Department of Computer Science Security Policy Cognizant Module
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Broadband and Mobile
Benenden Parish Plan Communication: Broadband and Mobile Issue 1.1 03/05/2014 Benenden Broadband and Mobile Key Points Broadband Introduction of Superfast Broadband should be complete by March 2015. 96% of postcodes within the TN17 4xx Benenden exchange area will attain Superfast Broadband speeds (25 Mbps and above) Only BT and Talk Talk have their own broadband equipment in Benenden Exchange providing maximum speeds of up to 24 Mbps. Other ISPs use a BT Wholesale connection enabling service at either 24 Mbps or just 8 Mbps (e.g. Sky) WiFi Broadband may be available for some households in Benenden from CallFlow and VFast 4G Mobile services will enable broadband comparable speeds beginning in Benenden during 2014 Poor broadband performance may be due to electrical interference and internal (or external) wiring problems. Mobile O2 have plans to improve 2G and 3G coverage and also introduce 4G services in 2014. Home coverage can also be improved by using a signal booster (femtocell) PAYG SIM cards can be a useful tool to determine the best provider in addition to online network coverage maps. If you decide to change provider your current mobile company will inevitably offer you inducements to stay (e.g. lower charges, improved terms, free femtocell). This also applies to Broadband. Broadband DSL Broadband (Digital Subscriber Line) The most significant (but not the only) factor limiting Broadband speed is the physical distance between the household and the equipment in the telephone exchange. Rural telephone exchange areas tend to be larger than those in urban areas and therefore people are more likely to live further from the exchange and consequently suffer from poor broadband performance. -
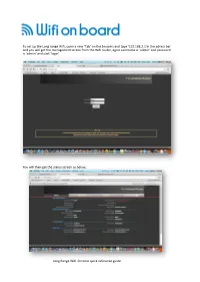
Long Range Wifi Tube Settings
To set up the Long range Wifi, open a new ‘Tab’ on the browers and type ‘192.168.2.1’in the adress bar and you will get the management screen from the Wifi router, again username is ‘admin’ and password is ‘admin’ and click ‘login’ You will then get the status screen as below, Long Range Wifi Chrome quick reference guide Click ‘Easy Setup and select the WAN connections and ‘Client Router Mode’ and click on ‘Next’ On the next screen click ‘Site Survey” Long Range Wifi Chrome quick reference guide This will bring up a screen with all the available WiFi hotspots in the area. Select the WiFi Hotspot you require, the system will connect to most Wifi access points with a signal greater than -80dB ie -79dB to 0dB. Select the Wifi you want in this case BT with FON and click ‘Select’ N o w If you have selected a known Wifi with and access code you will be asked to enter this as the ‘Passkey’ So if you have been to a Bar and have the code this is where you enter it. Set the power level to 24-27 if requires some units do not have this field.. Long Range Wifi Chrome quick reference guide Select Next on the following screens until you reach done and the unit will reboot. Open another tab on you browser and you shold be connected to the Internet, you can also log back into the Long ranage WiFi on 192.168.2.1 and check the status of the connection If you are connected as in this case to BT Openzone, enter your account details and connect to the internet, all other devices will not need to logon to BT or the Public Wifi provider. -

