Library Maintenance Web UI
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Open Source Software Notice
Open Source Software Notice This document describes open source software contained in LG Smart TV SDK. Introduction This chapter describes open source software contained in LG Smart TV SDK. Terms and Conditions of the Applicable Open Source Licenses Please be informed that the open source software is subject to the terms and conditions of the applicable open source licenses, which are described in this chapter. | 1 Contents Introduction............................................................................................................................................................................................. 4 Open Source Software Contained in LG Smart TV SDK ........................................................... 4 Revision History ........................................................................................................................ 5 Terms and Conditions of the Applicable Open Source Licenses..................................................................................... 6 GNU Lesser General Public License ......................................................................................... 6 GNU Lesser General Public License ....................................................................................... 11 Mozilla Public License 1.1 (MPL 1.1) ....................................................................................... 13 Common Public License Version v 1.0 .................................................................................... 18 Eclipse Public License Version -

Juridische Aandachtspunten Bij Het Gebruik Van Open Source Software
Juridische aandachtspunten bij het gebruik van Open Source Software [email protected] 1 Inhoud Achtergrond en open source definitie Voorbeelden open source software en licenties Welke licentie is van toepassing? Enkele bepalingen uitgelicht Praktijktips 2 Technische achtergrond 3 Conceptuele achtergrond 4 Open source definitie 1. De licentie mag niemand verbieden de software gratis weg te geven óf te verkopen. 2. De broncode moet met de software meegeleverd worden of vrij beschikbaar zijn. 3. Wederverspreiding van afgeleide werken en aangepaste versies van de software moet toegestaan zijn. 4. Licenties mogen vereisen dat aanpassingen alleen als patch verspreid worden. 5. De licentie mag niet discrimineren tegen gebruikers(groepen). 6. De licentie mag niet discrimineren tegen gebruiksomgeving van de software. 7. De rechten verbonden aan het programma moeten opgaan voor iedereen aan wie het programma gedistribueerd wordt. 8. De rechten verbonden aan het programma moeten niet afhangen van softwaredistributies waarvan de software een onderdeel is. 9. De licentie mag niet verlangen dat andere software die samen met de software verspreid wordt onder dezelfde licentie valt. 10. Geen van de bepalingen van de licentie mag slaan op een bepaalde technologie of interface-stijl. 5 Voorbeelden Apache License, 2.0 BSD licenses GNU General Public License (GPL) GNU Library or "Lesser" General Public License (LGPL) MIT license Mozilla Public License 1.1 (MPL) Common Development and Distribution License Common Public License 1.0 Eclipse Public License -
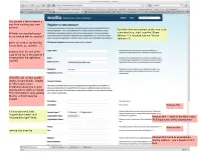
Eg, Right Now the "Street Address 2 Is Required, but Not "
You are just a few moments a way from creating your new browser. For fields that are required, make sure to be All fields are required except consistent (e.g., right now the "Street those marked with an asterisk * Address 2 is required, but not "Street Address 1") [note: no need to say that this is your basic account info....”] [remove all of the rest of the copy at the top of the page as it is repeated in the right-hand column] UPDATE: will call this “profile” Under account details, simplify to: “We require some information about you or your organization in order to register. This information is only used by Mozilla and will never be shared. Remove this If select personal, hide "organization name" and "organization type" fields Remove this -- add it to the field name: “Full legal name of the organization” Remove this remove star from fax Change field name to organization mailing address - use a header in that form Simplify this copy to something like: “The information in this section will show up in the browser directory [note is there a way not to have this publicly available?]. Simplify this copy to something like: Headline: Thank you for registering! Youʼre almost ready to create a customized browser! Youʼll receive an email shortly confirming that your account is approved. Please follow the instructions in order to finalize your registration. If for some reason you donʼt receive an email after 24 hours, please contact us at [email protected] (check your SPAM filter first!). Alternatively, click the button below to re-send your activation information now. -

IFIP AICT 404, Pp
Identifying Success Factors for the Mozilla Project Robert Viseur1,2 1 University of Mons (FPMs), Rue de Houdain, 9, B-7000 Mons, Belgium [email protected] 2 CETIC, Rue des Frères Wright, 29/3, B-6041 Charleroi, Belgium [email protected] Abstract. The publication of the Netscape source code under free software li- cense and the launch of the Mozilla project constitute a pioneering initiative in the field of free and open source software. However, five years after the publi- cation came years of decline. The market shares rose again after 2004 with the lighter Firefox browser. We propose a case study covering the period from 1998 to 2012. We identify the factors that explain the evolution of the Mozilla project. Our study deepens different success factors identified in the literature. It is based on authors' experience as well as the abundant literature dedicated to the Netscape company and the Mozilla project. It particularly highlights the im- portance of the source code complexity, its modularity, the responsibility as- signment and the existence of an organisational sponsorship. 1 Introduction After the launch of the GNU project in 1984 and the emergence of Linux in 1991, the Mozilla project was probably one of the most important events in the field of free and open source software at the end of the nineteenth century (Viseur, 2011). It was a pioneering initiative in the release of proprietary software, while commercial involvement in the development of free and open source software has accelerated over the last ten years (Fitzgerald, 2006). Netscape was the initiator. -

