Prior to an examination of the proposed amendments to Part FCL as proposed in NPA No. 2009-17B, due regard must be had to the contents of the Draft Opinion [NPA No. 2008-17A]. It is clearly understood, as declared in paragraph 2 of the Draft Opinion, that : “The European Aviation Safety Agency (the Agency) is directly involved in the rule -shaping process” in accordance with the functions set out in the Basic Regulation 1. The European Aviation Safety Agency, being an Agency of the European Union, does not have the function to enact law, however it is understood to be a duty of the Agency to present to the institution of the European Union a view of the matter being addressed which is correct and to forward proposals which are coherent with EU policy, in particular that any measures adopted are in conformity with the principle of proportionality. The aims pursued are the subject of the Basic Regulation – in a generic manner – as well as the Terms of Reference ToR FCL.001 reproduced in the Draft Opinion [NPA No. 2008-17A].These terms of reference are, inter alia : - “to establish in the form of essential requirements, high level safety objectives to be achieved by the regulations of pilot licensing” - “to require all pilots operating in the Community to hold a licence attesting compliance with common safety requirement covering their theoretical and practical knowledge, as well as they physical fitness” Whereas AOPA Malta agrees with the adoption of a harmonized approach to regulation on a European level to address the issue of pilot licensing in accordance with the terms of reference, it emphasis that all such regulation must conform with the principle of proportionality. -
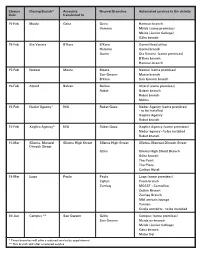
Closure Closing Branch* Accounts Nearest Branches Automated Services in the Vicinity Date Transferred to 15-Feb Msida Gωira G
Closure Closing Branch* Accounts Nearest Branches Automated services in the vicinity Date transferred to 15-Feb Msida GΩira GΩira Óamrun branch Óamrun Msida (same premises) Msida (Junior College) GΩira branch 15-Feb Sta Venera B'Kara B'Kara Qormi Head office Óamrun Qormi branch Qormi Sta Venera (same premises) B'Kara branch Óamrun branch 15-Feb Naxxar Mosta Mosta Naxxar (same premises) San Ìwann Mosta branch B'Kara San Ìwann branch 15-Feb Attard Balzan Balzan Attard (same premises) Rabat Balzan branch Rabat branch Mdina 15-Feb Nadur Agency* N/A Rabat Gozo Nadur Agency (same premises) - to be installed Xag˙ra Agency Rabat branch 15-Feb Xag˙ra Agency* N/A Rabat Gozo Xag˙ra Agency (same premises) Nadur agency - to be installed Rabat branch 15-Mar Sliema, Manwel Sliema High Street Sliema High Street Sliema, Manwel Dimech Street Dimech Street GΩira Sliema High Street Branch GΩira branch The Point The Plaza Carlton Hotel 15-Mar Luqa Paola Paola Luqa (same premises) Ûejtun Paola branch Ûurrieq MCAST - Corradino Ûejtun Branch Ûurrieq Branch MIA arrivals lounge Tarxien Gudja outskirts - to be installed 30-Jun Campus ** San Ìwann ÌΩira Campus (same premises) San Ìwann Msida ex-branch Msida (Junior College) GΩira branch Mater Dei * These branches will offer a reduced service by appointment ** This branch will offer a reduced service Data tal- Ferg˙a li ser Kontijiet ser ji©u L-eqreb ferg˙at Servizzi awtomatizzati g˙eluq ting˙alaq* trasferiti lejn fil-qrib 15-Frar L-Imsida Il-GΩira Il-GΩira Ferg˙a tal-Óamrun Il-Óamrun L-Imsida (fl-istess post) L-Imsida -
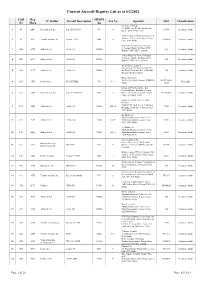
To Access the List of Registered Aircraft As on 2Nd August
