IDOL Keyview Filter SDK 12.6 .NET Programming Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FLAC Decoder Using ARM920T Using S3C2440
International Journal of Engineering Research and Development e-ISSN: 2278-067X, p-ISSN: 2278-800X, www.ijerd.com Volume 4, Issue 7 (November 2012), PP. 21-24 FLAC Decoder using ARM920T using S3C2440 J. L. DivyaShivani1, M. Madan Gopal 2 1M.Tech (Embedded Systems) Student, 2Assoc.Professor Aurora’s Technological & Research Institute Uppal, Hyderabad, INDIA Abstract: In this paper, an embedded FLAC decoder system was designed, and the embedded development platform of ARM920T was built for the design. Furthermore, the IIS bus of S3C2440 in Linux which were used in designing the decoder system. Results show that the FLAC format sound can play well in the decoder system. The decoding solution can be applied to many high-end audio devices. With the development of multimedia technology, as well as the people's requirements to higher sound quality, the Lossy compression coding audio format such as MP3 cannot satisfy many music lovers. Therefore, many R & D staffs have research on how to develop Lossless Audio Decoding systems based on embedded devices with lower price and better sound quality. FLAC stands for Free Lossless Audio Codec, an audio format similar to MP3, but lossless, meaning that audio is compressed in FLAC without any loss in quality. This is similar to how Zip works, except with FLAC you will get much better compression because it is designed specifically for audio, and you can play back compressed FLAC files in your favorite player (or your car or home stereo) just like you would an MP3 file. FLAC stands out as the fastest and most widely supported lossless audio codec, and the only one that at once is non-proprietary, is unencumbered by patents, has an open- source reference implementation, has a well-documented format and API, and has several other independent implementations. -

Lossless Audio Codec Comparison
Contents Introduction 3 1 CD-audio test 4 1.1 CD's used . .4 1.2 Results all CD's together . .4 1.3 Interesting quirks . .7 1.3.1 Mono encoded as stereo (Dan Browns Angels and Demons) . .7 1.3.2 Compressibility . .9 1.4 Convergence of the results . 10 2 High-resolution audio 13 2.1 Nine Inch Nails' The Slip . 13 2.2 Howard Shore's soundtrack for The Lord of the Rings: The Return of the King . 16 2.3 Wasted bits . 18 3 Multichannel audio 20 3.1 Howard Shore's soundtrack for The Lord of the Rings: The Return of the King . 20 A Motivation for choosing these CDs 23 B Test setup 27 B.1 Scripting and graphing . 27 B.2 Codecs and parameters used . 27 B.3 MD5 checksumming . 28 C Revision history 30 Bibliography 31 2 Introduction While testing the efficiency of lossy codecs can be quite cumbersome (as results differ for each person), comparing lossless codecs is much easier. As the last well documented and comprehensive test available on the internet has been a few years ago, I thought it would be a good idea to update. Beside comparing with CD-audio (which is often done to assess codec performance) and spitting out a grand total, this comparison also looks at extremes that occurred during the test and takes a look at 'high-resolution audio' and multichannel/surround audio. While the comparison was made to update the comparison-page on the FLAC website, it aims to be fair and unbiased. -
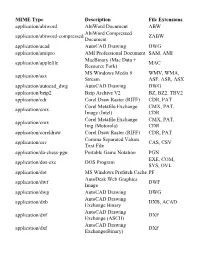
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

Energy-Efficient Design of the Secure Better Portable
Energy-Efficient Design of the Secure Better Portable Graphics Compression Architecture for Trusted Image Communication in the IoT Umar Albalawi Saraju P. Mohanty Elias Kougianos Computer Science and Engineering Computer Science and Engineering Engineering Technology University of North Texas, USA. University of North Texas, USA. University of North Texas. USA. Email: [email protected] Email: [email protected] Email: [email protected] Abstract—Energy consumption has become a major concern it. On the other hand, researchers from the software field in portable applications. This paper proposes an energy-efficient investigate how the software itself and its different uses can design of the Secure Better Portable Graphics Compression influence energy consumption. An efficient software is capable (SBPG) Architecture. The architecture proposed in this paper is suitable for imaging in the Internet of Things (IoT) as the main of adapting to the requirements of everyday usage while saving concentration is on the energy efficiency. The novel contributions as much energy as possible. Software engineers contribute to of this paper are divided into two parts. One is the energy efficient improving energy consumption by designing frameworks and SBPG architecture, which offers encryption and watermarking, tools used in the process of energy metering and profiling [2]. a double layer protection to address most of the issues related to As a specific type of data, images can have a long life if privacy, security and digital rights management. The other novel contribution is the Secure Digital Camera integrated with the stored properly. However, images require a large storage space. SBPG architecture. The combination of these two gives the best The process of storing an image starts with its compression. -

