Google Pixel Phones on Android 11 Administrator Guidance Documentation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Google ARCORE
Google ARCORE Nisfu Asrul Sani @ Lab Langit 9 - PENS 20 - 22 November 2017 environtment Setting up your development environment Install the Android SDK version 7.0 (API Level 24) or higher. To install the Android SDK, install Android Studio. To update the Android SDK, use the Android SDK Manager tool in Android Studio. Install Unity 2017.2 Beta 11 or higher, with the Android Build Support component. For more info, see Downloading and Installing Unity. You will need to get the ARCore SDK for Unity. You can either: Download the SDK Preview for Unity and extract it. -or- Clone the repository with the following command: git clone https://github.com/google-ar/arcore-unity-sdk.git Prepare your device You must use a supported, physical device. ARCore does not support virtual devices such as the Android Emulator. To prepare your device: Enable developer options Enable USB debugging Install the ARCore Service on the device: Download the ARCore Service Connect your Android device to the development machine with a USB cable Install the service by running the following adb command: adb install -r -d arcore-preview.apk https://play.google.com/store/apps/details?id=com.un Additional ity3d.genericremote Supported Devices ARCore is designed to work on a wide variety of qualified Android phones running N and later. During the SDK preview, ARCore supports the following devices: Google Pixel, Pixel XL, Pixel 2, Pixel 2 XL Samsung Galaxy S8 (SM-G950U, SM-G950N, SM- G950F, SM-G950FD, SM-G950W, SM-G950U1) Initially, ARCore will only work with Samsung’s S8 and S8+ and Google’s Pixel phone, but by the end of the year, Google promised to have support for 100 million Android phones, including devices from LG, Huawei and Asus, among others. -

Nokia Lumia 521 User Manual
www.nokia.com Product and safety information Copyright © 2013 Nokia. All rights reserved. Nokia and Nokia Connecting People are trademarks or registered trademarks of Nokia Corporation. Other product and company names mentioned herein may be trademarks or trade names of their respective owners. The phone supplied in the sales package may differ from that shown. Specifications subject to change without notice. Printed in China. 9260765 Ver. 1.0 03/13 Quick Guide Psst... Nokia Lumia 521 This guide isn't all there is... For the online user guide, even more info, user Contents guides in another language, and Safety 3 troubleshooting help, go to www.nokia.com/ support. Keys and parts 4 Check out the videos at www.youtube.com/ Get started 5 NokiaSupportVideos. Get the basics 9 For info on Nokia Service terms and Privacy policy, go to www.nokia.com/privacy. Try out the touch screen 10 First start-up Take your friends with you 15 Your new phone comes with great features that will be installed when you start your phone Messages 17 for the first time. Allow some minutes for your Mail 21 phone to be ready. Take photos and share 25 HERE Maps 27 Browse the web 29 Feature-specific instructions 36 Product and safety information 38 2 Stop using the device until the glass is replaced by Safety qualified service personnel. Read these simple guidelines. Not following them may be dangerous or illegal. For further info, read the PROTECT YOUR HEARING complete user guide. To prevent possible hearing damage, do not listen at high volume levels for long periods. -

RADA Sense Mobile Application End-User Licence Agreement
RADA Sense Mobile Application End-User Licence Agreement PLEASE READ THESE LICENCE TERMS CAREFULLY BY CONTINUING TO USE THIS APP YOU AGREE TO THESE TERMS WHICH WILL BIND YOU. IF YOU DO NOT AGREE TO THESE TERMS, PLEASE IMMEDIATELY DISCONTINUE USING THIS APP. WHO WE ARE AND WHAT THIS AGREEMENT DOES We Kohler Mira Limited of Cromwell Road, Cheltenham, GL52 5EP license you to use: • Rada Sense mobile application software, the data supplied with the software, (App) and any updates or supplements to it. • The service you connect to via the App and the content we provide to you through it (Service). as permitted in these terms. YOUR PRIVACY Under data protection legislation, we are required to provide you with certain information about who we are, how we process your personal data and for what purposes and your rights in relation to your personal data and how to exercise them. This information is provided in https://www.radacontrols.com/en/privacy/ and it is important that you read that information. Please be aware that internet transmissions are never completely private or secure and that any message or information you send using the App or any Service may be read or intercepted by others, even if there is a special notice that a particular transmission is encrypted. APPLE APP STORE’S TERMS ALSO APPLY The ways in which you can use the App and Documentation may also be controlled by the Apple App Store’s rules and policies https://www.apple.com/uk/legal/internet-services/itunes/uk/terms.html and Apple App Store’s rules and policies will apply instead of these terms where there are differences between the two. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