Current Aircraft Registry List as at 8/2/2021 CofR Reg MTOM TC Holder Aircraft Description Pax No Operator MSN Classification No Mark /kg Cherokee 160 Ltd. 24, Id-Dwejra, De La Cruz Avenue, 1 41 ABW Piper Aircraft Inc. Piper PA-28-160 998 4 28-586 Aeroplane (land) Qormi QRM 2456, Malta Malta School of Flying Company Ltd. Aurora, 18, Triq Santa Marija, Luqa, 2 62 ACL Textron Aviation Inc. Cessna 172M 1043 4 17260955 Aeroplane (land) LQA 1643, Malta Airbus Financial Services Limited 6, George's Dock, 5th Floor, IFSC, 3 1584 ACX Airbus S.A.S. A340-313 275000 544 Aeroplane (land) Dublin 1, D01 K5C7,, Ireland Airbus Financial Services Limited 6, George's Dock, 5th Floor, IFSC, 4 1583 ACY Airbus S.A.S. A340-313 275000 582 Aeroplane (land) Dublin 1, D01 K5C7,, Ireland Air X Charter Limited SmartCity Malta, Building SCM 01, 5 1589 ACZ Airbus S.A.S. A340-313 275000 4th Floor, Units 401 403, SCM 1001, 590 Aeroplane (land) Ricasoli, Kalkara, Malta Nazzareno Psaila 40, Triq Is-Sejjieh, Naxxar, NXR1930, 001-PFA262- 6 105 ADX Reno Psaila RP-KESTREL 703 1+1 Microlight Malta 12665 European Pilot Academy Ltd. Falcon Alliance Building, Security 7 107 AEB Piper Aircraft Inc. Piper PA-34-200T 1999 6 Gate 1, Malta International Airport, 34-7870066 Aeroplane (land) Luqa LQA 4000, Malta Malta Air Travel Ltd. dba 'Malta MedAir' Camilleri Preziosi, Level 3, Valletta 8 134 AEO Airbus S.A.S. A320-214 75500 168+10 2768 Aeroplane (land) Building, South Street, Valletta VLT 1103, Malta Air Malta p.l.c. -

Report of the Secretary-General, Implementation of Resolution 2437
United Nations S/2019/711 Security Council Distr.: General 5 September 2019 Original: English Implementation of resolution 2437 (2018) Report of the Secretary-General I. Introduction 1. The present report is submitted pursuant to paragraph 3 of Security Council resolution 2437 (2018), in which the Council renewed its request to me to report on the implementation of resolution 2240 (2015), in particular the implementation of paragraphs 7 to 10 of that resolution. 2. The report covers developments since my previous report of 31 August 2018 (S/2018/807) until 31 August 2019. The information and observations herein are based on submissions by Member States, relevant international and regional bodies and United Nations entities. II. Smuggling of migrants and trafficking in persons in the Mediterranean Sea off the coast of Libya 3. Since the issuance of my previous report, the world continues to face the grim reality that the Mediterranean Sea remains a high-volume thoroughfare for the smuggling of and trafficking in refugees and migrants. In 2019, thousands have again perished or gone missing en route or have been returned to situations of grave harm and uncertainty. In the period from 1 September 2018 to 31 July 2019, the Office of the United Nations High Commissioner for Refugees (UNHCR) and the International Organization for Migration (IOM) recorded a total of 82,236 arrivals of refugees and migrants by sea in Europe, a 26 per cent decrease from the same period in 2018, when approximately 111,200 individuals were recorded to have arrived in Europe by sea. For the period from September 2018 to July 2019, 1,485 refugees and migrants were recorded to have died or gone missing at sea on all the Mediterranean routes, including 736 on the so-called central Mediterranean route from North Africa to Italy and Malta. -

On the Way Towards a European Defence Union - a White Book As a First Step
DIRECTORATE-GENERAL FOR EXTERNAL POLICIES POLICY DEPARTMENT STUDY On the way towards a European Defence Union - A White Book as a first step ABSTRACT This study proposes a process, framed in the Lisbon Treaty, for the EU to produce a White Book (WB) on European defence. Based on document reviews and expert interviewing, this study details the core elements of a future EU Defence White Book: strategic objectives, necessary capabilities development, specific programs and measures aimed at achieving the improved capabilities, and the process and drafting team of a future European WB. The study synthesizes concrete proposals for each European institution, chief among which is calling on the European Council to entrust the High Representative with the drafting of the White Book. EP/EXPO/B/SEDE/2015/03 EN April 2016 - PE 535.011 © European Union, 2016 Policy Department, Directorate-General for External Policies This paper was requested by the European Parliament's Committee on Foreign Affairs and the Sub-Committee on Security and Defence. English-language manuscript was completed on 18 April 2016. Translated into FR/ DE. Printed in Belgium. Author(s): Prof. Dr. Javier SOLANA, President, ESADE Center for Global Economy and Geopolitics, Spain Prof. Dr. Angel SAZ-CARRANZA, Director, ESADE Center for Global Economy and Geopolitics, Spain María GARCÍA CASAS, Research Assistant, ESADE Center for Global Economy and Geopolitics, Spain Jose Francisco ESTÉBANEZ GÓMEZ, Research Assistant, ESADE Center for Global Economy and Geopolitics, Spain Official Responsible: Wanda TROSZCZYNSKA-VAN GENDEREN, Jérôme LEGRAND Editorial Assistants: Elina STERGATOU, Ifigeneia ZAMPA Feedback of all kind is welcome. Please write to: [email protected]. -