ACS – the Archival Cytometry Standard
http://flowcyt.sf.net/acs/latest.pdf ACS – the Archival Cytometry Standard Archival Cytometry Standard ACS International Society for Advancement of Cytometry Candidate Recommendation DRAFT Document Status The Archival Cytometry Standard (ACS) has undergone several revisions since its initial development in June 2007. The current proposal is an ISAC Candidate Recommendation Draft. It is assumed, however not guaranteed, that significant features and design aspects will remain unchanged for the final version of the Recommendation. This specification has been formally tested to comply with the W3C XML schema version 1.0 specification but no position is taken with respect to whether a particular software implementing this specification performs according to medical or other valid regulations. The work may be used under the terms of the Creative Commons Attribution-ShareAlike 3.0 Unported license. You are free to share (copy, distribute and transmit), and adapt the work under the conditions specified at http://creativecommons.org/licenses/by-sa/3.0/legalcode. Disclaimer of Liability The International Society for Advancement of Cytometry (ISAC) disclaims liability for any injury, harm, or other damage of any nature whatsoever, to persons or property, whether direct, indirect, consequential or compensatory, directly or indirectly resulting from publication, use of, or reliance on this Specification, and users of this Specification, as a condition of use, forever release ISAC from such liability and waive all claims against ISAC that may in any manner arise out of such liability. ISAC further disclaims all warranties, whether express, implied or statutory, and makes no assurances as to the accuracy or completeness of any information published in the Specification. -

Es Fluttert Gewaltig René Jahn, SIB Visions Gmbh
Es Fluttert gewaltig René Jahn, SIB Visions GmbH Wer eine App für mobile Geräte entwickeln möchte, as JVx Framework [1] ermöglicht die Erstellung von Daten- steht zumindest vor einer wichtigen Frage: Mit D bank-Applikationen für unterschiedlichste GUI-Technologien welcher Technologie soll die App realisiert werden? mit einer einzigen Source-Basis. Es ist sowohl eine GUI-Abstraktion als auch ein Full-Stack Application Framework. Die damit erstell- Da es aktuell verschiedenste Möglichkeiten gibt, ist ten Applikationen laufen ohne Änderungen im Browser mittels Ja- die Antwort nicht sofort klar. Mit diesem Problem vaScript/CSS, am Desktop mit Swing oder JavaFX und auf mobilen war das Framework-Team von SIB Visions ebenfalls Geräten mithilfe nativer Apps. Mit JVx können Applikationen unter- schiedlichster Größe und Komplexität realisiert werden. Zwei Pro- konfrontiert, als es darum ging, einen Client für dukte, die mit JVx entwickelt wurden, sind beispielsweise SNOWsat das Open Source Application Framework JVx zu Maintain [3] und VisionX [4]. entwickeln. Wie es zu einer Entscheidung kam und vor allem was umgesetzt wurde, wird in diesem Wie soeben erwähnt, werden für die Ausführung auf mobilen Gerä- ten native Apps eingesetzt. Es gibt eine App für iOS und eine andere Artikel erklärt. für Android. Erfahrene App-Entwickler werden vermuten, dass die- iii iii 30 www.ijug.eu iiiiii se Apps unabhängig voneinander entwickelt wurden. Das ist auch Gesamteindruck war nicht zufriedenstellend. So blieb am Ende also genauso. Die iOS-App wurde mit Objective-C und die Android-App Flutter übrig. Doch nicht, weil es der letzte Kandidat war, sondern mit Java entwickelt. Das war im Jahr 2014 auch ein gangbarer Weg, weil man von Anfang an den Eindruck hatte, dass es sich um die da es nur wenige Lösungen gab, die eine Entwicklung mit nur einer richtige Technologie handelt. -

February 2005)
TechNews November 2006 TechNews is a technology, news and analysis service aimed at those in the education sector keen to stay informed about technology developments, trends and issues. Please navigate the newsletter by clicking on items within the table of contents. Networking and wireless ........................................................................................................... 2 Analysis: Trusted Computing and Network Access Control............................................................................. 2 Networking and wireless news ................................................................................................. 4 Becta Infrastructure Services Framework ............................................................................................................... 4 802.11n update ....................................................................................................................................................... 4 Predicted growth in GPS-based services................................................................................................................ 4 Mobile WiMAX......................................................................................................................................................... 5 Short range wireless developments ........................................................................................................................ 5 4G progress ........................................................................................................................................................... -

