Application Programming Interface (API) Task Force Recommendations May 12, 2016
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Name Integration Status Market Supported Products Cerner Live
Name Integration Market Supported Products Status Cerner Live EHR Millenium (includes the Cerner HIE) product; PowerWorks product DrFirst Live EHR / E- EPCS Gold with PDMP Access Prescribing Epic Live EHR Epic EMR - versions may be customized by facility Glenwood Systems, LLC Live EHR GlaceEMR Lagniappe Pharmacy Live Pharmacy Rx1/Synercom Services (LPS) Medent Live EHR Medent EHR Medicity Live HIE Unknown PDX Live E- EPS (Enterprise); will require additional software updates based Prescribing on customer, release 2.6.06 or higher. PioneerRx Live Pharmacy PioneerRx ProComp Live EHR CATT EHR v3.5 QS/1 Live Pharmacy NRx; Primecare; SharpRx Transaction Data Live Pharmacy Rx30 (build 16217 or higher) Systems (TDS) NOTE - RX30 is Linux only and does not support Windows. 2/2/18 Allscripts In Development EHR Sunrise; Touchworks; Professional EHR; EHR Aprima Live EHR Aprima PRM (2016 Patch A and later) Amazing Charts Testing EHR Unknown AthenaHealth In Development EHR Athena Clinicals Bizmatics Live EHR PrognoCIS eClinicalWorks (eCW) Live EHR eClinicalWorks V11 e-MDs No Progress EHR e-MDs solution series 8.0 GE Health Testing EHR CPS 12.3 and newer; CEMR 9.12 and newer (customer will need to upgrade in order to have access to the functionality). Greenway Health In Review EHR Prime Suite; Intergy (largest customer-base); Success EHS Health Business Testing RxAXIS (17.8 or higher) Systems (HBS) RxGENESYS (still in development) McKesson (Pharmacy) In Development Pharmacy PharmacyRx; EnterpriseRx; Pharmaserve Netsmart Live EHR Built in OrderConnect (OE) & accessible from the following Care (Behavioral Records when they are used in an integrated fashion with OE: Health) MyAvatar, MyEvolv, TIER, MIS, MyHelper. -

Placing Customer Centricity at the Heart of Healthcare
Exerpted Articles From: Placing Customer Centricity at the Heart of Healthcare A look at how healthcare providers, pharmaceuticals, and health insurers are adapting to the changing customer landscape and evolving their patient experiences Table of Contents: An Eye on Healthcare’s Wearable Future ......................................................... 2 What the Net Neutrality Debate Means to Healthcare ................................... 17 Making Way for Consumerized Healthcare ..................................................... 5 Healthcare’s Cybersecurity Threat ................................................................. 19 Boosting Patient Outcomes with Big Data ...................................................... 7 United Healthcare Gives Behavioral Analytics a Seat at the Table ................ 21 Healthcare Accountability: Sizing Up the Metrics for Meet Healthcare’s Newest Players ................................................................ 22 Delivering Value-Based Care ......................................................................... 10 Taking the Pulse of Customer Service ........................................................... 25 The Top Healthcare Tech Trends to Watch in 2015 ....................................... 12 A Prescription for Patient-Centric Healthcare ................................................ 28 Balancing Act: How Population Health Impacts Individuals ......................... 15 Cigna Personalizes Its Approach to Healthcare Customer Service .............. 31 Healthcare An Eye on -

Software & Services
