Interagency Journal Vol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Purpose of the First World War War Aims and Military Strategies Schriften Des Historischen Kollegs
The Purpose of the First World War War Aims and Military Strategies Schriften des Historischen Kollegs Herausgegeben von Andreas Wirsching Kolloquien 91 The Purpose of the First World War War Aims and Military Strategies Herausgegeben von Holger Afflerbach An electronic version of this book is freely available, thanks to the support of libra- ries working with Knowledge Unlatched. KU is a collaborative initiative designed to make high quality books Open Access. More information about the initiative can be found at www.knowledgeunlatched.org Schriften des Historischen Kollegs herausgegeben von Andreas Wirsching in Verbindung mit Georg Brun, Peter Funke, Karl-Heinz Hoffmann, Martin Jehne, Susanne Lepsius, Helmut Neuhaus, Frank Rexroth, Martin Schulze Wessel, Willibald Steinmetz und Gerrit Walther Das Historische Kolleg fördert im Bereich der historisch orientierten Wissenschaften Gelehrte, die sich durch herausragende Leistungen in Forschung und Lehre ausgewiesen haben. Es vergibt zu diesem Zweck jährlich bis zu drei Forschungsstipendien und zwei Förderstipendien sowie alle drei Jahre den „Preis des Historischen Kollegs“. Die Forschungsstipendien, deren Verleihung zugleich eine Auszeichnung für die bisherigen Leis- tungen darstellt, sollen den berufenen Wissenschaftlern während eines Kollegjahres die Möglich- keit bieten, frei von anderen Verpflichtungen eine größere Arbeit abzuschließen. Professor Dr. Hol- ger Afflerbach (Leeds/UK) war – zusammen mit Professor Dr. Paul Nolte (Berlin), Dr. Martina Steber (London/UK) und Juniorprofessor Simon Wendt (Frankfurt am Main) – Stipendiat des Historischen Kollegs im Kollegjahr 2012/2013. Den Obliegenheiten der Stipendiaten gemäß hat Holger Afflerbach aus seinem Arbeitsbereich ein Kolloquium zum Thema „Der Sinn des Krieges. Politische Ziele und militärische Instrumente der kriegführenden Parteien von 1914–1918“ vom 21. -
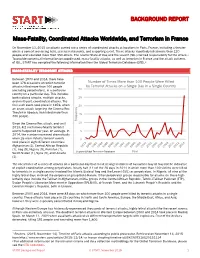
Mass-Fatality, Coordinated Attacks Worldwide, and Terrorism in France
BACKGROUND REPORT Mass-Fatality, Coordinated Attacks Worldwide, and Terrorism in France On November 13, 2015 assailants carried out a series of coordinated attacks at locations in Paris, France, including a theater where a concert was being held, several restaurants, and a sporting event. These attacks reportedly killed more than 120 people and wounded more than 350 others. The Islamic State of Iraq and the Levant (ISIL) claimed responsibility for the attack.1 To provide contextual information on coordinated, mass-fatality attacks, as well as terrorism in France and the attack patterns of ISIL, START has compiled the following information from the Global Terrorism Database (GTD).2 MASS-FATALITY TERRORIST ATTACKS Between 1970 and 2014, there have been 176 occasions on which terrorist Number of Times More than 100 People Were Killed attacks killed more than 100 people by Terrorist Attacks on a Single Day in a Single Country (excluding perpetrators), in a particular 30 country on a particular day. This includes both isolated attacks, multiple attacks, 25 and multi-part, coordinated attacks. The first such event took place in 1978, when 20 an arson attack targeting the Cinema Rex Theater in Abadan, Iran killed more than 15 400 people. Frequency Since the Cinema Rex attack, and until 10 2013, 4.2 such mass-fatality terrorist events happened per year, on average. In 5 2014, the number increased dramatically when 26 mass-fatality terrorist events 0 took place in eight different countries: Afghanistan (1), Central African Republic (1), Iraq (9), Nigeria (9), Pakistan (1), Source: Global Terrorism Database Year South Sudan (1), Syria (3), and Ukraine (1). -

