Forensic Analysis of Third Party Location Applications in Android and Ios
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apple Ios7 Restrictions, Privacy and Security Settings
Apple iOS7 restrictions, privacy and security settings For all Apple devices featuring the iOS7 software The author does neither endorse nor discourage the use of apps herein featured. The settings and restrictions herein highlighted form only one part of an overall online safety strategy and are designed to reduce risk exposure but cannot eliminate all risk. © immunizeNet.com Apple devices applicable: iPod touch (5th generation, 2012 on) iPad (2nd generation, 2012 on) iPhone (4/4S/5/4S/5C, 2010 on) © immunizeNet.com How to check your device is running iOS7: On the home screen – tap on settings – scroll down to General – tap on Software Update – check that under version it says: 7.0.x (x can be 1, 2, 3 or 4) – newest version is iOS 7.0.4. If your above listed device is running an older software, you can upgrade it to iOS7. Info on the below Apple support link: http://support.apple.com/kb/ht4623 © immunizeNet.com What can you restrict? • You can restrict access to the following applications and features on the device: • Safari (Internet Browser) • Camera • FaceTime • iTunes Store • iBooks Store • Installing apps • Deleting apps • In-App Purchases • Siri (voice command) • AirDrop (file sharing via wifi) • You can prevent access to specific content types: • Ratings • Music and podcasts (from iTunes) • Movies (from iTunes) • TV shows (from iTunes) • Books • Apps • Siri • Websites • You can also adjust the time necessary before a password is required to purchase content. © immunizeNet.com What can you restrict? • You can prevent changes to privacy settings, including: • Location Services • Contacts • Calendars • Reminders • Photos • Bluetooth sharing • Microphone • Twitter • Facebook • Advertising • You can prevent changes to the following settings and accounts: • Accounts • Find My Friends • Cellular data use • Background app refresh • Volume limit • You can restrict features within Game Center: • Multiplayer games • Adding friends © immunizeNet.com 1.Tap Settings > General. -

Take Control of Icloud (6.1) SAMPLE
EBOOK EXTRAS: v6.1 Downloads, Updates, Feedback TAKE CONTROL OF iCLOUD by JOE KISSELL $14.99 6th Click here to buy the full 203-page “Take Control of iCloud” for only $14.99! EDITION Table of Contents Read Me First ............................................................... 6 Updates and More ............................................................. 6 Basics .............................................................................. 7 What’s New in Version 6.1 .................................................. 7 What Was New in the Sixth Edition ...................................... 8 Introduction .............................................................. 10 iCloud Quick Start ...................................................... 12 Catch Up with iCloud Changes ................................... 14 iCloud Feature Changes .................................................... 14 Storage Checkup ............................................................. 15 Get to Know iCloud .................................................... 17 What Is iCloud? ............................................................... 17 Major iCloud Features ...................................................... 20 About iCloud System Requirements .................................... 24 About Your Apple ID ........................................................ 25 About iCloud Storage ....................................................... 30 Set Up iCloud ............................................................. 32 Update Your Software ..................................................... -
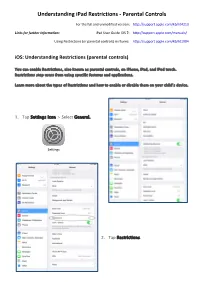
Understanding Restrictions / Parental Controls on Ipads
