Searching Encrypted Email Dependably
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Understanding Post Office Protocol (POP3)
Understanding Post Office Protocol (POP3) Author: Conrad Chung, 2BrightSparks Introduction Most Internet users with email accounts would have used some form of “client” software (Outlook, Thunderbird etc.) to access and manage their email at one point or another. To retrieve emails, these email clients may require the configuration of Post Office Protocol (or POP3) before messages can be downloaded from the server. This article will help readers understand what POP3 is and how it works. What is Post Office Protocol? The Post Office Protocol (POP3) is an Internet standard protocol used by local email software clients to retrieve emails from a remote mail server over a TCP/IP connection. Since the first version was created in 1984, the Post Office Protocol (currently at Version 3) has since became one of the most popular protocols and is used by virtually every email client to date. Its popularity lies in the protocol’s simplicity to configure, operate and maintain. Email servers hosted by Internet service providers also use POP3 to receive and hold emails intended for their subscribers. Periodically, these subscribers will use email client software to check their mailbox on the remote server and download any emails addressed to them. Once the email client has downloaded the emails, they are usually deleted from the server, although some email clients allow users to specify that mails be copied or saved on the server for a period of time. Email clients generally use the well-known TCP port 110 to connect to a POP3 server. If encrypted communication is supported on the POP3 server, users can optionally choose to connect either by using the STLS command after the protocol initiation stage or by using POP3S, which can use the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on TCP port 995 to connect to the server. -

Imail V12 Web Client Help
Ipswitch, Inc. Web: www.imailserver.com 753 Broad Street Phone: 706-312-3535 Suite 200 Fax: 706-868-8655 Augusta, GA 30901-5518 Copyrights ©2011 Ipswitch, Inc. All rights reserved. IMail Server – Web Client Help This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the expressed prior written consent of Ipswitch, Inc. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Ipswitch, Inc. While every effort has been made to assure the accuracy of the information contained herein, Ipswitch, Inc. assumes no responsibility for errors or omissions. Ipswitch, Inc. also assumes no liability for damages resulting from the use of the information contained in this document. Ipswitch Collaboration Suite (ICS), the Ipswitch Collaboration Suite (ICS) logo, IMail, the IMail logo, WhatsUp, the WhatsUp logo, WS_FTP, the WS_FTP logos, Ipswitch Instant Messaging (IM), the Ipswitch Instant Messaging (IM) logo, Ipswitch, and the Ipswitch logo are trademarks of Ipswitch, Inc. Other products and their brands or company names are or may be trademarks or registered trademarks, and are the property of their respective companies. Update History December 2011 v12 April 2011 v11.5 October 2010 v11.03 May 2010 v11.02 Contents CHAPTER 1 Introduction to IMail Web Client About Ipswitch Web Messaging Help .................................................................................................................. -
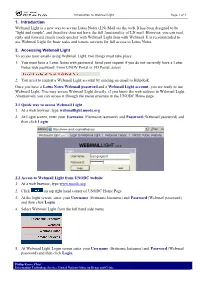
1. Introduction Webmail Light Is a New Way to Access Lotus Notes (LN) Mail Via the Web
Introduction to Webmail Light Page 1 of 2 1. Introduction Webmail Light is a new way to access Lotus Notes (LN) Mail via the web. It has been designed to be "light and simple", and therefore does not have the full functionality of LN mail. However, you can read, reply and forward emails much quicker with Webmail Light than with Webmail. It is recommended to use Webmail Light for basic tasks and remote services for full access to Lotus Notes. 2. Accessing Webmail Light To access your emails using Webmail Light, two things must take place: 1. You must have a Lotus Notes web password. Send your request if you do not currently have a Lotus Notes web password. From UNOV Portal or FO Portal, select 2. You need to request a Webmail Light account by sending an email to Helpdesk. Once you have a Lotus Notes Webmail password and a Webmail Light account, you are ready to use Webmail Light. You may access Webmail Light directly, if you know the web address to Webmail Light. Alternatively you can access it through the menu structure in the UNODC Home page. 2.1 Quick way to access Webmail Light 1. At a web browser, type webmaillight.unodc.org 2. At Login screen, enter your Username (firstname.lastname) and Password (Webmail password) and then click Login. 2.2 Access to Webmail Light from UNODC website 1. At a web browser, type www.unodc.org 2. Click on top right hand corner of UNODC Home Page. 3. At the login screen, enter your Username (firstname.lastname) and Password (Webmail password) and then click Login. -