US-World War I
World War One (The Great War) 1914 - 1918 http://www.bbc.co.uk/remembrance/img/gassed_446x251.jpg “Gassed,” John Singer Sargent (1919) Quick Overview The war began in August 1914 When war broke out, the U. S. declared itself neutral The U.S. entered the war on April 6, 1917 The fighting ended with a cease-fire agreement on November 11, 1918 Approximately 9 million soldiers were killed. At least 21 million soldiers were wounded. MAIN Causes of the War MILITARISM The Glorification of military power An Arms Race (Competition to build the most powerful weapons) took place - lead to fear MAIN Causes of the War Alliances Suspicions about other nations led to the formation of alliances Triple Alliance Germany, Austria-Hungary, and Italy Triple Entente Britain, France and Russia MAIN Causes of the War Imperialism Competition between European nations over land and resources created rivalries in Africa American imperialism in Latin America and Asia was also a source of concern & tension MAIN Causes of the War Nationalism A deep pride in one’s own country - believing that it is better than all nations European nations competed to prove the superiority of their cultures U.S. - “God’s Chosen People” http://web.viu.ca/davies/H482.WWI/poster.US.DestroyThisMadBrute.jpg Archduke Franz Ferdinand and His Family He was to be the next emperor of Austria-Hungary The Assassination Franz Ferdinand was killed by a Serbian nationalist in Sarajevo June 28, 1914 This event “sparked” war in Europe The Fighting Begins Austria-Hungary declared war on Serbia on July 28, -

Attentats Du 13 Novembre 2015 En France
Attentats du 13 novembre 2015 en France Les attentats du 13 novembre 2015 en France, sur- et de l'État islamique, commettent une série d'attentats venus dans la soirée du vendredi 13 novembre 2015, et — qui commence par la tuerie au siège du journal Char- revendiqués par l'organisation terroriste État islamique, lie Hebdo et se termine par la prise d'otages de l’Hyper sont une série de fusillades et d’attentats-suicides qui Cacher — faisant dix-sept victimes. s’est produite en Île-de-France, pour l’essentiel à Paris e e D'autres attentats de moindre échelle ont eu lieu depuis dans les 10 et 11 arrondissements (rue Bichat, rue de la fin de l'année 2014. En avril 2015, Sid Ahmed Gh- , rue de Charonne, au Bataclan, et la Fontaine-au-Roi lam échoue dans son projet d'attentat, mais tue néan- boulevard Voltaire), ainsi qu’à Saint-Denis aux abords du moins Aurélie Châtelain à Villejuif (Val-de-Marne). Le stade de France. 26 juin, Yassin Salhi étrangle et égorge son patron, puis Des coups de feu visant des terrasses de restaurants et tente de faire exploser une usine de production de gaz cafés font plusieurs dizaines de morts dans les 10e et industriels et médicaux classée Seveso à Saint-Quentin- 11e arrondissements de Paris. Dans le même temps, des Fallavier (Isère). Le 13 juillet, quatre jeunes de 16 à 23 terroristes kamikazes se font exploser aux abords du stade ans, dont un ancien militaire, sont soupçonnés de pro- de France, où se déroule un match amical de football jeter une attaque contre le camp militaire du fort Béar, France-Allemagne. -

La Memorisation Et Perception Des Attentats Du 13 Novembre 2015 En France 7 Mois Apres
POLE EVALUATION ET SOCIETE LA MEMORISATION ET PERCEPTION DES ATTENTATS DU 13 NOVEMBRE 2015 EN FRANCE 7 MOIS APRES Rapport rédigé dans le cadre du programme 13 novembre, porté par le CNRS, l'Inserm et héSam Université, financé par l'Agence nationale de la recherche (ANR) dans le cadre du Programme Investissements d'Avenir (PIA). Contrat ANR-10-EQPX-0021-01 volet Programme 13-Novembre. DOI : 10.5281/zenodo.4249155 Sandra Hoibian, Charlotte Millot, Jacqueline Eidelman, Gérôme Truc, Mathilde Perrin, Francis Eustache, Denis Peschanski Avec la participation de Régis Bigot, Radmila Datsenko et Pauline Jauneau- Cottet 142, rue du Chevaleret 75013 PARIS Tél. 01 40 77 85 50 Fax 01 40 77 85 09 NOVEMBRE 2016 Avant-propos méthodologique Programme 13 novembre CREDOC 13-Novembre est un programme de recherche transdisciplinaire qui se déroulera sur 12 ans. Son objectif est d’étudier la construction et l’évolution de la mémoire après les attentats du 13 novembre 2015, et en particulier l’articulation entre mémoire individuelle et mémoire collective. La mémoire est un élément essentiel de la construction de l’identité individuelle comme de l’identité collective. En ce sens, la mémoire des attentats du 13 novembre participe et participera à façonner la société de demain. C’est le rôle de la recherche scientifique d’analyser ces phénomènes pour nous permettre de mieux les comprendre et mieux les appréhender. Il s’agit également de conserver et de transmettre la mémoire des attentats du 13 novembre. C’est une forme d’engagement de la part de la communauté scientifique envers les citoyens. -