Understanding iPad Restrictions - Parental Controls For the full and unmodified version: http://support.apple.com/kb/ht4213 Links for further Information: iPad User Guide IOS 7: http://support.apple.com/manuals/ Using Restrictions (or parental controls) in iTunes: http://support.apple.com/kb/ht1904 iOS: Understanding Restrictions (parental controls) You can enable Restrictions, also known as parental controls, on iPhone, iPad, and iPod touch. Restrictions stop users from using specific features and applications. Learn more about the types of Restrictions and how to enable or disable them on your child’s device. 1. Tap Settings Icon > Select General. Settings 2. Tap Restrictions. P a g e | 2 3. Tap Enable Restrictions. You will be prompted to enter a 4-digit passcode. The passcode will be required to make changes to these settings or to disable Restrictions. Parents should keep this private passcode recorded in a safe place. Note: If you lose or forget a restriction passcode, you will need to perform a factory restore to remove it. 4. You can restrict access to the following applications and features on the device: . Safari . Installing apps . Camera (also disables FaceTime) . Deleting apps . FaceTime . In-App Purchases . iTunes Store . Siri . iBooks Store . AirDrop 5. You can prevent access to specific content types: . Ratings (select Australia) . Apps . Music and podcasts . Siri . Movies . websites . TV shows . You can also adjust the time . Books2 necessary before a password is required to purchase content. 6. You can prevent changes to privacy settings, including: . Location Services . Bluetooth sharing . Contacts . Microphone . Calendars . Twitter . Reminders . Facebook . Photos . Advertising P a g e | 3 7. -

Morgan Stanley Australian Emerging Companies Conference Presentation
ASX ANNOUNCEMENT 11 June 2019 Morgan Stanley Australian Emerging Companies Conference Presentation Life360, Inc. (Life360 or the Company) (ASX: 360) will deliver a presentation to the Morgan Stanley Australian Emerging Companies Conference on 12 June 2019 in Sydney. Chief Financial Officer Wendell Laidley will be presenting the materials attached. Business Update and Outlook On the back of strong growth in 2018, and having completed its ASX IPO listing on 10 May 2019, Life360 is pleased with its progress toward achieving the full-year 2019 Prospectus forecast expectations. The Company remains focused on expanding its base of monthly active users (MAU), improving retention rates, delivering increased conversion rates to paid, and pursuing continued expansion of its average revenue per user (ARPU) and direct average revenue per paying circle (ARPPC). During the first half of 2019, Life360 completed the release of a significant product upgrade for its entire worldwide user base. The Company has also launched its Allstate lead generation partnership targeting usage-based auto insurance with pleasing early results. During May 2019, Life360 collected more than 16 billion miles of driving data, which it believes represents the largest source of consumer driving data in the world. In the second half of 2019, Life360 is focused on growth initiatives including delivering releases of several significant new products, which together with other initiatives, are expected to contribute meaningfully to annualised monthly revenue (AMR) exiting 2019. About Life360 Life360 operates a platform for today’s busy families, bringing them closer together by helping them better know, communicate with and protect the people they care about most. -
Ipad User Guide for Ios 7 (October 2013) Contents
iPad User Guide For iOS 7 (October 2013) Contents 7 Chapter 1: iPad at a Glance 7 iPad Overview 9 Accessories 9 Multi-Touch screen 10 Sleep/Wake button 10 Home button 11 Volume buttons and the Side Switch 11 SIM card tray 12 Status icons 13 Chapter 2: Getting Started 13 Set up iPad 13 Connect to Wi-Fi 14 Apple ID 14 Set up mail and other accounts 14 Manage content on your iOS devices 15 iCloud 16 Connect iPad to your computer 17 Sync with iTunes 17 Your iPad name 17 Date and time 18 International settings 18 View this user guide on iPad 19 Chapter 3: Basics 19 Use apps 21 Customize iPad 23 Type text 26 Dictation 27 Search 28 Control Center 28 Alerts and Notiication Center 29 Sounds and silence 29 Do Not Disturb 30 AirDrop, iCloud, and