HEATING/COOLING BEVERAGE BASE with WIRELESS CHARGING Item No
HEATING/COOLING BEVERAGE BASE WITH WIRELESS CHARGING Item No. 207196 User Guide Thank you for purchasing the Sharper Image Heating/Cooling Beverage Base with Wireless Charging. Please take a moment to read this guide and store it for future reference. FEATURES • Keeps coffee mug hot or soda can cold • Charges your Qi-enabled phone without cables or wires • Quick charge capable (10W and 7.5W) • Standard charge 5W • Auto sensor supplies the correct power for your device • Automatic safety shut-off after 4 hours (charging) CONTENTS OF BOX • 1X Mug • 1X Base Unit • 1 Power Adapter OPERATION 1. Connect the power adapter to the device. 2. Plug the power adapter into an AC outlet. 3. Place the included mug or your beverage can on top of the heating/cooling element, properly aligning it with the bottom of the container. 4. Press the power button ONCE to activate COOLING. Press a SECOND TIME to activate HEATING. 5. Place your wireless charging device on the charging surface. The Qi wireless charging pad will begin charging automatically. NOTE: There is no On/Off Switch for the wireless charger. Your phone will charge automatically if it is compatible with wireless charging. See the Compatibility list below or consult your device’s owner’s manual to check if your device is Qi enabled for wireless charging. For safety purposes, the Qi wireless charging pad will shut off automatically after 4 hours. - 1 - COMPATIBILITY Qi wireless charging is compatible with most newer phones, including: • Apple iPhone 8, 8 Plus, X, XS, XS Max, XR, 11, 11 Pro, 11 -

English-P360-Deductible-Tool.Pdf
T-Mobile® Deductible and Fee Schedule Alcatel Tier BlackBerry Tier Huawei Tier 9810, 9900 3T 8 Comet Q10 665 3 Prism, Prism II Z10 768 Sonic 4G A30 Priv 4 Summit 1 Aspire Tap Evolve webConnect Fierce XL Coolpad Tier Fierce, Fierce 2, Fierce 4 1 Catalyst GO FLIP myTouch 2 LINKZONE Defiant Pixi 7 Rogue 1 S7 PRO 3 POP 7 Snap POP Astro Surf REVVL REVVL Plus 2 Kyocera Tier Soul Hydro WAVE 1 IDOL 4S 3 Dell Tier Rally Streak 7 2 DuraForce PRO, DuraForceXD 3 Apple Tier Ericsson Tier iPad iPad Air 2 World 1 LG Tier iPad Mini, iPad Mini 2, iPad Mini 4 450 iPhone 4, iPhone 4s 3 GARMIN Tier Aristo iPhone 5, iPhone 5c, iPhone 5s Aristo 2 PLUS iPhone 6s Garminfone 3 dLite iPhone SE GS170 Watch Series 3 1 GEOTAB Tier K7, K10 K20 Plus iPad Air SyncUP FLEET 1 Leon iPad Mini 3 Optimus L90 iPad Pro 9.7 Sentio iPhone 6 4 GOOGLE Tier iPhone 6s Plus Pixel 3a DoublePlay iPhone 7, iPhone 7 Plus Pixel 3a XL 3 Watch Series 4 G Pad F 8.0 G Pad X2 8.0, G Pad X2 8.0 Plus Pixel 3 4 G Pad X 8.0 iPad Pro 10.5-inch Pixel 3 XL G Stylo iPad Pro 11-inch G2 iPad Pro 12.9-inch G2x iPhone 6 Plus HTC Tier1 5 K30 2 iPhone 8, iPhone 8 Plus Desire iPhone X Lion iPhone XR myTouch iPhone XS, iPhone XS MAX Amaze 4G Optimus F3, F3Q, F6, L9, T Dash 3G Stylo 2 PLUS, Stylo 3 PLUS G2 Stylo 4 ASUS Tier HD2, HD7 V20 life Google Nexus 7 2 myTouch 3G 1.2, myTouch 3G slide 2 G3, G5, G6 myTouch 4G G-Slate One M9 Nexus 4, Nexus 5 3 BlackBerry Tier One S P Plus Radar 4G Q7+ 7100T, 7105T Shadow 7230, 7290 Wildfire S G Flex 8120, 8520 G7 9780 Bold 2 4 10 G8 Classic Flyer V30 Curve myTouch V10 myTouch 4G Slide 3 5 9700 Bold 3 One V30+ Sensation 4G Windows Phone 8X Please note: If you switch your device to one that is classified in another tier, the monthly charge for your new tier will be reflected on your T-Mobile bill. -

