Keeping Secrets in Hardware: the Microsoft Xboxtm Case Study
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Direct Memory Access Components Verification System
ТРУДЫ МФТИ. — 2012. — Том 4, № 1 Frolov P. V. et al. 1 УДК 004.052.42 P. V. Frolov, V. N. Kutsevol, A. N. Meshkov, N. Yu. Polyakov, M. P. Ryzhov AO «MCST» PAO «INEUM» Direct Memory Access components verification system A method of direct memory access subsystem verification used for Elbrus series micro- processors has been described. A peripheral controller imitator has been developed in order to reduce verification overhead. The model of imitator has been included into the functional machine simulator. A pseudorandom test generator for verification of the direct memory access subsystem has been based on the simulator. Ключевые слова: system verification, functional model, direct memory access, pseu- dorandom test generation. Direct Memory Access components verification system 1. Introduction Modern computer systems require very intensive data exchange between the peripheral de- vices and the random-access memory. In the most cases this exchange is performed by the direct memory access (DMA) subsystem. The increasing demands for the performance of the subsys- tem lead to an increase in its complexity, therefore requiring development of effective approaches to DMA subsystem verification [1,2]. This article is based on a result of a comprehensive project than combined implementation of a there co-designed verification techniques based on the consecutive investigation of theDMA subsystem employing one the three models: 1) a functional model written in C++ that corre- sponds to behaviour of the subsystem in the environment determined by a real computer system configuration, 2) RTL model in Verilog and 3) FPGA-based prototype. This article describesthe first method that enables verifying correctness of the design at an early stage of the verification and eliminate a large quantity of bugs using simple tests. -

VIA RAID Configurations
VIA RAID configurations The motherboard includes a high performance IDE RAID controller integrated in the VIA VT8237R southbridge chipset. It supports RAID 0, RAID 1 and JBOD with two independent Serial ATA channels. RAID 0 (called Data striping) optimizes two identical hard disk drives to read and write data in parallel, interleaved stacks. Two hard disks perform the same work as a single drive but at a sustained data transfer rate, double that of a single disk alone, thus improving data access and storage. Use of two new identical hard disk drives is required for this setup. RAID 1 (called Data mirroring) copies and maintains an identical image of data from one drive to a second drive. If one drive fails, the disk array management software directs all applications to the surviving drive as it contains a complete copy of the data in the other drive. This RAID configuration provides data protection and increases fault tolerance to the entire system. Use two new drives or use an existing drive and a new drive for this setup. The new drive must be of the same size or larger than the existing drive. JBOD (Spanning) stands for Just a Bunch of Disks and refers to hard disk drives that are not yet configured as a RAID set. This configuration stores the same data redundantly on multiple disks that appear as a single disk on the operating system. Spanning does not deliver any advantage over using separate disks independently and does not provide fault tolerance or other RAID performance benefits. If you use either Windows® XP or Windows® 2000 operating system (OS), copy first the RAID driver from the support CD to a floppy disk before creating RAID configurations. -

ATX-945G Industrial Motherboard in ATX Form Factor with Intel® 945G Chipset
ATX-945G Industrial Motherboard in ATX form factor with Intel® 945G chipset Supports Intel® Core™2 Duo, Pentium® D CPU on LGA775 socket 1066/800/533MHz Front Side Bus Intel® Graphics Media Accelerator 950 Dual Channel DDR2 DIMM, maximum 4GB Integrated PCI Express LAN, USB 2.0 and SATA 3Gb/s ATX-945G Product Overview The ATX-945G is an ATX form factor single-processor (x8) and SATA round out the package for a powerful industrial motherboard that is based on the Intel® 945G industrial PC. I/O features of the ATX-945G include a chipset with ICH7 I/O Controller Hub. It supports the Intel® 32-bit/33MHz PCI Bus, 16-bit/8MHz ISA bus, 1x PCI Express Core™2 Duo, Pentium® D, Pentium® 4 with Hyper-Threading x16 slot, 2x PCI Express x1 slots, 3x PCI slots, 1x ISA slot Technology, or Celeron® D Processor on the LGA775 socket, (shared w/ PCI), onboard Gigabit Ethernet, LPC, EIDE Ultra 1066/800/533MHz Front Side Bus, Dual Channel DDR2 DIMM ATA/100, 4 channels SATA 3Gb/s, Mini PCI card slot, UART 667/533/400MHz, up to 4 DIMMs and a maximum of 4GB. The compatible serial ports, parallel port, floppy drive port, HD Intel® Graphic Media Accelerator 950 technology with Audio, and PS/2 Keyboard and Mouse ports. 2048x1536x8bit at 75Hz resolution, PCI Express LAN, USB 2.0 Block Diagram CPU Core™2 Duo Pentium® D LGA775 package 533/800/1066MHz FSB Dual-Core Hyper-Threading 533/800/1066 MHz FSB D I M Northbridge DDR Channel A M ® x Intel 945G GMCH 2 DDRII 400/533/667 MHz D I CRT M M DB-15 DDR Channel B x 2 Discrete PCIe x16 Graphics DMI Interface 2 GB/s IDE Device -

