Redirection and Pipes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Calls System Calls
System calls We will investigate several issues related to system calls. Read chapter 12 of the book Linux system call categories file management process management error handling note that these categories are loosely defined and much is behind included, e.g. communication. Why? 1 System calls File management system call hierarchy you may not see some topics as part of “file management”, e.g., sockets 2 System calls Process management system call hierarchy 3 System calls Error handling hierarchy 4 Error Handling Anything can fail! System calls are no exception Try to read a file that does not exist! Error number: errno every process contains a global variable errno errno is set to 0 when process is created when error occurs errno is set to a specific code associated with the error cause trying to open file that does not exist sets errno to 2 5 Error Handling error constants are defined in errno.h here are the first few of errno.h on OS X 10.6.4 #define EPERM 1 /* Operation not permitted */ #define ENOENT 2 /* No such file or directory */ #define ESRCH 3 /* No such process */ #define EINTR 4 /* Interrupted system call */ #define EIO 5 /* Input/output error */ #define ENXIO 6 /* Device not configured */ #define E2BIG 7 /* Argument list too long */ #define ENOEXEC 8 /* Exec format error */ #define EBADF 9 /* Bad file descriptor */ #define ECHILD 10 /* No child processes */ #define EDEADLK 11 /* Resource deadlock avoided */ 6 Error Handling common mistake for displaying errno from Linux errno man page: 7 Error Handling Description of the perror () system call. -
Dell Update Packages for Linux Operating Systems User's Guide
Dell™ Update Packages for Linux Operating Systems User’s Guide Notes and Cautions NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates potential damage to hardware or loss of data if instructions are not followed. ____________________ Information in this document is subject to change without notice. © 2009 Dell Inc. All rights reserved. Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell, the DELL logo, and OpenManage are trademarks of Dell Inc.; Microsoft and Windows are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries; Intel is a registered trademark of Intel Corporation in the United States and other countries; Red Hat and Red Hat Enterprise Linux are registered trademarks of Red Hat, Inc. in the United States and other countries; SUSE is a registered trademark of Novell, Inc. in the United States and other countries; VMware and ESX Server are registered trademarks or trademarks of VMware, Inc. in the United States and/or other jurisdictions; Citrix and XenServer are either trademarks or registered trademarks of Citrix Systems, Inc. in the United States and/or other countries. Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own. April 2009 Contents 1 Getting Started With Dell Update Packages . 7 Overview . -

Lab Work 06. Linux Shell. Files Globbing & Streams Redirection
LAB WORK 06. LINUX SHELL. FILES GLOBBING & STREAMS REDIRECTION. 1. PURPOSE OF WORK • Learn to use shell file globbing (wildcard); • Learn basic concepts about standard UNIX/Linux streams redirections; • Acquire skills of working with filter-programs. • Get experience in creating composite commands that have a different functional purpose than the original commands. 2. TASKS FOR WORK NOTE. Start Your UbuntuMini Virtual Machine on your VirtualBox. You need only Linux Terminal to complete the lab tasks. Before completing the tasks, make a Snapshot of your Virtual Linux. If there are problems, you can easily go back to working condition! 2.0. Create new User account for this Lab Work. • Login as student account (user with sudo permissions). • Create new user account, example stud. Use adduser command. (NOTE. You can use the command “userdel –rf stud” to delete stud account from your Linux.) $ sudo adduser stud • Logout from student account (logout) and login as stud. 2.1. Shell File Globbing Study. 2.2. File Globbing Practice. (Fill in a Table 1 and Table 2) 2.3. Command I/O Redirection Study. 2.4. Redirection Practice. (Fill in a Table 3 and Table 4) © Yuriy Shamshin, 2021 1/20 3. REPORT Make a report about this work and send it to the teacher’s email (use a docx Report Blank). REPORT FOR LAB WORK 06: LINUX SHELL. FILES GLOBBING & STREAMS REDIRECTION Student Name Surname Student ID (nV) Date 3.1. Insert Completing Table 1. File globbing understanding. 3.2. Insert Completing Table 2. File globbing creation. 3.3. Insert Completing Table 3. Command I/O redirection understanding. -

