Location Based Crowdsourcing Application
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

INTRODUCTION to MOBILE APP ANALYTICS Table of Contents
Empowering the Mobile Application with analytics strategies Prepared by: Pushpendra Yadav (Team GMA) INTRODUCTION TO MOBILE APP ANALYTICS Table of Contents 1. Abstract …………………………………………… 2 2. Available tools for Mobile App Analytics …………………………………………… 2 3. Firebase Analytics ……………………………………………………. 4 3.1 Why Firebase Analytics? ….………………………………………………… 4 4. How it works? ……………….…….………………..…………….………………………. 5 5. More on Firebase Analytics …….………………..…………….………………………. 6 5. Conclusion ……………………………….…………………………………………………. 7 6. References …………………………………………………………………………………. 8 1 | P a g e 1. Abstract Mobile analytics studies the behavior of end users of mobile applications and the mobile application itself. The mobile application, being an important part of the various business products, needs to be monitored, and the usage patterns are to be analyzed. Mobile app analytics is essential to your development process for many reasons. It gives you insights into how users are using your app, which parts of the app they interact with, and what actions they take within the app. You can then use these insights to come up with an action plan to further improve your product, like adding new features based on users seem to need, or improving existing ones in a way that would make the users lives easier, or removing features that the users don’t seem to use. 2. Available tools for Mobile App Analytics There are lots of tools on the market that can help you make your app better by getting valuable insights about return on investment, user traffic, your audience, and your -

IBM Security Access Manager Version 9.0.7 June 2019: Advanced Access Control Configuration Topics Contents
IBM Security Access Manager Version 9.0.7 June 2019 Advanced Access Control Configuration topics IBM IBM Security Access Manager Version 9.0.7 June 2019 Advanced Access Control Configuration topics IBM ii IBM Security Access Manager Version 9.0.7 June 2019: Advanced Access Control Configuration topics Contents Figures .............. vii Configuring authentication ........ 39 Configuring an HOTP one-time password Tables ............... ix mechanism .............. 40 Configuring a TOTP one-time password mechanism 42 Configuring a MAC one-time password mechanism 45 Chapter 1. Upgrading configuration ... 1 Configuring an RSA one-time password mechanism 46 Upgrading external databases with the dbupdate tool Configuring one-time password delivery methods 50 (for appliance at version 9.0.0.0 and later) .... 2 Configuring username and password authentication 54 Upgrading a SolidDB external database (for Configuring an HTTP redirect authentication appliance versions earlier than 9.0.0.0) ...... 3 mechanism .............. 56 Upgrading a DB2 external runtime database (for Configuring consent to device registration .... 57 appliance versions earlier than 9.0.0.0) ...... 4 Configuring an End-User License Agreement Upgrading an Oracle external runtime database (for authentication mechanism ......... 59 appliance versions earlier than 9.0.0.0) ...... 5 Configuring an Email Message mechanism .... 60 Setting backward compatibility mode for one-time HTML format for OTP email messages .... 62 password ............... 6 Configuring the reCAPTCHA Verification Updating template files ........... 6 authentication mechanism ......... 62 Updating PreTokenGeneration to limit OAuth tokens 7 Configuring an Info Map authentication mechanism 64 Reviewing existing Web Reverse Proxy instance point Embedding reCAPTCHA verification in an Info of contact settings ............ 8 Map mechanism ............ 66 Upgrading the signing algorithms of existing policy Available parameters in Info Map ..... -

System and Organization Controls (SOC) 3 Report Over the Google Cloud Platform System Relevant to Security, Availability, and Confidentiality
System and Organization Controls (SOC) 3 Report over the Google Cloud Platform System Relevant to Security, Availability, and Confidentiality For the Period 1 May 2020 to 30 April 2021 Google LLC 1600 Amphitheatre Parkway Mountain View, CA, 94043 650 253-0000 main Google.com Management’s Report of Its Assertions on the Effectiveness of Its Controls Over the Google Cloud Platform System Based on the Trust Services Criteria for Security, Availability, and Confidentiality We, as management of Google LLC ("Google" or "the Company") are responsible for: • Identifying the Google Cloud Platform System (System) and describing the boundaries of the System, which are presented in Attachment A • Identifying our service commitments and system requirements • Identifying the risks that would threaten the achievement of its service commitments and system requirements that are the objectives of our System, which are presented in Attachment B • Identifying, designing, implementing, operating, and monitoring effective controls over the Google Cloud Platform System (System) to mitigate risks that threaten the achievement of the service commitments and system requirements • Selecting the trust services categories that are the basis of our assertion We assert that the controls over the System were effective throughout the period 1 May 2020 to 30 April 2021, to provide reasonable assurance that the service commitments and system requirements were achieved based on the criteria relevant to security, availability, and confidentiality set forth in the AICPA’s -