Following in the Footsteps of St. Paul
YOUTH PILGRIMAGE TO MALTA JULY 26th - 31st 2020 Following in the footsteps of St. Paul WHY PILGRIMAGE Pilgrimage could be described as a meaningful journey to a sacred place. It provides the opportunity to step out of the non-stop busyness of our lives, to seek a time of quiet and reflection. It is a time of simply ‘being’ rather than always ‘doing’. For Christians, the reasons for going on pilgrimage include setting aside time for God; to help discern his plan; to be strengthened in our faith; and to feel inspired by the communion of saints who have gone before us. Pilgrimage can also be a highly sociable activity, allowing us to enjoy the company of others we meet. It gives us the chance re-energise mentally, physically and spiritually. WHY A PILGRIMAGE TO MALTA In between international World Youth Days, the Diocesan Youth Service runs a pilgrimage. In recent years, we have taken groups to York, Iona, and Santiago de Compostela. In this ‘Year of the Word’ we will be going to Malta to follow in the footsteps of one of the great writers of the epistles in the New Testament – St. Paul. It was in 60 AD, that St. Paul was on the way to Rome, to be tried when he was shipwrecked just off the coast of Malta during a storm. The people of Malta looked after the crew and St. Paul until they could continue with their journey. During this time, St. Paul preached the Gospel to the locals, who at the time were under Roman rule. -
Malta & Gozo Directions
DIRECTIONS Malta & Gozo Up-to-date DIRECTIONS Inspired IDEAS User-friendly MAPS A ROUGH GUIDES SERIES Malta & Gozo DIRECTIONS WRITTEN AND RESEARCHED BY Victor Paul Borg NEW YORK • LONDON • DELHI www.roughguides.com 2 Tips for reading this e-book Your e-book Reader has many options for viewing and navigating through an e-book. Explore the dropdown menus and toolbar at the top and the status bar at the bottom of the display window to familiarize yourself with these. The following guidelines are provided to assist users who are not familiar with PDF files. For a complete user guide, see the Help menu of your Reader. • You can read the pages in this e-book one at a time, or as two pages facing each other, as in a regular book. To select how you’d like to view the pages, click on the View menu on the top panel and choose the Single Page, Continuous, Facing or Continuous – Facing option. • You can scroll through the pages or use the arrows at the top or bottom of the display window to turn pages. You can also type a page number into the status bar at the bottom and be taken directly there. Or else use the arrows or the PageUp and PageDown keys on your keyboard. • You can view thumbnail images of all the pages by clicking on the Thumbnail tab on the left. Clicking on the thumbnail of a particular page will take you there. • You can use the Zoom In and Zoom Out tools (magnifying glass) to magnify or reduce the print size: click on the tool, then enclose what you want to magnify or reduce in a rectangle. -

Reference Sheet