Chapter Six the War Grinds to a Gruesome End
Chapter Six The War Grinds to a Gruesome End 5 The Armistice came, the day we had dreamed of. The guns stopped, the fighting stopped. Four years of noise and bangs ended in silence. The killings had stopped. We were stunned. I had been out since 1914. I should have been happy. I was sad. I thought of the slaughter, the hardships, the waste, and the friends I had lost.1 —British sergeant-major Richard Tobin of the Army’s Royal Naval Division ussia’s withdrawal from the Great War in late 1917 was a major benefit to Germany and the other Central Powers. True, the Germans would have R to leave some manpower in place in the East in order to keep an eye on Ukraine, Poland, Finland, and Baltic states that it had received according to the terms of the Treaty of Brest-Litovsk. But with Russia no longer a concern, Ger- man military commanders could still shift huge numbers of troops, guns, and other military resources to the Western Front, where the enemy remained for- midable. The only question that remained, according to German strategists, was whether this additional muscle would enable them to defeat reeling French and British armies before Americans troops began pouring into Europe. A Race Against Time for Germany In early 1918 Kaiser Wilhelm II remained Germany’s emperor and the offi- cial commander-in-chief of its military. In reality, however, the war had elevat- ed the country’s generals to positions of influence that eclipsed the Kaiser. From 1916 to 1918, in fact, Germany operated under an unoffical military dictator- 89 Defining Moments: World War I and the Age of Modern Warfare ship—a “silent dictatorship” in the words of some historians—led by two men, Chief of the General Staff Paul von Hindenburg and his deputy, First Quar- termaster-General Erich Ludendorff (see biography, p. -

The Impact of World War I
IMPACTIMPACT OF OF WORLD WORLD WAR WAR I I •• WorldWorld War War I I has has been been called called a a ““warwar with with many many causes causes but but no no objectivesobjectives..”” •• ThisThis profound profound sense sense of of wastewaste andand pointlessness pointlessness willwill shape shape EuropeanEuropean politics politics in in the the post post-- warwar period. period. NewNew Horrors Horrors for for a a New New Century Century •• TotalTotal WarWar •• IndustrialIndustrial weaponsweapons ofof massmass--killingkilling •• ExtremeExtreme NationalismNationalism •• CiviliansCivilians targetedtargeted •• Genocide:Genocide: TurksTurks slaughterslaughter ArmeniansArmenians •• CommunistCommunist RevolutionRevolution •• TerrorismTerrorism AftermathAftermath ofof WorldWorld WarWar I:I: ConsequencesConsequences SocialSocial:: •• almostalmost 1010 millionmillion soldierssoldiers werewere killedkilled andand overover 2020 millionmillion areare woundedwounded •• millionsmillions ofof civilianscivilians dieddied asas aa resultresult ofof thethe hostilities,hostilities, famine,famine, andand diseasedisease •• thethe worldworld waswas leftleft withwith hatred,hatred, intolerance,intolerance, andand extremeextreme nationalism.nationalism. WorldWorld War War I I Casualties Casualties 10,000,000 9,000,000 Russia 8,000,000 Germany 7,000,000 Austria-Hungary 6,000,000 France 5,000,000 4,000,000 Great Britain 3,000,000 Italy 2,000,000 Turkey 1,000,000 US 0 TheThe Spanish Spanish Flu Flu (Influenza) (Influenza) -- 19181918 •• StruckStruck inin thethe -