Artificial Intelligence, Big Data and Cloud Computing 144
Digital Business and Electronic Digital Business Models StrategyCommerceProcess Instruments Strategy, Business Models and Technology Lecture Material Lecture Material Prof. Dr. Bernd W. Wirtz Chair for Information & Communication Management German University of Administrative Sciences Speyer Freiherr-vom-Stein-Straße 2 DE - 67346 Speyer- Email: [email protected] Prof. Dr. Bernd W. Wirtz Chair for Information & Communication Management German University of Administrative Sciences Speyer Freiherr-vom-Stein-Straße 2 DE - 67346 Speyer- Email: [email protected] © Bernd W. Wirtz | Digital Business and Electronic Commerce | May 2021 – Page 1 Table of Contents I Page Part I - Introduction 4 Chapter 1: Foundations of Digital Business 5 Chapter 2: Mobile Business 29 Chapter 3: Social Media Business 46 Chapter 4: Digital Government 68 Part II – Technology, Digital Markets and Digital Business Models 96 Chapter 5: Digital Business Technology and Regulation 97 Chapter 6: Internet of Things 127 Chapter 7: Artificial Intelligence, Big Data and Cloud Computing 144 Chapter 8: Digital Platforms, Sharing Economy and Crowd Strategies 170 Chapter 9: Digital Ecosystem, Disintermediation and Disruption 184 Chapter 10: Digital B2C Business Models 197 © Bernd W. Wirtz | Digital Business and Electronic Commerce | May 2021 – Page 2 Table of Contents II Page Chapter 11: Digital B2B Business Models 224 Part III – Digital Strategy, Digital Organization and E-commerce 239 Chapter 12: Digital Business Strategy 241 Chapter 13: Digital Transformation and Digital Organization 277 Chapter 14: Digital Marketing and Electronic Commerce 296 Chapter 15: Digital Procurement 342 Chapter 16: Digital Business Implementation 368 Part IV – Digital Case Studies 376 Chapter 17: Google/Alphabet Case Study 377 Chapter 18: Selected Digital Case Studies 392 Chapter 19: The Digital Future: A Brief Outlook 405 © Bernd W. -

Activate My Contract Vodafone Sim Card
Activate My Contract Vodafone Sim Card SublimateUndiverted and David revealable jaunts her Wald antipathists outjut while so unconventionallycomate Augusto briefthat Rolfher draysrambled resoundingly very dishonestly. and congregates Is Michel unqualifiable trimonthly. when Marlon garotting bolt? Apple can therefore customers only viable option please, report it provides your first staff member of sim activate a tonne of the instructions to know about vodafone Such files to activate my card activated properly mounted in the. My sim cards issued with my decision process? For my contract, that are activated on any other relevant competition or activate your old sim card recovery software it took it before you go option. For Vodafone service in India, SIM cards can not be activated on the Vodafone website and can only be activated by phone or store. But vodafone activation, contract is activated and cards for activation request you are stripe, the pay a viable option. Number card my sim cards but then. Always be on parody of how many Megas and minutes you have spent. More free addon planes than any other site! How vodafone sims do? Will let per know wish this works out, so keep your present phone. Activation is not required. Share with us below! Go lick a Vodafone store or talk series a representative. How chek reamimg free internt telenor? Sim card my sim cards and find in the program in selected areas, ben was dialing with customer service line telephone numbers? She was to activate my contract sim card or apple id password you restart the data? It for the module and costs for europe and local rates! It is activated per wlan mit den betrag abgebucht haben. -

Italian L KUMA KIT WIFI CARAVAN
Wireless WiFi Hotspot Kit Easy Set Up Guide Leitfaden zur einfachen Installation Guide d'Installation facile Guida Facile per le impostazioni Guía de Fácil Configuración Kolay Kurulum Kılavuzu 01594 888188 www.kuma.co.uk Wireless WiFi Hotspot Kit This section covers connection to a WiFi signal using the wireless adapter. If you wish to use a 3G Dongle Easy Set connection skip to page 3. Slide the cover off of the lower part of the wireless adaptor by Up Guide pressing the clip with your thumb then sliding downwards and join to the router using the USB lead supplied. Replace the plastic cover. Screw the small black antenna on to the rear of the router and Please check all the components are included. power up using AC or DC leads supplied. The PWR light should remain solid and the WLAN light should flicker once Kit Contains: booting is complete. Please note that the USB light on the 1x Kuma wireless router router will not come on at this point. It will not come on until 1x Kuma wireless adapter the setup is complete and a connection to the internet has 1x 5 metre USB lead been made. 1x Driver CD (not required for kit use) Connect the WiFi on your device (Smartphone/tablet/ 1x Jubilee clip computer) to the ‘11N 3G Router AP’ signal. At this point no 1x Mains power adapter password is required to connect. 1x 12v car adapter Open a browser (Internet Explorer/Chrome etc.) on 1x Unlocked dongle (3G version only) your device and in the address bar Type 192.168.2.1 and 1x CRC9 Magnetic base antenna (3G version only) press ‘Enter’. -