TACTICALL NAVY REFERENCES Internal Communication External Communication TactiCall gives you complete control and fast access to all net- TactiCall is a perfect match for Task- or coalition force operations, works on board your vessel. Be it Functional Nets including teleph- including other military arms. SOF teams, air force, marine detach- ony, public address, entertainment systems and the like or Fighting ments and even civil and NGO agencies can be important players Nets handling alarms, broadcasts and orders, weapon teams or in the operation. More often than not, this setup includes a multi- mission control. tude of different frequency bands, networks and radio equipment. TactiCall will integrate all these into one simple and easy to use TactiCall is highly flexible and scalable, it is platform independent solution that permits everybody to reach each other regardless of and will integrate seamlessly into your combat management sys- equipment and technology used. tem of choice. In other words TactiCall lets you control all internal communication on board your vessel and with features such as TactiCall will allow key features for modern day operations like red/ record and playback helps you log and later analyze your commu- black separation, multi-level security operations, global public ad- nication flows. dress and allowing government or task force commanders to com- municate directly with whoever needs to be addressed in a given situation - facilitating a much smoother and more rapid “Statement of No Objections” chain. Contact Porten -

Following Paul from Shipwreck on Malta to Martyrdom in Rome MALTA • SICILY • ITALY Led by Dr
Following Paul from Shipwreck on Malta to Martyrdom in Rome MALTA • SICILY • ITALY Led by Dr. Carl Rasmussen MAY 11-22, 2021 organized by Following Paul from Shipwreck on Malta to Martyrdom in Rome / May 11-22, 2021 Malta Following Paul from Shipwreck on Malta to Martyrdom in Rome MAY 11-22, 2021 Fri 14 May Ferry to POZZALLO (SICILY) - SYRACUSE – Ferry to REGGIO CALABRIA Early check out, pick up our box breakfasts, meet the English-speaking assistant at our hotel and transfer to the port of Malta. 06:30am Take a ferry VR-100 from Malta to Pozzallo (Sicily) 08:15am Drive to Syracuse (where Paul stayed for three days, Acts 28.12). Meet our guide and visit the archeological park of Syracuse. Drive to Messina (approx. 165km) and take the ferry to Reggio Calabria on the Italian mainland (= Rhegium; Acts 28:13, where Paul stopped). Meet our guide and visit the Museum of Magna Grecia. Check-in to our hotel in Reggio Calabria. Dr. Carl and Mary Rasmussen Dinner at our hotel and overnight. Greetings! Mary and I are excited to invite you to join our handcrafted adult “study” trip entitled Following Paul from Shipwreck on Malta to Sat 15 May PAESTUM - to POMPEII Martyrdom in Rome. We begin our tour on Malta where we will explore the Breakfast and checkout. Drive to Paestum (435km). Visit the archeological bays where the shipwreck of Paul may have occurred as well as the Island of area and the museum of Paestum. Paestum was a major ancient Greek city Malta. Mark Gatt, who discovered an anchor that may have been jettisoned on the coast of the Tyrrhenian Sea in Magna Graecia (southern Italy). -

IMLI VISITING FELLOWS Academic Year 2019 – 2020
IMLI VISITING FELLOWS Academic year 2019 – 2020 Mr. C. Abela (Malta, Senior Project Officer for International Relations, European Maritime Safety Agency (EMSA)) Prof. I. Arroyo (Spain, Father of Modern Spanish Maritime Law) Prof. A. Blanco-Bazan (Argentina, International Lawyer & Consultant) Mr. L. Barchue (Liberia, Assistant Secretary-General/Director, Department for Member State Audit and Implementation Support, International Maritime Organization (IMO)) Prof. C. J. Cheng (China, Secretary-General, Xiamen Academy of International Law) Dr. A. Fenech (Malta, Vice-President of the Comité Maritime International (CMI)) Prof. M. Fitzmaurice (Poland, Queen Mary University of London) Ms. G. Grant (Canada, Alternative Representative of Canada to the International Maritime Organization (IMO)) Mr. M. Ghorbel (Tunisia, Technical Officer of Maritime Safety Division, International Maritime Organization (IMO)) Dr. P. J. S. Griggs CBE (UK, Former President, Comité Maritime International (CMI)) Dr. A. Henriksen (Germany, Lawyer and Certified Specialist in Commercial and Corporate Law) Dr. X. Hinrichs (Germany, Registrar, International Tribunal for the Law of the Sea (ITLOS)) Dr. J. Hoffmann (Germany, Chief, Trade Logistics Branch Division on Technology and Logistics, UNCTAD) Dr. Y. Ishii (Japan, Associate Professor, National Defence Academy of Japan) Prof. A. Kanehara (Japan, Professor, Faculty of Law, Sophia University, Member of IMLI Governing Board) Mr. N. Kanehara (Japan, Former Deputy Secretary-General, National Security Secretariat of the Prime Minister’s Office) Mr. F. Kenney (USA, Director, Legal Affairs and External Relations Division, International Maritime Organization (IMO)) Ms. S. Kuma (Japan, Executive Director, Yokohama-Kawasaki International Port) 1 Mr. A. Kennedy (UK, Global Head of Dispute Resolution and Compliance, Lloyd’s Register) Mrs. K. -