Diplomarbeit
Max Schlager Einsatzmöglichkeiten von freier und Open-Source-Software in Klein- und Mittelbetrieben als Alternative zu proprietärer Software Eine Betrachtung im Kontext von Sprachdienstleistungsunternehmen eingereicht als DIPLOMARBEIT an der HOCHSCHULE MITTWEIDA ___________________________________________ UNIVERSITY OF APPLIED SCIENCES Fachbereich Wirtschaftswissenschaften Klagenfurt, 2009 Erstprüfer: Prof. Dr.-Ing. Hartmut Linder Zweitprüfer: Prof. Dr.-Ing. habil. Christian-Andreas Schumann Vorgelegte Arbeit wurde verteidigt am: Bibliographische Beschreibung Bibliographische Beschreibung Schlager, Max: Einsatzmöglichkeiten von freier und Open‐Source‐Software in Klein‐ und Mittelbetrieben als Alternative zu proprietärer Software. Eine Betrachtung im Kontext von Sprachdienstleistungsunternehmen. – 2009. – 114 S. Klagenfurt, Hochschule Mittweida (FH), Fachbereich Wirtschaftswissen‐ schaften, Diplomarbeit, 2009 Referat: Ziel der Diplomarbeit ist es herauszufinden, ob freie und Open‐Source‐ Software eine sinnvolle Alternative für Klein‐ und Mittelbetriebe darstellen könnte. Als Untersuchungsobjekt wurde die Sparte der Sprachdienstleistungsunternehmungen gewählt, um einerseits eine thematische Abgrenzung des Umfanges an Softwareprogrammen zu gewährleisten und andererseits eine Empfehlung für eine spezielle Sparte der Softwareanwender abgeben zu können. Nach der thematischen Abgrenzung und einer theoretischen Einführung in die Aspekte der Softwarelizenzierung erfolgt ein Auszug über die auf dem Markt befindliche freie und Open‐Source‐Software. -

A Framework for Purposeful Open Source
Open Source Archetypes: A frameworkFramework For For Purposeful Open Source May 2018 Open Source Archetypes: A Framework For Purposeful Open Source Table of Contents Preface. 03 Introduction . 04 How to Use This Document. 05 Benefits of Open Source . 06 Open Source Project Archetypes. 10 Business-to-Business (B2B) Open Source . 11 Multi-Vendor Infrastructure . 12 Rocket Ship to Mars . 14 Controlled Ecosystem . 16 Wide Open. .. 17 Mass Market . 19 Specialty Library . 21 Trusted Vendor . 22 Upstream Dependency . 24 Bathwater . 25 Quick-Reference Comparison Of All Archetypes . 28 Practical Questions To Ask About A Project . 29 Basics of Open Source Licensing . 33 Methodology . 37 Acknowledgements . 38 Appendix – Work On ‘Openness’ At Mozilla . 38 BACK TO CONTENTS 02 Open Source Archetypes: A Framework For Purposeful Open Source Preface This report was originally commissioned by Mozilla for internal purposes. Mozilla wanted a shared framework for discussing its options in running open source projects, and requested a survey and comparative analysis of open source project archetypes — the various shapes that open source projects take in order to meet their various goals. For example, should a project prioritize development momentum over early collaborator acquisition, or vice versa? Should it optimize for individual contributors or for institutional partners? Different projects will have different answers to these and many other questions. The benefits of having a common vocabulary of archetypes extend beyond Mozilla, however, and the vocabulary is more useful and more easily improvable the more widely it is shared. Accordingly, Mozilla decided to release the report publicly. Very little has been changed from the original internal version: the Mozilla-specific orientation has been left intact, on the theory that the analysis will be clearer if tuned to a specific (and fortunately well-known) organization rather than rewritten for a hypothetical general audience. -