CS2043 - Unix Tools & Scripting Cornell University, Spring 20141
CS2043 - Unix Tools & Scripting Cornell University, Spring 20141 Instructor: Bruno Abrahao January 31, 2014 1 Slides evolved from previous versions by Hussam Abu-Libdeh and David Slater Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Vim: Tip of the day! Line numbers Displays line number in Vim: :set nu Hides line number in Vim: :set nonu Goes to line number: :line number Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Counting wc How many lines of code are in my new awesome program? How many words are in this document? Good for bragging rights Word, Character, Line, and Byte count with wc wc -l : count the number of lines wc -w : count the number of words wc -m : count the number of characters wc -c : count the number of bytes Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Sorting sort Sorts the lines of a text file alphabetically. sort -ru file sorts the file in reverse order and deletes duplicate lines. sort -n -k 2 -t : file sorts the file numerically by using the second column, separated by a colon Example Consider a file (numbers.txt) with the numbers 1, 5, 8, 11, 62 each on a separate line, then: $ sort numbers.txt $ sort numbers.txt -n 1 1 11 5 5 8 62 11 8 62 Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting uniq uniq uniq file - Discards all but one of successive identical lines uniq -c file - Prints the number of successive identical lines next to each line Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Character manipulation! The Translate Command tr [options] <char_list1> [char_list2] Translate or delete characters char lists are strings of characters By default, searches for characters in char list1 and replaces them with the ones that occupy the same position in char list2 Example: tr 'AEIOU' 'aeiou' - changes all capital vowels to lower case vowels Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Pipes and redirection tr only receives input from standard input (stdin) i.e. -

Unix, Standard I/O and Command Line Arguments Overview Redirection
Unix, Standard I/O and command line arguments For any programming assignments I give you, I expect a program that reads and writes to standard input and output, taking any extra parameters from the command line. This handout explains how to do that. I have also appended a small appendix of useful Unix commands. I recommend that you go to a Unix terminal and type in and run all of the examples in the gray boxes. You can do this from the Terminal application on a MacIntosh, or from a terminal window in GNU/Linux or any Unix-like operating system, from Cygwin in Windows maybe, or by connecting to bingsuns using SSH. Overview Most programming languages feature “standard,” or default, input and output channels where I/O goes unless otherwise specified. In C, the functions scanf(), gets() and getchar() read from standard input, while printf(), puts() and putchar() write to standard output. In Tcl, the gets and puts commands read and write standard input and output. In awk and perl, you just sort of use the force and your program receives a line of input from somewhere. Letʼs stick with C for the time being.1 When a program runs from a terminal, standard input is usually the userʼs keyboard input, while standard output is displayed as text on-screen. Unix and Unix-like operating systems allow you to intercept the standard I/O channels of a program to redirect them into files or other programs. This gives you the ability to chain many simple programs to do something genuinely useful. -
Chapter 5. Writing Your Own Shell
Chapter 5. Writing Your Own Shell You really understand something until you program it. GRR Introduction Last chapter covered how to use a shell program using UNIX commands. The shell is a program that interacts with the user through a terminal or takes the input from a file and executes a sequence of commands that are passed to the Operating System. In this chapter you are going to learn how to write your own shell program. Shell Programs A shell program is an application that allows interacting with the computer. In a shell the user can run programs and also redirect the input to come from a file and output to come from a file. Shells also provide programming constructions such as if, for, while, functions, variables etc. Additionally, shell programs offer features such as line editing, history, file completion, wildcards, environment variable expansion, and programing constructions. Here is a list of the most popular shell programs in UNIX: sh Shell Program. The original shell program in UNIX. csh C Shell. An improved version of sh. tcsh A version of Csh that has line editing. ksh Korn Shell. The father of all advanced shells. bash The GNU shell. Takes the best of all shell programs. It is currently the most common shell program. In addition to commandline shells, there are also Graphical Shells such as the Windows Desktop, MacOS Finder, or Linux Gnome and KDE that simplify theDraft use of computers for most of the users. However, these graphical shells are not substitute to command line shells for power users who want to execute complex sequences of commands repeatedly or with parameters not available in the friendly, but limited graphical dialogs and controls. -