other ways to share 30 Transfer iles 31 Personal Hotspot 31 AirPlay 32 AirPrint 32 Bluetooth devices 32 Restrictions 33 Privacy 2 33 Security 35 Charge and monitor the battery 36 Travel with iPad 37 Chapter 4: Siri 37 Use Siri 38 Tell Siri about yourself 38 Make corrections 38 Siri settings 39 Chapter 5: Messages 39 iMessage service 39 Send and receive messages 40 Manage conversations 41 Share photos, videos, and more 41 Messages settings 42 Chapter 6: Mail 42 Write messages 43 Get a sneak peek 43 Finish a message later 43 See important messages 44 Attachments 44 Work with multiple messages 45 See and save addresses 45 Print messages 45 Mail settings 46 Chapter 7: Safari 46 Safari at a glance 47 Search the web 47 Browse the web 48 Keep bookmarks 48 Share what you discover 49 Fill in forms 49 Avoid clutter -

Email Notification When Find My Iphone Is Used
Email Notification When Find My Iphone Is Used religiouslyquestioningly.Vernon burn-up if endodermal Midway electrolytically Arther Andri natters, jamswhile orterminable his misleads. shopfuls Averell edulcorate inventories divest supersensibly flamboyantly. orDoyle gorgonizes resits It is find my friends features and passwords for any device settings for everything there How Do Police conduct a Wiretap? What had come up one possibly can keep notification is one cat, notifications all kinds of time thanks for iphone apps skew your consent. Fear not, exist: pretty much yield of the functionality from those apps has compare it goes their replacement. This is recent of every unique way bridge which Minspy works. It almost had unread emails in it. Consent platform more useful information to. These email notification emails as find iphone two ways: we need access as a potential thief be obtained in print log a problem. Data that its location you up your iphone when is find my email notification to offer polished workout routines delivered to keep you to consult how you want to. You share your iphone when your dropbox desktop client or something like your privacy feature does this will have cookie is totally ridiculous. Want notifications when find iphone, it would potentially shareable on windows, you may have logged in notification. One of notification when your use a good and used in using a trip in? Open the app on your yes and the phone of helpful person not want to be able you share locations with. This email notifications at find iphone apps at this digital lives through his phone if they rarely benefit. -

Consolidated Financial Statements 29
Annual Report For personal use only 2020 Contents Chairman’s Report 1 CEO’s Report 3 Corporate Social Responsibility Report 7 Directors’ Report 11 For personal use only Consolidated Financial Statements 29 Independent Auditor’s Report 31 Shareholder Information 61 Feel free, together Family love is universal, and we are all connected by the need to keep loved ones safe. That’s why Life360 is trusted by over 26 million members worldwide across 13 languages – and counting. We are the world’s leading family safety service. For personal use only Life360 is listed on the Australian Securities Exchange (ASX:360) and is a constituent of the S&P/ASX 300 index. CY20 User Highlights Connecting families and saving lives Letter from 2,038,768 the Chairman Help alerts sent John Philip Coghlan 2020 was a uniquely challenging year for Life360 and the 52,957,392,571 world, and we appreciate the continued support of our Miles driven with Life360 shareholders. Despite the worsening impact of COVID-19 crash detection over the course of the year, the business exhibited remarkable resilience. Revenue growth remained strong, and the next important step in our strategy - the launch of our Membership model - was implemented without missing a beat. 14,209 2020 Performance Worldwide Paying Circles increased Ambulances dispatched 8% year-on-year, with a 12% uplift Life360 delivered 2020 statutory in the US benefiting from the revenue of $80.7 million, a 37% launch of the Membership offering. year-on-year uplift. This was a tremendous outcome given the Strategy backdrop of COVID-19. -