A Guide to Free and Open Source Software
Competence Center in Digital Law www.ccdigitallaw.ch [email protected] Podcast series A Guide to Free and Open Source Software Episode 2: Free and Open Source Software Licenses Summary of Episode 1 Hello and welcome to the second part of the CCdigitallaw podcast with the focus on free and open source software. In the first part on free and open source software you went through the simplified process of developing software. You wrote a code for an email program and learned that to make your code free and open source you have to make the human readable source code accessible to everyone. You have to license your copyrights so that everyone is able and allowed to use, copy, share, modify and share modifications of your computer program. The easiest way to do that is to choose one of the many free and open source software licenses available online. Introduction to Episode 2 In this second part, you will learn where to find all the free and open source software licenses. To do that I have to differentiate between the free software definition and the open source software definition. Definition of Free Software and Open Source Software The term free and open source software pulls together two definitions. One is the free software definition made by the Free Software Foundation, the other is the open source software definition made by the Open Source Initiative. The two definitions are very similar in their content but not a hundred percent the same. “Free software” is defined by the free software foundation it says1 that a computer program is free software if the users of the program have the following four freedoms: . -

Open Source Software
Open Source Software Clemens Zeidler May 19, 2017 1 / 42 Table of Content Open Source Software Open Source Software Licences Creative Commons Open source not only for software 2 / 42 What is open source software (OSS)1? Proprietary Software/ Closed Source Software I a person, team, or organization has exclusive control over the code/software I source code is not available to others Open Source Software I source code is publicly available I shareable I can be modified/enhanced I can be redistributed (depends on license) 1opensource.com/resources/what-open-source 3 / 42 OSS is everywhere... Kernels: Linux, BSD I servers, super computers, embedded devices, mobile, desktop Android I Linux kernel + open source user land (often with proprietary firmware) I most shipped mobile devices running Android 4 / 42 OSS is everywhere... Web Browsers I Firefox (Gecko engine) (originates from Netscape) I WebKit and Blink web engine (forked from the KHTML/KJS project) I Chrome Web server I Apache, NGINX... 5 / 42 OSS is everywhere... Software Development I most programming languages are open source I many libs are open source, e.g. standard libs, Qt, Apache Commons,... I dev tools: Git, Eclipse, Intellij IDEA,... I build tools: maven, gradle,... 6 / 42 OSS is everywhere... Applications I Gimp, LibreOffice, Inkscape, Thunderbird,... 7 / 42 Motivation: User’s Point of View Code quality/security I public code reviews/ code analysis I review security issues, check for backdoors, is the software spying on me? I doesn’t mean all OSS code is secure/ has high quality.. -
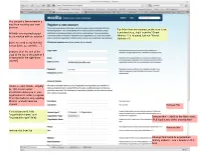
For Fields That Are Required, Make Sure to Be Consistent (E.G., Right Now The
You are just a few moments a way from creating your new browser. For fields that are required, make sure to be All fields are required except consistent (e.g., right now the "Street those marked with an asterisk * Address 2 is required, but not "Street Address 1") [note: no need to say that this is your basic account info....”] [remove all of the rest of the copy at the top of the page as it is repeated in the right-hand column] Under account details, simplify to: “We require some information about you or your organization in order to register. This information is only used by Mozilla and will never be shared. Remove this If select personal, hide "organization name" and "organization type" fields Remove this -- add it to the field name: “Full legal name of the organization” Remove this remove star from fax Change field name to organization mailing address - use a header in that form Simplify this copy to something like: “The information in this section will show up in the browser directory [note is there a way not to have this publicly available?]. Simplify this copy to something like: Headline: Thank you for registering! Youʼre almost ready to create a customized browser! Youʼll receive an email shortly confirming that your account is approved. Please follow the instructions in order to finalize your registration. If for some reason you donʼt receive an email after 24 hours, please contact us at [email protected] (check your SPAM filter first!). Alternatively, click the button below to re-send your activation information now. -

MOZILLA PUBLIC LICENSE Version 1.0 ---1
MOZILLA PUBLIC LICENSE Version 1.0 ---------------- 1. Definitions. 1.1. ‘‘Contributor’’ means each entity that creates or contributes to the creation of Modifications. 1.2. ‘‘Contributor Version’’ means the combination of the Original Code, prior Modifications used by a Contributor, and the Modifications made by that particular Contributor. 1.3. ‘‘Covered Code’’ means the Original Code or Modifications or the combination of the Original Code and Modifications, in each case including portions thereof. 1.4. ‘‘Electronic Distribution Mechanism’’ means a mechanism generally accepted in the software development community for the electronic transfer of data. 1.5. ‘‘Executable’’ means Covered Code in any form other than Source Code. 1.6. ‘‘Initial Developer’’ means the individual or entity identified as the Initial Developer in the Source Code notice required by Exhibit A. 1.7. ‘‘Larger Work’’ means a work which combines Covered Code or portions thereof with code not governed by the terms of this License. 1.8. ‘‘License’’ means this document. 1.9. ‘‘Modifications’’ means any addition to or deletion from the substance or structure of either the Original Code or any previous Modifications. When Covered Code is released as a series of files, a Modification is: A. Any addition to or deletion from the contents of a file containing Original Code or previous Modifications. B. Any new file that contains any part of the Original Code or previous Modifications. 1.10. ‘‘Original Code’’ means Source Code of computer software code which is described in the Source Code notice required by Exhibit A as Original Code, and which, at the time of its release under this License is not already Covered Code governed by this License. -

