Cve-2019-13225
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
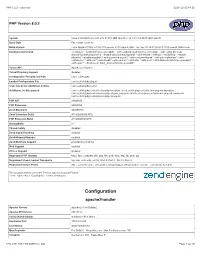
PHP 8.0.2 - Phpinfo() 2021-02-23 14:53
PHP 8.0.2 - phpinfo() 2021-02-23 14:53 PHP Version 8.0.2 System Linux effa5f35b7e3 5.4.83-v7l+ #1379 SMP Mon Dec 14 13:11:54 GMT 2020 armv7l Build Date Feb 9 2021 12:01:16 Build System Linux 96bc8a22765c 4.15.0-129-generic #132-Ubuntu SMP Thu Dec 10 14:07:05 UTC 2020 armv8l GNU/Linux Configure Command './configure' '--build=arm-linux-gnueabihf' '--with-config-file-path=/usr/local/etc/php' '--with-config-file-scan- dir=/usr/local/etc/php/conf.d' '--enable-option-checking=fatal' '--with-mhash' '--with-pic' '--enable-ftp' '--enable- mbstring' '--enable-mysqlnd' '--with-password-argon2' '--with-sodium=shared' '--with-pdo-sqlite=/usr' '--with- sqlite3=/usr' '--with-curl' '--with-libedit' '--with-openssl' '--with-zlib' '--with-pear' '--with-libdir=lib/arm-linux-gnueabihf' '- -with-apxs2' '--disable-cgi' 'build_alias=arm-linux-gnueabihf' Server API Apache 2.0 Handler Virtual Directory Support disabled Configuration File (php.ini) Path /usr/local/etc/php Loaded Configuration File /usr/local/etc/php/php.ini Scan this dir for additional .ini files /usr/local/etc/php/conf.d Additional .ini files parsed /usr/local/etc/php/conf.d/docker-php-ext-gd.ini, /usr/local/etc/php/conf.d/docker-php-ext-mysqli.ini, /usr/local/etc/php/conf.d/docker-php-ext-pdo_mysql.ini, /usr/local/etc/php/conf.d/docker-php-ext-sodium.ini, /usr/local/etc/php/conf.d/docker-php-ext-zip.ini PHP API 20200930 PHP Extension 20200930 Zend Extension 420200930 Zend Extension Build API420200930,NTS PHP Extension Build API20200930,NTS Debug Build no Thread Safety disabled Zend Signal Handling enabled -

MC-1200 Series Linux Software User's Manual
MC-1200 Series Linux Software User’s Manual Version 1.0, November 2020 www.moxa.com/product © 2020 Moxa Inc. All rights reserved. MC-1200 Series Linux Software User’s Manual The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. Copyright Notice © 2020 Moxa Inc. All rights reserved. Trademarks The MOXA logo is a registered trademark of Moxa Inc. All other trademarks or registered marks in this manual belong to their respective manufacturers. Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Moxa. Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any time. Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for its use, or for any infringements on the rights of third parties that may result from its use. This product might include unintentional technical or typographical errors. Changes are periodically made to the information herein to correct such errors, and these changes are incorporated into new editions of the publication. Technical Support Contact Information www.moxa.com/support Moxa Americas Moxa China (Shanghai office) Toll-free: 1-888-669-2872 Toll-free: 800-820-5036 Tel: +1-714-528-6777 Tel: +86-21-5258-9955 Fax: +1-714-528-6778 Fax: +86-21-5258-5505 Moxa Europe Moxa Asia-Pacific Tel: +49-89-3 70 03 99-0 Tel: +886-2-8919-1230 Fax: +49-89-3 70 03 99-99 Fax: +886-2-8919-1231 Moxa India Tel: +91-80-4172-9088 Fax: +91-80-4132-1045 Table of Contents 1. -