SOFTWARE & SERVICES Recognizing the software and service organizations that excelled in helping providers deliver better patient care PHYSICIAN PRACTICE SOLUTIONS BEST IN KLAS AMBULATORY EMR (1–10 PHYSICIANS) HOW DO VENDOR SOLUTIONS COMPARE? WHO IS KONFIDENCE SCORE TREND LEVEL 1. Cerner PowerChart Ambulatory BEST IN KLAS? 84.3 +13% üü 2. Amazing Charts 83.3 +4% üüü 3. SRSsoft EHR 81.0 -11% üü 4. athenahealth athenaClinicals 80.9 -7% üüü 5. Greenway PrimeSUITE Chart 79.1 -2% üüü HOW DO THEY SCORE? 6. Aprima EHR IN FIVE KEY PERFORMANCE CATEGORIES 78.2 -1% üüü 100 92.4 7. ADP AdvancedMD EHR +3% üüü 90 84.9 78.0 80.6 81.7 81.2 80 8. e-MDs Chart -13% üüü 70 74.0 60 AVG. SEGMENT MKT. 9. GE Healthcare Centricity Practice Solution EMR +1% üü PHYSICIAN PRACTICE PHYSICIAN 50 73.8 40 T10. eClinicalWorks EHR 73.4 -7% üüü 30 20 T10. Henry Schein MicroMD EMR 73.4 +4% üü 10 12. NextGen Healthcare EHR 0 65.1 -3% üüü SALES & FUNCTIONALITY GENERAL CONTRACTING & UPGRADES 13. Allscripts Professional EHR 64.7 -6% üüü SERVICE & IMPLEMENTATION SUPPORT 14. McKesson Practice Partner -14% & TRAINING 48.0 üü 0 10 20 30 40 50 60 70 80 90 100 SEE HOW OTHER VENDOR SOLUTIONS SCORE AT KLASRESEARCH.COM HOW DO THE TOP THREE SOLUTIONS TREND? SOLUTIONS NOT RANKED PRELIMINARY DATA PRODUCTS CompuGroup Medical Enterprise EHR (HEHR)*..................71.0 MIE WebChart EMR* ............................................................75.7 MTBC EMR* .........................................................................82.1 Optum Physician EMR* ........................................................79.6 -

Top 20 Ehr Software
TOP 20 EHR SOFTWARE C M CONVERTED MEDIA TOP 20 EHR SOFTWARE 1 AdvancedMD AdvancedEHR 11 Allscripts Allscripts Professional EHR 2 Cerner Cerner Ambulatory EHR 12 CareCloud CareCloud Charts 3 athenahealth athenahealth EHR 13 CureMD All in One EHR 4 Epic Epic EHR 14 Practice Velocity VelociDoc EHR Azalea Health 5 Practice Fusion Practice Fusion EHR 15 Azalea EHR Innovations 6 Kareo Kareo Clinical 16 ReLi Med Solutions ReLiMed EMR 7 Henry Schein MicroMD EMR 17 MedEZ MedEZ 8 drchrono drchrono EHR 18 iSALUS Healthcare OfficeEMR 9 NextGen Healthcare NextGen Healthcare EHR 19 ChartLogic ChartLogic EMR Modernizing 10 EMA 20 ICANotes ICANotes EHR Medicine C M CONVERTED MEDIA EHR IN PRACTICE HOW THESE RANKINGS WERE GENERATED This ranking was determined using a number of factors including industry standing, public opinion of software, social media presence, and available software features relevant to the needs of a small business. This ranking should serve as a rough estimate of software suitability, and more in-depth analysis can be taken below or by using our EHR software comparison. C M CONVERTED MEDIA SHORTLISTING EHR VENDORS CHECKLIST Research EHR employed by similar sized practices in 1 6 Produce an RFI document and send to vendor shortlist the same specialty Identify market leading solutions which offer some 2 7 Narrow shortlist based on RFI responses support in your specialty Leverage professional network for recommendations Compile requirements and business processes in an 3 8 based on their experience RFP document Narrow shortlist based -

EHR Vendors Who Have Onboarded
