Netapp Technical Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dell Vs. Netapp: Don't Let Cloud Be an Afterthought
Dell vs. NetApp: Don’t let cloud be an afterthought Introduction Three waves Seven questions Eight ways to the cloud Contents Introduction 3 Three waves impacting your data center 4 Seven questions to ask about your data center 7 Eight ways you can pave a path to the cloud today 12 Resources 16 2 Introduction Three waves Seven questions Eight ways to the cloud It’s time to put on your belt, suspenders, and overalls Nearly everything seems uncertain Asking you to absorb the full now. With so much out of your control, operating expenses of a forklift data you need to take a comprehensive migration may be good for Dell’s approach to business continuity, as business, but it’s not necessarily the well as to infrastructure disruption. As right thing for your bottom line. It’s an IT professional, you are a frontline time to consider your options. hero responding to the increasing demands of an aging infrastructure In this eBook we’ll help you and an evolving IT landscape. determine where your data center stands, and what you need to have Amid this rapid change, Dell in place so you can pave a path to Technologies is asking you to migrate the cloud today. your data center… again. 3 Introduction Three waves Seven questions Eight ways to the cloud Catch the wave, connect your data, connect the world IT evolution happens in waves. And like ocean waves, one doesn’t come to an end before the next one begins. We see the data services market evolving in three waves: 4 Introduction Three waves Seven questions Eight ways to the cloud First wave: 1 It’s all about infrastructure Users and applications create data, and infrastructure delivers capabilities around capacity, speed, and efficiency. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Serverless Network File Systems
Serverless Network File Systems Thomas E. Anderson, Michael D. Dahlin, Jeanna M. Neefe, David A. Patterson, Drew S. Roselli, and Randolph Y. Wang Computer Science Division University of California at Berkeley Abstract In this paper, we propose a new paradigm for network file system design, serverless network file systems. While traditional network file systems rely on a central server machine, a serverless system utilizes workstations cooperating as peers to provide all file system services. Any machine in the system can store, cache, or control any block of data. Our approach uses this location independence, in combination with fast local area networks, to provide better performance and scalability than traditional file systems. Further, because any machine in the system can assume the responsibilities of a failed component, our serverless design also provides high availability via redundant data storage. To demonstrate our approach, we have implemented a prototype serverless network file system called xFS. Preliminary performance measurements suggest that our architecture achieves its goal of scalability. For instance, in a 32-node xFS system with 32 active clients, each client receives nearly as much read or write throughput as it would see if it were the only active client. 1. Introduction A serverless network file system distributes storage, cache, and control over cooperating workstations. This approach contrasts with traditional file systems such as Netware [Majo94], NFS [Sand85], Andrew [Howa88], and Sprite [Nels88] where a central server machine stores all data and satisfies all client cache misses. Such a central server is both a performance and reliability bottleneck. A serverless system, on the other hand, distributes control processing and data storage to achieve scalable high performance, migrates the responsibilities of failed components to the remaining machines to provide high availability, and scales gracefully to simplify system management. -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -
![NASD) Storage Architecture, Prototype Implementations of [Patterson88]](https://docslib.b-cdn.net/cover/0551/nasd-storage-architecture-prototype-implementations-of-patterson88-190551.webp)
NASD) Storage Architecture, Prototype Implementations of [Patterson88]
Proceedings of the 8th Conference on Architectural Support for Programming Languages and Operating Systems, 1998. A Cost-Effective, High-Bandwidth Storage Architecture Garth A. Gibson*, David F. Nagle†, Khalil Amiri†, Jeff Butler†, Fay W. Chang*, Howard Gobioff*, Charles Hardin†, Erik Riedel†, David Rochberg*, Jim Zelenka* School of Computer Science* Department of Electrical and Computer Engineering† Carnegie Mellon University, Pittsburgh, PA 15213 [email protected] ABSTRACT width, that is, linearly increasing application bandwidth with increasing numbers of storage devices and client processors, This paper describes the Network-Attached Secure Disk the data must be striped over many disks and network links (NASD) storage architecture, prototype implementations of [Patterson88]. With 1998 technology, most office, engineer- NASD drives, array management for our architecture, and ing, and data processing shops have sufficient numbers of three filesystems built on our prototype. NASD provides scal- disks and scalable switched networking, but they access stor- able storage bandwidth without the cost of servers used age through storage controller and distributed fileserver primarily for transferring data from peripheral networks bottlenecks. These bottlenecks arise because a single (e.g. SCSI) to client networks (e.g. ethernet). Increasing “server” computer receives data from the storage (periph- eral) network and forwards it to the client (local area) dataset sizes, new attachment technologies, the convergence network while adding -
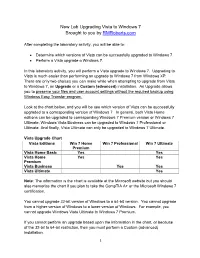
Performing a Windows 7 Upgrade from Windows Vista
New Lab Upgrading Vista to Windows 7 Brought to you by RMRoberts.com After completing the laboratory activity, you will be able to: Determine which versions of Vista can be successfully upgraded to Windows 7. Perform a Vista upgrade o Windows 7. In this laboratory activity, you will perform a Vista upgrade to Windows 7. Upgrading to Vista is much easier than performing an upgrade to Windows 7 from Windows XP. There are only two choices you can make while when attempting to upgrade from Vista to Windows 7, an Upgrade or a Custom (advanced) installation. An Upgrade allows you to preserve your files and user account settings without the required backup using Windows Easy Transfer program. Look at the chart below, and you will be see which version of Vista can be successfully upgraded to a corresponding version of Windows 7. In general, both Vista Home editions can be upgraded to corresponding Windows 7 Premium version or Windows 7 Ultimate. Windows Vista Business can be upgraded to Windows 7 Professional or Ultimate. And finally, Vista Ultimate can only be upgraded to Windows 7 Ultimate. Vista Upgrade Chart Vista Editions Win 7 Home Win 7 Professional Win 7 Ultimate Premium Vista Home Basic Yes Yes Vista Home Yes Yes Premium Vista Business Yes Yes Vista Ultimate Yes Note: The information is the chart is available at the Microsoft website but you should also memorize the chart if you plan to take the CompTIA A+ or the Microsoft Windows 7 certification. You cannot upgrade 32-bit version of Windows to a 64-bit version. -