Implementation of the Programming Language Dino – a Case Study in Dynamic Language Performance
Implementation of the Programming Language Dino – A Case Study in Dynamic Language Performance Vladimir N. Makarov Red Hat [email protected] Abstract design of the language, its type system and particular features such The article gives a brief overview of the current state of program- as multithreading, heterogeneous extensible arrays, array slices, ming language Dino in order to see where its stands between other associative tables, first-class functions, pattern-matching, as well dynamic programming languages. Then it describes the current im- as Dino’s unique approach to class inheritance via the ‘use’ class plementation, used tools and major implementation decisions in- composition operator. cluding how to implement a stable, portable and simple JIT com- The second part of the article describes Dino’s implementation. piler. We outline the overall structure of the Dino interpreter and just- We study the effect of major implementation decisions on the in-time compiler (JIT) and the design of the byte code and major performance of Dino on x86-64, AARCH64, and Powerpc64. In optimizations. We also describe implementation details such as brief, the performance of some model benchmark on x86-64 was the garbage collection system, the algorithms underlying Dino’s improved by 3.1 times after moving from a stack based virtual data structures, Dino’s built-in profiling system, and the various machine to a register-transfer architecture, a further 1.5 times by tools and libraries used in the implementation. Our goal is to give adding byte code combining, a further 2.3 times through the use an overview of the major implementation decisions involved in of JIT, and a further 4.4 times by performing type inference with a dynamic language, including how to implement a stable and byte code specialization, with a resulting overall performance im- portable JIT. -

Red Hat Virtualization 4.4 Package Manifest
Red Hat Virtualization 4.4 Package Manifest Package listing for Red Hat Virtualization 4.4 Last Updated: 2021-09-09 Red Hat Virtualization 4.4 Package Manifest Package listing for Red Hat Virtualization 4.4 Red Hat Virtualization Documentation Team Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -
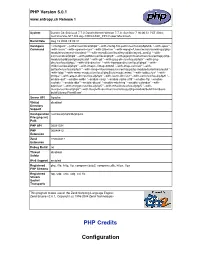
PHP Credits Configuration
PHP Version 5.0.1 www.entropy.ch Release 1 System Darwin G4-500.local 7.7.0 Darwin Kernel Version 7.7.0: Sun Nov 7 16:06:51 PST 2004; root:xnu/xnu-517.9.5.obj~1/RELEASE_PPC Power Macintosh Build Date Aug 13 2004 15:03:31 Configure './configure' '--prefix=/usr/local/php5' '--with-config-file-path=/usr/local/php5/lib' '--with-apxs' '- Command -with-iconv' '--with-openssl=/usr' '--with-zlib=/usr' '--with-mysql=/Users/marc/cvs/entropy/php- module/src/mysql-standard-*' '--with-mysqli=/usr/local/mysql/bin/mysql_config' '--with- xsl=/usr/local/php5' '--with-pdflib=/usr/local/php5' '--with-pgsql=/Users/marc/cvs/entropy/php- module/build/postgresql-build' '--with-gd' '--with-jpeg-dir=/usr/local/php5' '--with-png- dir=/usr/local/php5' '--with-zlib-dir=/usr' '--with-freetype-dir=/usr/local/php5' '--with- t1lib=/usr/local/php5' '--with-imap=../imap-2002d' '--with-imap-ssl=/usr' '--with- gettext=/usr/local/php5' '--with-ming=/Users/marc/cvs/entropy/php-module/build/ming-build' '- -with-ldap' '--with-mime-magic=/usr/local/php5/etc/magic.mime' '--with-iodbc=/usr' '--with- xmlrpc' '--with-expat -dir=/usr/local/php5' '--with-iconv-dir=/usr' '--with-curl=/usr/local/php5' '-- enable-exif' '--enable-wddx' '--enable-soap' '--enable-sqlite-utf8' '--enable-ftp' '--enable- sockets' '--enable-dbx' '--enable-dbase' '--enable-mbstring' '--enable-calendar' '--with- bz2=/usr' '--with-mcrypt=/usr/local/php5' '--with-mhash=/usr/local/php5' '--with- mssql=/usr/local/php5' '--with-fbsql=/Users/marc/cvs/entropy/php-module/build/frontbase- build/Library/FrontBase' Server -