Vendors that sent passed the NIST cases, in Testing or in Production with CT WiZ Vendor Product_Name Version Status Advanced Business Software LLC Public Health Information Management System (PHIMS) v.20.5 In Testing with CT WiZ Advanced Data Systems Doc Assist 2015 edition CEHRT In Testing with CT WiZ ADVANCEDMD advancedmd ehr 12.8 In Testing with CT WiZ Allscripts Touchworks EHR 17.1 CU3 WC3 In Production with CT WiZ Amazing Charts Amazing Charts 10.0.2 NIST cases passed Aprima Medical Software, Inc Aprima PRM 2016 RC 16.0.0.576 In Production with CT WiZ Athenahealth, Inc AthenaHealth, Inc In Testing with CT WiZ Cerner Corporation Cerner Corporation In Testing with CT WiZ CureMD CureMD 10G In Testing with CT WiZ eClinicalWorks LLC ECLINICALWORKS EMR 11 In Production with CT WiZ e-MDs, Inc e-MDs, Inc In Production with CT WiZ Epic Epic 2018 In Production with CT WiZ FUSION Centricity CPS 12 In Production with CT WiZ Glenwood Systems LLC GLACEEMR 6.0 In Production with CT WiZ Greenway Health Intergy V. 11.10.00.51 In Production with CT WiZ Harris Caretracker Harris Caretracker v9.9.2018 In Production with CT WiZ Insync Insync In Testing with CT WiZ Iron Bridge Integration Iron Bridge Integration In Production with CT WiZ Medent MEDENT EMR/EHR 23.0 In Production with CT WiZ MEDITECH MEDITECH 6.08 In Testing with CT WiZ NextGen Healthcare Rosetta 5.9.0.124 In Production with CT WiZ OFFICE PRACTICUM OFFICE PRACTICUM 20.0.0 In Testing with CT WiZ Patagonia Health Patagonia Health EHR 5.0 In Production with CT WiZ Physicians Computer Company PCC HER 8.6 In Production with CT WiZ Practice Fusion Practice Fusion EHR 3.5 In Production with CT WiZ PrescribeWellness SMP SMP 2 In Production with CT WiZ Scientific Technologies Corporation ImmsLink 3.4 In Production with CT WiZ STI Computer Services ChartMaker Medical Suite 2016 In Production with CT WiZ Transact RX Transact RX In Testing with CT WiZ Revised: 04/13/2021 * If your clinic has the same vendor, product and version, you only need to send the CT WiZ HL7 Application form to start the onboarding . -

Top Integrated Electronic Health Records Physician Practice Management & Billing Vendors
BLACK BOOK RANKINGS 2014 USER SURVEY Top Integrated Electronic Health Records Physician Practice Management & Billing Vendors Publication Date: May 2014 Electronic Health Records Ambulatory Practice Management Software Solutions Outsourced Revenue Cycle Management Services BLACK BOOK™ TOP INTEGRATED PRACTICE MANAGEMENT & REVENUE CYCLE MANAGEMENT EHR SOFTWARE VENDORS May 2014 ©2014 Black Book Rankings LLC. This report is a licensed product. Do not duplicate or distribute without permission. Page 1 2014 Black Book Integrated Practice Management – Revenue Cycle Management EHR Software Top Vendors Report Black Book™ annually evaluates leading health care/medical software and service providers across 18 operational excellence key performance indicators completely from the perspective of the client experience. Independent and unbiased from vendor influence, more than 380,000 healthcare IT users are invited to contribute to various annual customer satisfaction polls. Suppliers also encourage their clients to participate to produce current and objective customer service data for buyers, analysts, investors, consultants, competitive suppliers and the media. For more information or to order customized research results, please contact the Client Resource Center at +1 727.953.3355 or [email protected] © 2014, 2013 Black Book Rankings LLC All Rights Reserved. Reproduction of this publication in any form without prior written permission is forbidden. The information contained herein has been obtained from sources believed to be reliable. Brown-Wilson Group, Inc. the parent corporation of Black Book™, Black Book Rankings LLC, Black Book Market Research LLC, and The Black Book of Outsourcing®, disclaims all warranties as to the accuracy, completeness or adequacy of such information. Brown-Wilson Group shall have no liability for errors, omissions or inadequacies in the information contained herein or for interpretations thereof. -

