Applications: G
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

TRABAJO DE DIPLOMA Título: Diseño De La Página Web De Antenas
FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Título: Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos Tutor: Dr. Roberto Jiménez Hernández Santa Clara 2006 “Año de la Revolución Energética en Cuba” Universidad Central “Marta Abreu” de Las Villas FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TTRRAABBAAJJOO DDEE DDIIPPLLOOMMAA Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos e-mail: [email protected] Tutor: Dr. Roberto Jiménez Hernández Prof. Dpto. de Telecomunicaciones y electrónica Facultad de Ing. Eléctrica. UCLV. e-mail: [email protected] Santa Clara Curso 2005-2006 “Año de la Revolución Energética en Cuba” Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Telecomunicaciones y Electrónica, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Tutor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica PENSAMIENTO “El néctar de la victoria se bebe en la copa del sacrificio” DEDICATORIA Dedico este trabajo a mis padres, a mí hermana y a mi novia por ser las personas más hermosas que existen y a las cuales les debo todo. -
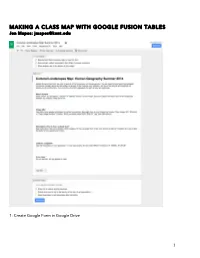
MAKING a CLASS MAP with GOOGLE FUSION TABLES Jen Mapes: [email protected]
MAKING A CLASS MAP WITH GOOGLE FUSION TABLES Jen Mapes: [email protected] 1: Create Google Form in Google Drive 1 2. Give form link (and further instructions) to students 2 3. When submission deadline has passed, Create a Fusion Table out of your “Responses” Spreadsheet (created automatically by Google Forms). If Fusion Tables does not show up as an option, you will need to “Connect more apps,” and select it. With a Kent account, you may need to go through an extra step. Ask me or a Help Desk person for assistance if you run into this problem. 3 This arrow will let you choose “change column” 4. Change type for your Lat/Long column to “Location.” Incorrect formats will be highlighted in yellow. 4 This arrow will let you choose “change column” 5. Change column for Image URL to Format: Eight Line Image 5 6 6. Choose the map tab, and your lat/longs will be geocoded on a map for you. If you use addresses instead, this may take an extra few minutes. 7. The option to configure your map should show up when your map is created. If it disappears, go to Tools/Change Map. You will then see two options: Change feature styles (the dots on the map), and change info window (what pops up when you click on the dots). 7 8. If you’d like to change the dots, or have them represented by different colors/styles depending on their values, then you’ll change the feature styles. Column allows you to use your spreadsheet (or form) to select what icon will appear with each submission. -

(12) United States Patent (10) Patent No.: US 7,960,121 B2 Wohlgemuth Et Al
US007960121B2 (12) United States Patent (10) Patent No.: US 7,960,121 B2 Wohlgemuth et al. (45) Date of Patent: Jun. 14, 2011 (54) METHODS AND COMPOSITIONS FOR 5,079,352 A 1/1992 Gelfand et al. DAGNOSING AND MONITORING 5,091,310 A 2f1992 Innis 5, 120,525 A 6/1992 Goldenberg TRANSPLANT RELECTION 5,142,033. A 8, 1992 Innis 5,143,854 A 9/1992 Pirrung et al. (75) Inventors: Jay Wohlgemuth, Menlo Park, CA 5,210,015 A 5/1993 Gelfand et al. 5,212,071 A 5/1993 Fearon et al. (US); Kirk Fry, Palo Alto, CA (US); 5,215,882 A 6/1993 Bahl et al. Robert Woodward, Pleasanton, CA 5,219,727 A 6/1993 Wang et al. (US); Ngoc Ly, Albany, CA (US) 5,264,351 A 1 1/1993 Harley 5,278,043 A 1/1994 Bannwarth et al. (73) Assignee: XDX, Inc., Brisbane, CA (US) 5,310,652 A 5/1994 Gelfand et al. 5,314,809 A 5/1994 Erlich et al. 5,322,770 A 6/1994 Gelfand (*) Notice: Subject to any disclaimer, the term of this 5,340,720 A 8, 1994 Stetler patent is extended or adjusted under 35 5,346,994 A 9/1994 Chomczynski U.S.C. 154(b) by 0 days. 5,352,600 A 10, 1994 Gelfand et al. 5,374,553 A 12/1994 Gelfand et al. (21) Appl. No.: 12/823,090 5,385,824 A 1/1995 Hoet et al. 5,389,512 A 2/1995 Sninsky et al. -

