Securing Amazon Web Services with Qualys
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -

Oracle Database on AWS October 2013
Amazon Web Services – RDBMS in the Cloud: Oracle Database on AWS October 2013 RDBMS in the Cloud: Oracle Database on AWS Jean-Pierre Le Goaller, Carlos Conde, and Shakil Langha October 2013 (Please consult http://aws.amazon.com/whitepapers/ for the latest version of this paper) Page 1 of 33 Amazon Web Services – RDBMS in the Cloud: Oracle Database on AWS October 2013 Table of Contents Abstract ................................................................................................................................................................................... 3 Oracle Database Solutions on AWS ........................................................................................................................................ 3 Oracle Database on Amazon RDS ....................................................................................................................................... 3 Oracle Database on Amazon EC2 ........................................................................................................................................ 3 Other Database Scenarios ................................................................................................................................................... 3 Choosing between Amazon RDS and Amazon EC2 for an Oracle Database ........................................................................... 4 Oracle Database Feature Comparison between Amazon RDS and Amazon EC2 ............................................................... 5 Oracle Licensing and -
Securebox Azure
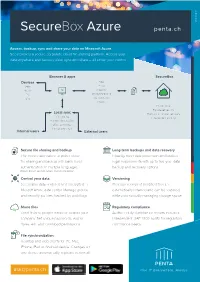
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Website Hosting Amazon Web Services
Website Hosting Amazon Web Services Arpit Ahuja, Principal Consultant [email protected] Why to host your website on AWS Website on Amazon Web Service Low Scalable Flexible Cost Stable About Amazon Web Services • World’s leading Cloud Computing Platform • Collection of Remote Computing Services (Web Services) • Powered by Amazon.com – World’s leading Ecommerce Portal • Currently have Data Centers in 10 Geographic locations • Multiple Availability Zones in each region • Edge locations for content distribution in many other geographies • Have done 42 Price Reductions in the last 8 years (Launched in 2006) • More than a Use Cases • Public Website • A company’s website is one of its most visible, accessible, and valuable ways of communicating with current and potential customers. Putting your website on the AWS cloud is fast, easy, and low-cost. • Online Application • Connected applications underpin the modern Internet. Amazon Web Services provides the services you need to make your application successful online. • Intranet Site • Internal websites help share information within your organization and aid collaboration while keeping the information protected from those outside your organization. • Connected Mobile Application • Many mobile applications rely on servers behind the scenes to deliver the information that makes them useful. Many of the world’s biggest sites uses AWS Capabilities • AWS is a flexible cloud computing solution. You can use whatever platform you like. AWS even provides SDKs for many popular platforms like Java, Ruby, PHP, Node.js, .Net, and more. Use Your Favorite Tools • Your content management system (CMS) may be the core of your website. No matter which system you choose; it can run on AWS Let your website grow and shrink with demand • Website traffic can fluctuate a lot. -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

Wandisco Fusion® Microsoft Azure Data Box
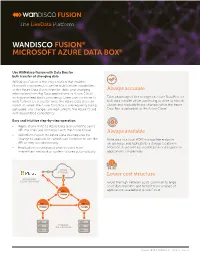
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

Creating Smart Virtual Appliances with IBM Image Construction and Composition Tool
Front cover Creating Smart Virtual Appliances with IBM Image Construction and Composition Tool Create smart appliances that are cloud-ready Develop PowerVM, KVM, and ESX customized virtual appliances Learn from experts how to cloudify your applications Jarek Miszczyk Greg Hurlebaus Pat Nickel Rashed Ferdous David Peraza John Jacobson Moises Romo Li-Fang Lee Kerry Staples ibm.com/redbooks International Technical Support Organization Creating Smart Virtual Appliances with IBM Image Construction and Composition Tool July 2013 SG24-8042-01 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. Second Edition (July 2013) This edition applies to Version 2, Release 2, Modification 1.1 of the IBM Image Construction and Composition Tool. © Copyright International Business Machines Corporation 2012, 2013. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . .x Preface . xi Authors. xi Now you can become a published author, too! . xiii Comments welcome. xiii Stay connected to IBM Redbooks . xiv Chapter 1. Introduction to virtual appliance construction . 1 1.1 Deploying your applications into the cloud . 2 1.2 Solving the terminology puzzle . 3 1.3 Why implement software virtual appliances . 4 1.4 A need for a virtual appliance construction tool . 5 1.4.1 Application packaging options . 5 1.4.2 Supported deployment options . 5 1.5 Putting the Image Construction and Composition Tool into context . 7 1.5.1 Image Construction and Composition Tool and the IBM PureSystems . 7 1.5.2 Image Construction and Composition Tool and the IBM Workload Deployer. -