A Survey of U.S. Healthcare IT Industry Landscape
July 28, 2016 Industry Research Department, Mizuho Bank Mizuho Industry Focus Vol. 183 A Survey of U.S. Healthcare IT Industry Landscape Global Corporate Advisory Americas Tim Wang, CFA, 2016 [email protected] 〈Summary〉 ○ U.S. Healthcare IT industry is booming. Over the recent years, many companies have had robust growth and the sector has attracted huge inflow of private and public investments. There are many types of HCIT companies, operating with different business models and participating in various segments of HCIT. In this report, we try to first identify the drivers behind HCIT growth and then delineate the dynamics in each HCIT segment. ○ Key drivers of HCIT are also the underlying drivers of the U.S. healthcare system, namely Obamacare, the transition to value-based reimbursement model, rising consumerism, industry consolidation, etc. Within HCIT, major drivers include the HITECH Act, advancement of technology, and the convergence of healthcare, IT, and consumer industries. ○ The booming HCIT market is in transition. Incentives for EHR created by the HITECH Act have largely run their course. In the future, the marketplace will be driven less by government subsidies and more by private spending. To earn revenues from private payers, HCIT companies increasingly need to demonstrate the clinical and financial value of their offerings. To achieve this, HCIT companies need to collaborate closely with their customers. ○ For the various HCIT segments, we see three especially promising areas – integration of remote patient monitoring either through wearables or other devices with data analytics and intervention capabilities; big data analytics by Artificial Intelligence; and telemedicine. We expect stable growth for RCM, PM, payer solution segments. -

Ehr Software Vendor Directory
EHR SOFTWARE VENDOR DIRECTORY 2017 Edition C M CONVERTED MEDIA OVERVIEW CONTACT ADP acquired AdvancedMD, an established provider of EHR solutions for private practice healthcare environments in 2011. ADP AdvancedMD With ADP, the AdvancedMD product offerings have expanded to include an enhanced in-house billing suite, medical coding 10876 S River Front Pkwy capabilities and integration with outsourced medical billing providers. Suite 400 South Jordan ADP AdvancedMD EHR provides functionality for medical practices as well as components designed for administrative and UT billing use. 84095 United States For medical practices, ADP AdvancedMD EHR provides a patient portal for admissions and check-ins alongside document 800-825-0224 management, e-prescriptions and more. All of this is available as a mobile platform on iOS devices. [email protected] Role-based access to the EHR for nurses and physicians improves workflow by limiting system complexity for each role. During the medical coding and billing phase, there are options to present the information for in-house coders or to integrate it with the API from an outsourced medical billing company. The ADP AdvancedMD EHR and revenue cycle management solutions are available to clients via a tiered subscription access program. There is an initial installation and training fee, and then clients may select “a-la-carte” options for their subscription package that are best suited to their practice. COMPARE ADP ADVANCEDMD EHR & MANY MORE ADP AdvancedMD EHR provides a complete healthcare solution for practices of any size. Their products are cloud based, Compare software features, mobile accessible but can also be installed as desktop only. -