Introducing Regular Expressions
Introducing Regular Expressions wnload from Wow! eBook <www.wowebook.com> o D Michael Fitzgerald Beijing • Cambridge • Farnham • Köln • Sebastopol • Tokyo Introducing Regular Expressions by Michael Fitzgerald Copyright © 2012 Michael Fitzgerald. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Simon St. Laurent Indexer: Lucie Haskins Production Editor: Holly Bauer Cover Designer: Karen Montgomery Proofreader: Julie Van Keuren Interior Designer: David Futato Illustrator: Rebecca Demarest July 2012: First Edition. Revision History for the First Edition: 2012-07-10 First release See http://oreilly.com/catalog/errata.csp?isbn=9781449392680 for release details. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Introducing Regular Expressions, the image of a fruit bat, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc., was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and authors assume no responsibility for errors or omissions, or for damages resulting from the use of the information con- tained herein. -

Ruby Programming
Ruby Programming Wikibooks.org December 1, 2012 On the 28th of April 2012 the contents of the English as well as German Wikibooks and Wikipedia projects were licensed under Creative Commons Attribution-ShareAlike 3.0 Unported license. An URI to this license is given in the list of figures on page 249. If this document is a derived work from the contents of one of these projects and the content was still licensed by the project under this license at the time of derivation this document has to be licensed under the same, a similar or a compatible license, as stated in section 4b of the license. The list of contributors is included in chapter Contributors on page 243. The licenses GPL, LGPL and GFDL are included in chapter Licenses on page 253, since this book and/or parts of it may or may not be licensed under one or more of these licenses, and thus require inclusion of these licenses. The licenses of the figures are given in the list of figures on page 249. This PDF was generated by the LATEX typesetting software. The LATEX source code is included as an attachment (source.7z.txt) in this PDF file. To extract the source from the PDF file, we recommend the use of http://www.pdflabs.com/tools/pdftk-the-pdf-toolkit/ utility or clicking the paper clip attachment symbol on the lower left of your PDF Viewer, selecting Save Attachment. After extracting it from the PDF file you have to rename it to source.7z. To uncompress the resulting archive we recommend the use of http://www.7-zip.org/. -

Sublime Text Help Release X
Sublime Text Help Release X guillermooo Mar 25, 2017 Contents 1 About This Documentation 1 1.1 Conventions in This Guide........................................1 2 Basic Concepts 3 2.1 The Data Directory...........................................3 2.2 The Packages Directory........................................3 2.3 The Python Console...........................................4 2.4 Textmate Compatibility.........................................4 2.5 Be Sublime, My Friend.........................................4 3 Core Features 5 3.1 Commands................................................5 3.2 Build Systems..............................................6 3.3 Command Line Usage..........................................7 3.4 Projects..................................................8 4 Customizing Sublime Text 9 4.1 Settings..................................................9 4.2 Indentation................................................ 11 4.3 Key Bindings............................................... 11 4.4 Menus.................................................. 12 5 Extending Sublime Text 13 5.1 Macros.................................................. 13 5.2 Snippets................................................. 14 5.3 Completions............................................... 17 5.4 Command Palette............................................. 20 5.5 Syntax Definitions............................................ 21 5.6 Plugins.................................................. 28 5.7 Packages................................................ -

Protogate Freeway® Software Version Description (SVD)
Protogate Freeway® Software Version Description (SVD) DC 900-2023C Protogate, Inc. 12225 World Trade Drive Suite R San Diego, CA 92128 USA Web: www.protogate.com Email: [email protected] Voice: (858) 451-0865 Fax: (877) 473-0190 Protogate Freeway® Software Version Description (SVD): DC 900-2023C by Protogate,Inc. Published October 2019 Copyright © 2013, 2015, 2019 Protogate, Inc. This Software Version Description (SVD) identifies the version information of a specific release of the Protogate Freeway® software. The latest version of this document is always available, in a variety of formats and compression options, from the Protogate World Wide Web server (http://www.protogate.com/support/manuals). This document can change without notice. Protogate, Inc. accepts no liability for any errors this document might contain. Freeway is a registered trademark of Protogate, Inc. All other trademarks and trade names are the properties of their respective holders. Table of Contents Preface............................................................................................................................................................................v Purpose of Document............................................................................................................................................v Intended Audience.................................................................................................................................................v Organization of Document ....................................................................................................................................v -