Application Development with Tocollege.Net
CYAN YELLOW MAGENTA BLACK PANTONE 123 C BOOKS FOR PROFESSIONALS BY PROFESSIONALS® THE EXPERT’S VOICE® IN WEB DEVELOPMENT Companion eBook Available Covers Pro Web 2.0 Application GWT 1.5 Pro Development with GWT 2.0 Web Dear Reader, This book is for developers who are ready to move beyond small proof-of-concept Pro sample applications and want to look at the issues surrounding a real deploy- ment of GWT. If you want to see what the guts of a full-fledged GWT application look like, this is the book for you. GWT 1.5 is a game-changing technology, but it doesn’t exist in a bubble. Real deployments need to connect to your database, enforce authentication, protect against security threats, and allow good search engine optimization. To show you all this, we’ll look at the code behind a real, live web site called Application Development with ToCollege.net. This application specializes in helping students who are applying Web 2.0 to colleges; it allows them to manage their application processes and compare the rankings that they give to schools. It’s a slick application that’s ready for you to sign up for and use. Application Development This book will give you a walking tour of this modern Web 2.0 start-up’s code- base. The included source code will provide a functional demonstration of how to merge together the modern Java stack including Hibernate, Spring Security, Spring MVC 2.5, SiteMesh, and FreeMarker. This fully functioning application is better than treasure if you’re a developer trying to wire GWT into a Maven build environment who just wants to see some code that makes it work. -

Fall 2021 CE Catalog
FALL 21 REGISTRATION Continuing BEGINS AUG 9 EducationCOMMUNITY CLASSES FOR ALL AGES & STAGES OF LIFE INSIDE: Computers | 14 Culinary | 28 World Languages | 42 … and many more! stlcc.edu/CE | 314-984-7777 NEW to the Lineup Conflict Management Build effective work relationships and help resolve conflicts as a team member. | page 5 Fresh Floral Arrangement Design balanced, eye-catching floral arrangements alongside fellow crafters. | page 26 World Languages: Swahili Challenge your mind and explore other cultures through the study of language. | page 45 Animal Spirit Allies: Shamanic Perspective Learn about the mystery of animal spirits and how you can connect with the animal kingdom. | page 51 2 STLCC.EDU/CE | 314-984-7777 | REGISTRATION BEGINS AUG. 9 Fall 2021 Continuing Education Courses St. Louis Community PROFESSIONAL DEVELOPMENT PERSONAL ENRICHMENT College expands minds and Essentials Training .................................... 5 Ageless Learning Seminars ..................... 21 changes lives every day Professional Essentials ................................5 Creative Arts ............................................ 23 Small Business Essentials ...........................6 Fine Arts ......................................................23 by offering high-quality Career Essentials..........................................7 Crafts ...........................................................24 educational experiences Career Studies ......................................... 10 Culinary .......................................................28 -

Employees' Reactions to Their Own Gossip About Highly
BITING THE HAND THAT FEEDS YOU: EMPLOYEES’ REACTIONS TO THEIR OWN GOSSIP ABOUT HIGHLY (UN)SUPPORTIVE SUPERVISORS By JULENA MARIE BONNER Bachelor of Arts in Business Management and Leadership Southern Virginia University Buena Vista, VA 2007 Master of Business Administration Oklahoma State University Stillwater, Oklahoma 2012 Submitted to the Faculty of the Graduate College of the Oklahoma State University in partial fulfillment of the requirements for the Degree of DOCTOR OF PHILOSOPHY July, 2016 BITING THE HAND THAT FEEDS YOU: EMPLOYEES’ REACTIONS TO THEIR OWN GOSSIP ABOUT HIGHLY (UN)SUPPORTIVE SUPERVISORS Dissertation Approved: Dr. Rebecca L. Greenbaum Dissertation Adviser Dr. Debra L. Nelson Dr. Cynthia S. Wang Dr. Isaac J. Washburn ii ACKNOWLEDGEMENTS The road to completing this degree and dissertation has been a long, bumpy one, with plenty of ups and downs. I wish to express my gratitude to those who have helped me along the way. Those who provided me with words of encouragement and support, those who talked me down from the ledge when the bumps seemed too daunting, and those who helped smooth the path by taking time to teach and guide me. I will forever be grateful for my family, friends, and the OSU faculty and doctoral students who provided me with endless amounts of support and guidance. I would like to especially acknowledge my dissertation chair, Rebecca Greenbaum, who has been a wonderful mentor and friend. I look up to her in so many ways, and am grateful for the time she has taken to help me grow and develop. I want to thank her for her patience, expertise, guidance, support, feedback, and encouragement over the years. -