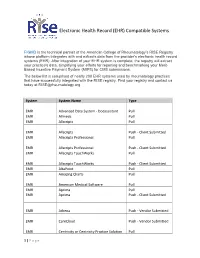
Electronic Health Record (EHR) Compatible Systems
Electronic Health Record (EHR) Compatible Systems FIGMD is the technical partner of the American College of Rheumatology’s RISE Registry whose platform integrates with and extracts data from the provider’s electronic health record systems (EHR). After integration of your EHR system is complete, the registry will extract your practice's data, simplifying your efforts for reporting and benchmarking your Merit- Based Incentive Payment System (MIPS) for CMS submissions. The below list is comprised of nearly 200 EHR systems used by rheumatology practices that have successfully integrated with the RISE registry. Find your registry and contact us today at [email protected]. System System Name Type EMR Advanced Data System - Docassistant Pull EMR Allmeds Pull EMR Allscripts Pull EMR Allscripts Push - Client Submitted EMR Allscripts Professional Pull EMR Allscripts Professional Push - Client Submitted EMR Allscripts TouchWorks Pull EMR Allscripts TouchWorks Push - Client Submitted EMR AltaPoint Pull EMR Amazing Charts Pull EMR American Medical Software Pull EMR Aprima Pull EMR Aprima Push - Client Submitted EMR Athena Push - Vendor Submitted EMR CareCloud Push - Vendor Submitted EMR Centricity or Centricity Practice Solution Pull 1 | P a g e Electronic Health Record (EHR) Compatible Systems EMR Cerner Pull System System Name Type EMR Cerner Push - Vendor Submitted EMR Cerner - Power Chart Push - Vendor Submitted EMR Chart Maker Clinical Pull EMR Chart Perfect Pull EMR ChartLogic Pull EMR ChartLogic Push - Vendor Submitted EMR Chartmaker Medical -

Top Ambulatory Electronic Health Records Vendors Dermatology
BLACK BOOK MARKET RESEARCH 2015 SURVEY Top Ambulatory Electronic Health Records Vendors Part One: Aggregate Black Book Survey Findings Part Two: Data Set of Top EHR Vendors, Specialists Ambulatory EMR/EHR Physician Practices, Groups & Facilities Dermatology Top Electronic Medical Records/Electronic Health Records Vendors Published March 2015 © Black Book Market Research. This report is a licensed product. Page 1 Black Book Market Research LLC, a division of Brown-Wilson Group Inc. annually evaluates leading healthcare/medical software and service providers across 18 operational excellence key performance indicators completely from the perspective of the client experience. Independent and unbiased from vendors’ influence, Over 420,000 healthcare IT users are invited to contribute. Suppliers also encourage their clients to participate to produce current and objective customer service data for buyers, analysts, investors, consultants, competitive suppliers and the media. For more information or to order customized research results, please contact the Client Resource Center at +1 800 863 7590 or [email protected] © 2014, 2015 Black Book Market Research LLC. All Rights Reserved. Reproduction of this publication in any form without prior written permission is forbidden. The information contained herein has been obtained from sources believed to be reliable. Brown-Wilson Group disclaims all warranties as to the accuracy, completeness or adequacy of such information. Brown-Wilson Group shall have no liability for errors, omissions or inadequacies in the information contained herein or for interpretations thereof. The reader assumes sole responsibility for the selection of these materials to achieve its intended results. The opinions expressed herein are subject to change without notice. -

