Insecure Context Switching: Inoculating Regular Expressions for Survivability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Replicated Execution for a More Secure and Reliable Web Browser
Using Replicated Execution for a More Secure and Reliable Web Browser Hui Xue Nathan Dautenhahn Samuel T. King University of Illinois at Urbana Champaign huixue2, dautenh1, kingst @uiuc.edu { } Abstract Unfortunately, hackers actively exploit these vulnerabil- ities as indicated in reports from the University of Wash- Modern web browsers are complex. They provide a ington [46], Microsoft [61], and Google [49, 48]. high-performance and rich computational environment Both industry and academia have improved the se- for web-based applications, but they are prone to nu- curity and reliability of web browsers. Current com- merous types of security vulnerabilities that attackers modity browsers make large strides towards improving actively exploit. However, because major browser plat- the security and reliability of plugins by using sandbox- forms differ in their implementations they rarely exhibit ing techniques to isolate plugins from the rest of the the same vulnerabilities. browser [62, 33]. However, these browsers still scatter In this paper we present Cocktail, a system that uses security logic throughout millions of lines of code, leav- three different off-the-shelf web browsers in parallel to ing these systems susceptible to browser-based attacks. provide replicated execution for withstanding browser- Current research efforts, like Tahoma [32], the OP web based attacks and improving browser reliability. Cock- browser [36], the Gazelle web browser [59], and the Illi- tail mirrors inputs to each replica and votes on browser nois Browser Operating System [58] all propose build- states and outputs to detect potential attacks, while con- ing new web browsers to improve security. Although tinuing to run. -

SAP on Google Cloud: High Availability
SAP on Google Cloud: High availability Overview © 2020 Google LLC. All rights reserved. Contents About this document 2 Introduction 2 Levels of high availability 3 Level 1: Infrastructure 3 Zones and regions 3 Live migration 4 Host auto restart 4 Level 2: Database setup 5 SAP HANA databases 5 Synchronous SAP HANA System Replication 5 SAP HANA host auto-failover on Google Cloud 7 SAP ASE databases 8 MaxDB databases 8 IBM Db2 databases 9 Microsoft SQL Server databases 9 Level 3: Application servers 10 Summary 12 Further reading 13 1 © 2020 Google LLC. All rights reserved. About this document This document is part of a series about working with SAP on Google Cloud. The series includes the following documents: ● High availability (this document) ● Migration strategies ● Backup strategies and solutions ● Disaster-recovery strategies Introduction The term high availability (HA) is used to describe an architecture that improves a system’s availability. The availability of a system refers to a user’s ability to connect to the system and conduct the required operations. If a user can’t connect, the system is perceived as unavailable, regardless of the underlying issue. For example, a networking issue can prevent users from accessing the service, even though the system is running. A high-availability setup interacts with multiple components of the architecture to minimize the points of failure, typically by using redundancy. To measure a service’s performance throughout the year, the metric of percentage of uptime is used to calculate the ratio of uptime to the aggregate of uptime and downtime. A system that is available for ~8750 hours during the 8760 hours of a year has an uptime of 99.89% (8750/8760) and a downtime of 10 hours. -
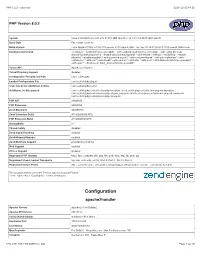
PHP 8.0.2 - Phpinfo() 2021-02-23 14:53
PHP 8.0.2 - phpinfo() 2021-02-23 14:53 PHP Version 8.0.2 System Linux effa5f35b7e3 5.4.83-v7l+ #1379 SMP Mon Dec 14 13:11:54 GMT 2020 armv7l Build Date Feb 9 2021 12:01:16 Build System Linux 96bc8a22765c 4.15.0-129-generic #132-Ubuntu SMP Thu Dec 10 14:07:05 UTC 2020 armv8l GNU/Linux Configure Command './configure' '--build=arm-linux-gnueabihf' '--with-config-file-path=/usr/local/etc/php' '--with-config-file-scan- dir=/usr/local/etc/php/conf.d' '--enable-option-checking=fatal' '--with-mhash' '--with-pic' '--enable-ftp' '--enable- mbstring' '--enable-mysqlnd' '--with-password-argon2' '--with-sodium=shared' '--with-pdo-sqlite=/usr' '--with- sqlite3=/usr' '--with-curl' '--with-libedit' '--with-openssl' '--with-zlib' '--with-pear' '--with-libdir=lib/arm-linux-gnueabihf' '- -with-apxs2' '--disable-cgi' 'build_alias=arm-linux-gnueabihf' Server API Apache 2.0 Handler Virtual Directory Support disabled Configuration File (php.ini) Path /usr/local/etc/php Loaded Configuration File /usr/local/etc/php/php.ini Scan this dir for additional .ini files /usr/local/etc/php/conf.d Additional .ini files parsed /usr/local/etc/php/conf.d/docker-php-ext-gd.ini, /usr/local/etc/php/conf.d/docker-php-ext-mysqli.ini, /usr/local/etc/php/conf.d/docker-php-ext-pdo_mysql.ini, /usr/local/etc/php/conf.d/docker-php-ext-sodium.ini, /usr/local/etc/php/conf.d/docker-php-ext-zip.ini PHP API 20200930 PHP Extension 20200930 Zend Extension 420200930 Zend Extension Build API420200930,NTS PHP Extension Build API20200930,NTS Debug Build no Thread Safety disabled Zend Signal Handling enabled -