9.Ibitàcola.Pdf
ProgramariBit Solucions de programari lliure per a les pimes Cap del projecte Marcos Blázquez Autor Marcos Blázquez Col·laboradors Francina Mas, Jordi Morell i David Palou Alguns drets reservats Aquesta obra està sota una llicència Reconeixement-No comercial-Compartir sota la mateixa llicència 3.0 Espanya de Creative Commons. Per veure una còpia d’aquesta llicència, visiteu http://creativecommons.org/licenses/by-nc-sa/3.0/es/ o envieu una carta a Creative Commons, 171 Second Street, Suite 300, San Francisco, Califòrnia 94105, USA. Edita: Fundació IBIT Parc Bit. Ctra. Valldemossa, Km. 7,4 Edifici 17 - 3r pis Porta D-2 07121 Palma, Illes Balears, Espanya Tel: +34 971177270/1 www.ibit.org Disseny i il·lustracions: www.accentgrafic.com Impressió: Gràfiques Rubines Dip. Legal: 1888 - 2010 ISBN: 978-84-694-0370-9 Sumari Pròleg 7 Introducció 11 Un poc d’història 15 Què és el programari lliure? 19 Desavantatges del programari privatiu en l’àmbit de les pimes 25 Programari lliure i pimes: de l’ètica a la productivitat 29 Aspectes legals del programari lliure 35 Llicències de programari lliure 39 Lliure no vol dir gratis: aspectes econòmics del programari lliure 43 El secret del programari lliure: la comunitat 47 Necessitats de programari a les pimes 51 Ordinador 54 Sistema operatiu 54 Eines de gestió empresarial 54 Multimèdia 62 Eines de seguretat informàtica 63 Els inicis amb programari lliure 65 Eines lliures 69 Sistemes operatius 71 FreeBSD 71 GNU/Linux 72 Aplicacions de gestió 79 OpenERP 79 Openbravo ERP 81 SugarCRM 83 VTiger CRM 84 BulmaGés 86 OpenProj 87 DotProject 88 OpenKM 89 Alfresco 90 Oficina 92 OpenOffice / LibreOffice 92 Gimp 94 Inkscape 96 PDFCreator 98 Mozilla Sunbird/Lightning 98 Comunicació 101 Mozilla Firefox 101 Mozilla Thunderbird 102 Seguretat 103 ClamAv Antivirus 103 Gestors de contingut web 105 Joomla! 105 Wordpress 107 Drupal 109 Utilitats 111 XMind 111 7-Zip 112 Ekiga 113 Recopilatoris i/o repositoris web 114 Bibliografia 115 <Pròleg> ProgramariBit La característica principal del programari lliure rau en el fet que és lliure. -

Mozilla Public License Version 2.0
MOZILLA PUBLIC LICENSE VERSION 2.0 1. DEFINITIONS 1.1. “Contributor” means each individual or legal entity that creates, contributes to the creation of, or owns Covered Software. 1.2. “Contributor Version” means the combination of the Contributions of others (if any) used by a Contributor and that particular Contributor’s Contribution. 1.3. “Contribution” means Covered Software of a particular Contributor. 1.4. “Covered Software” means Source Code Form to which the initial Contributor has attached the notice in Exhibit A, the Executable Form of such Source Code Form, and Modifications of such Source Code Form, in each case including portions thereof. 1.5. “Incompatible With Secondary Licenses” means a. that the initial Contributor has attached the notice described in Exhibit B to the Covered Software; or b. that the Covered Software was made available under the terms of version 1.1 or earlier of the License, but not also under the terms of a Secondary License. 1.6. “Executable Form” means any form of the work other than Source Code Form. 1.7. “Larger Work” means a work that combines Covered Software with other material, in a separate file or files, that is not Covered Software. 1.8. “License” means this document. 1.9. “Licensable” means having the right to grant, to the maximum extent possible, whether at the time of the initial grant or subsequently, any and all of the rights conveyed by this License. 1.10. “Modifications” means any of the following: a. any file in Source Code Form that results from an addition to, deletion from, or modification of the contents of Covered Software; or b.