Lock-Free Collaboration Support for Cloud Storage Services With
Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation Jian Chen, Minghao Zhao, and Zhenhua Li, Tsinghua University; Ennan Zhai, Alibaba Group Inc.; Feng Qian, University of Minnesota - Twin Cities; Hongyi Chen, Tsinghua University; Yunhao Liu, Michigan State University & Tsinghua University; Tianyin Xu, University of Illinois Urbana-Champaign https://www.usenix.org/conference/fast20/presentation/chen This paper is included in the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) February 25–27, 2020 • Santa Clara, CA, USA 978-1-939133-12-0 Open access to the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) is sponsored by Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation ⇤ 1 1 1 2 Jian Chen ⇤, Minghao Zhao ⇤, Zhenhua Li , Ennan Zhai Feng Qian3, Hongyi Chen1, Yunhao Liu1,4, Tianyin Xu5 1Tsinghua University, 2Alibaba Group, 3University of Minnesota, 4Michigan State University, 5UIUC Abstract Pattern 1: Losing updates Alice is editing a file. Suddenly, her file is overwritten All studied This paper studies how today’s cloud storage services support by a new version from her collaborator, Bob. Sometimes, cloud storage collaborative file editing. As a tradeoff for transparency/user- Alice can even lose her edits on the older version. services friendliness, they do not ask collaborators to use version con- Pattern 2: Conflicts despite coordination trol systems but instead implement their own heuristics for Alice coordinates her edits with Bob through emails to All studied handling conflicts, which however often lead to unexpected avoid conflicts by enforcing a sequential order. -
Wandisco Fusion® Microsoft Azure Data Box®
FUSION WANDISCO FUSION® MICROSOFT AZURE DATA BOX® Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Always accurate information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. Always available • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the Write data to a local HDFS-compatible endpoint API as they would normally. on-premises and replicate to a storage location in • Replication is continuous and recovers from Microsoft Azure with no modification or disruption to intermittent network or system failures automatically. applications on-premises. AZURE 2 STORAGE Lower cost structure MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of applications available in Azure Cloud. FUSION FUSION FUSION HADOOP ON-PREMISES Copyright © 2018 WANdisco, Inc. -

Best Practices for Building Virtual Appliances Vmware White Paper
WHITE PAPER Best Practices for Building Virtual Appliances VMWARE WHITE PAPER Table of Contents Objectives. 3 Design Principles . 3 Completely Encapsulated. 3 Optimized Virtual Disk and Operating System. 4 Initial Configuration. 4 ‘Standard’ Components. 5 Command Line Interface . 5 SSH Support. 5 Web Management Interface . 5 External Management . 5 Virtual Machine Configuration. 6 Updates and Ongoing Maintenance. 6 Packaging and Publishing . 6 2 VMWARE WHITE PAPER Best Practices for Building Virtual Appliances A virtual appliance is a pre-installed, pre-configured operating system and software solution delivered inside a virtual machine. 60-70% of support calls relate to initial installation and Deploying a software solution as a virtual appliance enables you configuration of a software application to build a complete turnkey package that customers are able to download and immediately deploy. Thus, customers skip the time-consuming and often support-intensive task of installing and configuring the appliance. This lets customers focus all their energies on trying or using your solution rather than struggling Design Principles to get it to run. Completely Encapsulated This document describes the best practices for building a virtual A virtual appliance contains all of the components required to appliance. It covers high level design principles as well as low run your solution on top of a virtualization layer. Since virtual level details for building virtual appliances ready for certification appliances are designed to run a specific solution, customers under the VMware Certified Virtual Appliance program. In turn, should not need root access to the operating system inside virtual appliances built according to these standards will allow your appliance. -

Igneous Backup with Microsoft Azure Data Box Executive Overview the Benefits of Cloud Backup, Including Scalability, Accessibility, and Agility, Are Immense
SOLUTION GUIDE Igneous Backup with Microsoft Azure Data Box Executive Overview The benefits of cloud backup, including scalability, accessibility, and agility, are immense. However, significant challenges lie in effectively deploying cloud backups for enterprise. To help enterprises harness the value of cloud backup while overcoming the challenges of massive scale, Igneous Unstructured Data Management as-a-Service and Microsoft Azure Data Box combine to offer an integrated solution that accelerates data migration from network attached storage (NAS) to Microsoft Azure Storage, and manages ongoing replication and tiering to cloud. With backup environments, the challenge of using public cloud is often seeding the initial backup before doing incrementals. Azure Data Box provides an economical way to transport those initial backups (often called “level- 0’s”) into Azure Storage without worrying about network bandwidth between your on-premises environment and Azure Storage. Igneous Unstructured Data Management as-a-Service solution, built for managing file-based backups, provides native integration with Azure Storage, including the Azure Data Box. Together, Igneous and Azure allow you to backup unstructured data stored on your primary network attached storage (NAS) file systems, efficiently move large amounts of data to Azure Storage, and protect and manage your data with tiering and replication to cloud. Microsoft Azure Data Box provides a secure, tamper-resistant method for quick and simple transfer of your data to Azure. Use Azure Data Box service when you want to transfer large amounts of data to Azure but are limited by time, network availability, or costs. Azure Data Box is supported by Igneous as a method to support transfers or initial sync to Azure Storage. -

Reproducibility, Virtual Appliances, and Cloud Computing
1 Reproducibility, Virtual Appliances, and Cloud Computing Bill Howe University of Washington CONTENTS 1.1 Introduction ...................................................... 1 1.2 Background on Cloud Computing and Virtualization ........... 2 1.3 Related Approaches and Examples .............................. 3 1.3.1 Other Uses of Virtual Machines ......................... 5 1.3.2 Towards Services Instead of Artifacts ................... 6 1.4 How Cloud Computing can Improve Reproducibility ........... 6 1.4.1 Capturing More Variables ............................... 6 1.4.2 Fewer constraints on research methods ................. 6 1.4.3 On-Demand Backups .................................... 7 1.4.4 Virtual Machines as Citable Publications ............... 7 1.4.5 Code, Data, Environment, plus Resources .............. 7 1.4.6 Automatic Upgrades ..................................... 8 1.4.7 Competitive, Elastic Pricing ............................ 8 1.4.8 Reproducibility for Complex Architectures. ............. 8 1.4.9 Unfettered Collaborative Experiments .................. 8 1.4.10 Data-intensive Computing ............................... 9 1.4.11 Cost Sharing ............................................. 9 1.4.12 A Foundation for Single-Payer Funding ................. 9 1.4.13 Compatibility with Other Approaches .................. 9 1.5 Remaining Challenges ............................................ 10 1.5.1 Cost ...................................................... 10 1.5.2 Culture ..................................................