MC-1200 Series Linux Software User's Manual
MC-1200 Series Linux Software User’s Manual Version 1.0, November 2020 www.moxa.com/product © 2020 Moxa Inc. All rights reserved. MC-1200 Series Linux Software User’s Manual The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. Copyright Notice © 2020 Moxa Inc. All rights reserved. Trademarks The MOXA logo is a registered trademark of Moxa Inc. All other trademarks or registered marks in this manual belong to their respective manufacturers. Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Moxa. Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any time. Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for its use, or for any infringements on the rights of third parties that may result from its use. This product might include unintentional technical or typographical errors. Changes are periodically made to the information herein to correct such errors, and these changes are incorporated into new editions of the publication. Technical Support Contact Information www.moxa.com/support Moxa Americas Moxa China (Shanghai office) Toll-free: 1-888-669-2872 Toll-free: 800-820-5036 Tel: +1-714-528-6777 Tel: +86-21-5258-9955 Fax: +1-714-528-6778 Fax: +86-21-5258-5505 Moxa Europe Moxa Asia-Pacific Tel: +49-89-3 70 03 99-0 Tel: +886-2-8919-1230 Fax: +49-89-3 70 03 99-99 Fax: +886-2-8919-1231 Moxa India Tel: +91-80-4172-9088 Fax: +91-80-4132-1045 Table of Contents 1. -

Implementation of the Programming Language Dino – a Case Study in Dynamic Language Performance
Implementation of the Programming Language Dino – A Case Study in Dynamic Language Performance Vladimir N. Makarov Red Hat [email protected] Abstract design of the language, its type system and particular features such The article gives a brief overview of the current state of program- as multithreading, heterogeneous extensible arrays, array slices, ming language Dino in order to see where its stands between other associative tables, first-class functions, pattern-matching, as well dynamic programming languages. Then it describes the current im- as Dino’s unique approach to class inheritance via the ‘use’ class plementation, used tools and major implementation decisions in- composition operator. cluding how to implement a stable, portable and simple JIT com- The second part of the article describes Dino’s implementation. piler. We outline the overall structure of the Dino interpreter and just- We study the effect of major implementation decisions on the in-time compiler (JIT) and the design of the byte code and major performance of Dino on x86-64, AARCH64, and Powerpc64. In optimizations. We also describe implementation details such as brief, the performance of some model benchmark on x86-64 was the garbage collection system, the algorithms underlying Dino’s improved by 3.1 times after moving from a stack based virtual data structures, Dino’s built-in profiling system, and the various machine to a register-transfer architecture, a further 1.5 times by tools and libraries used in the implementation. Our goal is to give adding byte code combining, a further 2.3 times through the use an overview of the major implementation decisions involved in of JIT, and a further 4.4 times by performing type inference with a dynamic language, including how to implement a stable and byte code specialization, with a resulting overall performance im- portable JIT. -

Red Hat Virtualization 4.4 Package Manifest
Red Hat Virtualization 4.4 Package Manifest Package listing for Red Hat Virtualization 4.4 Last Updated: 2021-09-09 Red Hat Virtualization 4.4 Package Manifest Package listing for Red Hat Virtualization 4.4 Red Hat Virtualization Documentation Team Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. -