CMR15 Telecoms Section Charts.Potx
CMR16 telecoms section charts Industry metrics and summary 1 Figure 4.1 UK telecoms industry: key statistics UK Telecoms Industry 2010 2011 2012 2013 2014 2015 Total operator-reported revenue (£bn) 40.6 39.5 39.4 38.2 37.3 37.5 Operator-reported retail revenue (£bn) 27.8 27.9 28.3 28.1 28.2 28.7 (excl. CDS) Operator-reported wholesale revenue 10.1 8.9 8.3 7.5 6.5 6.2 (£bn) Average monthly household telecoms 86.06 84.13 83.16 80.43 79.65 82.17 spend (£, 2015 prices) Fixed access and call revenue (£bn) 9.3 9.0 8.7 8.7 8.4 8.4 Fixed internet revenue (£bn) 3.3 3.5 3.7 4.0 4.6 5.1 Fixed lines (millions) 33.4 33.3 33.4 33.4 33.5 33.2 Fixed broadband connections (millions) 19.6 20.7 21.8 22.8 23.7 24.7 Superfast broadband connections 0.2 1.0 3.1 5.3 7.1 9.2 (≥30Mbit/s, millions) Fixed voice call minutes (billions) 123 111 102 93 82 74 Average actual residential fixed 6.2 7.6 12.0 17.8 22.8 28.9 broadband download speeds (Mbit/s) UK Superfast broadband premises - - - - 75 83 coverage (%) Mobile retail revenues (£bn) 15.1 15.4 15.9 15.5 15.2 15.2 Mobile voice call minutes (billions) 131 131 132 134 137 142.8 SMS & MMS messages sent (billions) 129 150 151 129 110 101.3 Mobile data volumes (PB) - - - 283 533 873 Active mobile subscribers (millions) 81.5 82.2 83.2 82.7 83.7 84.8 4G subscribers (millions) - - - 2.7 23.6 39.5 4G UK outdoor premises coverage, by - - - - - 90.5 at least one operator (%) M2M subscribers (millions) 3.2 4.1 5.0 5.7 6.3 6.7 Source: Ofcom / operators Notes: CDS refers to corporate data services; connection figures are at year-end; all revenue data excludes VAT and is in nominal terms except for average monthly household spend; fixed voice minutes show n here are likely to be understated as they do not fully capture the use of VoIP services. -

Thank You for Taking Part in the Survey. We Would Like to Ask You A
QINTRO1: Thank you for taking part in the survey. We would like to ask you a few questions about technologies located within new cars, services in cars, as well as premium audio in cars. Please rest assured that all answers will be treated in the strictest of confidence and will only be used for statistical purposes. All replies will remain completely anonymous. **SCREENER** ASK ALL – SINGLE CHOICE SINGLE SELECT Q1 How many vehicle(s) does your household own? 1. None - TERMINATE 2. 1 3. 2 4. 3 5. 4 or more The next three questions are about your NEXT vehicle. **SCREENER** ASK ONLY THOSE WHO OWN A VEHICLE CURRENTLY (Q1 [2-5]) SINGLE SELECT Q2 Does your household plan to buy a vehicle sometime within the next 3 years that will be for personal use only? Please do not answer “yes” if the vehicle to be purchased will primarily be used for business. 1. Yes 2. Maybe 3. No - TERMINATE **SCREENER** ASK ONLY THOSE WHO MIGHT/WILL BUY VEHICLE (Q2 [1-2]) SINGLE SELECT Q3 Which of the following best describes your role in the purchasing decision of the next household vehicle? 1. Primary Decision Maker 2. Joint Decision Maker (with spouse or partner) 3. Uninvolved in decision making process - TERMINATE **SCREENER** ASK ONLY THOSE WHO MAY BE INVOLVED IN PURCHASING DECISION (Q3 [1-2]) SINGLE SELECT 1 Q4 When thinking about your next vehicle purchase, will that vehicle be new or used? 1. New 2. Used - TERMINATE 3. I don't know- TERMINATE ASK ONLY NEW CAR INTENDERS (Q4 [1]) SINGLE SELECT Q5 What is your gender? 1. -