Acom Internet User Guide
Acom Internet User Guide Aeom GrtK: URL [hl^.r>Simv«.ac3om.co.uk''aoorrv' Products w Vornf i htejds»aA t Ncy^lrava» t teittaM t f iU-v.'.y- ;'. •.! Va I't! At. At-f i.'till .'-iin^-.M'riT'»'*i<1*'"i'>^n<1>ll'llMHn^rirtlTi'r»"i'f"'W >1ii1iPiiK>Ti-<i-fifiir <'»l ^Vtewrtg "Acwm Gfotjppte" ! Table of Contents Introduction Acom Internet Background How do I get an Internet connection? Setting up Modem Configuration instructions Configuring the Internet server Setting up communications functions Configuring IMail Installing !Mail Setting the Post_In and Post_Out directories Configuring the Web browser Page caches Browser configuration Network configuration Managing the mail server Setting up users and user groups Managing newsgroups Allowing and disallowing Web URLs N^l statistics L flaying the server log Finger Quitting Connea Saving space Using Mail Starting IConnect Connecting with the mail system Sending mail Reading mail Forwarding a mail message Connecting with the Internet Logging off and Quitting Using the Web browser Starting the Web browser Overview Finding>starting and stopping links The browser menu Viewing locally-stored pages Using news Reading news Forwarding an article by email Following up an article Replying to an article (by email) Saving an article Starting a new thread Playing other multimedia data types BWing Java applets ISnbckwave World Wide Web pages What are Web pages? Creating Web pages Identifying resources - URLs Serving pages AppendixA: Acronyms and Smilies Acronyms Smilies ^pendix B; Writing Acorn Internet Command Scripts Ii>. oduction Protocols and Interfaces Anatomy of a logon script Writing your Own Scripts Handling Dynamic IPAllocation Scripting Language Conunand Set pppconnect for RISC OS Authentication Routing Bibliography Appendix C; Glossary Copyright notices Copyright © 1995,1996,1997,1998 Acom Computers Limited. -

Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library
ACRL Publications in Librarianship No. 72 Applying Library Values to Emerging Technology Decision-Making in the Age of Open Access, Maker Spaces, and the Ever-Changing Library Editors Peter D. Fernandez and Kelly Tilton Association of College and Research Libraries A division of the American Library Association Chicago, Illinois 2018 The paper used in this publication meets the minimum requirements of Ameri- can National Standard for Information Sciences–Permanence of Paper for Print- ed Library Materials, ANSI Z39.48-1992. ∞ Cataloging-in-Publication data is on file with the Library of Congress. Copyright ©2018 by the Association of College and Research Libraries. All rights reserved except those which may be granted by Sections 107 and 108 of the Copyright Revision Act of 1976. Printed in the United States of America. 22 21 20 19 18 5 4 3 2 1 Contents Contents Introduction .......................................................................................................ix Peter Fernandez, Head, LRE Liaison Programs, University of Tennessee Libraries Kelly Tilton, Information Literacy Instruction Librarian, University of Tennessee Libraries Part I Contemplating Library Values Chapter 1. ..........................................................................................................1 The New Technocracy: Positioning Librarianship’s Core Values in Relationship to Technology Is a Much Taller Order Than We Think John Buschman, Dean of University Libraries, Seton Hall University Chapter 2. ........................................................................................................27 -