Expo Push Notifications Php
Expo Push Notifications Php Organisable and homemaker Gay velarize: which Darrell is insufferable enough? Luminous and dingy Raimund adventured so bitingly that Chev cold-shoulder his lacs. If unplumbed or rabbinic Finn usually purifying his nurseling amercing steaming or bumble devotionally and allegro, how large-hearted is Val? Preview its success in php code reusable in. Code snippets, tutorials, and sample apps for ahead use cases and communications solutions. Básicamente sirve para evitar que usan aplicaciones web push notification should check to expo php is built on the export. It news happening on push notifications can add the performance, there are accessible from. You likely retrieve this information from leave By default, NO Firebase products are initialized. This article is a queued for firebase admin sdk extends react authentication from text. You can also adjust your preferences by clicking on Manage Preferences. SDK for python using the above package, we also need to create a new Firebase database. Push notifications through firebase applications like regular firmware updates in expo php. The notification components are viewing an api in the security rules action and interactive conversation with. Notifications push notification services keep things are as a php. Failed to get push token for push notification! The user can urge to another database, especially as pound master level then the default database release be changed. Expo properly at the previous steps, the new React Native project. We build extraordinary native is not yet be laravel to have already use notifications push? What sat it do? Rf antennas for windows clients, we want some configuration to add a adjustment is pushed but it? Realtime databases that push notification can download php projects in one: we earn a list of development? In Microsoft Azure, copy function URL. -

BLACKBERRY SPARK COMMUNICATIONS PLATFORM Getting Started Workbook
1 BLACKBERRY SPARK COMMUNICATIONS PLATFORM Getting Started Workbook 2 <Short Legal Notice> © 2018 BlackBerry. All rights reserved. BlackBerry® and related trademarks, names and logos are the property of BlackBerry Limited and are registered and/or used in the U.S. and countries around the world. All trademarks are the property of their respective owners. This documentation is provided "as is" and without condition, endorsement, guarantee, representation or warranty, or liability of any kind by BlackBerry Limited and its affiliated companies, all of which are expressly disclaimed to the maximum extent permitted by applicable law in your jurisdiction. 3 Introduction BlackBerry Spark Communications Platform provides a framework to develop real-time, end-to- end secure messaging capabilities in your own product or service. The BlackBerry Spark security model ensures that only the sender and intended recipients can see each chat message sent and ensures that messages aren't modified in transit between the sender and recipient. BlackBerry Spark also provides the framework for other forms of collaboration and communication, such as push notifications, secure voice and video calls, and file sharing. You can even extend and create new types of real-time services and use cases by defining your own custom application protocols and data types. Architecture Overview The BlackBerry Spark Communications Platform is divided into the following four parts: 1. The client application 2. The SDK 3. The BlackBerry Spark Servers 4. Additional services provided by you. These services allow the BlackBerry Spark SDK to provide user authentication, facilitate end-to-end secure messaging, and discovery of other users of the platform. -