Get More out of the Intel Foxhollow Platform
Get More Out Of the Intel Foxhollow Platform Akber Kazmi, Marketing Director, PLX Technology Introduction As being reported by the mainstream technology media, Intel is leveraging the technology from its latest server-class Nehalem CPU to offer the Lynnfield CPU, targeted for high-end desktop and entry-level servers. This platform is codenamed “Foxhollow “. Intel is expected to launch this new platform sometime in the second half of 2009. This entry-level uni-processor (UP) server platform will feature two to four cores as Intel wants to pack a lot of processing power in all its platforms. The Foxhollow platform is quite different from the previous Desktops and UP servers in that it reduces the solution from three chips to two chips by eliminating the northbridge and replacing the southbridge with a new device called the Platform Controller Hub (or PCH) code named Ibexpeak (5 Series Chipset). As Intel has moved the memory controller and the graphics function into the CPU, there's no need for an MCH (Memory Controller Hub), so Intel has simplified its chipset design to keep costs down in the entry-level and mainstream segments. The PCH chip interfaces with the CPU through Intel’s DMI interconnect. The PCH will support eight PCIe lanes, up to four PCI slots, the GE MAC, display interface controllers, I/O controllers, RAID controllers, SATA controllers, USB 2.0 controllers, etc. Foxhollow Motherboards Foxhollow motherboards are being offered in two configurations, providing either two or three x8 PCIe ports for high performance I/Os. However, motherboard vendors can use an alternate configuration that provides one more PCIe x8 port with no significant burden and instead offers 33% more value than the three port solution and 50% more value than the two port solution. -

Report to the President: MIT and the Prosecution of Aaron Swartz
Report to the President MIT and the Prosecution of Aaron Swartz Review Panel Harold Abelson Peter A. Diamond Andrew Grosso Douglas W. Pfeiffer (support) July 26, 2013 © Copyright 2013, Massachusetts Institute of Technology This worK is licensed under a Creative Commons Attribution 3.0 Unported License. PRESIDENT REIF’S CHARGE TO HAL ABELSON | iii L. Rafael Reif, President 77 Massachusetts Avenue, Building 3-208 Cambridge, MA 02139-4307 U.S.A. Phone 1-617-253-0148 !"#$"%&'(()'(*+,' ' -."%'/%01.220%'34.520#6' ' 78#9.'1"55'(*+*)':;<'="2'4..#'8#>05>.?'8#'.>.#@2'"%828#A'1%0B'"9@80#2'@"C.#'4&'3"%0#'7D"%@E'@0' "99.22'!7<FG'@=%0$A='@=.':;<'90BH$@.%'#.@D0%CI';'=">.'"2C.?'&0$)'"#?'&0$'=">.'A%"980$25&' "A%..?)'@0'%.>8.D':;<J2'8#>05>.B.#@I' ' <=.'H$%H02.'01'@=82'%.>8.D'82'@0'?.29%84.':;<J2'"9@80#2'"#?'@0'5."%#'1%0B'@=.BI'K0$%'%.>8.D' 2=0$5?'L+M'?.29%84.':;<J2'"9@80#2'"#?'?.98280#2'?$%8#A'@=.'H.%80?'4.A8##8#A'D=.#':;<'18%2@' 4.9"B.'"D"%.'01'$#$2$"5'!7<FGN%.5"@.?'"9@8>8@&'0#'8@2'#.@D0%C'4&'"'@=.#N$#8?.#@818.?'H.%20#)' $#@85'@=.'?."@='01'3"%0#'7D"%@E'0#'!"#$"%&'++)'(*+,)'L(M'%.>8.D'@=.'90#@.O@'01'@=.2.'?.98280#2'"#?' @=.'0H@80#2'@="@':;<'90#28?.%.?)'"#?'L,M'8?.#@81&'@=.'822$.2'@="@'D"%%"#@'1$%@=.%'"#"5&282'8#'0%?.%' @0'5."%#'1%0B'@=.2.'.>.#@2I' ' ;'@%$2@'@="@'@=.':;<'90BB$#8@&)'8#95$?8#A'@=02.'8#>05>.?'8#'@=.2.'.>.#@2)'"5D"&2'"9@2'D8@='=8A=' H%01.2280#"5'8#@.A%8@&'"#?'"'2@%0#A'2.#2.'01'%.2H0#284858@&'@0':;<I'P0D.>.%)':;<'@%8.2'90#@8#$0$25&' @0'8BH%0>.'"#?'@0'B..@'8@2'=8A=.2@'"2H8%"@80#2I';@'82'8#'@="@'2H8%8@'@="@';'"2C'&0$'@0'=.5H':;<'5."%#' 1%0B'@=.2.'.>.#@2I' -