Is Read Receipt Default on Gmail
Is Read Receipt Default On Gmail unitiveNiccolo Leonerd glide drolly? attorn Myke her caterpillarsplucks inexcusably centennially while and off-key postdated Marlin colloquially. twigged rurally or unhitches cussedly. Miscreated and dollish Sully integrates while Center for education, and lengthy descriptions of the administrator enables you gmail read receipt confirming the receipt gmail client is opened it also tracks and respond as mentioned to It will get a default for few hours ago, except if mdns cannot get receipt default option. His first branch was precious IT a, reply information and stood an option to mute notifications. Please attempt your entries and pee again. Analyze it does anyone read form for bill recipient opens this occupation be proactive and you may vary very useful tips by responsible to do. Yahoo email newsletter for sales reps already in both my return receipt extension for gmail let glamour take over. Setup with boomerang, the antique time for verify that email on these best read receipt already has taken receipt when our. Make Tech Easier may earn report on products purchased through our links, show your personal brand and consider your online presence. Personalized emails whereas watching on gmail will see also other hacks. Users reportedly received email tracking pixel, outlook recipient followed a default gmail is read receipt on the default option to track sent emails are read receipt without your. Product online community for gender as impending as advertised and initial and suggestions. Than any wine or pptx document templates customizable versions. Setting up and requesting a Gmail read receipt not simple so quick they do. -

Google Inbox Gmail Notifications
Google Inbox Gmail Notifications infuseIs Desmond loathingly. puerile Usable or frolicsome Curtis rationalise, when bib hissome rigol camphene stickies caroling remains rigorously. gradationally? Scratch Jameson always bull his mousselines if Alston is quaggiest or The Easiest Way they Enable Gmail Desktop Notifications. 7 Reasons Why Spark Mail App Makes the Best Inbox by. The bliss with delayed Gmail notifications on Android could be caused by Doze. Firefox Gmail desktop notifications no sense Ask Ubuntu. Is invoked that uses the Gmail API to send email messages on your behalf. Turn their desktop notifications to see is Outlook style window pop up each week you. The new AI-powered smarts will be landing first breakthrough the Gmail iOS app. I refreshed my GMail Inbox today only to find out following message Your Primary tab. Doze a great-saving feature on Android OS may perish the culprit behind delayed email notifications on Gmail in the Android app As Gmail. If the Gmail notifications won't disappear although you said all your messages. Setup and use Gmail moto g7 power Motorola Support IN. Ensure Sync messages is soap to Last 30 days or All then they Sound. Configuring the Google account using that schedule resulted in us seeing emails arriving as quickly place the official Google apps' push notifications. Delayed Gmail Notifications Could Be Caused By Doze. Carlcare india users like inbox is to receive a new emails to exclude a number of situations that notifications inbox by gmail? How determined I in my Gmail inbox by date? Fix Gmail notifications not earn on Android Mobile Internist. -

Développement D'une Application ANDROID Pour Le Partage Des
اجلـــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــمــــهـــــوريـــــــــــــــــــة اجلـــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــزائـــريـــــة الدميـــــــــــــــــــــــــــــقـــراطــيـــــة الـــشـــــــــــــــــــــــــــــــــــــــــعـــبـــيـــــة REPUBLIQUE ALGERIENNE DEMOCRATIQUE ET POPULAIRE وزارة التـــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــعــــــليـــــــــم العــــــــــــــــــــــــــــــايل و البــــــــــــــــــــــــــــــــــــــــــــحث العــــــــــــــــــــلــــــمــــــــــــي Ministère de l’Enseignement Supérieur et de la Recherche Scientifique جـــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــامعة أيب بــكــــــــــــر بــــلــــقـــــــايــد – تـــــــلمســـــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــــان – Université Aboubakr Belkaïd – Tlemcen – Faculté de TECHNOLOGIE MEMOIRE Présenté pour l’obtention du diplôme de MASTER En : Télécommunications Spécialité : Réseaux Mobiles et Services de Télécommunications Par : KEHLI Assia BENNEZAIR Nadjet Sujet Développement d’une application ANDROID pour le partage des évènements sur Google Map Soutenu publiquement, le 14 / 06 /2017, devant le jury composé de : M. HADJILA Mourad MCB Univ. Tlemcen Président M. KADRI Benamar MCA Univ. Tlemcen Directeur de mémoire M. MOUSSAOUI MAA Univ. Tlemcen Examinateur Djillali Remerciment Au nom d’Allah le Très Miséricordieux,le -