Sublime Text Unofficial Documentation
Sublime Text Unofficial Documentation Release 3.0 guillermooo Sep 16, 2017 Contents 1 Backers 2014 1 2 Content 3 2.1 About This Documentation.......................................3 2.2 Installation................................................5 2.3 Basic Concepts..............................................8 2.4 Editing.................................................. 11 2.5 Search and Replace............................................ 12 2.6 Build Systems (Batch Processing).................................... 17 2.7 File Management and Navigation.................................... 18 2.8 Customizing Sublime Text........................................ 22 2.9 Extending Sublime Text......................................... 32 2.10 Command Line Usage.......................................... 58 2.11 Reference................................................. 59 2.12 Glossary................................................. 128 Python Module Index 131 i ii CHAPTER 1 Backers 2014 Backers 2014 1 Sublime Text Unofficial Documentation, Release 3.0 2 Chapter 1. Backers 2014 CHAPTER 2 Content About This Documentation Welcome to the unofficial documentation for the Sublime Text editor! 3 Sublime Text Unofficial Documentation, Release 3.0 Sublime Text is a versatile and fun text editor for code and prose that automates repetitive tasks so you can focus the important stuff. It works on OS X, Windows and Linux. If you’re starting out with Sublime Text, read the Basic Concepts section first. Happy learning! Contributing to the Documentation If you want to contribute to this documentation, head over to the GitHub repo. This guide has been created with Sphinx. 4 Chapter 2. Content Sublime Text Unofficial Documentation, Release 3.0 Installation Make sure to read the conditions for use on the official site. Sublime Text is not free. The process of installing Sublime Text is different for each platform. 32 bits or 64 bits? OS X You can ignore this section: there is only one version of Sublime Text for OS X. -

Sublime Text Unofficial Documentation
Sublime Text Unofficial Documentation Release 3.0 guillermooo July 16, 2016 Contents 1 Backers 2014 1 2 3 2.1 Installation................................................3 2.2 Editing..................................................6 2.3 Search and Replace............................................7 2.4 Build Systems (Batch Processing).................................... 11 2.5 File Navigation and File Management.................................. 13 2.6 Customizing Sublime Text........................................ 17 2.7 Extending Sublime Text......................................... 27 2.8 Command Line Usage.......................................... 52 2.9...................................................... 53 2.10...................................................... 79 Python Module Index 81 i ii CHAPTER 1 Backers 2014 Backers 2014 1 Sublime Text Unofficial Documentation, Release 3.0 2 Chapter 1. Backers 2014 CHAPTER 2 2.1 Installation Make sure to read the conditions for use on the official site. Sublime Text is not free. The process of installing Sublime Text is different for each platform. 2.1.1 32 bits or 64 bits? OS X You can ignore this section: there is only one version of Sublime Text for OS X. Windows You should be able to run the 64-bit version if you are using a modern version Windows. If you are having trouble running the 64-bit version, try the 32-bit version. Linux Run this command in your terminal to check your operating system’s type: uname-m 2.1.2 Windows Portable or Not Portable? Sublime Text comes in two flavors for Windows: normal, and portable. Most users should be better served by a normal installation. Use the portable version only if you know you need it. Normal installations separate data between two folders: the installation folder proper, and the data directory (user- specific directory for data; explained later in this guide). -

V2616 Linux User's Manual Introduction
V2616 Linux User’s Manual First Edition, October 2011 www.moxa.com/product © 2011 Moxa Inc. All rights reserved. V2616 Linux User’s Manual The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. Copyright Notice © 2011 Moxa Inc. All rights reserved. Trademarks The MOXA logo is a registered trademark of Moxa Inc. All other trademarks or registered marks in this manual belong to their respective manufacturers. Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Moxa. Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any time. Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for its use, or for any infringements on the rights of third parties that may result from its use. This product might include unintentional technical or typographical errors. Changes are periodically made to the information herein to correct such errors, and these changes are incorporated into new editions of the publication. Technical Support Contact Information www.moxa.com/support Moxa Americas Moxa China (Shanghai office) Toll-free: 1-888-669-2872 Toll-free: 800-820-5036 Tel: +1-714-528-6777 Tel: +86-21-5258-9955 Fax: +1-714-528-6778 Fax: +86-21-5258-5505 Moxa Europe Moxa Asia-Pacific Tel: +49-89-3 70 03 99-0 Tel: +886-2-8919-1230 Fax: +49-89-3 70 03 99-99 Fax: +886-2-8919-1231 Table of Contents 1.