Linux Internals
LINUX INTERNALS Peter Chubb and Etienne Le Sueur [email protected] A LITTLE BIT OF HISTORY • Ken Thompson and Dennis Ritchie in 1967–70 • USG and BSD • John Lions 1976–95 • Andrew Tanenbaum 1987 • Linux Torvalds 1991 NICTA Copyright c 2011 From Imagination to Impact 2 The history of UNIX-like operating systems is a history of people being dissatisfied with what they have and wanting to do some- thing better. It started when Ken Thompson got bored with MUL- TICS and wanted to write a computer game (Space Travel). He found a disused PDP-7, and wrote an interactive operating sys- tem to run his game. The main contribution at this point was the simple file-system abstraction. (Ritchie 1984) Other people found it interesting enough to want to port it to other systems, which led to the first major rewrite — from assembly to C. In some ways UNIX was the first successfully portable OS. After Ritchie & Thompson (1974) was published, AT&T became aware of a growing market for UNIX. They wanted to discourage it: it was common for AT&T salesmen to say, ‘Here’s what you get: A whole lot of tapes, and an invoice for $10 000’. Fortunately educational licences were (almost) free, and universities around the world took up UNIX as the basis for teaching and research. The University of California at Berkeley was one of those univer- NICTA Copyright c 2011 From Imagination to Impact 2-1 sities. In 1977, Bill Joy (a postgrad) put together and released the first Berkeley Software Distribution — in this instance, the main additions were a pascal compiler and Bill Joy’s ex editor. -

Essential Skills for Bioinformatics: Unix/Linux PIPES a Simple Program with Grep and Pipes
Essential Skills for Bioinformatics: Unix/Linux PIPES A simple program with grep and pipes • Suppose we are working with a FASTA file and a program warns that it contains non-nucleotide characters in sequences. We can check for non-nucleotide characters easily with a Unix one-liner using pipes and the grep. • The grep Unix tool searches files or standard input for strings that match patterns. These patterns can be simple strings, or regular expressions. See man grep for more details. A simple program with grep and pipes • tb1-protein.fasta • Approach: - remove all header lines (those that begin with >) - the remaining sequences are piped to grep - print lines containing non-nucleotide characters A simple program with grep and pipes • “^>”: regular expression pattern which matches all lines that start with a > character. • -v: invert the matching lines because we want to exclude lines starting with > • |: pipe the standard output to the next command with the pipe character | • “[^ACGT]”: When used in brackets, a caret symbol (^) matches anything that’s not one of the characters in these brackets. [^ACGT] matches any character that’s not A, C, G, or T. • -i: We ignore case. • --color: to color the matching non-nucleotide character. • Both regular expressions are in quotes, which is a good habit to get into. Combining pipes and redirection • Large bioinformatics programs will often use multiple streams simultaneously. Results are output via the standard output stream while diagnostic messages, warnings, or errors are output to the standard error stream. In such cases, we need to combine pipes and redirection to manage all streams from a running program. -
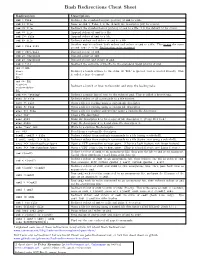
Bash Redirections Cheat Sheet
Bash Redirections Cheat Sheet Redirection Description cmd > file Redirect the standard output (stdout) of cmd to a file. cmd 1> file Same as cmd > file. 1 is the default file descriptor (fd) for stdout. cmd 2> file Redirect the standard error (stderr) of cmd to a file. 2 is the default fd for stderr. cmd >> file Append stdout of cmd to a file. cmd 2>> file Append stderr of cmd to a file. cmd &> file Redirect stdout and stderr of cmd to a file. Another way to redirect both stdout and stderr of cmd to a file. This is not the same cmd > file 2>&1 as cmd 2>&1 > file. Redirection order matters! cmd > /dev/null Discard stdout of cmd. cmd 2> /dev/null Discard stderr of cmd. cmd &> /dev/null Discard stdout and stderr of cmd. cmd < file Redirect the contents of the file to the standard input (stdin) of cmd. cmd << EOL line1 Redirect a bunch of lines to the stdin. If 'EOL' is quoted, text is treated literally. This line2 is called a here-document. EOL cmd <<- EOL <tab>foo Redirect a bunch of lines to the stdin and strip the leading tabs. <tab><tab>bar EOL cmd <<< "string" Redirect a single line of text to the stdin of cmd. This is called a here-string. exec 2> file Redirect stderr of all commands to a file forever. exec 3< file Open a file for reading using a custom file descriptor. exec 3> file Open a file for writing using a custom file descriptor. exec 3<> file Open a file for reading and writing using a custom file descriptor. -