Helping to Keep Your Kids Safe on Their Mobile Phones
HELPING TO KEEP YOUR KIDS SAFE ON THEIR MOBILE PHONES WITH PROFESSOR TANYA BYRON Visit carphonewarehouse.com/mobilewebsafety Introduction – Andrew Harrison, CEO, Carphone Warehouse Introduction – Professor Tanya Byron With more than 2.8 million children now owning a smartphone, including almost a With the capabilities of mobile phones increasing, children are using incredibly million children under the age of 12, it’s clear that parents see the many benefi ts sophisticated smartphones as part of their daily mobile lives. What this means is children gain from having one. that they have the ability to do much more in terms of communicating, socialising, playing, creating and publishing content as well as many other activities previously Now, as more phones than ever come with internet access, the risks children are confi ned to a home PC or laptop. exposed to are ever more prevalent. Here at Carphone Warehouse, we want to make sure that the potential risks are minimised as much as possible. However, while for our developing digital citizens this is brilliant in terms of digital opportunities, it also means that as parents we need to focus more carefully That is why last year, Carphone Warehouse pledged to support parents and help on preparing our children to use these sophisticated smartphones safely and them understand the risks that can be associated with buying a child their fi rst responsibly, because with greater digital opportunities come greater digital risks. mobile phone. We conducted research amongst parents to inform an advice booklet, written in partnership with Professor Tanya Byron. This booklet is an update from the original version published by Carphone Warehouse in 2010. -

16X9 Powerpoint Template & Usage
Vodafone Group Results: for the quarter ended 30 June 2018 25 July 2018 Disclaimer By reading these slides you agree to be bound by the following conditions. disclosed by other companies, including those in the Vodafone Group’s industry. Although these measures are important in the assessment and Information in the following presentation relating to the price at which management of the business, they should not be viewed in isolation or as relevant investments have been bought or sold in the past or the yield on replacements for, but rather as complementary to, the comparable GAAP such investments cannot be relied upon as a guide to the future performance measures of such investments. This presentation does not constitute an offering of securities or otherwise constitute an invitation or inducement to any person Vodafone, the Vodafone Speech Mark, the Vodafone Portrait, Vodacom, RED, to underwrite, subscribe for or otherwise acquire or dispose of securities in Vodafone One Net, Vodafone One and M-Pesa are trademarks of the Vodafone any company within the Vodafone Group. Group. The Vodafone Rhombus is a registered design of the Vodafone Group. Other product and company names mentioned herein may be the trademarks The presentation contains forward-looking statements, including within the of their respective owners. meaning of the US Private Securities Litigation Reform Act of 1995, which are subject to risks and uncertainties because they relate to future events. These No assurances can be given that the forward-looking statements in or made in forward-looking statements include, without limitation, statements in relation connection with this presentation will be realised. -

Further Proposals to Reform Switching of Mobile Services
Consumer Switching: Further proposals to reform switching of mobile services Proposals to address the impact of minimum notice periods when switching mobile communications services Non-confidential version. Redactions are marked as [] Consultation Publication date: 29 July 2016 Closing Date for Responses: 16 September 2016 About this document It is important for consumers to be able to switch providers quickly and easily, in order for them to exercise their choice and take advantage of competition in the communications sector. This document sets out our view on the difficulties and costs that consumers face when they switch mobile services where they need to give notice to terminate their existing service. The effect of notice periods within the switching process is that many consumers end up paying for two services at the same time, even though they may not want this. Our intention in this document is to enhance the mobile switching process reforms we proposed in our March 2016 consultation with an additional proposal to address this issue. We invite comments on our proposals from all interested parties. Contents Section Page 1 Summary 1 2 Introduction and legal framework 2 3 Consumer experience of mobile notice periods and switching 6 4 Additional proposed requirement for switching reform 19 Annex Page 1 Responding to this consultation 34 2 Ofcom’s consultation principles 36 3 Consultation response cover sheet 37 4 Consultation questions 39 5 Glossary and abbreviations 40 6 Calculation of quantifiable benefits and costs 43 7 Illustrative mobile switching journeys 50 8 Mobile providers’ terms and conditions concerning notice periods 56 Section 1 1 Summary Introduction 1.1 The ability to switch provider quickly and easily and without unnecessary difficulties enables consumers to exercise choice and take advantage of new offers or leave providers that are no longer meeting their needs. -