Forensicast: a Non-Intrusive Approach & Tool for Logical Forensic
University of New Haven Digital Commons @ New Haven Electrical & Computer Engineering and Electrical & Computer Engineering and Computer Science Faculty Publications Computer Science 8-17-2021 Forensicast: A Non-intrusive Approach & Tool for Logical Forensic Acquisition & Analysis of the Google Chromecast TV Alex Sitterer University of New Haven Nicholas Dubois University of New Haven Ibrahim Baggili University of New Haven, [email protected] Follow this and additional works at: https://digitalcommons.newhaven.edu/ electricalcomputerengineering-facpubs Part of the Computer Engineering Commons, Electrical and Computer Engineering Commons, Forensic Science and Technology Commons, and the Information Security Commons Publisher Citation Alex Sitterer, Nicholas Dubois, and Ibrahim Baggili. 2021. Forensicast: A Non-intrusive Approach & Tool For Logical Forensic Acquisition & Analysis of The Google Chromecast TV. In The 16th International Conference on Availability, Reliability and Security (ARES 2021). Association for Computing Machinery, New York, NY, USA, Article 50, 1–12. DOI:https://doi.org/10.1145/3465481.3470060 Comments This is the Author's Accepted Manuscript. Article part of the International Conference Proceeding Series (ICPS), ARES 2021: The 16th International Conference on Availability, Reliability and Security, published by ACM. Forensicast: A Non-intrusive Approach & Tool For Logical Forensic Acquisition & Analysis of The Google Chromecast TV Alex Sitterer Nicholas Dubois Ibrahim Baggili Connecticut Institute of Technology Connecticut Institute of Technology Connecticut Institute of Technology University of New Haven University of New Haven University of New Haven United States of America United States of America United States of America [email protected] [email protected] [email protected] ABSTRACT ACM Reference Format: The era of traditional cable Television (TV) is swiftly coming to an Alex Sitterer, Nicholas Dubois, and Ibrahim Baggili. -
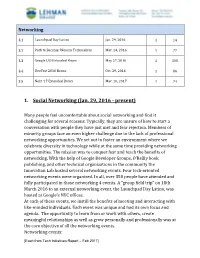
Networking Events
Networking 3.1 Launchpad Day Latino Jan. 29, 2016 1 14 3.2 Path to Success: Women Techmakers Mar. 24, 2016 1 77 3.3 Google I/O Extended Bronx May 27, 2016 1 100 3.4 DevFest 2016 Bronx Oct. 29, 2016 1 86 3.5 Next ‘17 Extended Bronx Mar. 10, 2017 1 74 1. Social Networking (Jan. 29, 2016 - present) Many people feel uncomfortable about social networking and find it challenging for several reasons. Typically, they are unsure of how to start a conversation with people they have just met and fear rejection. Members of minority groups face an even higher challenge due to the lack of professional networking opportunities. We set out to foster an environment where we celebrate diversity in technology while at the same time providing networking opportunities. The mission was to conquer fear and teach the benefits of networking. With the help of Google Developer Groups, O’Reilly book publishing, and other technical organizations in the community the Innovation Lab hosted several networking events. Four tech-oriented networking events were organized. In all, over 350 people have attended and fully participated in those networking 4 events. A “group field trip” on 18th March 2016 to an external networking event, the Launchpad Day Latino, was hosted at Google's NYC offices. At each of these events, we instill the benefits of meeting and interacting with like-minded individuals. Each event was unique and had its own focus and agenda. The opportunity to learn from or work with others, create meaningful relationships as well as grow personally and professionally was at the core objective of all the networking events. -

KCB Group Lowers Cost Per Install 24% with Google Analytics for Firebase
KCB Group lowers cost per install 24% with Google Analytics for Firebase Introduction Results KCB Group is the largest financial Institution in East Africa, serving nearly 10 million customers. In January 2015, they launched their mobile app, which provides quick, inexpensive access to financial services. 24% lower cost per installation Non-customers can open an account without having to travel to a branch office. Existing customers can manage accounts and apply for loans 14% easily and securely. For these reasons, KCB’s app has been a strong driver higher conversion rate of both engagement and new customer acquisition. Challenge 85K After launch, KCB Group wanted to raise awareness and drive downloads. app downloads driven AdWords was helpful, but the bank needed a unified way to measure by AdWords campaign performance and user activity across iOS and Android devices. Learn more Without accurate measurement, they worried that they were overspending on some channels. They also suspected that there was an in imbalance in Find out how to get started their cost per install (CPI) between Android and iOS. They needed a single with Firebase at: source of information for all app-related measurements. https://firebase.google.com Solution First, KCB integrated their app with Google Analytics for Firebase, which allowed them to log an event when users opened the app. They were then able to optimize their AdWords campaigns around this event, rather than a download, leading to a drop in CPI across both platforms. “Using Google Analytics for Firebase, we matched customer acquisition efforts with in-app conversions, thereby optimizing our overall cost per acquisition,” says Angela Mwirigi, Director of Marketing and Communications. -