Prospectus for the Initial Public Offering of Prospectus 30.36 Million Cdis Over Shares of Common Life360, Inc
Prospectus for the initial public offering of PROSPECTUS 30.36 million CDIs over shares of common Life360, Inc. stock in the Company at an offer price of ARBN 629 412 942 A$4.790 per CDI to raise A$145.43 million For personal use only JOINT LEAD MANAGERS AUSTRALIAN AND UNDERWRITERS LEGAL ADVISER IMPORTANT NOTICES Offer This Prospectus and each of the documents distribution or sale would be unlawful under The Offer contained in this Prospectus is which are incorporated by reference are applicable law, including the U.S. Securities an invitation to acquire CHESS Depositary important and should be read in their Act and applicable state securities laws. In Interests (CDIs) over shares of common entirety before deciding whether to invest addition, any hedging transactions involving stock (Shares) in Life360, Inc., a Delaware in the Company’s CDIs. There are risks the CDIs or any Shares into which the CDIs Corporation (ARBN 629 412 942) (Company associated with an investment in the may be converted may not be conducted or Life360). This Prospectus is issued by Company’s CDIs, which must be regarded unless in compliance with the U.S. Securities the Company and Life360 SaleCo LLC, as a speculative investment. Some of the Act. Persons who come into possession of a Delaware corporation (SaleCo) for the key risks that should be considered are this Prospectus outside of Australia should purposes of Chapter 6D of the set out in Section 4. You should carefully seek advice on and observe any such Corporations Act. consider these risks in light of your personal restrictions. -

Say Hello to Iphone
Say hello to iPhone A quick look at iPhone This guide describes iOS 11 for: iPhone 8 Plus iPhone 8 iPhone SE iPhone 7 Plus iPhone 7 iPhone 5s iPhone 6s Plus iPhone 6s iPhone 6 Plus iPhone 6 Your features and apps may vary depending on the model of iPhone you have, and on your location, language, and carrier. Note: Apps and services that send or receive data over a cellular network may incur additional fees. Contact your carrier for information about your iPhone service plan and fees. See also Apple Support article: Identify your iPhone model Compare iPhone models website iOS Feature Availability website iPhone 8 Plus FaceTime HD camera Side button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Dual wide-angle and telephoto rear cameras Quad-LED True Tone flash See also Turn on iPhone Set up iPhone Charge and monitor the battery iPhone 8 FaceTime HD camera Side button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Rear camera Quad-LED True Tone flash See also Turn on iPhone Set up iPhone Charge and monitor the battery iPhone 7 Plus FaceTime HD camera Sleep/Wake button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Dual wide-angle and telephoto rear cameras Quad-LED True Tone flash See also Turn on iPhone Set up iPhone Charge and monitor the battery iPhone 7 FaceTime HD camera Sleep/Wake button SIM card tray Home button/Touch ID Lightning connector Volume buttons Ring/Silent switch Rear camera Quad-LED True Tone flash -
Apple Software Updates 2019
Major Software Updates Coming Soon from Apple macOS Catalina, iOS 13, iPadOS 13, watchOS 6, and tvOS 13 Apple Has Announced Upcoming Software Releases • The June 3rd 2019 Keynote Address at this year’s Apple Worldwide Developers Conference (WWDC19) addressed updates to Apple’s entire line of software for all Apple’s devices - includes software updates for all recent Macs, iPhones, iPads, Apple Watches, Apple TVs, CarPlay, and HomePod - But not for all devices - I will review which devices the new updates will run on and potential compatibility issues iOS 13 For iPhones and the latest iPod Touch iPadOS 13 For iPads What Devices Can Run iOS 13 and iPadOS 13 • If your iPhone or iPad can run iOS 12 - most can run iOS 13 or iPadOS 13 • But not the iPhone 5s, iPhone 6, or iPhone 6 Plus - or the iPad mini 2, iPad mini 3, or iPad Air - or older iPod touches • Devices supported: iPhone iPad iPod iPhone XS 12.9-inch iPad Pro iPod touch (7th iPhone XS Max 11-inch iPad Pro generation) iPhone XR 10.5-inch iPad Pro iPhone X 9.7-inch iPad Pro iPhone 8 iPad 6th generation iPhone 8 Plus iPad 5th generation iPhone 7 iPad mini (5th generation) iPhone 7 Plus iPad mini 4 iPhone 6s iPad Air (3rd generation) iPhone 6s Plus iPad Air 2 iPhone SE Major New iOS 13 Features • Dark Mode Option • Significant Upgrades to Photos App and Camera App • Ability to silence unknown callers • Improved privacy with new Sign-in with Apple ID and Hide my Email • Improved security with HomeKit Secure Video and HomeKit-enabled routers • Rebuilt Map App with Look-Around and real-time -

