Open Source Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AMNESIA 33: How TCP/IP Stacks Breed Critical Vulnerabilities in Iot
AMNESIA:33 | RESEARCH REPORT How TCP/IP Stacks Breed Critical Vulnerabilities in IoT, OT and IT Devices Published by Forescout Research Labs Written by Daniel dos Santos, Stanislav Dashevskyi, Jos Wetzels and Amine Amri RESEARCH REPORT | AMNESIA:33 Contents 1. Executive summary 4 2. About Project Memoria 5 3. AMNESIA:33 – a security analysis of open source TCP/IP stacks 7 3.1. Why focus on open source TCP/IP stacks? 7 3.2. Which open source stacks, exactly? 7 3.3. 33 new findings 9 4. A comparison with similar studies 14 4.1. Which components are typically flawed? 16 4.2. What are the most common vulnerability types? 17 4.3. Common anti-patterns 22 4.4. What about exploitability? 29 4.5. What is the actual danger? 32 5. Estimating the reach of AMNESIA:33 34 5.1. Where you can see AMNESIA:33 – the modern supply chain 34 5.2. The challenge – identifying and patching affected devices 36 5.3. Facing the challenge – estimating numbers 37 5.3.1. How many vendors 39 5.3.2. What device types 39 5.3.3. How many device units 40 6. An attack scenario 41 6.1. Other possible attack scenarios 44 7. Effective IoT risk mitigation 45 8. Conclusion 46 FORESCOUT RESEARCH LABS RESEARCH REPORT | AMNESIA:33 A note on vulnerability disclosure We would like to thank the CERT Coordination Center, the ICS-CERT, the German Federal Office for Information Security (BSI) and the JPCERT Coordination Center for their help in coordinating the disclosure of the AMNESIA:33 vulnerabilities. -

Analysis of Firmware Security in Embedded ARM Environments
Analysis of Firmware Security in Embedded ARM Environments Dane A. Brown Dissertation submitted to the Faculty of the Virginia Polytechnic Institute and State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Engineering T. Charles Clancy, Chair Ryan Gerdes Yaling Yang Jonathan Black Patrick Schaumont August 13, 2019 Arlington, Virginia Keywords: Security, Firmware, Embedded Devices, ARM Copyright 2019, Dane A. Brown Analysis of Firmware Security in Embedded ARM Environments Dane A. Brown (ABSTRACT) Modern enterprise-grade systems with virtually unlimited resources have many options when it comes to implementing state of the art intrusion prevention and detection solutions. These solutions are costly in terms of energy, execution time, circuit board area, and capital. Sus- tainable Internet of Things devices and power-constrained embedded systems are thus forced to make suboptimal security trade-offs. One such trade-off is the design of architectures which prevent execution of injected shell code, yet have allowed Return Oriented Program- ming (ROP) to emerge as a more reliable way to execute malicious code following attacks. ROP is a method used to take over the execution of a program by causing the return address of a function to be modified through an exploit vector, then returning to small segments of otherwise innocuous code located in executable memory one after the other to carry out the attacker’s aims. We show that the Tiva TM4C123GH6PM microcontroller, which utilizes an ARM Cortex-M4F processor, can be fully controlled with this technique. Firmware code is pre-loaded into a ROM on Tiva microcontrollers which can be subverted to erase and rewrite the flash memory where the program resides. -
Open Source Software Notice
Open Source Software Notice This document describes open source software contained in LG Smart TV SDK. Introduction This chapter describes open source software contained in LG Smart TV SDK. Terms and Conditions of the Applicable Open Source Licenses Please be informed that the open source software is subject to the terms and conditions of the applicable open source licenses, which are described in this chapter. | 1 Contents Introduction............................................................................................................................................................................................. 4 Open Source Software Contained in LG Smart TV SDK ........................................................... 4 Revision History ........................................................................................................................ 5 Terms and Conditions of the Applicable Open Source Licenses..................................................................................... 6 GNU Lesser General Public License ......................................................................................... 6 GNU Lesser General Public License ....................................................................................... 11 Mozilla Public License 1.1 (MPL 1.1) ....................................................................................... 13 Common Public License Version v 1.0 .................................................................................... 18 Eclipse Public License Version -