THE SUBLIME in CONTEMPORARY ART and POLITICS: “The Post-9/11 Art of the Middle Eastern Diaspora in North America”
THE SUBLIME IN CONTEMPORARY ART AND POLITICS: “The post-9/11 Art of the Middle Eastern Diaspora in North America” TALAT BALCA ARDA GUNEY A DISSERTATION SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY GRADUATE PROGRAM IN POLITICAL SCIENCE YORK UNIVERSITY TORONTO, ONTARIO April 2016 © Talat Balca Arda Guney, 2016 Abstract The Sublime in Contemporary Art and Politics: The post-9/11 Art of the Middle Eastern Diaspora in North America This dissertation takes ethnographic approach to researching art with an emphasis on the artistic practices of Middle Eastern diasporic artists in Canada and the USA. This dissertation moves from an account of aesthetic theory to the revival of public interest in art related to the Middle East and the artistic challenges faced by diasporic artists from the Middle East in presenting depictions of their own subjectivity. The Arab Spring, revolutions, bloody protests and riots, as well as the attacks of radical Islamist groups have crowded mainstream news coverage with images of terror and the paradigm of radical destruction. Such reflections of horrific scenery emulate the aesthetics of the sublime in the imagination of contemporary politics. The increasing body of art emphasizing the region of the Middle East has also regenerated this mainstream media focus on the Middle East, Arab lands, and the “Muslim landscape" with the same connotation of sublimity. I argue that these artistic reflections presume a particular Middle Eastern diasporic subjectivity that comes into visibility simultaneously as the translator and the witness, as well as the victim or perpetrator of this catastrophic imagery of the Middle East. -

(Macro-) Securitization? a Comparison of Political Reactions
Croatian International Same Old (Macro-) Relations Review — Securitization? A Comparison CIRR — XXV (84) 2019, of Political Reactions to Major 6-35 — Terrorist Attacks in the United DOI 10.2478/ cirr-2019-0001 — States and France UDC 323.28:327.8(73:44) — Elena Dück University of Passau, Germany [email protected] ORCID: 0000-0002-2624-0083 Robin Lucke [email protected] Abstract Key words: After the November 2015 terror attacks in Paris, the French government macro-securitization; reacted swiftly by declaring a state of emergency. This state of securitization; emergency remained in place for over two years before it was ended terrorism; Global in November 2017, only after being replaced by the new anti-terror War on Terror; legislation. The attacks as well as the government’s reactions evoked France. parallels to 9/11 and its aftermath. This is a puzzling observation when taking into consideration that the Bush administration’s reactions have been criticized harshly and that the US ‘War on Terror’ (WoT) was initially considered a serious failure in France. We can assume that this adaption of the discourse and practices stems from a successful establishment of the WoT macro-securitization. By using Securitization Theory, we outline the development of this macro-securitization by comparing its current manifestation in France against the backdrop of its origins in the US after 9/11. We analysed securitizing moves in the discourses, as well as domestic and international emergency measure policies. We find extensive similarities with view of both; yet there are differing degrees of securitizing terrorism and the institutionalisation of the WoT in the two states. -