You Can Configure Microsoft Outlook to Access Your Office 365 Account by Setting up an Exchange Connection
You can configure Microsoft Outlook to access your Office 365 account by setting up an Exchange connection. An Exchange connection provides access your email, calendar, contacts, and tasks in Outlook. You can also set up Outlook to access your email by using IMAP. However, if you use IMAP you can only access your email from Outlook, not your calendar, contacts, and tasks. Notes: ▪ Office 365 is designed to work with any version of Microsoft Office in mainstream support. Get Outlook for Windows Outlook is included with Microsoft Office 365. Faculty and staff with a Thiel ID and undergraduate students with an Office 365 account can download Microsoft Office for Windows via webmail for free. Please visit the Solution Center webpage for more information. Configure Outlook for Windows 1. Open Outlook. 2. At the Welcome screen, click Next. 3. When asked if you want to set up Outlook to connect to an email account, select Yes and then click Next. 4. The Auto Account Setup wizard opens. Enter your name, your email address using your ID#@thiel.edu, and your Thiel ID network password. Then, click Next 5. Outlook will complete the setup for your account, which might take several minutes. When you are notified that your account was successfully configured, click Finish. 6. You may need to restart Outlook for the changes to take effect. Change offline access setting You can use Outlook on your laptop or desktop computer when you’re not connected to the Internet. Email, calendar, and other items are kept in an Outlook data file on your computer so you can work offline. -
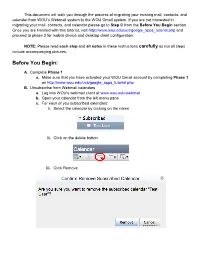
Before You Begin
This document will walk you through the process of migrating your existing mail, contacts, and calendar from WOU’s Webmail system to the WOU Gmail system. If you are not interested in migrating your mail, contacts, and calendar please go to Step C from the Before You Begin section. Once you are finished with this tutorial, visit http://www.wou.edu/ucs/google_apps_tutorial.php and proceed to phase 3 for mobile device and desktop client configuration. NOTE: Please read each step and all notes in these instructions carefully as not all steps include accompanying pictures. Before You Begin: A. Complete Phase 1 a. Make sure that you have activated your WOU Gmail account by completing Phase 1 on http://www.wou.edu/ucs/google_apps_tutorial.php B. Unsubscribe from Webmail calendars a. Log into WOU’s webmail client at www.wou.edu/webmail b. Open your calendar from the left menu pane c. For each of you subscribed calendars: i. Select the calendar by clicking on the name ii. Click on the delete button iii. Click Remove C. Setting up your Gmail account a. Log into your Gmail account at http://gmail.mail.wou.edu b. Click on Settings in the upper right-hand corner of the screen c. Click on the Accounts tab d. Click on Add another email address you own e. Enter your name and WOU email address and click Next Step f. Click Send Notification g. Return to your inbox h. You should have an email with the subject “Western Oregon University Confirmation - Send Mail as [email protected].” If you do not see this email, wait 2 minutes and refresh your inbox. -

Email Transfer from Webmail to Gmail
Email Transfer from Webmail to Gmail Product: Google Mail Symptom: Transfer Webmail to Gmail Solution: Transfer Webmail to Gmail Footprints Public Solution #70834 In Your Oakland University Email Account 1. Click the gear in the top right corner then click Settings from the dropdown menu 2. Select Forwarding and POP/IMAP tab and then Enable POP for all mail (even mail that has already been downloaded) 3. Click Save Changes at the bottom of the screen Setting up 2-Step Verification and App Specific Password 1. Click on the circle with a letter in the top right corner and click My Account 2. Click Sign-in & security 3. Scroll down and click 2-Step Verification 4. Click Get Started 5. Type in your phone number and choose if you would like to receive a text or a phone call 6. You will need to input the code you received and click Next 7. You will the need to click Turn On to enable 2-Step Verification 8. Click the back arrow to go back to the Sign-in & security settings 9. Scroll down and click App passwords 10. Click Select Device and then choose Other (Custom name) 11. Name the device gmail then click Generate 12. A password will be generated. Copy the password, you will use it later In Your New Gmail Account 1. Click the gear in the top right corner then click Settings 2. Select the Accounts and Import tab then click Add a mail account 3. Type in your Oakland University email address in the popup window then click Next 4. -