Coreboot - the Free firmware
coreboot - the free firmware Linux Club of Peking University April 9th, 2016 . Linux Club of Peking University coreboot - the free firmware April 9th, 2016 1 / 30 1 History 2 Why use coreboot 3 How coreboot works 4 Building and using coreboot 5 Flashing 6 Utilities and Debugging 7 Contribute to coreboot 8 Proprietary Components 9 References . Linux Club of Peking University coreboot - the free firmware April 9th, 2016 2 / 30 History: from LinuxBIOS to coreboot coreboot has a very long history, stretching back more than 15 years to when it was known as LinuxBIOS. While the project has gone through lots of changes over the years, many of the earliest developers still contribute today. Linux Club of Peking University coreboot - the free firmware April 9th, 2016 3 / 30 LinuxBIOS v1: 1999-2000 The coreboot project originally started as LinuxBIOS in 1999 at Los Alamos National Labs (LANL) by Ron Minnich. Ron needed to boot a cluster made up of many x86 mainboards without the hassles that are part of the PC BIOS. The goal was to do minimal hardware initilization in order to boot Linux as fast as possible. Linux already had the drivers and support to initialize the majority of devices. Ron and a number of other key contributors from LANL, Linux NetworkX, and other open source firmware projects successfully booted Linux from flash. From there they were able to discover other nodes in the cluster, load a full kernel and user space, and start the clustering software. Linux Club of Peking University coreboot - the free firmware April 9th, 2016 4 / 30 LinuxBIOS v2: 2000-2005 After the initial success of v1, the design was expanded to support more CPU architectures (x86, Alpha, PPC) and to support developers with increasingly diverse needs. -

Linux Kernel. LTS? LTSI?
ARM Reference Kernel of Tizen 3 MyungJoo Ham, Ph.D. MyungJoo Ham Tizen “System Domain” & System SW Lab “Base Domain” Architect SW Platform Team SWC Samsung Electronics ARM Reference Kernel of Tizen 3 1. What is it? 2. Idea & Principle 3. Design & Updates 4. Discussion What is “Tizen Reference Kernel” • Kernel (& BSP) for Tizen Reference Devices BSP Validated & Tested for the Reference Devices Image from seoz.com 3 What is “Tizen Reference Kernel” • Kernel (& BSP) for Tizen Reference Devices BSP Validated & Tested for the Reference Devices Yet Another BSP? Image from seoz.com 4 Need for “Tizen Reference Kernel” • Distribute reference devices • Tizen-common kernel features & interface • Basis for next-gen Tizen development 1 KDBUS, User PM-QoS, PASS, DMABUF Sync FW, … 2 CMA, DRM-Exynos, Devfreq, Extcon, Charger-manager, LAB/Turboboost … • Support Tizen Vendors! • Well-known and well-written example. • Code basis for vendors. 5 Previous Tizen ARM Reference Kernel (~2.2.1) • Linux 3.0.15 • Obsolete LTS. (Current: 3.4 & 3.10) • Support RD-PQ (Tizen 2) & RD-210 (Tizen 1 & 2) • RD-PQ: Exynos4412 • RD-210: Exynos4210 (Linux 2.6.36 for Tizen 1) • Not Good as Reference • Too many backported features. • Too OLD! No LTS/LTSI support • Many kernel hacks & dirty patches • git history removed. 1. Forked from production kernel. 2. Hard to read 6 Status of Tizen 3 Reference Kernels • Two Reference Kernels: ARM / Intel • ARM (armv7, aarch64) • Linux 3.10.y • 3.10.33 @ 2014/05 • Full git history. • armv6 support (Raspberry Pi) coming soon. (Thanks to Univ. of Warsaw) • Test & validation phase (integration test with userspace) • Intel (x86, x86_64) • Linux 3.14.1 • Recent ATOM SoC support merged @ 3.14 • Test & validation phase (integration test with userspace) 7 ARM Reference Kernel of Tizen 3 1. -

Introductory Lecture & FLOSS
Introductory Lecture & FLOSS Lecture 1 TU Wien, 193.067 Free and Open Technologies (WS 2019/2020) Christoph Derndorfer and Lukas F. Lang This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Introduction Organization ● Lectures: ○ Weekly lecture to cover course materials (until Christmas) ○ Lectures take place on Tuesdays, 17:00–19:00, Argentinierstraße 8, Seminarraum/Bibliothek 194-05 ○ Attendance is mandatory ● Group project: ○ In groups of 4 students ○ 3 meetings with lecturers during the semester (week 44/2019, week 48/2019, week 2/2020) ○ Final presentations at the end of January (week 4/2020) ● Final paper: ○ In groups of 2 students ○ Final presentations at the end of January (week 5/2020) ○ Deadline: Sunday, February 9, 2020, 23:59 CET (no exceptions!) Organization ● Grading: ○ 50% group project ○ 35% seminar paper ○ 15% participation during lectures ○ All course components need to be passed in order to pass the overall course! ● Course materials: ○ Will be provided at https://free-and-open-technologies.github.io ● For further questions: ○ Email [email protected] and [email protected] Lecture outline 1. FLOSS (Free/Libre and Open Source Software) 2. Open Hardware 3. Open Data 4. Open Content/Open Educational Resources 5. Open Science/Research 6. Open Access 7. Open Spaces/Open Practices: Metalab Vienna 8. Guest Lecture: Stefanie Wuschitz (Mz* Baltazar’s Lab) Group project ● Goal: ○ Extend, contribute to, or create a new open project within scope of lecture topics ● Choose topic from a list (see course website) or (even better) suggest your own: ○ Groups of 4 students ○ Send a 1-page proposal until Friday, October 25, via email to both lecturers ■ Define the idea, goal, (potential) impact, requirements, and estimated effort ■ State deliverables (should be broken down into three milestones to discuss in meetings) ● Requirements: ○ Open and accessible (Git repository, openly licensed) → others can access/use/study/extend ○ Use time sheet to track and compare estimated vs. -