KONYKS Interrupteur Pour Volets Roulants Vollo KONYKS
KONYKS Interrupteur pour volets roulants Vollo KONYKS Contrôlez votre interrupteur à la voix ou à distance grâce à votre smartphone. GENCODE : 3770008652316 REF. : KONYVOLLO Caractéristiques Interrupteur pour volets roulants Vollo KONYKS : - Interrupteur encastrable pour volet roulants (installation filaire, fonctionne aussi pour rideaux motorisés) - Pilotage à la voix : avec Google Home ou Alexa vous pilotez les volets très simplement: «OK Google, ouvre les volets, Alexa ferme les volets» - Contrôle depuis son Smartphone, de n'importe où dans le monde grâce à l'appli Konyks iOS et Android - Automatisez facilement: Fermer les volets au coucher du soleil, ou à une heure précise, programmer ouverture et fermetures en votre absence, fermer les volets s'il gèle dehors etc.... - Spécifications techniques : Nécessite un réseau Wifi 2.4 Ghz 802.11 b/g/n AC 110-240 V - 50-60 Hz 3A 600W max Matériau ABS retardateur de flamme Application en français avec Widgets, Programmation horaire, compte à rebours, scénarios et automatisations, compatible raccourcis Siri Atout Compatible Google Home ou Alexa Fermeture automatique des volets programmée Compatible avec les smartphones sous Android 4.1 et versions ultérieures Compatibilité ou iOS 8 et versions ultérieures Dimensions 86 x 86 x 35 mm Couleur Blanc Poids net 148 g Contenu du pack 1 Interrupteur pour volets roulants Vollo KONYKS MOBILES COMPATIBLES ACER ICONIA TAB B1-A71 / LIQUID E1 / LIQUID E2 / LIQUID Z2 / LIQUID Z200 / LIQUID Z3 ALCATEL 1 (5033) / 1X (5059) / 1X 2019 (5008) / 3 (5052) / 3C (5026) -

Step 1(To Be Performed on Your Google Pixel 2 XL)
For a connection between your mobile phone and your Mercedes-Benz hands-free system to be successful, Bluetooth® must be turned on in your mobile phone. Please make sure to also read the operating and pairing instructions of the mobile phone. Please follow the steps below to connect your mobile phone Google Pixel 2 XL with the mobile phone application of your Mercedes-Benz hands-free system using Bluetooth®. Step 1(to be performed on your Google Pixel 2 XL) Step 2 To get to the telephone screen of your Mercedes-Benz hands-free system press the Phone icon on the homescreen. Step 3 Select the Phone icon in the lower right corner. Step 4 Select the “Connect a New Device” application. Page 1 of 3 Step 5 Select the “Start Search Function” Step 6 The system will now search for any Bluetooth compatible phones. This may take some time depending on how many devices are found by the system. Step 7 Once the system completes searching select your mobile phone (example "My phone") from the list. Step 8 The pairing process will generate a 6-digit passcode and display it on the screen. Verify that the same 6 digits are shown on the display of your phone. Step 9 (to be performed on your Google Pixel 2 XL) There will be a pop-up "Bluetooth Request: 'MB Bluetooth' would like to pair with your phone. Confirm that the code '### ###' is shown on 'MB Bluetooth'. " Select "Pair" on your phone if the codes match. Page 2 of 3 Step 10 After the passcode is verified on both the mobile and the COMAND, the phone will begin to be authorized. -