Of the Modern Age
1 1 Interior with a Table, 1921. Vanessa Bell. Oil on canvas. 21 /4 x 25 /4 inches. Tate Gallery, London. ©1961 Estate of Vanessa Bell. Courtesy of Henrietta Garnett. 1028 Tate Gallery, London/Art Resource, NY 1028-1042 UOU6-845482.indd 1028 1/29/07 1:43:43 PM UNIT SIX THE MODERN AGE 1901–1950 Looking Ahead When the twentieth century began, Britain was at the height of its power. During the next half century, the British endured bitter class conflict, two world wars, global economic depression, and growing demands for independence among the colonial peoples they ruled. This period of profound change also witnessed the emergence of powerful Modernist writers, who modified and broke with the forms and traditions of British literature. Keep the following questions in mind as you read: ▲▲▲ ▲ How did World Wars I and II impact British literature? How was class conflict represented in British literature? How did attitudes toward the British Empire begin to change during this period? What were some major characteristics of Modernism? OBJECTIVES In learning about the Modern age, you will focus on the following: • analyzing the characteristics of modern literature and how issues of the period influenced writers • evaluating the influences of the historical forces that shaped literary characters, plots, settings, and themes in modern literature • connecting modern literature to historical contexts, current events, and your own experiences 1029 11028-1042028-1042 UOU6-845482.inddUOU6-845482.indd 10291029 11/10/07/10/07 8:29:258:29:25 AMAM TIMELINE 1901–1950 BRITISH LITERATURE 1900 1920 1901 1914 1917 1920 Rudyard Kipling publishes Modernist journal Blast William Butler Yeats Wilfred Owen’s Collected Kim begins publication ▼ publishes The Wild Swans Poems is published at Coole 1907 1922 Rudyard Kipling wins Nobel 1918 Katherine Mansfield Prize in Literature Siegfried Sassoon publishes publishes The Garden Party Counter-Attack 1913 1922 George Bernard Shaw’s T. -

Sasha Massey St Patrick's College
THE Simpson PRIZE A COMPETITION FOR YEAR 9 AND 10 STUDENTS 2017 Winner Tasmania Sasha Massey St Patrick's College "The experience of Australian soldiers on the Western Front in 1916 has been largely overlooked in accounts of the First World War." To what extent would you argue that battles such as Fromelles and Pozières should feature more prominently in accounts of the First World War? It has been engraved into our national identity to commemorate the sacrifice of those who have participated in conflict, but perhaps one of the greatest tragedies of how we remember World War 1 is that details of battles on the Western Front have eluded the Australian public. Gallipoli, ANZAC Cove and Lone Pine usually dominate the national conversation on ANZAC Day, but the Western Front deserves greater recognition. The loss of a loved one on the Western Front is not an uncommon story, with approximately 45,000 Australian’s being killed.1 The Australian soldiers faced a monumental struggle in France and Belgium, with an immense death toll and unspeakable conditions. It is not only the conditions that were faced that justify the need for a more prominent commemoration of the battles on the Western Front, but they are also very important in the formation of the ANZAC spirit. When Australians think of the ANZACs, we think of tremendous courage, mateship and heroism, qualities that were displayed in abundance on the Western Front, especially at Fromelles and Pozieres. By preserving the legacy of those who served at Pozieres and Fromelles we can remember the lessons they taught us and strive for the qualities they demonstrated. -

Active Shooter: Recommendations and Analysis for Risk Mitigation
. James P. O’Neill . Police Commissioner . John J. Miller . Deputy Commissioner of . Intelligence and . Counterterrorism ACTIVE SHOOTER James R. Waters RECOMMENDATIONS AND ANALYSIS Chief of Counterterrorism FOR RISK MITIGATION 2016 EDITION AS RELEASED BY THE NEW YORK CITY POLICE DEPARTMENT TABLE OF CONTENTS ACKNOWLEDGEMENTS ................................................................................................................2 EXECUTIVE SUMMARY .................................................................................................................3 RECENT TRENDS ........................................................................................................................6 TRAINING & AWARENESS CHALLENGE RESPONSE .................................................................................... 6 THE TARGETING OF LAW ENFORCEMENT & MILITARY PERSONNEL: IMPLICATIONS FOR PRIVATE SECURITY ........ 7 ATTACKERS INSPIRED BY A RANGE OF IDEOLOGIES PROMOTING VIOLENCE ................................................... 8 SOCIAL MEDIA PROVIDES POTENTIAL INDICATORS, SUPPORTS RESPONSE .................................................... 9 THE POPULARITY OF HANDGUNS, RIFLES, AND BODY ARMOR NECESSITATES SPECIALIZED TRAINING .............. 10 BARRICADE AND HOSTAGE-TAKING REMAIN RARE OCCURRENCES IN ACTIVE SHOOTER EVENTS .................... 10 RECOMMENDATIONS ................................................................................................................11 POLICY .........................................................................................................................................