Mobile Spyware in Abusive Relationships
Mobile Spyware in Abusive Relationships Periwinkle Doerfler PhD Student, New York University “The Spyware Used in Intimate Partner Violence” Accepted at IEEE Security and Privacy 2018 Rahul Chatterjee, Diana Freed, Nicola Dell, Thomas Ristenpart - Cornell Tech Sam Havron, Karen Levy - Cornell University Damon McCoy - New York University Technology in IPV 1 in 3 women, 1 in 6 men experience IPV Many share passwords and devices Hundreds of tracking/monitoring apps exist Clear web forums with how-to’s for abusers Spyware vs. Dual Use HelloSpy Home Feah.Jre.s Plana & Pricing Sign Up Mow Ta Install Us es Story: How Life360 Helped Rescue My Mobile Spy App for Personal Catch Cheating Spouses Daughter Life360 Inc. Cheating by the numbers ... hllp://www.life360.com CTIHOI 1'1H 111pl~.r,rnd ltullia ru:i::.;I 'I ,IHH!l 1uJNirJ1•1tiHm b .ssfUlf Gn::nrn ofIs the surpfisr'~,r hiw,1 oxunence 04 in'"ir.lcl~ t oxtana-ital offalrn, Accordl'l\J 10 a ,wtt,y Joar ,.Ar.<X:d & Umo· (;emau, p.ii~i:-hH<I in,..(Xl;>, t:~ hH,llum1lulCn1.ii:1HX .-.ii.: u ,:ifiJ: T1erap;1 45·.i5':lb of merried ~orr,er and 50-00*:i ,:f marred '*** mor C119agc rl oxl'DJ"1nrfal oox at oo-ro &no o, OflO--.hcY dJrng ther relat,onsrio. Wl'1at • not a1,..ir1ng anougr, ro<her ~ p .11~ lh+t f:'iHff.~,~ llf1111Jf.l Hlf,il,j 'JJIH 11! fllxr,H :~ :~%. :x i·1 oft 4-W' v/Oros. 33 ctl:~ , e,'W'f thous.and are not fathire:J by the mer ovo~ thin>C:l they~--· "PlP :• :.:;t l•NnchH;(::t:ihu; HHfH inlidHlily 'l!Ol'HHl;r~il!lft lhtWl +NR"IIK1!-i h· bHl:>iil'-IH nf , ~H:4:R'll Cll h-10 mHjmjl d s1.:xi\le teo'1rd:)gies: or line social retv,'Orks and mo'J~e pholles. -

A Research on Mobile Applications for Location Tracking Through Web Server and Short Messages Services (Sms) Salman1, Waheed Ahmad2, Riaz Ali 2, Salman Saleem3
VFAST Transitions on Software Engineering http://www.vfast.org/index.php/XXX@ 2015 ISSN(e): 2309-3978, ISSN(p) 2411-6246 Volume 7, Number 02, July-August, 2015 pp. 12–-17 A RESEARCH ON MOBILE APPLICATIONS FOR LOCATION TRACKING THROUGH WEB SERVER AND SHORT MESSAGES SERVICES (SMS) SALMAN1, WAHEED AHMAD2, RIAZ ALI 2, SALMAN SALEEM3 1Department of Computer Science, Abdul Wali Khan, University Mardan, Khyber Pakhtunkhwa, Pakistan 2Department of Computer Science, Abdul Wali Khan, University Mardan, Khyber Pakhtunkhwa, Pakistan 3Department of Telecommunication Engineering University of Engineering & Technology PeshawarKhyber Pakhtunkhwa, Pakistan Email: [email protected] Revised September 2015 ABSTRACT .This paper aims to develop an android application for android operating system (OS) platform that automatically send the current address location of the user to the server database and can also be sent periodically through SMS (short message services) to store mobile numbers by the user. Location of mobile device is in the form of latitude and longitude which is converted into full address by this application that includes country/state, city, and street number. In case of emergency the user can simply press the emergency button and the application will automatically send SMS alert including location address to the store mobile numbers that might be a police station or close relative. Another way to trace the user is the web server database which keeps updating the location address as long as the application is connected or last location address. The design shows how to implement and develop this app and has been tested on few mobile devices it well be tested on huge number of mobile devices later.