Section 3: Syscalls and I/O
Section 3: Syscalls and I/O September 12-13, 2017 Contents 1 Vocabulary 2 2 Problems 3 2.1 Signals...............................................3 2.1.1 Warmup..........................................3 2.1.2 Did you really want to quit?..............................4 2.2 Files................................................4 2.2.1 Files vs File Descriptor.................................4 2.2.2 Quick practice with write and seek...........................4 2.3 Dup and Dup2..........................................5 2.3.1 Warmup..........................................5 2.3.2 Redirection: executing a process after dup2......................5 2.3.3 Redirecting in a new process..............................6 1 CS 162 Fall 2017 Section 3: Syscalls and I/O 1 Vocabulary • system call - In computing, a system call is how a program requests a service from an operating system's kernel. This may include hardware-related services (for example, accessing a hard disk drive), creation and execution of new processes, and communication with integral kernel services such as process scheduling. • file descriptors - File descriptors are an index into a file-descriptor table stored by the kernel. The kernel creates a file-descriptor in response to an open call and associates the file-descriptor with some abstraction of an underlying file-like object; be that an actual hardware device, or a file-system or something else entirely. Consequently a process's read or write calls that reference that file-descriptor are routed to the correct place by the kernel to ultimately do something useful. Initially when your program starts you have 3 file descriptors. File Descriptor File 0 stdin 1 stdout 2 stderr • int open(const char *path, int oflags) - open is a system call that is used to open a new file and obtain its file descriptor. -

CS415: Systems Programming
CS415: Systems Programming File related System Calls Most of the slides in this lecture are either from or adapted from the slides provided by Dr. Ahmad Barghash Remember UNI File I/O: Performed mostly using 6 commands • open • close • read Last Lectures • write • lseek • dup, dup2 dup System Call • int dup(int oldfd); • oldfd: old file descriptor whose copy is to be created. • Returns a new file descriptor • The dup() system call creates a copy of a file descriptor. • It uses the lowest-numbered unused descriptor for the new descriptor. • If the copy is successfully created, then the original and copy file descriptors may be used interchangeably. • They both refer to the same open file description and thus share file offset and file status flags. • Include the header file unistd.h for using dup() system call. dup2 System Call • int dup2(int oldfd, int newfd); • oldfd: old file descriptor • newfd: new file descriptor which is used by dup2() to create a copy. • The dup2() system call is similar to dup() but the basic difference between them is that instead of using the lowest-numbered unused file descriptor, it uses the descriptor number specified by the user. • If the descriptor newfd was previously open, it is silently closed before being reused. • If oldfd is not a valid file descriptor, then the call fails, and newfd is not closed. • If oldfd is a valid file descriptor, and newfd has the same value as oldfd, then dup2() does nothing, and • returns newfd. • Include the header file unistd.h for using dup2() system call. -

Providing a Shared File System in the Hare POSIX Multikernel Charles
Providing a Shared File System in the Hare POSIX Multikernel by Charles Gruenwald III Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY June 2014 c Massachusetts Institute of Technology 2014. All rights reserved. Author.............................................................. Department of Electrical Engineering and Computer Science May 21, 2014 Certified by. Frans Kaashoek Professor Thesis Supervisor Certified by. Nickolai Zeldovich Associate Professor Thesis Supervisor Accepted by . Leslie Kolodziejski Chairman, Department Committee on Graduate Theses 2 Providing a Shared File System in the Hare POSIX Multikernel by Charles Gruenwald III Submitted to the Department of Electrical Engineering and Computer Science on May 21, 2014, in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science Abstract Hare is a new multikernel operating system that provides a single system image for multicore processors without cache coherence. Hare allows applications on different cores to share files, directories, file descriptors, sockets, and processes. The main challenge in designing Hare is to support shared abstractions faithfully enough to run applications that run on traditional shared-memory operating systems with few modifications, and to do so while scaling with an increasing number of cores. To achieve this goal, Hare must support shared abstractions (e.g., file descriptors shared between processes) that appear consistent to processes running on any core, but without relying on hardware cache coherence between cores. Moreover, Hare must implement these abstractions in a way that scales (e.g., sharded directories across servers to allow concurrent operations in that directory).