Maxdb Security Guide
MaxDB Security Guide NetWeaver 2004s, SP 08 SAP Online Help June 2006 Copyright © Copyright 2006 SAP AG. All rights reserved. No part of this publication may be reproduced or transmitted in any form or for any purpose without the express permission of SAP AG. The information contained herein may be changed without prior notice. Some software products marketed by SAP AG and its distributors contain proprietary software components of other software vendors. Microsoft, Windows, Outlook, and PowerPoint are registered trademarks of Microsoft Corporation. IBM, DB2, DB2 Universal Database, OS/2, Parallel Sysplex, MVS/ESA, AIX, S/390, AS/400, OS/390, OS/400, iSeries, pSeries, xSeries, zSeries, z/OS, AFP, Intelligent Miner, WebSphere, Netfinity, Tivoli, Informix, i5/OS, POWER, POWER5, OpenPower and PowerPC are trademarks or registered trademarks of IBM Corporation. Adobe, the Adobe logo, Acrobat, PostScript, and Reader are either trademarks or registered trademarks of Adobe Systems Incorporated in the United States and/or other countries. Oracle is a registered trademark of Oracle Corporation. UNIX, X/Open, OSF/1, and Motif are registered trademarks of the Open Group. Citrix, ICA, Program Neighborhood, MetaFrame, WinFrame, VideoFrame, and MultiWin are trademarks or registered trademarks of Citrix Systems, Inc. HTML, XML, XHTML and W3C are trademarks or registered trademarks of W3C®, World Wide Web Consortium, Massachusetts Institute of Technology. Java is a registered trademark of Sun Microsystems, Inc. JavaScript is a registered trademark of Sun Microsystems, Inc., used under license for technology invented and implemented by Netscape. MaxDB is a trademark of MySQL AB, Sweden. SAP, R/3, mySAP, mySAP.com, xApps, xApp, SAP NetWeaver, and other SAP products and services mentioned herein as well as their respective logos are trademarks or registered trademarks of SAP AG in Germany and in several other countries all over the world. -

CAMS Operations Guide, Which You Can Find on the SAP Service Marketplace At
Application Operations Guide Complex Assembly Manufacturing Solution (CAMS) Operations Guide Release 7.2 Document Version 1.00 June 2012 SAP AG 2121 Palomar Airport Rd. Suite 350 Carlsbad, CA 92011 USA T 00/1/760-929-2300 F 00/1/760-929-2301 www.sap.com © Copyright 2012 SAP AG. All rights reserved. licensing terms described here, provided that the new terms are clearly indicated on the first page of each file where they apply. No part of this publication may be reproduced or transmitted in any form or for any purpose without the express permission of SAP AG. The information contained herein may IN NO EVENT SHALL THE AUTHORS OR DISTRIBUTORS BE LIABLE TO ANY be changed without prior notice. PARTY FOR DIRECT, INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OF THIS SOFTWARE, ITS Some software products marketed by SAP AG and its distributors contain proprietary DOCUMENTATION, OR ANY DERIVATIVES THEREOF, EVEN IF THE AUTHORS software components of other software vendors. HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Microsoft, Windows, Outlook, and PowerPoint are registered trademarks of Microsoft THE AUTHORS AND DISTRIBUTORS SPECIFICALLY DISCLAIM ANY Corporation. WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR IBM, DB2, DB2 Universal Database, OS/2, Parallel Sysplex, MVS/ESA, AIX, S/390, PURPOSE, AND NON-INFRINGEMENT. THIS SOFTWARE IS PROVIDED ON AN AS/400, OS/390, OS/400, iSeries, pSeries, xSeries, zSeries, z/OS, AFP, Intelligent Miner, "AS IS" BASIS, AND THE AUTHORS AND DISTRIBUTORS HAVE NO WebSphere, Netfinity, Tivoli, and Informix are trademarks or registered trademarks of OBLIGATION TO PROVIDE MAINTENANCE, SUPPORT, UPDATES, IBM Corporation in the United States and/or other countries. -
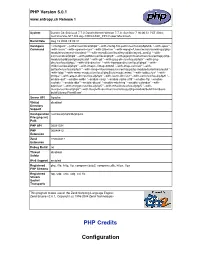
PHP Credits Configuration
PHP Version 5.0.1 www.entropy.ch Release 1 System Darwin G4-500.local 7.7.0 Darwin Kernel Version 7.7.0: Sun Nov 7 16:06:51 PST 2004; root:xnu/xnu-517.9.5.obj~1/RELEASE_PPC Power Macintosh Build Date Aug 13 2004 15:03:31 Configure './configure' '--prefix=/usr/local/php5' '--with-config-file-path=/usr/local/php5/lib' '--with-apxs' '- Command -with-iconv' '--with-openssl=/usr' '--with-zlib=/usr' '--with-mysql=/Users/marc/cvs/entropy/php- module/src/mysql-standard-*' '--with-mysqli=/usr/local/mysql/bin/mysql_config' '--with- xsl=/usr/local/php5' '--with-pdflib=/usr/local/php5' '--with-pgsql=/Users/marc/cvs/entropy/php- module/build/postgresql-build' '--with-gd' '--with-jpeg-dir=/usr/local/php5' '--with-png- dir=/usr/local/php5' '--with-zlib-dir=/usr' '--with-freetype-dir=/usr/local/php5' '--with- t1lib=/usr/local/php5' '--with-imap=../imap-2002d' '--with-imap-ssl=/usr' '--with- gettext=/usr/local/php5' '--with-ming=/Users/marc/cvs/entropy/php-module/build/ming-build' '- -with-ldap' '--with-mime-magic=/usr/local/php5/etc/magic.mime' '--with-iodbc=/usr' '--with- xmlrpc' '--with-expat -dir=/usr/local/php5' '--with-iconv-dir=/usr' '--with-curl=/usr/local/php5' '-- enable-exif' '--enable-wddx' '--enable-soap' '--enable-sqlite-utf8' '--enable-ftp' '--enable- sockets' '--enable-dbx' '--enable-dbase' '--enable-mbstring' '--enable-calendar' '--with- bz2=/usr' '--with-mcrypt=/usr/local/php5' '--with-mhash=/usr/local/php5' '--with- mssql=/usr/local/php5' '--with-fbsql=/Users/marc/cvs/entropy/php-module/build/frontbase- build/Library/FrontBase' Server -