YOU MAY PURCHASE the COMPLETE 268 PAGE REPORT at AMAZON.COM in the BLACK BOOK MARKET RESEARCH STORE Or (Search Amazon.Com For
THE FOLLOWING DATA IS AN EXCERPT FROM BLACK BOOK’S PROPRIETARY RESEARCH REPORT “STATE OF THE EHR REPLACEMENT MARKET PLACE: 2013 CONDITIONS & TOP PERFORMING VENDORS” DO NOT COPY, DUPLICATE, DISTRIBUTE OR REFERENCE THIS DOCUMENT EXCERPT WITHOUT FIRST RECEIVING WRITTEN PERMISSION FROM BROWN-WILSON GROUP. CONTACT DOUG BROWN, MANAGING PARTNER AT [email protected] YOU MAY PURCHASE THE COMPLETE 268 PAGE REPORT AT AMAZON.COM IN THE BLACK BOOK MARKET RESEARCH STORE http://tinyurl.com/ovvonnk or (Search Amazon.com for “Year of the Big EHR Switch”) © 2010, 2011, 2012, 2013 Brown-Wilson Group, Inc. All Rights Reserved. Do not duplicate or distribute without permission. EXECUTIVE SUMMARY: EHR REPLACEMENT MARKET VENDOR CLIENT EXPERIENCE METHODOLOGY BLACK BOOK RANKINGS, THE RECOGNIZED SOURCE FOR NEUTRAL AND PRECISE CUSTOMER SATISFACTION ANALYSIS IN THE HEALTHCARE INFORMATION TECHNOLOGY INDUSTRY, FIRST UNCOVERED THE SURGING WAVE OF USABILITY DISSATIFACTION AMONG EHR USERS IN THE 2012 ANNUAL CLIENT EXPERIENCE SURVEYING. THE FOLLOWING YEAR'S (2013) POLLING RESULTS REVEALED THE ISSUES HAD ESCALATED TO THE POINT THAT BETEEN 17% AND 31% OF ALL EHR-IMPLEMENTED PRACTICES WERE CONSIDERING SWITHCING VENDORS DUE TO UNMET EXPECTATIONS, LACK OF FUNCTIONALITY OR INNOVATION. NEARLY HALF OF ALL EHR USERS INDICATED THEY WOULD SHIFT TO ANOTHER VENDOR IF COST & LOSS OF PRODUCTIVITY WERE NOT ISSUES. EHR MARKET SHIFTERS NOW POSE TO REALLOCATE MORE THAN $5 BILLION IN SALES AS THE UNSTABLE VENDOR MARKETPLACE HEATS UP. FOLLOW-UP BLACK BOOK POLLS WERE CONDUCTED IN Q2 2013 TO STUDY VENDOR PREFERENCES DURING THIS “YEAR OF THE BIG EHR SWITCH” INCLUDING 500 TELEPHONE SURVEYS AND 2,900 ONLINE BALLOTS TO DETERMINE THE MOST POPULAR EHR SYSTEMS AMONG REPLACEMENT SYSTEM BUYERS. -
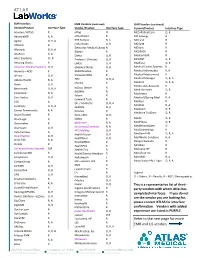
Refer to the Next Page for More EMR and LIS Vendors
EMR Vendors EMR Vendors (continued) EMR Vendors (continued) Vendor/Product Interface Type Vendor/Product Interface Type Vendor/Product Interface Type Acumen / HITSG R eFlag O MCS iPatientCare O, R AdvanceMD R, A eHealthcare R MD Synergy A Agility O, R, A EHS Success R, A MDLand R AllMeds R eInformatix O, R MDSuite R Electronic Medical Charts R MDSync R Allscripts O, R, A Elation R MED3000 R AltaPoint R, A Elekta O, R MedcomSoft R Altos Solutions O , R Emdeon / Clincians O, R MEDENT O, R Amazing Charts R eMDS O, R Medhost O, R American Medical Systems O, R eMedical Notes O, R Medical Comm Systems R Answers—AOD R EMEDPractice R Medical Informatics R, A aPrima O, R EncounterPRO R Medical Mastermind R Medical Manager O, R, A Athena Health R, A EPIC O, R, A eScribe R Medicat O, R, A Axion O, R Medics Doc Assistant R eZDocs Dexter R Benchmark O, R, A MedInformatix O, R EzEMRx R CareCloud R, A Medinotes R Falcon R CareTracker O, R Medisoft/Spring Med R, A Gamwell Tech R CDS A Medisys R GE / Centricity O, R, A Meditab R, A Centricity O, R, A GEMMS O, R Meditech O, R Cerner Powerworks R, A Genesis R Mediture TruChart O, R CharmTracker R GeniusDoc O, R, ChartLogic R GMed R Medix O, R MedPlexus O, R Chartmaker R gloStream R, A MedRecordsAlert O Chartware O, R Greenway (Emdeon) R, A HDS MyWay O, R MedStream(ing) R CHS-ClinView A Health Fusion O, R MedSym EHR O, R, A ClearPractice O, R Healthland O, R MedWorks Solutions R, A Clinix MD R, A HealthMEDX R Merge Flexisuite R Clinlab R HealthPAC R Meridian R CoCentrix (frmly Unicare) O,R HealthsTrio R