Motherboards, Processors, and Memory
220-1001 COPYRIGHTED MATERIAL c01.indd 03/23/2019 Page 1 Chapter Motherboards, Processors, and Memory THE FOLLOWING COMPTIA A+ 220-1001 OBJECTIVES ARE COVERED IN THIS CHAPTER: ✓ 3.3 Given a scenario, install RAM types. ■ RAM types ■ SODIMM ■ DDR2 ■ DDR3 ■ DDR4 ■ Single channel ■ Dual channel ■ Triple channel ■ Error correcting ■ Parity vs. non-parity ✓ 3.5 Given a scenario, install and configure motherboards, CPUs, and add-on cards. ■ Motherboard form factor ■ ATX ■ mATX ■ ITX ■ mITX ■ Motherboard connectors types ■ PCI ■ PCIe ■ Riser card ■ Socket types c01.indd 03/23/2019 Page 3 ■ SATA ■ IDE ■ Front panel connector ■ Internal USB connector ■ BIOS/UEFI settings ■ Boot options ■ Firmware upgrades ■ Security settings ■ Interface configurations ■ Security ■ Passwords ■ Drive encryption ■ TPM ■ LoJack ■ Secure boot ■ CMOS battery ■ CPU features ■ Single-core ■ Multicore ■ Virtual technology ■ Hyperthreading ■ Speeds ■ Overclocking ■ Integrated GPU ■ Compatibility ■ AMD ■ Intel ■ Cooling mechanism ■ Fans ■ Heat sink ■ Liquid ■ Thermal paste c01.indd 03/23/2019 Page 4 A personal computer (PC) is a computing device made up of many distinct electronic components that all function together in order to accomplish some useful task, such as adding up the numbers in a spreadsheet or helping you to write a letter. Note that this defi nition describes a computer as having many distinct parts that work together. Most PCs today are modular. That is, they have components that can be removed and replaced with another component of the same function but with different specifi cations in order to improve performance. Each component has a specifi c function. Much of the computing industry today is focused on smaller devices, such as laptops, tablets, and smartphones. -

ECS P4M890T-M2 Manual.Pdf
Preface Copyright This publication, including all photographs, illustrations and software, is protected under international copyright laws, with all rights reserved. Neither this manual, nor any of the material contained herein, may be reproduced without written consent of the author. Version 1.0B Disclaimer The information in this document is subject to change without notice. The manufacturer makes no representations or warranties with respect to the contents hereof and specifically disclaims any implied warranties of merchantability or fitness for any particular purpose. The manufacturer reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of the manufacturer to notify any person of such revision or changes. Trademark Recognition Microsoft, MS-DOS and Windows are registered trademarks of Microsoft Corp. MMX, Pentium, Pentium-II, Pentium-III, Pentium-4, Celeron are registered trademarks of Intel Corporation. Other product names used in this manual are the properties of their respective owners and are acknowledged. Federal Communications Commission (FCC) This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reason- able protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference -

Shuttle XPC Cube Barebone SH370R6V2 – Connectors
Product Specification Supports 8th/9th generation Intel Core XPC cube Barebone CPUs and up to three UHD displays SH370R6V2 The Shuttle XPC Barebone SH370R6V2 shows how discreet a modern PC can look and at the same time how powerful it can be. Its black- brushed aluminium case has barely a volume of 14 litres, but packs everything you need for a high-performance workstation for example. This includes the power of 8th/9th gen. Intel Core processors, a dual- slot graphics card, fast M.2 NVMe SSD drives, two 3.5’’ hard drives in 8/9th.Gen. 4x DDR4 Dual Triple UHD RAID and up to 128 GB of DDR4 memory, plus a Blu-ray drive. Even Intel Core max. 128GB LAN Display without a dedicated graphics card, up to three UHD displays are supported optionally [3]. Feature Highlights only. purposes illustration for Pictures . Black aluminium chassis (13.6-litre) R6 Chassis Dimensions: 33.2 x 21.5 x 19.0 cm (LWH) Bays: 1x 5.25“, 2x 3.5“ (1x external) Socket LGA 1151v2 supports the 8th and 9th generation Intel Core processors “Coffee Lake” Does not support older LGA 1151 processors. CPU Supports Intel Core i9/i7/i5/i3, Pentium Gold and Celeron Shuttle I.C.E. Heatpipe cooling system Operating Supports Windows 10 and Linux (64-bit) System Optional Optional Intel graphics (depends on CPU [3]) Graphics Supports three digital UHD displays at once Chipset Intel H370 PCH Supports up to 4x 32 GB DDR4-2400/2666 DIMM Memory memory modules (total max. 128 GB) [5] 1x PCIe x16 (v3.0) supports dual-slot graphics Slots cards up to 273 mm length (PCI-E and 1x PCIe x4 (v3.0) M.2) 1x M.2-2280 (SATA / PCIe X4) supports M.2 SSDs 1x M.2-2230 supports WLAN cards SATA 4x SATA 3.0 (6Gb/s) supports RAID and RST Video: HDMI 2.0a and 2x DisplayPort 1.2 Other 4x USB 3.2 Gen 2, 4x USB 3.2 Gen 1, 4x USB 2.0 Connectors 2x Intel LAN. -

J7F3 Mini-ITX Motherboard Series
Mainboard Diagram J7F3 Mini-ITX Motherboard Series -SiS 741CX Northbridge + SiS 964 Southbridge Chipsets -Support Socket-462 AMD Geode NX processor -Support Front Side Bus 133MHz -Single Channel DDR2 400 Memory DIMM -Support 2 Serial ATA Devices with RAID 0, 1 -Support 2xAD Connector With Expansion Daughter-boards -Ethernet LAN Supported -AC’97 6 Channel Audio CODEC -VIA VT6307S IEEE1394a Controller for J7F3E -17 x 17CM Mini-ITX Form Factor Features and Benefits Support Socket 462 AMD Geode™ NX Processor The AMD Geode™ NX processor family gives product designers a wide range of options in low-power, high-performance processors. Based on Mobile AMD Athlon™ processor technology, AMD NX processors deliver superior computing performance for applications including thin-client, point-of-sale terminals, kiosks, high-end printers, and home media systems. AMD Geode Solutions have received new model numbers to better reflect total performance beyond just megahertz. This presentation of attributes gives designers greater understanding of the capabilities of AMD Geode Solutions. SiS 741CX Northbridge Chipset and SiS964 Southbridge Chipset The SiS741CX chipset can be combined with three different AMD Geode NX processors, including the AMD Geode™ NX 1250@6W processor*, AMD Geode™ NX 1500@6W processor** and AMD Geode™ NX 1750@14W processor***, enabling development of a wider variety of products for different market segments. The SiS741CX chipset supports the AMD Geode NX processor family, DDR266 front side bus, as well as high-speed DDR333 DRAM. Furthermore, the SiS741CX chipset incorporates SiS's revolutionary HyperStreaming™ Technology, which provides multiple divided pipelines for data, allows data to be sent concurrently, and separates data for easier memory retrieval, resulting in a remarkable reduction in latency versus traditional chipsets. -