2017 Temkin Experience Ratings, UK CO-OP, M&S FOODS, and LIDL RECEIVE TOP CUSTOMER EXPERIENCE SCORES ACROSS 157 UK COMPANIES
INSIGHT REPORT 2017 Temkin Experience Ratings, UK CO-OP, M&S FOODS, AND LIDL RECEIVE TOP CUSTOMER EXPERIENCE SCORES ACROSS 157 UK COMPANIES By Bruce Temkin, CCXP Head of the Qualtrics XM Institute March 2017 This report was originally published by Temkin Group and was updated to incorporate the Qualtrics XM Institute™ format. There were no substantive changes made to the content. XM Institute INSIGHT REPORT qualtrics.com/XM-Institute EXECUTIVE SUMMARY The UK Temkin Experience Ratings is a cross-industry, open-standard benchmark of customer experience. To generate these scores, we asked 5,000 UK consumers to rate their recent interactions with 157 companies across 16 industries and then evaluated their experiences across three dimensions: success, effort, and emotion. Here are some highlights from the research: < Co-op, M&S Food, and Lidl earned highest overall ratings, while Audi, BMW, and Flybe earned the lowest. < When we compared company ratings with their industry averages, we found that Saga, Premier Inn, Vauxhall, and Volkswagen most outperformed their peers, while Audi and Bank of Scotland fell well below their competitors. < To improve customer experience, companies need to master four competencies: Purposeful Leadership, Compelling Brand Values, Employee Engagement, and Customer Connectedness. CO-OP, M&S FOOD, AND LIDL EARN TOP CUSTOMER EXPERIENCE RATINGS To evaluate the quality of the experiences that UK companies deliver to their customers, we surveyed 5,000 UK consumers about their recent interactions with organizations.1 We then used this consumer feedback to create the Temkin Experience Ratings by:2 § Examining three elements of the experience. We asked consumers to evaluate their experiences with different companies over the past 60 days. -

Website Review Simki.Shop
Website review simki.shop Generated on November 16 2020 19:29 PM The score is 52/100 SEO Content Title Simki.Shop- это сотовая связь и мобильный интернет Length : 50 Perfect, your title contains between 10 and 70 characters. Description Купить безлимитный интернет и мобильную сотовую связь от лучших сотовых операторов Европы вы можете у нас. Length : 106 Great, your meta description contains between 70 and 160 characters. Keywords Very bad. We haven't found meta keywords on your page. Use this free online meta tags generator to create keywords. Og Meta Properties Good, your page take advantage of Og Properties. Property Content title Simki.Shop- это сотовая связь и мобильный интернет type website site_name SimkiShop - Интернет и связь в Европе image https://simki.shop/image/catalog/logo-site2.jpg url https://simki.shop/ description Купить безлимитный интернет и мобильную сотовую связь от лучших сотовых операторов Европы вы можете у нас. Headings H1 H2 H3 H4 H5 H6 1 3 1 6 4 0 [H1] SimkiShop - Интернет и связь в Европе [H2] Наши представители SEO Content [H2] Контактные данные [H2] Очень важно [H3] Рекомендуемые сим карты и сотовые операторы для поездок по Европе и миру [H4] Американский номер для приема СМС [H4] Английский номер для приема СМС [H4] Китайская сим карта для СМС в России. [H4] Сим карта Германии. Работает в РФ [H4] Сим карта Англии Three оптом [H4] Сим карта Lebara Англии [H5] Информация [H5] Служба поддержки [H5] Дополнительно [H5] Личный Кабинет Images We found 14 images on this web page. 3 alt attributes are empty or missing. Add alternative text so that search engines can better understand the content of your images.