Background on FERC Docket No. NP19-4-000
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Energy Information Administration (EIA) 2014 and 2015 Q1 EIA-923 Monthly Time Series File
SPREADSHEET PREPARED BY WINDACTION.ORG Based on U.S. Department of Energy - Energy Information Administration (EIA) 2014 and 2015 Q1 EIA-923 Monthly Time Series File Q1'2015 Q1'2014 State MW CF CF Arizona 227 15.8% 21.0% California 5,182 13.2% 19.8% Colorado 2,299 36.4% 40.9% Hawaii 171 21.0% 18.3% Iowa 4,977 40.8% 44.4% Idaho 532 28.3% 42.0% Illinois 3,524 38.0% 42.3% Indiana 1,537 32.6% 29.8% Kansas 2,898 41.0% 46.5% Massachusetts 29 41.7% 52.4% Maryland 120 38.6% 37.6% Maine 401 40.1% 36.3% Michigan 1,374 37.9% 36.7% Minnesota 2,440 42.4% 45.5% Missouri 454 29.3% 35.5% Montana 605 46.4% 43.5% North Dakota 1,767 42.8% 49.8% Nebraska 518 49.4% 53.2% New Hampshire 147 36.7% 34.6% New Mexico 773 23.1% 40.8% Nevada 152 22.1% 22.0% New York 1,712 33.5% 32.8% Ohio 403 37.6% 41.7% Oklahoma 3,158 36.2% 45.1% Oregon 3,044 15.3% 23.7% Pennsylvania 1,278 39.2% 40.0% South Dakota 779 47.4% 50.4% Tennessee 29 22.2% 26.4% Texas 12,308 27.5% 37.7% Utah 306 16.5% 24.2% Vermont 109 39.1% 33.1% Washington 2,724 20.6% 29.5% Wisconsin 608 33.4% 38.7% West Virginia 583 37.8% 38.0% Wyoming 1,340 39.3% 52.2% Total 58,507 31.6% 37.7% SPREADSHEET PREPARED BY WINDACTION.ORG Based on U.S. -

Wind Powering America FY07 Activities Summary
Wind Powering America FY07 Activities Summary Dear Wind Powering America Colleague, We are pleased to present the Wind Powering America FY07 Activities Summary, which reflects the accomplishments of our state Wind Working Groups, our programs at the National Renewable Energy Laboratory, and our partner organizations. The national WPA team remains a leading force for moving wind energy forward in the United States. At the beginning of 2007, there were more than 11,500 megawatts (MW) of wind power installed across the United States, with an additional 4,000 MW projected in both 2007 and 2008. The American Wind Energy Association (AWEA) estimates that the U.S. installed capacity will exceed 16,000 MW by the end of 2007. When our partnership was launched in 2000, there were 2,500 MW of installed wind capacity in the United States. At that time, only four states had more than 100 MW of installed wind capacity. Seventeen states now have more than 100 MW installed. We anticipate five to six additional states will join the 100-MW club early in 2008, and by the end of the decade, more than 30 states will have passed the 100-MW milestone. WPA celebrates the 100-MW milestones because the first 100 megawatts are always the most difficult and lead to significant experience, recognition of the wind energy’s benefits, and expansion of the vision of a more economically and environmentally secure and sustainable future. WPA continues to work with its national, regional, and state partners to communicate the opportunities and benefits of wind energy to a diverse set of stakeholders. -

Wind Powering America Fy08 Activities Summary
WIND POWERING AMERICA FY08 ACTIVITIES SUMMARY Energy Efficiency & Renewable Energy Dear Wind Powering America Colleague, We are pleased to present the Wind Powering America FY08 Activities Summary, which reflects the accomplishments of our state Wind Working Groups, our programs at the National Renewable Energy Laboratory, and our partner organizations. The national WPA team remains a leading force for moving wind energy forward in the United States. At the beginning of 2008, there were more than 16,500 megawatts (MW) of wind power installed across the United States, with an additional 7,000 MW projected by year end, bringing the U.S. installed capacity to more than 23,000 MW by the end of 2008. When our partnership was launched in 2000, there were 2,500 MW of installed wind capacity in the United States. At that time, only four states had more than 100 MW of installed wind capacity. Twenty-two states now have more than 100 MW installed, compared to 17 at the end of 2007. We anticipate that four or five additional states will join the 100-MW club in 2009, and by the end of the decade, more than 30 states will have passed the 100-MW milestone. WPA celebrates the 100-MW milestones because the first 100 megawatts are always the most difficult and lead to significant experience, recognition of the wind energy’s benefits, and expansion of the vision of a more economically and environmentally secure and sustainable future. Of course, the 20% Wind Energy by 2030 report (developed by AWEA, the U.S. Department of Energy, the National Renewable Energy Laboratory, and other stakeholders) indicates that 44 states may be in the 100-MW club by 2030, and 33 states will have more than 1,000 MW installed (at the end of 2008, there were six states in that category). -