Malta 2017 Crime & Safety Report
Malta 2017 Crime & Safety Report Overall Crime and Safety Situation U.S. Embassy Valletta does not assume responsibility for the professional ability or integrity of the persons or firms appearing in this report. The ACS Unit cannot recommend a particular individual or location and assumes no responsibility for the quality of service provided. THE U.S. DEPARTMENT OF STATE HAS ASSESSED VALLETTA AS BEING A MEDIUM- THREAT LOCATION FOR CRIME DIRECTED AT OR AFFECTING OFFICIAL U.S. GOVERNMENT INTERESTS. Please review OSAC’s Malta-specific webpage for proprietary analytic reports, Consular Messages, and contact information. Crime Threats Malta is a generally safe country that receives numerous foreign tourists on a yearly basis. However, crimes of opportunity and violent crime do occur. Most street crimes are non-violent and non-confrontational and range from scams to petty theft. Theft of cell phones, computers, money, jewelry, and iPods is common. Visitors should keep these items out of sight and only use them in safe locations. Most street criminals are unarmed and are not prone to gratuitous violence. Victims of street crime are often inattentive targets of opportunity. Women should keep purses zipped and in front of them. Wear the shoulder straps of bags across your chest. Keep your money, credit cards, wallet, and other valuables in your front pockets. In 2016, crime statistics revealed that theft was the predominate criminal offense, making up over half of the crimes committed in Malta. Assaults numbered under 1,000, with the peak being June, July, and August (height of tourism season). Nationwide crime rates are higher in areas frequented by tourists to include: St. -

Annual Report 2017 Contents
ANNUAL REPORT 2017 CONTENTS 3 4 9 CEO Water Water Report Resources Quality 14 20 32 Compliance Network Corporate Infrastructure Services Directorate 38 45 48 Strategic Human Unaudited Information Resources Financial Directorate Statement 2017 ANNUAL REPORT CEO REPORT CEO Report 2017 was a busy year for the Water Services quality across Malta. Secondly, RO plants will be Corporation, during which it worked hard to become upgraded to further improve energy efficiency and more efficient without compromising the high quality production capacity. Furthermore, a new RO plant service we offer our customers. will be commissioned in Gozo. This RO will ensure self-sufficiency in water production for the whole During a year, in which the Corporation celebrated island of Gozo. The potable water supply network to its 25th anniversary, it proudly inaugurated the North remote areas near Siġġiewi, Qrendi and Haż-Żebbuġ Wastewater Treatment Polishing Plant in Mellieħa. will be extended. Moreover, ground water galleries This is allowing farmers in the Northern region to will also be upgraded to prevent saline intrusion. benefit from highly polished water, also known as The project also includes the extension of the sewer ‘New Water’. network to remote areas that are currently not WSC also had the opportunity to establish a number connected to the network. Areas with performance of key performance indicator dashboards, produced issues will also be addressed. inhouse, to ensure guaranteed improvement. These Having only been recently appointed to lead the dashboards allow the Corporation to be more Water Services Corporation, I fully recognize that the efficient, both in terms of performance as well as privileges of running Malta’s water company come customer service.