Free As in Freedom (2.0): Richard Stallman and the Free Software Revolution
Free as in Freedom (2.0): Richard Stallman and the Free Software Revolution Sam Williams Second edition revisions by Richard M. Stallman i This is Free as in Freedom 2.0: Richard Stallman and the Free Soft- ware Revolution, a revision of Free as in Freedom: Richard Stallman's Crusade for Free Software. Copyright c 2002, 2010 Sam Williams Copyright c 2010 Richard M. Stallman Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled \GNU Free Documentation License." Published by the Free Software Foundation 51 Franklin St., Fifth Floor Boston, MA 02110-1335 USA ISBN: 9780983159216 The cover photograph of Richard Stallman is by Peter Hinely. The PDP-10 photograph in Chapter 7 is by Rodney Brooks. The photo- graph of St. IGNUcius in Chapter 8 is by Stian Eikeland. Contents Foreword by Richard M. Stallmanv Preface by Sam Williams vii 1 For Want of a Printer1 2 2001: A Hacker's Odyssey 13 3 A Portrait of the Hacker as a Young Man 25 4 Impeach God 37 5 Puddle of Freedom 59 6 The Emacs Commune 77 7 A Stark Moral Choice 89 8 St. Ignucius 109 9 The GNU General Public License 123 10 GNU/Linux 145 iii iv CONTENTS 11 Open Source 159 12 A Brief Journey through Hacker Hell 175 13 Continuing the Fight 181 Epilogue from Sam Williams: Crushing Loneliness 193 Appendix A { Hack, Hackers, and Hacking 209 Appendix B { GNU Free Documentation License 217 Foreword by Richard M. -

BCIS 1305 Business Computer Applications
BCIS 1305 Business Computer Applications BCIS 1305 Business Computer Applications San Jacinto College This course was developed from generally available open educational resources (OER) in use at multiple institutions, drawing mostly from a primary work curated by the Extended Learning Institute (ELI) at Northern Virginia Community College (NOVA), but also including additional open works from various sources as noted in attributions on each page of materials. Cover Image: “Keyboard” by John Ward from https://flic.kr/p/tFuRZ licensed under a Creative Commons Attribution License. BCIS 1305 Business Computer Applications by Extended Learning Institute (ELI) at NOVA is licensed under a Creative Commons Attribution 4.0 International License, except where otherwise noted. CONTENTS Module 1: Introduction to Computers ..........................................................................................1 • Reading: File systems ....................................................................................................................................... 1 • Reading: Basic Computer Skills ........................................................................................................................ 1 • Reading: Computer Concepts ........................................................................................................................... 1 • Tutorials: Computer Basics................................................................................................................................ 1 Module 2: Computer -

Copyright Protection for Computer Programs in Read Only Memory Chips Peter D
Hofstra Law Review Volume 11 | Issue 1 Article 8 1982 Copyright Protection for Computer Programs in Read Only Memory Chips Peter D. Aufrichtig Follow this and additional works at: http://scholarlycommons.law.hofstra.edu/hlr Part of the Law Commons Recommended Citation Aufrichtig, Peter D. (1982) "Copyright Protection for Computer Programs in Read Only Memory Chips," Hofstra Law Review: Vol. 11: Iss. 1, Article 8. Available at: http://scholarlycommons.law.hofstra.edu/hlr/vol11/iss1/8 This document is brought to you for free and open access by Scholarly Commons at Hofstra Law. It has been accepted for inclusion in Hofstra Law Review by an authorized administrator of Scholarly Commons at Hofstra Law. For more information, please contact [email protected]. Aufrichtig: Copyright Protection for Computer Programs in Read Only Memory Ch COPYRIGHT PROTECTION FOR COMPUTER PROGRAMS IN READ ONLY MEMORY CHIPS INTRODUCTION You walk into a store looking for a computer chess game and see two apparently identical models. One, however, is considerably cheaper than the other." You inquire as to the difference and are told that there is none, but for the price. The reason for this price differential is the lack of copyright protection' for a computer pro- gram implanted in a Read Only Memory (ROM) chip.' As the computer has developed, the programs which make the computer useful have also changed. To bring the computer out of the temperature and humidity controlled rooms, and into the consumer's palm, various advances have been required. First, the computer itself became smaller, faster, and more affordable than was imaginable twenty-five years ago.4 Second, the memory spaces for the computers have developed to the stage where they can hold billions of bytes5 of information in chiclet-sized packages." Third, the programs which run the hardware7 can be stored so that they are nonvolatile,8 and * This note has been submitted in a slightly different form to the Nathan Burkan Memorial Copyright Competition. -