Executive Summary ¾ Electricity Report ¾ Natural Gas Report ¾ Communications Report ¾ Water/Wastewater Report ¾ Acronyms ¾ Glossary
Indiana Utility Regulatory Commission 2007 Regulatory Flexibility Report to the Indiana General Assembly Links to Major Sections of the Regulatory Flexibility Report Click on Links Below to Navigate to Major Sections of the Regulatory Flexibility Report ¾ Executive Summary ¾ Electricity Report ¾ Natural Gas Report ¾ Communications Report ¾ Water/Wastewater Report ¾ Acronyms ¾ Glossary Executive Summary EXECUTIVE SUMMARY This 2007 Indiana Utility Regulatory Commission Report to the Regulatory Flexibility Committee of the Indiana General Assembly highlights key issues that confront Indiana Electric, Gas, Communications, and Water/Wastewater industries, as well as the role of the Indiana Utility Regulatory Commission (IURC, Commission) in addressing these issues. For the first time, and while not required by statute, a section on the Water/Wastewater industry is included in this Report in response to concerns raised during the most recent session of the legislature. While each industry has unique issues, several issues discussed in this Report cut across multiple industries. This Executive Summary contains a brief overview of these cross-industry and industry-specific issues which are more fully addressed in the body of the Report. For your convenience there is a list of acronyms and a glossary in the back of the Report. CROSS-INDUSTRY ISSUES Aging infrastructure is a concern for many Indiana utilities. The Electric, Gas, and Water/Wastewater sections of this Report specifically discuss aging infrastructure and the potential problems and costs associated with repairing or replacing old facilities. Coupled with aging facilities is increasing consumer demand for electric, gas, telecommunications, and water services. Increased consumer demand can accelerate the deterioration of equipment and limit periods in which facilities can be conveniently removed from service for maintenance or replacement. -

Renewable Energy: Wind and Solar
Renewable Energy: Chapter | 19 Wind and Solar ❖ Can Texans harness the wind and sun and even the jobs that go with these energy sources? 600-turbine development across 336,000 Introduction acres of West Texas. Financed by Chinese In late 2009, German utility giant E.ON banks, the development will feature new constructed the world’s largest wind farm in turbines made in China and will bring the tiny West Texas town of Roscoe. The 300 temporary construction jobs and 30 Roscoe wind farm has the capacity to produce permanent jobs to the area. Renewable 781.5 megawatts — enough electricity for energy in Texas is new — and it has already every home in Plano, McKinney and the been globalized. rest of the 265,000 households in Collin These giant wind projects illustrate County. The $1 billion project in Roscoe two key trends: Texas is emerging as took 21 months to complete and employed the capital of renewable energy, and 500 construction workers, who built 627 wind foreign companies are moving fast to take turbines on the fields of 300 property owners advantage. “People in Texas think it has — land that once pumped oil. got to be conventional energy or renewable The wind turbines of West Texas spin at energy. It’s not. It’s both,” said Michael 7 miles per hour. And one turbine produces Webber, an engineering professor at the about as much electricity as 350 households University of Texas at Austin and associate consume in a year. These economics are director of the Center for International attracting more wind turbines to the state, Energy and Environmental Policy. -

Financial Statement 2013 of Enel Green Power S.P.A
Annual Report 2013 Annual Report2013 Annual Report 2013 Contents Report on operations Consolidated financial statements Enel Green Power | 6 Consolidated Income Statement | 110 The Group structure | 7 Statement of Consolidated Comprehensive Income | 111 Enel Green Power in the world | 8 Consolidated Balance Sheet | 112 Corporate boards and Powers | 10 Statement of Changes in Consolidated Shareholders’ Equity | 113 Letter to the shareholders and other stakeholders | 12 Consolidated Statement of Cash Flows | 114 Summary of results | 16 Notes to the financial statements | 115 Significant events in 2013 | 25 Reference scenario | 33 Economic and energy conditions in 2013 | 35 Corporate governance | 187 Electricity markets | 39 How we operate | 57 Overview of the Group’s performance and financial position | 73 Declaration of the Chief Executive Officer and the Performance and financial position by segment | 90 officer responsible for the preparation of corporate > Italy and Europe | 91 financial reports | 188 > Iberia and Latin America | 95 > North America | 98 Main risks and uncertainties | 101 Annexes Outlook | 102 Regulations governing non-EU subsidiaries | 103 Subsidiaries, associates and other significant equity investments of the Enel Green Power Group at December 31, 2013 | 192 Regulations governing subsidiaries subject to the management and coordination of other companies | 104 Related parties | 105 Reconciliation of shareholders’ equity and net income of Enel Green Reports Power SpA and the corresponding consolidated figures | 107 Report of the Independent Auditors | 210 3 Report on operations Enel Green Power Enel Green Power, founded in December 2008, is the Enel Group company entirely devoted to the development and management of the Group’s renewables generation operations around the world, with a presence in Europe and the Americas. -