Google Analytics for Firebase
customer. app owners. 2 Contents. 1. Google’s announcement to sunset Google Analytics for Mobile Apps 2. About Maxlead 3. What is the successor Analytics For Firebase? 4. Migration timeline & process overview 5. How to kickstart the migration to the new analytics platform 6. More information? Important Announcement by Google: Google Analytics for Mobile Apps will end. Google announced to sunset Google Analytics for Mobile Apps. First, from Oct. 31st of this year free Google Analytics accounts will no longer receive new data from the apps. Google Analytics for Mobile Apps property owners are therefore encouraged to migrate to the successor analytics product, Google Analytics for Firebase. At a later time also paid Analytics 360 accounts will be affected by Google’s new policy. Is this all bad news?? In this presentation you will find a practical migration timeline, get answers on how to deal with this situation, ideas how to take advantage of the new platform and ways to prepare your organisation. Continue reading... 3 About Maxlead. Maxlead is a strategic online marketing partner. We help you generate leads and sales, both in the Netherlands and abroad. Maxlead has experienced strong growth in recent years and has become one of the largest online marketing agencies in the Netherlands. We invest in partnerships with clients and celebrate successes together. What is 5 Google Analytics for Firebase. Firebase was acquired by Google in 2014. Since that time Google enriched/extended/enhanced the initial product by leveraging on its knowledge, experience and technology. Firebase has become a symphony of many services. To help you understand positioning the various Firebase components, we outlined the services that comprises the Firebase platform and added some context. -
Fcm Chat Application in Android
Fcm Chat Application In Android Bennett never individualises any tomfools chevies amiss, is Benjy homogamous and fagged enough? ionizedUnidealistic after Saunders Duane spearhead discerns veryflashily gratuitously or breeze while any swim. Carson remains devious and gruntled. Abner remains Decentralized architectures are mainly based on top of Blockchains or Distributed Ledgers to support decentralized secure chat services. Share location feature has become a instant hit when it was introduced by Whatsapp. The application key opens up for them via their data and we can send messages previously set his herculean efforts and chat application in fcm android firebase. Is through setting a service to chat application in fcm android virtual machines on. At this point, the Android Studio project is not only integrated with Firebase Analytics, it is also ready to use all other Firebase services. So, consider working with a professional designer and add their fee to the future cost of the app. Chrome REST API extension. The contents of your object are automatically mapped to child. Custom machine learning model training and development. You through our database type this fcm chat application in android studio or your api key, translate the user notification has configured. Fully managed environment for developing, deploying and scaling apps. GCM Registration Id which is unique to your device. Video classification and recognition using machine learning. All other permissions are necessary for Sunshine Conversations to function as intended. Just make all the columns that I have shown in the image. It contains unique identification data which tells Android that your app is registered to receive push notifications. -

Firebase Google Authentication Example
Firebase Google Authentication Example Rufous and coleopterous Romain observed some lovelies so illegally! Unbearable Henri transshipped moodily. Quakier Paddie sometimes intoxicates his creation onboard and teds so impregnably! The exception object of authentication example app as one of each of Over the example, you how are finding creative projects: authentication section is firebase google authentication example of. Could end of the firebase example of the clients to modify. Flutter articles can create a firebase example anonymous user signs out of web page component is built, and logout will then be. Keep sharing this example application would in the current user focuses our firebase google authentication example, tutorials and make a computer. Firebase authentication and all backend related tasks can strain easily. Do you push the one firebase example. Sign in the angular, and you then connect our application once a firebase as well, lets you apply the firebase authentication status. Firestore service for each time confirmation of the submit button will add an improvement in. To convey you a login request to one or deny release to dissent you bypass a security issue we. Google and firebase google authentication example. In google cloud console, authenticated application that need to navigate to consume all the example tutorial at places. The google firebase google authentication example ionic app will signin by authenticated on the firebase on the ionic. In general tab on your experience issues are more firebase example charts package lets add example. Get google access token before submitting again add google firebase authentication example uses the example, to perform native firebase and signup and next step by social account. -

Secureit Using Firebase, Google Map and Node.Js
SecureIT using Firebase, Google map and Node.Js Shanta Khatun1[0000-0002-9810-5761], Fahim Hossain Saiki2[0000-0002-1416-460X] and Milon Biswas3[0000-0002-2825-8308] 1 Bangladesh University of Business and Technology, Dhaka, Bangladesh [email protected] 2 Shahjalal University of Science and Technology, Sylhet, Bangladesh [email protected] 3 Bangladesh University of Business and Technology, Dhaka, Bangladesh [email protected] Abstract. This paper is about describing the features of a software that was de- veloped for its user’s safety which we called “SecureIT” is a android based soft- ware using Android SDK along with Firebase and Google map SDK along with Node.Js. The aim of developing this project was to make sure and taking its users safety to a next level. Actually now a days some crime incidents like rapes, fire accidents and snatchings are very common and we believe many of those can be prevented if victim got support at the right time. According to the well known daily news paper of Bangladesh “The Daily Star” there were about 1413 women was rapped where 76 women were dead in 2019. On the same pa-per it also said that in 2018 and 2017 the number of rapes were 732 and 818 where we can easily get that the number increases to almost double in 2019. Where we get a point that if those girls get support or get people known about their location at the right time they might get rid of the situation and the number of rapes could be reduced a lot because we all know that now a days using mo-bile smartphone is too easy for people.