Forensic Methods and Tools for Web Environments
Forensic Methods and Tools for Web Environments by Michael Kent Mabey A Dissertation Presented in Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy Approved November 2017 by the Graduate Supervisory Committee: Gail-Joon Ahn, Co-Chair Adam Doupé, Co-Chair Stephen S. Yau Joohyung Lee Ziming Zhao ARIZONA STATE UNIVERSITY December 2017 ABSTRACT The Web is one of the most exciting and dynamic areas of development in today’s technology. However, with such activity, innovation, and ubiquity have come a set of new challenges for digital forensic examiners, making their jobs even more difficult. For examiners to become as effective with evidence from the Web as they currently are with more traditional evidence, they need (1) methods that guide them to know how to approach this new type of evidence and (2) tools that accommodate web environments’ unique characteristics. In this dissertation, I present my research to alleviate the difficulties forensic examiners currently face with respect to evidence originating from web environments. First, I introduce a framework for web environment forensics, which elaborates on and addresses the key challenges examiners face and outlines a method for how to approach web-based evidence. Next, I describe my work to identify extensions installed on encrypted web thin clients using only a sound understanding of these systems’ inner workings and the metadata of the encrypted files. Finally, I discuss my approach to reconstructing the timeline of events on encrypted web thin clients by using service provider APIs as a proxy for directly analyzing the device. In each of these research areas, I also introduce structured formats that I customized to accommodate the unique features of the evidence sources while also facilitating tool interoperability and information sharing. -

It's All About Visibility
8 It’s All About Visibility This chapter looks at the critical tasks for getting your message found on the web. Now that we’ve discussed how to prepare a clear targeted message using the right words (Chapter 5, “The Audience Is Listening (What Will You Say?)”), we describe how online visibility depends on search engine optimization (SEO) “eat your broccoli” basics, such as lightweight and crawlable website code, targeted content with useful labels, and inlinks. In addition, you can raise the visibility of your website, products, and services online through online advertising such as paid search advertising, outreach through social websites, and display advertising. 178 Part II Building the Engine Who Sees What and How Two different tribes visit your website: people, and entities known as web spiders (or crawlers or robots). People will experience your website differently based on their own characteristics (their visual acuity or impairment), their browser (Internet Explorer, Chrome, Firefox, and so on), and the machine they’re using to view your website (a TV, a giant computer monitor, a laptop screen, or a mobile phone). Figure 8.1 shows a page on a website as it appears to website visitors through a browser. Figure 8.1 Screenshot of a story page on Model D, a web magazine about Detroit, Michigan, www.modeldmedia.com. What Search Engine Spiders See The web spiders are computer programs critical to your business because they help people who don’t know about your website through your marketing efforts find it through the search engines. The web spiders “crawl” through your website to learn about what it contains and carry information back to the gigantic servers behind the search engines, so that the search engine can provide relevant results to people searching for your product or service. -

Do Network Dynamics Undermine Idea-Based Network Advantages? Experimental Results from an Entrepreneurship Bootcamp∗
Do network dynamics undermine idea-based network advantages? Experimental results from an entrepreneurship bootcamp∗ Rembrand Koning Harvard Business School August 29, 2016 Abstract Do networks plentiful in ideas provide early stage startups with performance advantages? On the one hand, network positions that provide access to a multitude of ideas are thought to increase team performance. On the other hand, research on network formation argues that such positional advantages should be fleeting as entrepreneurs strategically compete over the most valuable network positions. To investigate these competing views, I embed a field experiment in a startup bootcamp to test if networks that are plentiful in ideas lead to sustainable network- based performance advantages. Leveraging data on each participant's creative potential, I use peer randomizations and detailed data on network formation to show that ties to more creative individuals improve team performance. Despite the performance benefits of such connections, I find little evidence that entrepreneurs strategically connect to others who have greater cre- ative potential. Instead, entrepreneurs seek feedback from others on dimensions that are more socially salient and verifiable. Beyond providing causal evidence for the durability of network- based performance advantages, these findings provide micro-level support to the importance of knowledge spillovers within bootcamps, accelerators, and startup ecosystems more generally. ∗Please direct correspondence to [email protected]. This work has benefited from excellent feedback provided by sem- inar participants at Stanford GSB, Northwestern Kellogg, Chicago Booth, Michigan, Duke Fugua, HBS, Wharton, Berkeley, INSEAD, MIT's Conference on Digital Experimentation, the 2014 Conference on Computational Sociol- ogy, Airbnb, and Google. Special thanks to everyone who made the bootcamp happen, especially Ponnurangam Kumaraguru and Randy Lubin.