File Manager Manual
FileManager Operations Guide for Unisys MCP Systems Release 9.069W November 2017 Copyright This document is protected by Federal Copyright Law. It may not be reproduced, transcribed, copied, or duplicated by any means to or from any media, magnetic or otherwise without the express written permission of DYNAMIC SOLUTIONS INTERNATIONAL, INC. It is believed that the information contained in this manual is accurate and reliable, and much care has been taken in its preparation. However, no responsibility, financial or otherwise, can be accepted for any consequence arising out of the use of this material. THERE ARE NO WARRANTIES WHICH EXTEND BEYOND THE PROGRAM SPECIFICATION. Correspondence regarding this document should be addressed to: Dynamic Solutions International, Inc. Product Development Group 373 Inverness Parkway Suite 110, Englewood, Colorado 80112 (800)641-5215 or (303)754-2000 Technical Support Hot-Line (800)332-9020 E-Mail: [email protected] ii November 2017 Contents ................................................................................................................................ OVERVIEW .......................................................................................................... 1 FILEMANAGER CONSIDERATIONS................................................................... 3 FileManager File Tracking ................................................................................................ 3 File Recovery .................................................................................................................... -
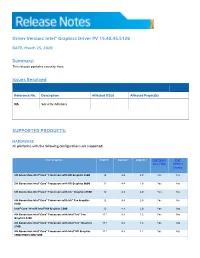
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism. -

Data File Manager
Data File Manager Welcome to Data File Manager! Thank you for using the data file manager. Highlights of the data file manager are as follows: Intuitive operability Buttons on the tool menu, drag & drop, and context menu with a right click are supported to use each function. Tree view for data in SD memory card Files and folders in SD memory card are shown in a tree structure and target files can easily be found. Operations for files and folders Files and folders can be added, renamed or deleted. PLC maintenance Viewing the PLC status, such as Run/Stop state or error status, downloading/uploading user programs, or upgrading the system software of the PLC are supported. MICRO/I maintenance Viewing the target information, such as system software version or external memory device information, or downloading/uploading project is supported. Notes - Data File Manager There are the following notes when you use Data File Manager: Supported hardware Data File Manager supports the following hardware: FC4A series MICROSmart FC5A series MICROSmart Pentra FC6A series MICROSmart FT1A series SmartAXIS expect FT1A Touch HG3G/4G series MICRO/I HG2G-5F series MICRO/I HG2G-5T series MICRO/I HG1G series MICRO/I SD card access (SmartAXIS Pro & Lite) SD card inserted on SmartAXIS series can be accessed while the PLC is stopped only. Downloading or uploading the user program (PLC) You can download or upload the user programs using ZLD files, which can be created or read with WindLDR. Downloading or uploading the project (MICRO/I) You can download or upload the project using ZNV files, which can be created or read with WindO/I-NV4. -

Infrastructure : Netapp Solutions
Infrastructure NetApp Solutions NetApp October 06, 2021 This PDF was generated from https://docs.netapp.com/us-en/netapp-solutions/infra/rhv- architecture_overview.html on October 06, 2021. Always check docs.netapp.com for the latest. Table of Contents Infrastructure . 1 NVA-1148: NetApp HCI with Red Hat Virtualization. 1 TR-4857: NetApp HCI with Cisco ACI . 84 Workload Performance. 121 Infrastructure NVA-1148: NetApp HCI with Red Hat Virtualization Alan Cowles, Nikhil M Kulkarni, NetApp NetApp HCI with Red Hat Virtualization is a verified, best-practice architecture for the deployment of an on- premises virtual datacenter environment in a reliable and dependable manner. This architecture reference document serves as both a design guide and a deployment validation of the Red Hat Virtualization solution on NetApp HCI. The architecture described in this document has been validated by subject matter experts at NetApp and Red Hat to provide a best-practice implementation for an enterprise virtual datacenter deployment using Red Hat Virtualization on NetApp HCI within your own enterprise datacenter environment. Use Cases The NetApp HCI for Red Hat OpenShift on Red Hat Virtualization solution is architected to deliver exceptional value for customers with the following use cases: 1. Infrastructure to scale on demand with NetApp HCI 2. Enterprise virtualized workloads in Red Hat Virtualization Value Proposition and Differentiation of NetApp HCI with Red Hat Virtualization NetApp HCI provides the following advantages with this virtual infrastructure solution: • A disaggregated architecture that allows for independent scaling of compute and storage. • The elimination of virtualization licensing costs and a performance tax on independent NetApp HCI storage nodes.