Java Security White Paper
WHERE’S THE FIRE? Java Security Fears Are More “Smoke and Mirrors” Than Five-Alarm Fire In fact, the government agency tasked with monitoring technological security vulnerabilities ranks Java as more secure than dozens of other technologies and products. This paper will explore the disconnect between inflammatory rhetoric and data-backed reality. Java security is a disaster, if the headlines are FUD is not a realistic portrayal of the state of to be believed. No other technology poses such Java security; it's a propagandistic tactic meant an egregious risk, they tell us. The only to influence public perception with the overwhelming presentation of negative, solution, many pundits and proponents of dubious or outright inaccurate information. other technologies insist, is the nuclear option: FUD is also known as “fear-mongering,” and completely uninstall Java from your computers, you may recognize it from other areas of life, servers and networks. like politics. Is Java truly such an abysmal security failure, as But fear not: in this paper, we are going to ask portrayed by the press and non-Java software and answer three very specific, pertinent questions whose answers are then drawn from companies? No, but the point of this paper is reputable, independent sources. not to prove that it's totally secure. Yes, Java has security vulnerabilities. So does everything 1. Does Java face more security else. No technology platform or product is vulnerabilities than other technologies? totally secure; and the surprising reality is that, 2. Are Java security vulnerabilities more in the spectrum of security risk, Java does not severe? fall anywhere close to where you think it does. -

Proceedings: Shrubland Dynamics -- Fire and Water
Proceedings: Shrubland Dynamics—Fire and Water Lubbock, TX, August 10-12, 2004 United States Department of Agriculture Forest Service Rocky Mountain Research Station Proceedings RMRS-P-47 July 2007 Sosebee, Ronald E.; Wester, David B.; Britton, Carlton M.; McArthur, E. Durant; Kitchen, Stanley G., comps. 2007. Proceedings: Shrubland dynamics—fire and water; 2004 August 10-12; Lubbock, TX. Proceedings RMRS-P-47. Fort Collins, CO: U.S. Department of Agriculture, Forest Service, Rocky Mountain Research Station. 173 p. Abstract The 26 papers in these proceedings are divided into five sections. The first two sections are an introduction and a plenary session that introduce the principles and role of the shrub life-form in the High Plains, including the changing dynamics of shrublands and grasslands during the last four plus centuries. The remaining three sections are devoted to: fire, both prescribed fire and wildfire, in shrublands and grassland-shrubland interfac- es; water and ecophysiology shrubland ecosystems; and the ecology and population biology of several shrub species. Keywords: wildland shrubs, fire, water, ecophysiology, ecology The use of trade or firm names in this publication is for reader information and does not imply endorsement by the U.S. Department of Agriculture or any product or service. Publisher’s note: Papers in this report were reviewed by the compilers. Rocky Mountain Research Station Publishing Services reviewed papers for format and style. Authors are responsible for content. You may order additional copies of this publication by sending your mailing information in label form through one of the following media. Please specify the publication title and series number. -

Introducing Regular Expressions
Introducing Regular Expressions wnload from Wow! eBook <www.wowebook.com> o D Michael Fitzgerald Beijing • Cambridge • Farnham • Köln • Sebastopol • Tokyo Introducing Regular Expressions by Michael Fitzgerald Copyright © 2012 Michael Fitzgerald. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Simon St. Laurent Indexer: Lucie Haskins Production Editor: Holly Bauer Cover Designer: Karen Montgomery Proofreader: Julie Van Keuren Interior Designer: David Futato Illustrator: Rebecca Demarest July 2012: First Edition. Revision History for the First Edition: 2012-07-10 First release See http://oreilly.com/catalog/errata.csp?isbn=9781449392680 for release details. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. Introducing Regular Expressions, the image of a fruit bat, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc., was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and authors assume no responsibility for errors or omissions, or for damages resulting from the use of the information con- tained herein.