Comparison of High Performance Northbridge Architectures in Multiprocessor Servers
Comparison of High Performance Northbridge Architectures in Multiprocessor Servers Michael Koontz MS CpE Scholarly Paper Advisor: Dr. Jens-Peter Kaps Co-Advisor: Dr. Daniel Tabak - 1 - Table of Contents 1. Introduction ...............................................................................................................3 2. The x86-64 Instruction Set Architecture (ISA) ...................................................... 3 3. Memory Coherency ...................................................................................................4 4. The MOESI and MESI Cache Coherency Models.................................................8 5. Scalable Coherent Interface (SCI) and HyperTransport ....................................14 6. Fully-Buffered DIMMS ..........................................................................................16 7. The AMD Opteron Northbridge ............................................................................19 8. The Intel Blackford Northbridge Architecture .................................................... 27 9. Performance and Power Consumption .................................................................32 10. Additional Considerations ..................................................................................34 11. Conclusion ............................................................................................................ 36 - 2 - 1. Introduction With the continuing growth of today’s multi-media, Internet based culture, businesses are becoming more dependent -
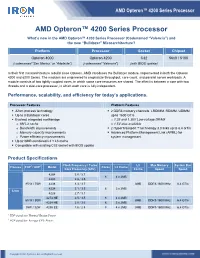
AMD Opteron™ 4200 Series Processor
AMD Opteron™ 4200 Series Processor AMD Opteron™ 4200 Series Processor What’s new in the AMD Opteron™ 4200 Series Processor (Codenamed “Valencia”) and the new “Bulldozer” Microarchitecture? Platform Processor Socket Chipset Opteron 4000 Opteron 4200 C32 56x0 / 5100 (codenamed “San Marino” or “Adelaide”) (codenamed “Valencia") (with BIOS update) In their first microarchitecture rebuild since Opteron, AMD introduces the Bulldozer module, implemented in both the Opteron 4200 and 6200 Series. The modules are engineered to emphasize throughput, core count, and parallel server workloads. A module consists of two tightly coupled cores, in which some core resources are shared. The effect is between a core with two threads and a dual-core processor, in which each core is fully independent. Performance, scalability, and efficiency for today’s applications. Processor Features Platform Features . 32nm process technology . 2 DDR3 memory channels, LRDIMM, RDIMM, UDIMM . Up to 8 Bulldozer cores up to 1600 GT/s . Evolved integrated northbridge o 1.25 and 1.35V Low-voltage DRAM o 8M L3 cache o 1.5V also available o Bandwidth improvements . 2 HyperTransport™ technology 3.0 links up to 6.4 GT/s o Memory capacity improvements . Advanced Platform Management Link (APML) for o Power efficiency improvements system management . Up to16MB combined L2 + L3 cache . Compatible with existing C32 socket with BIOS update Product Specifications Clock Frequency / Turbo L3 Max Memory System Bus Process TDP1 / ACP2 Model Cores L2 Cache Core Frequency (GHz) Cache Speed Speed 4284 3.0 / 3.7 8 4 x 2MB 4280 2.8 / 3.5 95 W / 75W 4238 3.3 / 3.7 8MB DDR3-1600 MHz 6.4 GT/s 4234 3.1 / 3.5 6 3 x 2MB 32nm 4226 2.7 / 3.1 4274 HE 2.5 / 3.5 8 4 x 2MB 65 W / 50W 8MB DDR3-1600 MHz 6.4 GT/s 4228 HE 2.8 / 3.6 6 3 x 2MB 35W / 32W 4256 EE 1.6 / 2.8 8 4 x 2MB 8MB DDR3-1600 MHz 6.4 GT/s 1 TDP stands for Thermal Design Power. -

ESPRIMO Mobile V5505
Issue February 2008 ESPRIMO Mobile V5505 Pages 3 The ESPRIMO Mobile V5505 is a versatile all-round notebook, equally suitable for occasional or professional users, and heavy-duty operation by mobile field sales people. This professional notebook features a superb 15.4-inch WXGA display, an ergonomic keyboard and a built-in super multi DVD writer drive. LAN are integrated for easier connection, courtesy of the latest Intel® Centrino® Duo Mobile Technology based on Intel® 965GM chipset. It has great connections; four USB ports and an integrated 3in1 Card Reader. Connect to printers, scanners, cameras or any other accessory. Elegance Designed for the most demanding mobile users, ESPRIMO Mobile is the perfect synthesis of form, function and style. Power-saving Intel® Centrino® Duo Mobile for long independent working Increased productivity due to latest Intel® 965GM chipset which supports latest technology standards: DDR2 memory, PCI Express and S-ATA Ergonomics Enjoy the viewing quality of brilliant 15.4-inch WXGA TFT display Convenient working with full sized keyboard Connectivity Ideal connectivity through WLAN. Antennas are integrated for best signal reception. Variety of interfaces for best connection to the peripherals Reliability Germany‘s quality standard Award-winning best-in-class manufacturing Mechanical and function stability through extensive quality tests Data Sheet ⏐ Issue: February 2008⏐ ESPRIMO Mobile V5505 Page 2 / 3 System ESPRIMO Mobile V5505 Processor Intel® Core™2 Duo Processor Up to T7500 (2.2 GHz) Second level