Automating Configuration N49(PDF)
Automating Network Configuration Brent Chapman Netomata, Inc. [email protected] www.netomata.com NANOG 49 — 13 June 2010 Copyright © 2010, Netomata, Inc. All Rights Reserved. Introduction Who I am What I'm here to talk about 2 Copyright © 2010, Netomata, Inc. All Rights Reserved. Why automate network configuration? Because automated networks are More reliable Easier to maintain Easier to scale 3 Copyright © 2010, Netomata, Inc. All Rights Reserved. For example... Imagine you're managing a moderately complex web site Multiple real and virtual hosts Several "environments" (production, testing, development, etc.) Separate VLAN for each environment 4 Copyright © 2010, Netomata, Inc. All Rights Reserved. For example... What networking devices & services need to be managed? Routers Switches Load Balancers Firewalls Real-time status monitoring (i.e., Nagios) Long-term usage monitoring (i.e., MRTG) 5 Copyright © 2010, Netomata, Inc. All Rights Reserved. For example... How to add new virtual host to existing load balancer pool? Set up host itself, using Puppet or cfengine or whatever Add host to VLAN defs on switches Add host to ACLs on routers Add host to pool on load balancers Add host to NAT and ACLs on firewalls Add host to real-time monitoring (i.e., Nagios) Add host to usage monitoring (i.e., MRTG) 6 Copyright © 2010, Netomata, Inc. All Rights Reserved. For example... What's the problem with doing all that by hand? You have to remember how to manage all those very different devices (and you probably don't do it very often) It takes a lot of time Every step is a chance to make a mistake You might get distracted, and never finish Over time, these small mistakes add up, leading to inconsistent networks that are unreliable and difficult to troubleshoot 7 Copyright © 2010, Netomata, Inc. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Metadefender Core V4.13.1
MetaDefender Core v4.13.1 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Improved Lossy Image Compression with Priming and Spatially Adaptive Bit Rates for Recurrent Networks
Improved Lossy Image Compression with Priming and Spatially Adaptive Bit Rates for Recurrent Networks Nick Johnston, Damien Vincent, David Minnen, Michele Covell, Saurabh Singh, Troy Chinen, Sung Jin Hwang, Joel Shor, George Toderici {nickj, damienv, dminnen, covell, saurabhsingh, tchinen, sjhwang, joelshor, gtoderici} @google.com, Google Research Abstract formation from the current residual and combines it with context stored in the hidden state of the recurrent layers. By We propose a method for lossy image compression based saving the bits from the quantized bottleneck after each it- on recurrent, convolutional neural networks that outper- eration, the model generates a progressive encoding of the forms BPG (4:2:0), WebP, JPEG2000, and JPEG as mea- input image. sured by MS-SSIM. We introduce three improvements over Our method provides a significant increase in compres- previous research that lead to this state-of-the-art result us- sion performance over previous models due to three im- ing a single model. First, we modify the recurrent architec- provements. First, by “priming” the network, that is, run- ture to improve spatial diffusion, which allows the network ning several iterations before generating the binary codes to more effectively capture and propagate image informa- (in the encoder) or a reconstructed image (in the decoder), tion through the network’s hidden state. Second, in addition we expand the spatial context, which allows the network to lossless entropy coding, we use a spatially adaptive bit to represent more complex representations in early itera- allocation algorithm to more efficiently use the limited num- tions. Second, we add support for spatially adaptive bit rates ber of bits to encode visually complex image regions. -

On the Interoperability of Ebook Formats
It is widely seen as a serious problem that European as well as international customers who have bought an ebook from one of the international ebook retailers implicitly subscribe to this retailer as their sole future ebook On the Interoperability supplier, i.e. in effect, they forego buying future ebooks from any other supplier. This is a threat to the qualified European book distribution infrastructure and hence the European book culture, since subscribers to one of these of eBook Formats ebook ecosystems cannot buy future ebooks from privately owned community-located bricks & mortar booksellers engaging in ebook retailing. This view is completely in line with the Digital Agenda of the European Commission calling in Pillar II for “an effective interoperability Prof. Christoph Bläsi between IT products and services to build a truly digital society. Europe must ensure that new IT devices, applications, data repositories and services interact seamlessly anywhere – just like the Internet.” Prof. Franz Rothlauf This report was commissioned from Johannes Gutenberg University Johannes Gutenberg-Universität Mainz – Germany Mainz by the European and International Booksellers Federation. EIBF is very grateful to its sponsors, namely the Booksellers Association of Denmark, the Booksellers Association of the Netherlands and the Booksellers Association of the UK & Ireland, whose financial contribution made this project possible. April 2013 European and International Booksellers Federation rue de la Science 10 – 1000 Brussels – Belgium – [email protected]