Summary Report of Wind Farm Data September 2008 Yih-Huei Wan
Technical Report Summary Report of Wind NREL/TP-500-44348 Farm Data May 2009 September 2008 Yih-huei Wan Technical Report Summary Report of Wind NREL/TP-500-44348 Farm Data May 2009 September 2008 Yih-huei Wan Prepared under Task No. WER8.5001 National Renewable Energy Laboratory 1617 Cole Boulevard, Golden, Colorado 80401-3393 303-275-3000 • www.nrel.gov NREL is a national laboratory of the U.S. Department of Energy Office of Energy Efficiency and Renewable Energy Operated by the Alliance for Sustainable Energy, LLC Contract No. DE-AC36-08-GO28308 NOTICE This report was prepared as an account of work sponsored by an agency of the United States government. Neither the United States government nor any agency thereof, nor any of their employees, makes any warranty, express or implied, or assumes any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial product, process, or service by trade name, trademark, manufacturer, or otherwise does not necessarily constitute or imply its endorsement, recommendation, or favoring by the United States government or any agency thereof. The views and opinions of authors expressed herein do not necessarily state or reflect those of the United States government or any agency thereof. Available electronically at http://www.osti.gov/bridge Available for a processing fee to U.S. Department of Energy and its contractors, in paper, from: U.S. Department of Energy Office of Scientific and Technical Information P.O. -

PUBLIC (REDACTED) VERSION May 14, 2007 1 TABLE of CONTENTS 2 3 I
RC Exhibit C (RMF) STATE OF INDIANA INDIANA UTILITY REGULATORY COMMISSION JOINT PETITION AND APPLICATION OF PSI ENERGY, INC. , D/B/A ) DUKE ENERGY INDIANA, INC., AND SOUTHERN INDIANA GAS ) AND ELECTRIC COMPANY, D/B/A VECTREN ENERGY DELIVERY ) OF INDIANA, INC., PURSUANT TO INDIANA CODE CHAPTERS 8-1- ) 8.5, 8-1-8.7, 8-1-8.8, AND SECTIONS 8-1-2-6.8, 8-1-2-6.7, 8-1-2-42 (A) ) REQUESTING THAT THE COMMISSION: (1) ISSUE APPICABLE ) CERTIFICATES OF PUBLIC CONVENIENCE AND NECESSITY AND ) APPLICABLE CERTIFICATES OF CLEA COAL TECHNOLOGY TO ) EACH JOINT PETITIONER FOR THE CONSTRUCTION OF AN ) INTEGRATED GASIFICATION COMBINED CYCLE GENERATING ) FACILITY (“IGCC PROJECT”) TO BE USED IN THE PROVISION OF ) ELECTRIC UTILITY SERVICE TO THE PUBLIC; (2) APPROVE THE ) ESTIMATED COSTS AND SCHEDULE OF THE IGCC PROJECT; (3) ) CAUSE NO. 43114 AUTHORIZE EACH JOINT PETITIONER TO RECOVER ITS ) CONSTRUCTION AND OPERATING COSTS ASSOCIATED WITH ) THE IGCC PROJECT ON A TIMELY BASIS VIA APPLICABLE RATE ) ADJUSTMENT MECHANISMS; (4) AUTHORIZE EACH JOINT ) PETITIONER TO USE ACCELERATED DEPRECIATION FOR THE ) IGCC PROJECT; (5) APPROVE CERTAIN OTHER FINANCIAL ) INCENTIVES FOR EACH JOINT PETITIONER ASSOCIATED WITH ) THE IGCC PROJECT; (6) GRANT EACH JOINT PETITIONER THE ) AUTHORITY TO DEFER ITS PROPERTY TAX EXPENSE, POST-IN- ) SERVICE CARRYING COSTS, DEPRECIATION COSTS, AND ) OPERATION AND MAINTENANCE COSTS ASSOCIATED WITH THE ) IGCC PROJECT ON AN INTERIM BASIS UNTIL THE APPLICABLE ) COSTS ARE REFLECTED IN EACH JOINT PETITIONER’S ) RESPECTIVE RETAIL ELECTRIC RATES; (7) AUTHORIZE EACH ) JOINT PETITIONER TO RECOVER ITS OTHER RELATED COSTS ) ASSOCIATED WITH THE IGCC PROJECT; AND (8) CONDUCT AN ) ONGOING REVIEW OF THE CONSTRUCTION OF THE IGCC ) PROJECT ) VERIFIED PETITION OF DUKE ENERGY INDIANA, INC. -