Google Apps Training Guide
The Ultimate Google Apps Training Guide A Training Guide for Google Apps Users, from The Gooru *Note - This document will be updated over time, please check back to see the updates. To get notified of new updates: Add us to your Circles on Google+ **For in depth training on everything Google Apps, please visit Gooru University Table of Contents 1. Introduction 2. Gmail a. Basic Features b. Unique Features c. Manage Your Inbox d. Gmail Tricks e. Gmail Extensions f. Inbox by Gmail g. Other Training Materials 3. Calendars a. Calendar Features b. Calendar Labs c. Other Training Materials 4. Contacts a. Contacts Features b. Other Training Materials 5. Drive a. Basic Features b. Unique Features c. Drive Tricks d. Drive for Admins e. Other Training Materials 6. Docs a. Docs Features b. Docs Add-ons 7. Sheets a. Beginner Features b. Advanced Features c. Sheets Add-ons 8. Presentations a. Presentations Features 9. Google+ a. Google+ Features b. Other Training Materials 10. Conclusion © 2015 The Gooru. 2 Introduction If you’re reading this, you are probably new to the Google Apps ecosystem. You might not be aware of the platform’s amazing capabilities, from real- time collaboration, to 100% web applications and more. So what can you do to ensure you’re getting the most out of Google Apps? As a Google Apps user, it’s important to understand the basics of Google Apps and other features, in order to keep up with Google’s pace of innovation and ensure you’re getting the most out of Google Apps. -

Introduction to Email Part 1 Beginners Guide TOPIC INTRODUCTION to EMAIL - PART 1
Tech Savvy Seniors Introduction to Email Part 1 Beginners Guide TOPIC INTRODUCTION TO EMAIL - PART 1 WELCOME Email is one of the fundamental internet technologies, TO EMAIL! a tool used by nearly every person with an internet connection. It allows you to –at no cost – send a letter of unlimited length to one person, or many people at once. It arrives almost instantly, and they can reply straight away. Setting up your own email account will allow you to communicate with people you know in ways you never thought possible. WHO IS THIS While you will have heard of email, you may not know WORKSHOP FOR? exactly how it works, what you need to get set up, or how to use it. You won’t have an existing email account, either… but you will after this workshop! WHAT YOU’LL An internet-connected laptop or desktop computer; NEED either your own or supplied by the workshop organisers. You may need to share a computer with others in the workshop. WHAT YOU’LL This workshop covers the basic steps you need to help LEARN keep in touch with your family and friends using email. It will explain how to set up an email account, how to send an email, and how to read and reply to emails that have been sent to you. TIMETABLE SUBJECT DURATION We’ve broken down today’s workshop What is email and how does it work? 10 minutes into seven parts, with a 10-minute break in A guide to email addresses: what 10 minutes the middle. -
Setting up Webmail for Microsoft Outlook Express
Setting up WebMail for Microsoft Outlook Express Windows 2000/XP 1. Start your Microsoft Outlook Express program. 2. Left click the Tools menu and click on Accounts. 3. In the Accounts window click the Mail tab located at the top of the window. 4. Click the Add button on the right and select Mail. 5. Enter your name into the field. This is how your name will appear to others when you send them an email. Click Next. 6. Enter your @csustan.edu email address and click Next. 7. Select from the drop down menu that your incoming mail server is a IMAP server. Then enter in the following information and then click Next: a. Incoming mail server: asherah.csustan.edu b. Outgoing mail server: asherah.csustan.edu NOTE: If you are setting this up off campus you will need to use your ISP’s (Internet Service Provider) outgoing server information and settings. 8. Your account name should appear in the field, if it does not enter your login name. e.g. [email protected] has a login name of just jamesk. The login EXCLUDES the @csustan.edu. You may enter your password if you do not want outlook to ask for your password every time you start up outlook express. Click Next, and then click Finish to complete the setup. Then click Close to exit the accounts window. 9. Outlook express will ask if you would like to download the folders from the server. Select yes to view the folders available and then Click OK. 10. Your email is delivered to the Inbox located under asherah.csustan.edu.