IRAC Test Report
1 L NASA Technical Memorandum 878 13 IRAC Test Report . Gallium Doped Silicon Band I1 READ NOISE AND DARK CURRENT Gerald Lamb, Peter Shu, John Mather, Audrey Ewin, and Jeffrey Bowser JANUARY 1987 NASA Technical Memorandum 878 13 IRAC Test Report Gallium Doped Silicon Band I1 READ NOISE AND DARK CURRENT Gerald Lamb, Peter Shu, John Mather, Audrey Ewin NASA Go&rd Space Flight Center Greenbelt, Maryland Jeffrey Bowser Science Applications Research Corp. a National Aeronautics and Space Ad ministration Goddard Space Flight Center Greenbelt, Maryland 20771 1987 TABLE OF CONTENTS Page Introduction .................................................... 1 Background ..................................................... Array ........................................................ 5 Unit Cell Performance ........................................... 8 Dewar ......................................................... 17 Electronic .................................................... 23 Timing Generator .............................................. 23 Warm Preamplifier .............................................. 23 Analog Signal Processor ........................................... 25 Signal Response ............................................... 26 Noise Response ............................................... 28 Digital Electronics ................................................. 31 Software ...................................................... 32 Experimental Procedure .............................................. 33 Read Noise ................................................... -
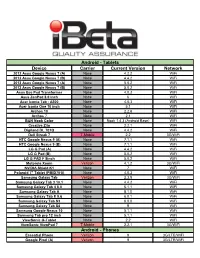
Ibeta-Device-Invento
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel (C) Factory Unlocked 9 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel -
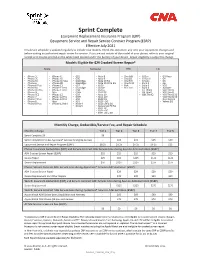
Sprint Complete
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) Effective July 2021 This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair* Apple Samsung HTC LG • iPhone 5 • iPhone X • GS5 • Note 8 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone XS • GS6 • Note 9 • One E8 • G Flex II • G4 • iPhone 5S • iPhone XS Max • GS6 Edge • Note 20 5G • One M9 • G Stylo • G5 • iPhone 6 • iPhone XR • GS6 Edge+ • Note 20 Ultra 5G • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 11 • GS7 • GS10 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone 11 Pro • GS7 Edge • GS10e • HTC U11 • Stylo 6 • X power • iPhone 6S Plus • iPhone 11 Pro • GS8 • GS10+ • G7 ThinQ • V40 ThinQ • iPhone SE Max • GS8+ • GS10 5G • G8 ThinQ • V50 ThinQ • iPhone SE2 • iPhone 12 • GS9 • Note 10 • G8X ThinQ • V60 ThinQ 5G • iPhone 7 • iPhone 12 Pro • GS9+ • Note 10+ • V60 ThinQ 5G • iPhone 7 Plus • iPhone 12 Pro • A50 • GS20 5G Dual Screen • iPhone 8 Max • A51 • GS20+ 5G • Velvet 5G • iPhone 8 Plus • iPhone 12 Mini • Note 4 • GS20 Ultra 5G • Note 5 • Galaxy S20 FE 5G • GS21 5G • GS21+ 5G • GS21 Ultra 5G Monthly Charge, Deductible/Service Fee, and Repair Schedule -

LG Nexus 4 Is Now Available Slightly Cheaper on the UK Play Store
LG Nexus 4 Is Now Available Slightly Cheaper On The UK Play Store LG Nexus 4 Is Now Available Slightly Cheaper On The UK Play Store 1 / 3 Buy LG Nexus 5 UK Smartphone - Black (16GB) at Amazon UK. ... or enable your printer by downloading an app from the Google Play™ Store. ... Then‚ swipe to check Google Now™ cards and find the latest information personalized for you. ... As soon as I powered on, the new Android Lollipop was available to install which .... Google Nexus 5 best price is Rs. 12000 as on 17th July 2020. ... 4.Last but not the least,Best value for money phone available in the market in this range. ... But for now, there is no compelling reason for people to buy a Pixel yet, so until then the ... I lost my Samsung galaxy S4 and decided to look for a cheaper alternative.. It's true: we're a bit late reviewing Google's latest Nexus-branded Android smartphone, which went on sale in the UK in November 2012. ... march into the mainstream - not just as a cheaper alternative to Apple's iPhone, but ... digital magazines and films all now available through the Google Play store app.. Do Google and LG Have a Nexus 4 Sequel On the Way Already? ... Now that CES is all done and dusted, MWC is next on the global tech roadshow. ... designing a phone that's slightly cheaper to produce and easier to manufacture. ... release of Key Lime Pie, as usually there's a reference device available.. The Nexus 4 just got a lot cheaper.