Perceived Risk and Response to the Wind Turbine Ice Throw
PERCEIVED RISK AND RESPONSE TO THE WIND TURBINE ICE THROW HAZARD: COMPARING COMMUNITY STAKEHOLDERS AND OPERATIONS AND MAINTENANCE PERSONNEL IN TWO REGIONS OF TEXAS by Greg Klaus, B.S., M.A.G. A dissertation submitted to the Graduate Council of Texas State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy with a major in Environmental Geography May 2017 Committee Members: Denise Blanchard-Boehm, Chair Richard Dixon Richard Earl Todd Moore COPYRIGHT by Greg Klaus 2017 FAIR USE AND AUTHOR’S PERMISSION STATEMENT Fair Use This work is protected by the Copyright Laws of the United States (Public Law 94-553, section 107). Consistent with fair use as defined in the Copyright Laws, brief quotations from this material are allowed with proper acknowledgment. Use of this material for financial gain without the author’s express written permission is not allowed. Duplication Permission As the copyright holder of this work I, Greg Klaus, authorize duplication of this work, in whole or in part, for educational or scholarly purposes only. DEDICATION The author would like to dedicate this dissertation to the men and women who work in the wind energy industry who at times put themselves in harm’s way in order to provide for their families and also supply this great nation with a clean, renewable source of electricity. ACKNOWLEDGEMENTS The author would like to thank his committee chair Dr. Denise Blanchard for all of her support and guidance throughout the dissertation process; as well as thank committee members Dr. Richard Dixon, Dr. Richard Earl, and Dr. -