Juridische Aandachtspunten Bij Het Gebruik Van Open Source Software
Juridische aandachtspunten bij het gebruik van Open Source Software [email protected] 1 Inhoud Achtergrond en open source definitie Voorbeelden open source software en licenties Welke licentie is van toepassing? Enkele bepalingen uitgelicht Praktijktips 2 Technische achtergrond 3 Conceptuele achtergrond 4 Open source definitie 1. De licentie mag niemand verbieden de software gratis weg te geven óf te verkopen. 2. De broncode moet met de software meegeleverd worden of vrij beschikbaar zijn. 3. Wederverspreiding van afgeleide werken en aangepaste versies van de software moet toegestaan zijn. 4. Licenties mogen vereisen dat aanpassingen alleen als patch verspreid worden. 5. De licentie mag niet discrimineren tegen gebruikers(groepen). 6. De licentie mag niet discrimineren tegen gebruiksomgeving van de software. 7. De rechten verbonden aan het programma moeten opgaan voor iedereen aan wie het programma gedistribueerd wordt. 8. De rechten verbonden aan het programma moeten niet afhangen van softwaredistributies waarvan de software een onderdeel is. 9. De licentie mag niet verlangen dat andere software die samen met de software verspreid wordt onder dezelfde licentie valt. 10. Geen van de bepalingen van de licentie mag slaan op een bepaalde technologie of interface-stijl. 5 Voorbeelden Apache License, 2.0 BSD licenses GNU General Public License (GPL) GNU Library or "Lesser" General Public License (LGPL) MIT license Mozilla Public License 1.1 (MPL) Common Development and Distribution License Common Public License 1.0 Eclipse Public License -
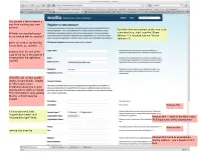
Eg, Right Now the "Street Address 2 Is Required, but Not "
You are just a few moments a way from creating your new browser. For fields that are required, make sure to be All fields are required except consistent (e.g., right now the "Street those marked with an asterisk * Address 2 is required, but not "Street Address 1") [note: no need to say that this is your basic account info....”] [remove all of the rest of the copy at the top of the page as it is repeated in the right-hand column] UPDATE: will call this “profile” Under account details, simplify to: “We require some information about you or your organization in order to register. This information is only used by Mozilla and will never be shared. Remove this If select personal, hide "organization name" and "organization type" fields Remove this -- add it to the field name: “Full legal name of the organization” Remove this remove star from fax Change field name to organization mailing address - use a header in that form Simplify this copy to something like: “The information in this section will show up in the browser directory [note is there a way not to have this publicly available?]. Simplify this copy to something like: Headline: Thank you for registering! Youʼre almost ready to create a customized browser! Youʼll receive an email shortly confirming that your account is approved. Please follow the instructions in order to finalize your registration. If for some reason you donʼt receive an email after 24 hours, please contact us at [email protected] (check your SPAM filter first!). Alternatively, click the button below to re-send your activation information now. -

IFIP AICT 404, Pp
Identifying Success Factors for the Mozilla Project Robert Viseur1,2 1 University of Mons (FPMs), Rue de Houdain, 9, B-7000 Mons, Belgium [email protected] 2 CETIC, Rue des Frères Wright, 29/3, B-6041 Charleroi, Belgium [email protected] Abstract. The publication of the Netscape source code under free software li- cense and the launch of the Mozilla project constitute a pioneering initiative in the field of free and open source software. However, five years after the publi- cation came years of decline. The market shares rose again after 2004 with the lighter Firefox browser. We propose a case study covering the period from 1998 to 2012. We identify the factors that explain the evolution of the Mozilla project. Our study deepens different success factors identified in the literature. It is based on authors' experience as well as the abundant literature dedicated to the Netscape company and the Mozilla project. It particularly highlights the im- portance of the source code complexity, its modularity, the responsibility as- signment and the existence of an organisational sponsorship. 1 Introduction After the launch of the GNU project in 1984 and the emergence of Linux in 1991, the Mozilla project was probably one of the most important events in the field of free and open source software at the end of the nineteenth century (Viseur, 2011). It was a pioneering initiative in the release of proprietary software, while commercial involvement in the development of free and open source software has accelerated over the last ten years (Fitzgerald, 2006). Netscape was the initiator.