Ride Like the Wind: Selected Issues in Multi-Party Wind Lease Negotiations
Texas A&M Journal of Property Law Volume 1 Number 3 Wind Farming: Obstacles to Planning Article 5 and Development 2014 Ride Like the Wind: Selected Issues in Multi-Party Wind Lease Negotiations Rod E. Wetsel University of Texas School of Law Steven K. DeWolf University of Texas School of Law Follow this and additional works at: https://scholarship.law.tamu.edu/journal-of-property-law Part of the Energy and Utilities Law Commons Recommended Citation Rod E. Wetsel & Steven K. DeWolf, Ride Like the Wind: Selected Issues in Multi-Party Wind Lease Negotiations, 1 Tex. A&M J. Real Prop. L. 447 (2013). Available at: https://doi.org/10.37419/JPL.V1.I3.5 This Symposia Article is brought to you for free and open access by Texas A&M Law Scholarship. It has been accepted for inclusion in Texas A&M Journal of Property Law by an authorized editor of Texas A&M Law Scholarship. For more information, please contact [email protected]. \\jciprod01\productn\T\TWR\1-3\TWR305.txt unknown Seq: 1 5-MAY-14 16:43 RIDE LIKE THE WIND:† SELECTED ISSUES IN MULTI-PARTY WIND LEASE NEGOTIATIONS By Rod E. Wetsel and Steven K. DeWolf ‡ I. INTRODUCTION .......................................... 448 R II. HISTORY OF WIND DEVELOPMENT IN TEXAS: THE WIND BOOM ............................................ 448 R III. THE TEXAS WIND LEASE ............................... 452 R A. Origins and Evolution .............................. 452 R B. Major Elements ..................................... 453 R IV. MULTI-PARTY WIND LEASE NEGOTIATIONS ............ 453 R A. The Town Hall Meeting Concept .................... 454 R B. Some Wind Groups and their Creators: Signing Parties ............................................. -
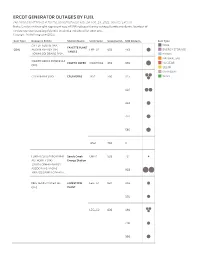
ERCOT GENERATOR OUTAGES by FUEL (As Named As of March 4 for the Period Between Feb
ERCOT GENERATOR OUTAGES BY FUEL (As named as of March 4 for the period between Feb. 14–Feb. 19, 2021. Source: ERCOT) Note: Circles on the right represent size of MW reduced during outage/derate incidents. Number of circles represents outage/derate incidents indicated for each unit. Copyright: POWER magazine (2021) Fuel Type Resource Entity Station Name Unit Name Seasonal M.. MW Reduct.. Fuel Type CITY OF AUSTIN DBA COAL FAYETTE PLANT COAL AUSTIN ENERGY (RE) FPP_G1 603 453 ENERGY STORAGE 1 AND 2 LOWER COLORADO RIVE.. HYDRO NATURAL GAS COLETO CREEK POWER LLC COLETO CREEK COLETOG1 655 655 NUCLEAR (RE) SOLAR UNKNOWN CPS ENERGY (RE) CALAVERAS JKS1 560 315 WIND 410 412 424 560 JKS2 785 0 LOWER COLORADO RIVER Sandy Creek UNIT1 933 73 AUTHORITY (RE) Energy Station SANDY CREEK ENERGY ASSOCIATES LP (RE) 933 BRAZOS SANDY CREEK EL.. NRG TEXAS POWER LLC LIMESTONE LEG_G1 824 262 (RE) PLANT 301 LEG_G2 836 194 290 396 836 ERCOT GENERATOR OUTAGES BY FUEL (As named as of March 4 for the period between Feb. 14–Feb. 19, 2021. Source: ERCOT) Note: Circles on the right represent size of MW reduced during outage/derate incidents. Number of circles represents outage/derate incidents indicated for each unit. Copyright: POWER magazine (2021) Fuel Type Resource Entity Station Name Unit Name Seasonal M.. 3M9W6 Reduct.. Fuel Type COAL NRG TEXAS POWER LLC LIMESTONE LEG_G2 836 COAL (RE) PLANT 836 ENERGY STORAGE HYDRO NATURAL GAS WA PARISH WAP_G5 664 80 NUCLEAR SOLAR UNKNOWN 136 WIND 146 664 WAP_G7 577 22 51 58 61 300 577 OAK GROVE MANAGEMENT OAK GROVE SES UNIT1A 855 855 COMPANY LLC (RE) UNIT2 855 855 BLUE SUMMIT STORAGE ENERGY BLUE SUMMIT BATTERY 30 15 LLC (RE) STORAGE COMMERCE ST CPS ENERGY (RE) SWRI 10 10 ESS KEY CAPTURE ENERGY LLC PORT LAVACA BESS1 10 10 2 (RE) BATT ERCOT GENERATOR OUTAGES BY FUEL (As named as of March 4 for the period between Feb. -

Statewide Air Emissions Calculations from Wind and Other Renewables
ESL-TR-20-07-01 STATEWIDE AIR EMISSIONS CALCULATIONS FROM WIND AND OTHER RENEWABLES VOLUME I A Report to the Texas Commission on Environmental Quality For the Period January 2019 – December 2019 Juan-Carlos Baltazar, Ph.D., P.E.; Jeff Haberl, Ph.D.; Bahman Yazdani, P.E.; David Claridge, Ph.D., P.E.; Sungkyun Jung; Farshad Kheiri; Chul Kim July 2020 Page 1 ENERGY SYSTEMS LABORATORY July 15, 2020 Mr. Robert Gifford Air Quality Division Texas Commission on Environmental Quality Austin, TX 78711-3087 Dear Mr. Gifford, The Energy Systems Laboratory (ESL) at the Texas Engineering Experiment Station of The Texas A&M University System is pleased to provide its annual report, “Statewide Emissions Calculations From Wind and Other Renewables,” as required by the 79th Legislature. This work has been performed through a contract with the Texas Commission on Environmental Quality (TCEQ). In this work, the ESL is required to obtain input from public/private stakeholders, and develop and use a methodology to annually report the energy savings from wind and other renewables. This report summarizes the work performed by the ESL on this project from January 2019 to December 2019. Please contact me at (979) 845-9213 should you have questions concerning this report or the work presently being done to quantify emissions reductions from renewable energy measures as a result of the TERP implementation. Sincerely, David E. Claridge, Ph.D., P.E. Director Enclosure . Page 2 Disclaimer This report is provided by the Texas Engineering Experiment Station (TEES) as required under Section 388.003 (e) of the Texas Health and Safety Code and is distributed for purposes of public information.